
Security and finance leaders think they're aligned. Our new research with 300 of them says otherwise.
54% of finance leaders need strategic alignment metrics. Security's giving them maturity metrics instead. The language barrier is real—and fixable. expel.com/blog/new-res...
14.01.2026 17:48 — 👍 0 🔁 0 💬 0 📌 0

New Expel AI upgrade: “Pop the hood” on our detection strategies
Expel added new AI-generated descriptions to our detection rules, written in plain English, to improve transparency and understanding.
We just dropped a new AI upgrade 🫳
Now you get plain-English explanations for every detection rule. See exactly which rules are firing, how your coverage evolves, and what's actually protecting you. Transparency isn't a feature, it's how MDR should work. expel.com/blog/new-exp...
09.01.2026 18:16 — 👍 1 🔁 0 💬 0 📌 0

On the radar: Weeding out XMRig
XMRig is a cryptocurrency miner considered less malicious than other threats, but it's still worth prioritizing.
We're seeing XMRig cryptominers popping up everywhere recently. Threat actors love them because they’re a simple way to make money, and they can go unnoticed.
Here's how to spot them and shut them down before threat actors start monetizing: expel.com/blog/on-the-...
07.01.2026 19:47 — 👍 0 🔁 0 💬 0 📌 0

Our cybersecurity predictions for 2026
Our experts and leaders are sharing their predictions for cybersecurity trends in 2026 to help you start strategizing.
Our security leaders made their (brutally honest) 2026 predictions. The one thing they agree on? AI isn’t going anywhere, and it’s bringing new capabilities and threats into the new year.
Read all of their unfiltered takes: expel.com/blog/cyberse...
02.01.2026 18:32 — 👍 0 🔁 0 💬 0 📌 0

Why building a 24x7 SOC is getting harder (and what actually works instead)
The math on building an in-house SOC has changed, including the real costs, why retention is brutal, and what actually works.
Your analysts are drowning. You can't hire fast enough. And even if you could, the math doesn't work.
The economics of running a 24×7 SOC have changed. Use our free calculator that shows you what your team needs whether that's building, buying, or augmenting: expel.com/blog/buildin...
29.12.2025 18:08 — 👍 0 🔁 0 💬 0 📌 0

Stories from the SOC: The second coming of Shai Hulud
A new variant of the Shai Hulud worm has been discovered, and we're sharing effective approaches to remediate the threat.
Since then, we’ve continued to see and field incidents involving compromised NPM packages.
Here's the approach we've developed to identify and stop Shai Hulud activity: expel.com/blog/the-sec...
23.12.2025 17:52 — 👍 1 🔁 1 💬 0 📌 0
In the SOC, you get used to the noise. But a couple weeks ago, a single string cut through the noise: SHA1HULUD. It felt like seeing a ghost.
We traced the activity to a public GitHub repository where the customer's private cloud keys and secrets were exposed for anyone to grab.
23.12.2025 17:52 — 👍 2 🔁 0 💬 1 📌 0

More SIEM flexibility: Expel MDR adds support for Panther
Expel announces support for Panther's cloud-native SIEM as the latest in our long list of advanced integrations.
Expel MDR now supports Panther.
We integrate with your cloud-native SIEM, bringing our detections, 24x7 monitoring, and incident response to work alongside what you've already built.
Use the tools that work for you. We'll make them work harder. expel.com/blog/more-si...
16.12.2025 17:51 — 👍 0 🔁 0 💬 0 📌 0

⚠️ Attackers are buying Google Ads that appear when looking up how to troubleshoot your Mac. The ad takes you to a shared ChatGPT chat that tells you to copy-paste some code. You've just executed malware.
Kroll has a solid write-up on the mechanics: www.kroll.com/en/publicati...
09.12.2025 17:50 — 👍 0 🔁 0 💬 0 📌 0

Expel Quarterly Threat Report, Q3 2025: Threat intel recap
Here's a refresher on the threat intel we shared throughout the third quarter of 2025. Catch up on what you missed.
What actually works: strict application control policies and sanctioned tools. If users need productivity apps, give them approved options—or they'll find their own.
Full threat intel recap here: expel.com/blog/expel-q...
06.11.2025 16:02 — 👍 1 🔁 0 💬 0 📌 0
AI is making this worse. LLMs let criminals create convincing decoy applications faster than ever. The line between malware and PUPs is blurring, and it's not coming back.
06.11.2025 16:02 — 👍 0 🔁 0 💬 1 📌 0

We tracked BaoLoader through code-signing certificates across dozens of companies in the US, Panama, and Malaysia. It made up 13% of all commodity malware we identified this quarter. TamperedChef had 34,000+ downloads.
06.11.2025 16:02 — 👍 0 🔁 0 💬 1 📌 0
Part two of our QTR, Q3 2025 just dropped: malware disguised as apps that actually work.
BaoLoader hides backdoors in PDF editors and browsers. TamperedChef is a recipe app with hidden command codes. These apps function as promised, which is why users don't suspect anything.
06.11.2025 16:02 — 👍 0 🔁 0 💬 1 📌 0

Ransomware gang runs ads for Microsoft Teams to pwn victims
: You click and think you're getting a download page, but get malware instead
Imagine searching for Microsoft Teams, visiting the link at the top of the results, & getting hit with malware. That's the malvertising campaign that the Rhysida ransomware gang has been running.
Expel Intel is tracking this campaign. Here's what we've uncovered: www.theregister.com/2025/10/31/r...
05.11.2025 15:49 — 👍 0 🔁 0 💬 0 📌 0
Orgs seeing success with defending against identity attacks are the ones treating it as the primary battleground—with budget, priority, and controls that block attackers before compromise.
The trend is moving in the right direction but there's still more work to do since 45.1% aren't being blocked.
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0
The attack surface lesson:
• Credentials → cloud services
• Malware → endpoints
• Misconfigurations → cloud infrastructure
Each surface is distinct. One defensive strategy doesn't cover all three. You need different plans for each.
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0

Industry breakdown shows distinct patterns:
• Manufacturing: highest total incident volume (overtook financial services)
• Healthcare: disproportionately hit by non-targeted malware
• Pharma & chemical: highest proportion of identity attacks in top 10
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0

Cloud infrastructure attacks remain low volume (1.1% of total incidents) but are diversifying.
Biggest increase: secret key exposure, up 7.8 percentage points from Q2 to 26.8% of cloud incidents. Keys exposed through hardcoded credentials or supply chain attacks like Shai Hulud.
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0
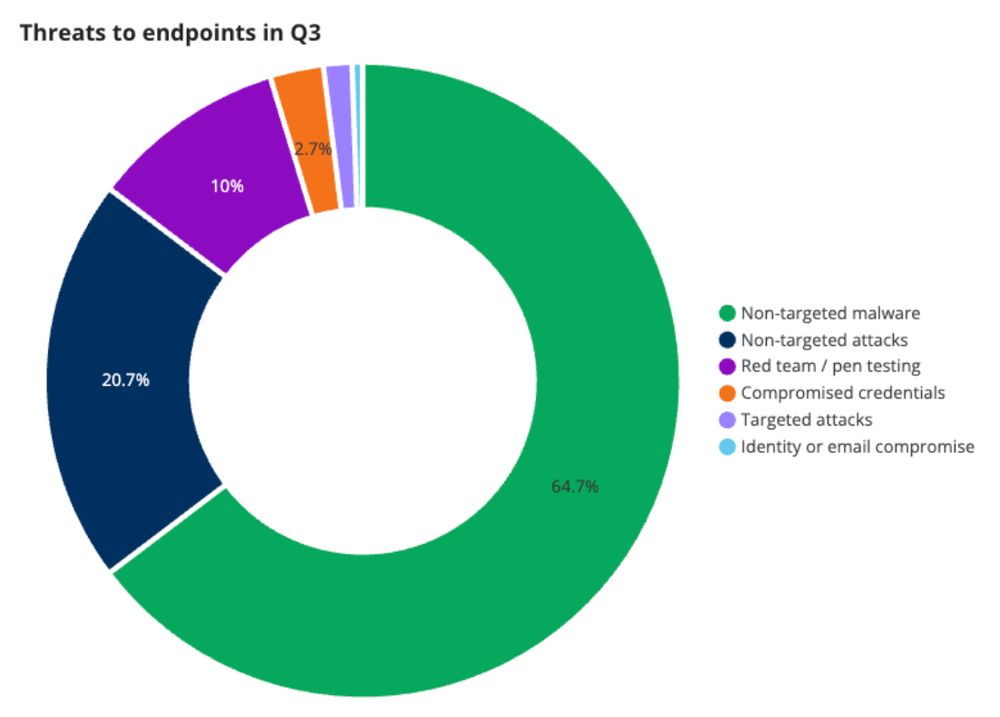
Endpoints tell a different story
Non-targeted malware dominates at 64.7% of endpoint incidents. This swung back up from 50.2% in Q2.
Attackers are still using traditional tactics—malware, compromising public-facing systems—to get onto devices.
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0

While identity attacks increased QoQ, 54.9% of those attacks were stopped when compromised credentials were entered—meaning controls blocked access before account takeover.
Modern identity controls (MFA, conditional access, monitoring) are working when implemented properly.
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0
Q3 2025 Threat Report is out. We analyzed thousands of real incidents across customer environments.
Here’s what stood out: 73.9% of all incidents were identity-based attacks. Up from 67.6% last quarter.
Let’s dive into the Q3 numbers 🧵
05.11.2025 14:52 — 👍 0 🔁 0 💬 1 📌 0

Certified OysterLoader: Tracking Rhysida ransomware gang activity via code-signing certificates
Rhysida ransomware gang has been using code-signing certificates to validate their malware campaigns repeatedly. Here's the latest.
Stay skeptical of sponsored search results. Verify downloads directly from vendor sites. We're here if you need help hunting for these indicators in your environment.
Overview of the campaign, IOCs, and file hashes: expel.com/blog/certifi...
31.10.2025 14:33 — 👍 0 🔁 0 💬 0 📌 0
The campaign is accelerating, not slowing down. It works because it exploits something security tools can't easily fix: users searching for legitimate software and trusting what looks official.
31.10.2025 14:33 — 👍 0 🔁 0 💬 1 📌 0
We're tracking this across hundreds of customer environments and feeding it into our detections. When we spot these techniques, we're already hunting for early indicators in other environments—before it becomes an incident.
31.10.2025 14:33 — 👍 0 🔁 0 💬 1 📌 0

These malicious ads don't just show up in search results. Windows 11 serves Bing ads directly in the Start menu. That "sponsored" PuTTy result with the lowercase Ts? Yeah, that won’t lead to the real PuTTy; that’ll download OysterLoader.
31.10.2025 14:33 — 👍 0 🔁 0 💬 1 📌 0
They've even figured out how to abuse Microsoft's Trusted Signing service at scale despite 72-hour certificate validity designed to prevent this. Microsoft has revoked 200+ of their certificates. They keep getting new ones.
31.10.2025 14:33 — 👍 0 🔁 0 💬 1 📌 0
What makes this campaign stick: they've burned through 40+ code-signing certificates to keep detection rates low. Fresh certificates = trusted by Windows. By the time AV catches up, they've moved to the next one.
31.10.2025 14:33 — 👍 0 🔁 0 💬 1 📌 0
The Rhysida ransomware gang (formerly Vice Society) is running the same playbook as last year—buying Bing ads to deliver fake Microsoft Teams, PuTTy, and Zoom downloads.
Click the wrong sponsored result? You’ve just installed OysterLoader, their initial access malware.
31.10.2025 14:33 — 👍 0 🔁 0 💬 1 📌 0

⚠️Attackers are actively exploiting CVE-2025-59287, a recently identified vulnerability in WSUS. Successful exploitation allows an attacker to run code using SYSTEM privileges. Expel caught & contained incidents related to this in two customer environments this AM.
Details: expel.com/blog/wsus-re...
24.10.2025 18:13 — 👍 1 🔁 0 💬 0 📌 0


















