nope I see no way you can get xss. sorry :)
11.11.2025 11:28 — 👍 1 🔁 0 💬 0 📌 0nope I see no way you can get xss. sorry :)
11.11.2025 11:28 — 👍 1 🔁 0 💬 0 📌 0
<script>eval(myUndefVar);var inject="INJECTION_STARTS_HERE";var myUndefVar;alert(1);//";</script>
Imagine you have a XSS vulnerability but you have a undefined variable before your injection. Is all hope lost? Not at all you can use a technique called XSS Hoisting to declare the variable and continue your exploit. Thanks to ycam_asafety for the submission.
portswigger.net/web-security...

Nice addition! The only one missing is let, const, class ”hoising in the temporal dead zone” 😉
on a serious note I dont think its needed. But all these snippets reminded me of my final challenge in this post joaxcar.com/blog/2023/12...
also made me realize glitch.me is gone. Need to re-host
I dont think thats a security boundary that is considered. But I might be wrong
18.08.2025 09:06 — 👍 1 🔁 0 💬 1 📌 0
Made a new small challenge where you have to break out of a web worker to leak a token in the URL
Only works in Firefox and Safari
joaxcar.com/fun/worker/a...
Feels like a good time to double down on this
28.07.2025 10:49 — 👍 4 🔁 0 💬 0 📌 0
yep, innerText will return "what the user sees." and html entities will look like their real value to users. and thus also in the innerText
React and other frameworks will auto-encode input when used in their templates, but two here will undo that
ChatGPT got it wrong, Gemini2.5 made a lucky guess that was not all wrong, but with the wrong explanation
13.07.2025 21:06 — 👍 1 🔁 0 💬 0 📌 0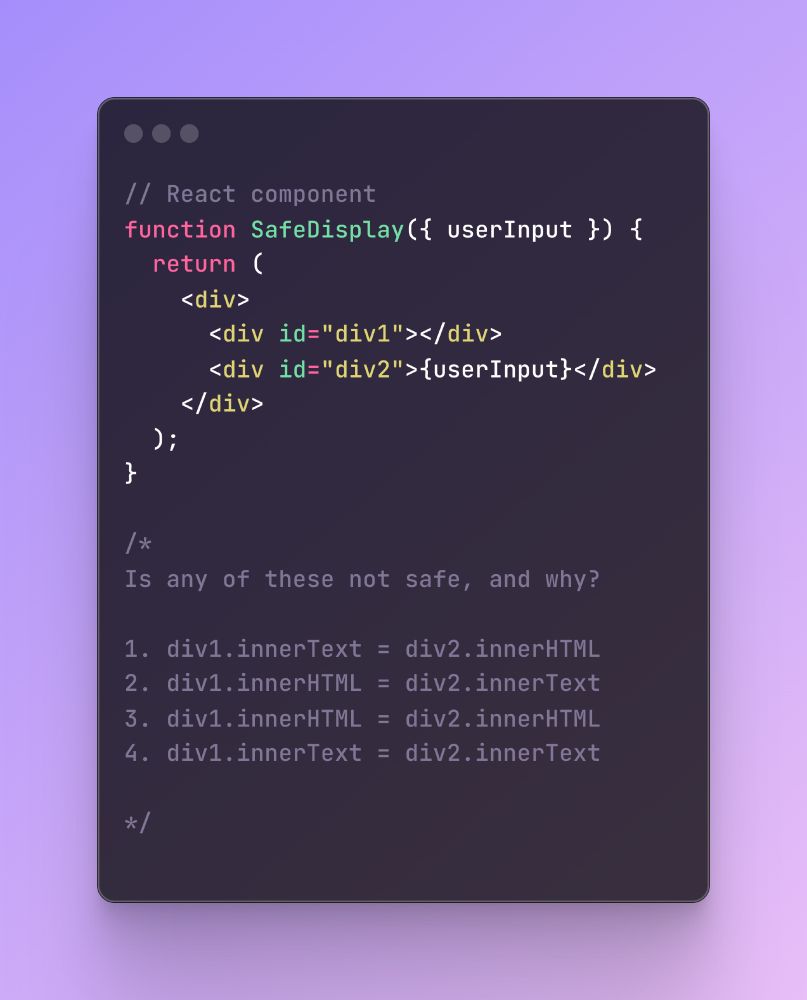
I often know that I know something. But when having to ask quickly, I stumble. I might have to start generating some "flash card" style questions for myself to try to ingrain some knowledge a bit deeper.
This is an example from earlier this week. It's not hard, but how quick and certain are you?

I am a huge fan of the #BuyFromEU movement! So far, I've ditched a lot of US stuff already, including Microsoft, Dropbox, 1Password, Notion, Grammarly, Amazon, Slack, and Google.
This helped a lot: european-alternatives.eu

Today was my last day as a pentester at Bsecure. After a three-year journey of hunting on the side, I’m ready to go all-in as a full-time bug bounty hunter. You can read about my journey from pentester to full-time hunter here: gelu.chat/posts/from-p...
04.07.2025 15:09 — 👍 23 🔁 7 💬 3 📌 0
Nice post! My journey followed a similar trajectory, but so far without the 200k LHE part :)
Inspiring. I will try to ramp up a bit after vacation and see if I can get to the next level as well. Even if I am quite happy where I am coasting right now
At the same time I often think after a finding something strange and niche: ”wow nice the codebase must be full of similar issues, lets cash in!” only to find that the one issue I found is the only one that exists.
02.07.2025 08:27 — 👍 1 🔁 0 💬 1 📌 0
where are you?
I have been enjoying south of France for two weeks now. A lot of great views, sunsets and the warm weather :)
This is great! have not had time to play with it yet but its definitely something I did not know I needed really badly 😄
17.06.2025 21:08 — 👍 2 🔁 0 💬 1 📌 0what are you doing now?
11.06.2025 19:41 — 👍 1 🔁 0 💬 0 📌 0
Double-Clickjacking, or "press buttons on other sites without preconditions". After seeing and experimenting with this technique for a while, I cooked up a variation that combines many small tricks and ends up being quite convincing.
Here's a flexible PoC:
jorianwoltjer.com/blog/p/hacki...
Cool! This is the built out POC that I only hinted at in my report :) my version was way less stable. But I did have the “and now a super high pipe” trick in my flappy game. Inspiring work Jorian
25.05.2025 19:23 — 👍 1 🔁 0 💬 0 📌 0A good suggestion, I think someone did try to use CSS in the challenge but failed. Never thought about it as a DOS vector
22.05.2025 21:34 — 👍 0 🔁 0 💬 0 📌 0@garethheyes.co.uk feel free to ignore the challenge part here, but would be awesome with your thoughts on shared processes and stalling the cpu. Especially as I have seen hints that cross-origin could potentially share process, even as it sounds strange
22.05.2025 07:25 — 👍 0 🔁 0 💬 1 📌 0
Here is the official writeup of my XSS challenge on Intigriti. I think it contains some fun browser trivia even for those who did not look at the chall
joaxcar.com/blog/2025/05...
links to blogs in discord is my new newsfeed. I recently found “the spanner” :)
my issue is that I am to much of a perfectionist to blog. write too much and too long. Need to learn to just post
Yep too bad. For me it sort of just went into not using these platforms at all. Doing more Discord. But there is something to “tweets” that I like. My X feed is way better though (if you filter p0rn and crypto bots. and the gore). Will try reviving bluesky again to see if it can be done
19.05.2025 18:55 — 👍 3 🔁 0 💬 0 📌 0This might be it. I kind of quit mastodon but it did have its own edge, while this place felt more like a watered out X. Might give it another go
19.05.2025 18:52 — 👍 0 🔁 0 💬 1 📌 0
I must have screwed up when setting up bluesky. Added to many “starterpacks”. My feed has been underwhelming.
Any one have any idea if there is an active bug bounty community here and how to tap into it?
Oh now I remember how it all came together. I actually read about the inconsistency in “The tangled web”. Which made me look up the spec and found the table with invalid but parsable urls
18.05.2025 08:53 — 👍 1 🔁 0 💬 0 📌 0Really great writeup @jorianwoltjer.com! The fuzzing part was inspiring. I originally found it myself by reading and playing with the docs. But I need to become more custom to just throw up small fuzzers myself
17.05.2025 21:56 — 👍 2 🔁 0 💬 1 📌 0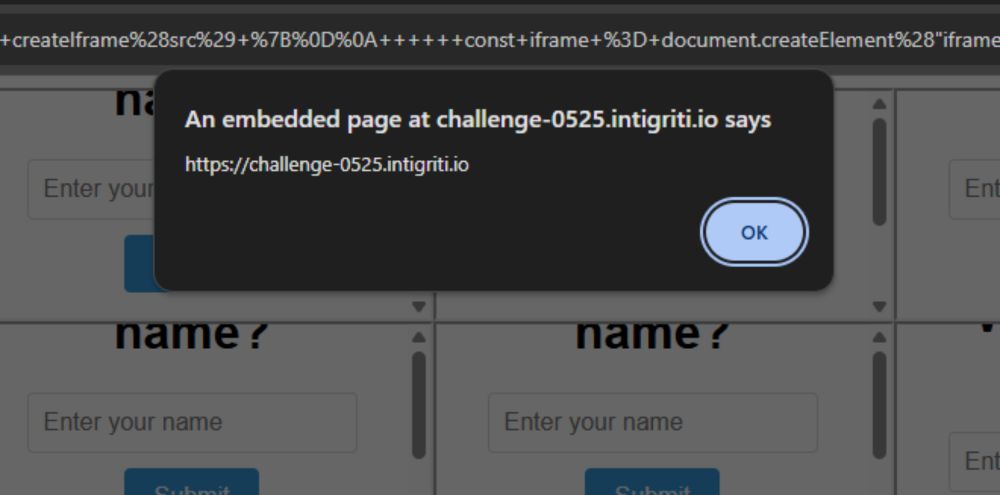
The legendary @joaxcar.bsky.social made a really interesting XSS challenge this month for Intigriti. My solution involved winning a race condition with 100 <iframe>s to utilize a DOM Clobbering gadget after bypassing a RegEx.
Check out the writeup below:
jorianwoltjer.com/blog/p/hacki...

I made a small Cross Site Scripting challenge for Intigriti that is live now. Feel free to practice your web hacking skills on it. “Based on a true story” as they say
challenge-0525.intigriti.io

A screenshot from Johan Carlsson's Linkedin account: "Last week, I participated in Nicolas Gregoire's course "Mastering Burp Suite Pro". I must say it was probably the single best technical course I have taken. Using Burp (one of the main tools I use daily) feels like a whole new experience. I can not recommend enough jumping on one of these sessions."
Getting feedback like this is what motivates me to work, again and again, on my Burp Suite training course. Thanks @joaxcar.bsky.social ☺️
02.04.2025 09:52 — 👍 21 🔁 4 💬 0 📌 0