LLMs can repair code, but often miss the broader context developers use every day.
We propose a 3-layer knowledge injection framework that incrementally feeds LLMs with bug, repository, and project knowledge.
Preprint of our ASE '25 paper: arxiv.org/pdf/2506.24015
24.08.2025 14:53 — 👍 1 🔁 1 💬 1 📌 0
Error analysis reveals that unresolved bugs are not randomly distributed; they cluster around specific bug types and higher complexity profiles. In particular, Program Anomaly, Network, and GUI bugs remain the most challenging for both models.
24.08.2025 14:55 — 👍 0 🔁 0 💬 0 📌 0
Evaluated on 314 real-world Python bugs, we observed consistent gains in both #fixed and Pass@k scores for Llama 3.3 and GPT-4o-mini, demonstrating a 23% improvement over prior work.
24.08.2025 14:54 — 👍 0 🔁 0 💬 1 📌 0
This layered approach offers several advantages.
Allows simpler bugs to be fixed with minimal input, conserving tokens and computation.
Scales context progressively, injecting more information only when necessary. Enables analysis of bug types & complexity.
24.08.2025 14:54 — 👍 0 🔁 0 💬 1 📌 0
1️⃣ Bug Knowledge (e.g., immediate code and test context)
2️⃣ Repository Knowledge (e.g., related files, dependencies, commit history)
3️⃣ Project Knowledge (e.g., documentation, past bug fixes)
24.08.2025 14:53 — 👍 0 🔁 0 💬 1 📌 0
LLMs can repair code, but often miss the broader context developers use every day.
We propose a 3-layer knowledge injection framework that incrementally feeds LLMs with bug, repository, and project knowledge.
Preprint of our ASE '25 paper: arxiv.org/pdf/2506.24015
24.08.2025 14:53 — 👍 1 🔁 1 💬 1 📌 0
💡 If you are building, evaluating, or relying on LLMs for software development, please ask yourself: Did it warn you about the hidden security risk?
07.04.2025 13:43 — 👍 0 🔁 0 💬 0 📌 0
As a preliminary solution to this problem, we built a CLI tool prototype that integrates static analysis with LLM prompting, aiming to make AI code suggestions more secure by design.
07.04.2025 13:43 — 👍 0 🔁 0 💬 1 📌 0
However, when LLMs do warn you, they tend to offer more complete explanations, including potential causes of the vulnerability, exploits, and even fixes.
07.04.2025 13:43 — 👍 0 🔁 0 💬 1 📌 0
We evaluated GPT-4, Claude 3, and Llama 3 across 300 real-world Stack Overflow posts containing vulnerable code.
The results?
⚠️<40% of vulns flagged
⚠️As low as 12.6% when code was obfuscated
⚠️Common issues (e.g., unsanitized input) often missed - unless explicitly prompted
07.04.2025 13:43 — 👍 0 🔁 0 💬 1 📌 0
Delighted to share that our paper, led by my PhD advisee Ramtin Ehsani, “Towards Detecting Prompt Knowledge Gaps for Improved LLM-guided Issue Resolution,” has been accepted to the Research Track of MSR 2025.
Preprint: soar-lab.github.io//papers/MSR2...
21.01.2025 02:17 — 👍 3 🔁 0 💬 0 📌 0
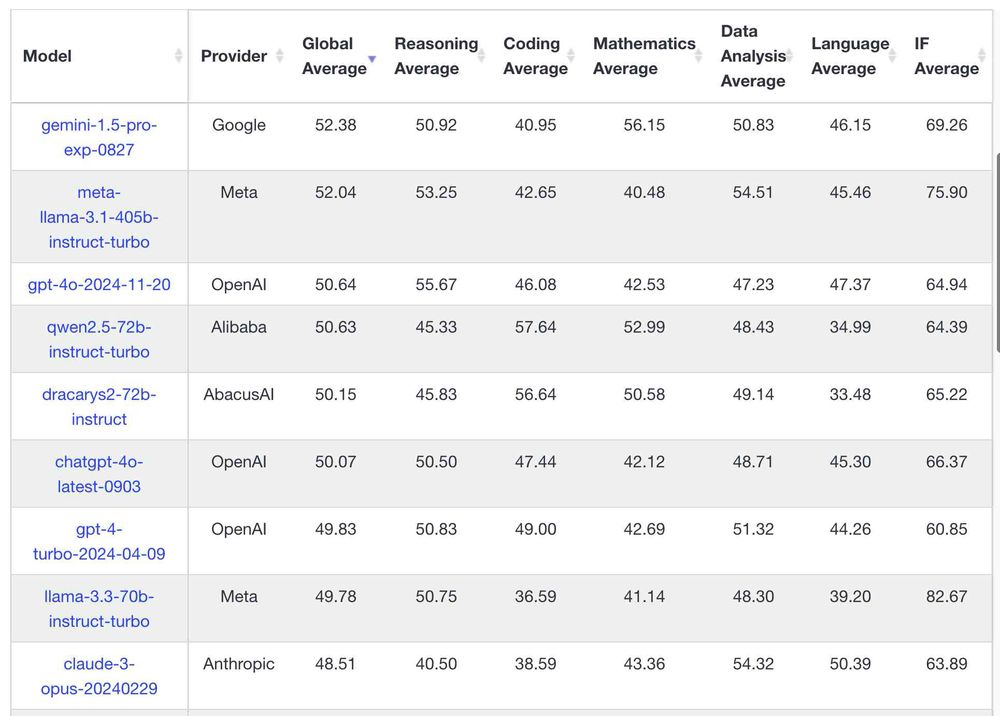
I can now run a GPT-4 class model on my laptop
Meta’s new Llama 3.3 70B is a genuinely GPT-4 class Large Language Model that runs on my laptop. Just 20 months ago I was amazed to see something that felt …
I can now run a GPT-4 class model on my laptop
(The exact same laptop that could just about run a GPT-3 class model 20 months ago)
The new Llama 3.3 70B is a striking example of the huge efficiency gains we've seen in the last two years
simonwillison.net/2024/Dec/9/l...
09.12.2024 15:19 — 👍 359 🔁 59 💬 11 📌 6
Congrats!!
10.12.2024 14:59 — 👍 1 🔁 0 💬 0 📌 0

#NeurIPS2024 paper 3, Assemblage - the dataset of source-to-binary projects compiled from GitHub that you've dreamed of bet never had before! Collab with @krismicinski.bsky.social and a multi-year effort to get to @NeurIPSConf @BoozAllen arxiv.org/abs/2405.03991
07.12.2024 20:01 — 👍 6 🔁 3 💬 1 📌 0

🎉 Thrilled to share that our paper (with Ramtin Ehsani and @rezapour.bsky.social) has been accepted at NLBSE'25, co-located with @icseconf.bsky.social! 🎉
Our work shows promise in improving toxicity detection in OSS using moral values & psycholinguistic cues. Preprint coming soon.
09.12.2024 16:42 — 👍 3 🔁 2 💬 0 📌 0
Can you please add me here
23.11.2024 03:28 — 👍 1 🔁 0 💬 0 📌 0
Researcher, Computer Security @ ICSI
Chief Mad Scientist @ Skerry Technologies
Putting the Science in "Mad Science"
Digital, Explainable, and (usually) Adversarial Systems
Looking for employment: CV is here https://skerry-tech.com/cv.html
he/him
Professor for Empirical Software Engineering, interested in Open Science and Public Outreach. Hiding sometimes in the water.
🔗 http://www.mendezfe.org
Principal Researcher CodeScene | Adjunct Associate Professor Lund University. Interests: software engineering intelligence, quality assurance, maintainability.
I make networks faster—because buffering is evil. Assoc Prof @UIC. PhD @Purdue. Ex-NVIDIA chip tinkerer. Your MacBook Air might run my chip.
Assistant Professor, Wayne State University, Software Engineering researcher.
Professor of Software Engineering and Computer Science at the University of Ottawa, Canada
Sr. Director @CrowdStrike. Visiting Prof @UMBC. Interested in all things ML
❤️ developer tools + empirical software engineering + programming languages. Pronouns: he/him. #MTL #YVR #LKA 🇱🇰🇨🇦 keheliya.github.io
Hridesh Rajan is the Dean of the Tulane University School of Science and Engineering. At Tulane, his goal is to grow interdisciplinary, research-focused education in science and engineering for better lives. https://sse.tulane.edu
2nd ACM International Conference on AI-powered Software (AIware) | Co-located with ASE 2025
Assistant Professor in Software Engineering, Nara Institute of Science and Technology, Japan. From Adelaide, Australia. 🦘
https://brittany-reid.github.io/
Cybersecurity R&D Lead, @berkeleylab.lbl.gov; Adjunct Professor, UC Davis; Director, Trusted CI, the NSF Cybersecurity Center of Excellence. Fmr EiC, IEEE Security & Privacy.
https://infosec.exchange/@peisert
https://www.cs.ucdavis.edu/~peisert/
CASCON - The IEEE International Conference on Collaborative Advances in Software and Computing (35th anniversary).
Official Hashtag: #CASCON2025
Junior Group Leader @ http://codelounge.si.usi.ch . Tweets about software engineering, politics & more | He/him
Software engineering phd student at Carnegie Mellon University. Enjoys empirical open source software supply chain sustainability and security research, cycling, and climbing.
http://courtney-e-miller.github.io/
Working on Trustworthy AI4Code, SE/HCI at Microsoft Research.
Trying this out
Associate Teaching Professor in Software Engineering @ Carnegie Mellon University
Professor of Software Engineering/Information Systems & Head of Complex Systems Engineering Lab (LabESC) & Researcher of Software Ecosystems/Systems-of-Systems at https://br.linkedin.com/in/profrodrigosantos







