
New chapter: I've transitioned to a part-time Chief Scientist role at @emproofsecurity.bsky.social .
I’m shifting my focus to my independent work in reverse engineering:
trainings • consulting • tooling • research
Details: synthesis.to
02.02.2026 10:29 —
👍 2
🔁 1
💬 0
📌 0

Happy to bring my Software Deobfuscation Techniques training back to @reconmtl.bsky.social - June 15–18, 2026 in Montreal!
Learn systematic approaches to defeating modern obfuscation found in DRM/anti-tamper & APT malware.
recon.cx/2026/en/trai...
28.01.2026 09:30 —
👍 5
🔁 1
💬 1
📌 0
YouTube video by VECTOR 35
Binary Ninja Live Stream: Nov 14th, 2025
Happy to share that later today (Friday, Nov 14, at 10:00 PM CET / 16:00 ET), I’ll be live on the #BinaryNinja livestream to talk about (anti-)reverse engineering & code (de)obfuscation. I'll also showcase some of my plugins.
www.youtube.com/watch?v=GQtX...
13.11.2025 22:36 —
👍 1
🔁 0
💬 0
📌 0
Impressive reverse engineering kung fu against widevine L3 by Felipe (x.com/_localo_) ! #hacklu
Cc @mrphrazer.bsky.social
23.10.2025 13:01 —
👍 3
🔁 2
💬 1
📌 0
YouTube video by Recon Conference
Recon 2025 - Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications
The recording of our (CC @nicolo.dev ) talk "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" at @reconmtl.bsky.social is now online!
Recording: www.youtube.com/watch?v=QxSG...
Slides: synthesis.to/presentation...
#BinaryNinja Plugin: github.com/mrphrazer/ob...
15.10.2025 22:56 —
👍 7
🔁 6
💬 0
📌 1
The new version of my #BinaryNinja plugin Obfuscation Analysis (v1.2) adds recursive function inlining in the decompiler.
It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries.
github.com/mrphrazer/ob...
11.10.2025 15:27 —
👍 5
🔁 3
💬 1
📌 0

GitHub - emproof-com/workshop_firmware_reverse_engineering: Workshop on firmware reverse engineering
Workshop on firmware reverse engineering. Contribute to emproof-com/workshop_firmware_reverse_engineering development by creating an account on GitHub.
We at @emproofsecurity.bsky.social open-sourced a free firmware reverse engineering workshop for self-study.
Topics: ELF analysis, cracking, malware triage, embedded-Linux, bare-metal, crypto-key extraction, anti-analysis. Docker setup and solutions included.
github.com/emproof-com/...
30.09.2025 08:36 —
👍 5
🔁 2
💬 0
📌 0
Reminder: If you’re interested in learning how to analyze and deal with obfuscated code, you’re welcome to join my training at @hexacon.bsky.social from October 6-9.
You can still register here: www.hexacon.fr/trainer/blaz...
04.08.2025 22:55 —
👍 2
🔁 0
💬 0
📌 0
Congrats!
01.08.2025 20:52 —
👍 1
🔁 0
💬 0
📌 0
A side-by-side view of Ghidra's decompiler. Left is the raw output, right is the output enhanced by the LLM.
Based on research by @mrphrazer.bsky.social and @mu00d8.bsky.social, presented at RECon 2024, I used graph theory code from Ghidra's codebase to select the order in which functions are sent to the LLM, ensuring as much context as possible is retained. The script is aptly named GhidrAI!
5/n
01.07.2025 12:35 —
👍 3
🔁 1
💬 1
📌 0
The slides from our @reconmtl.bsky.social talk, "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" (CC @nicolo.dev ), are now online!
Slides: synthesis.to/presentation...
Plugin: github.com/mrphrazer/ob...
27.06.2025 20:28 —
👍 10
🔁 5
💬 0
📌 1
Reminder: If you’re interested in code deobfuscation, you’re welcome to join my training at @reconmtl.bsky.social Montréal from June 24-27.
You can still register here: recon.cx/2025/trainin...
05.06.2025 14:31 —
👍 1
🔁 0
💬 0
📌 0
Honored to join @jstrosch.bsky.social on his podcast "Behind the Binary"! We discussed my RE journey, identifying & analyzing obfuscated code, software protection in industry vs malware, the dynamic between building & breaking protections, and others.
open.spotify.com/episode/7yJB...
04.06.2025 17:49 —
👍 5
🔁 1
💬 0
📌 0
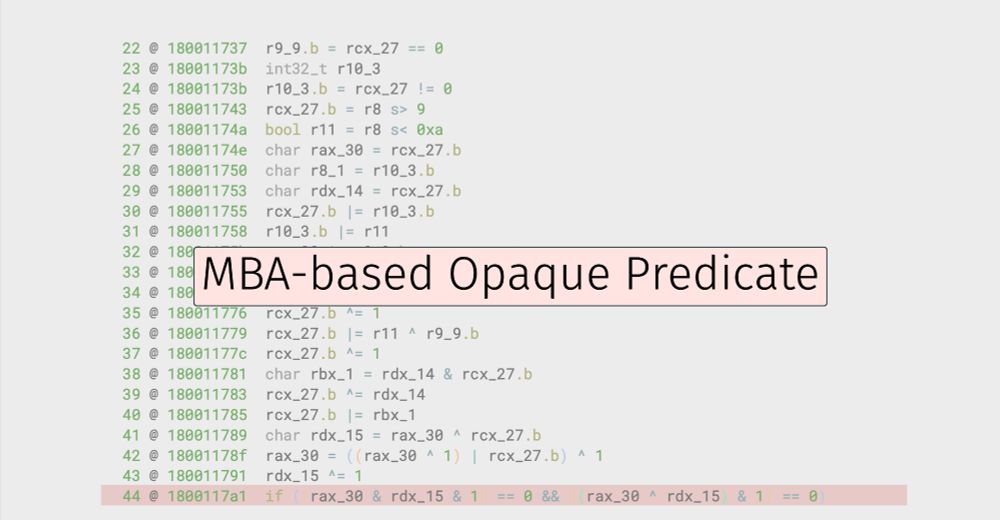
New #BinaryNinja plugin: Obfuscation Analysis
Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly.
Co-authored by @nicolo.dev; available in the plugin manager.
github.com/mrphrazer/ob...
25.05.2025 21:39 —
👍 21
🔁 9
💬 1
📌 1

Excited to teach my class on software deobfuscation in Paris at @hexacon.bsky.social , Oct 6–9, 2025!
Learn advanced techniques to defeat state-of-the-art obfuscation in DRMs & APT malware.
www.hexacon.fr/trainer/blaz...
05.05.2025 21:01 —
👍 8
🔁 0
💬 0
📌 1
Reminder: Training registrations are still open for my deobfuscation training at REcon Montreal. Secure your spot before prices go up on May 1!
27.04.2025 15:55 —
👍 2
🔁 0
💬 0
📌 0

At @reconmtl.bsky.social, @nicolo.dev and I discuss the current state of MBA (de)obfuscation and their applications. We’ll also introduce a new #BinaryNinja plugin for simplifying MBAs in the decompiler.
Details: cfp.recon.cx/recon-2025/f...
I'll also give a training: recon.cx/2025/trainin...
07.04.2025 16:12 —
👍 7
🔁 4
💬 0
📌 1
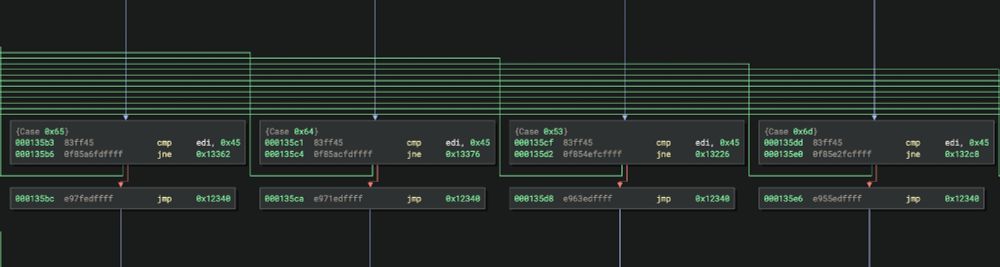
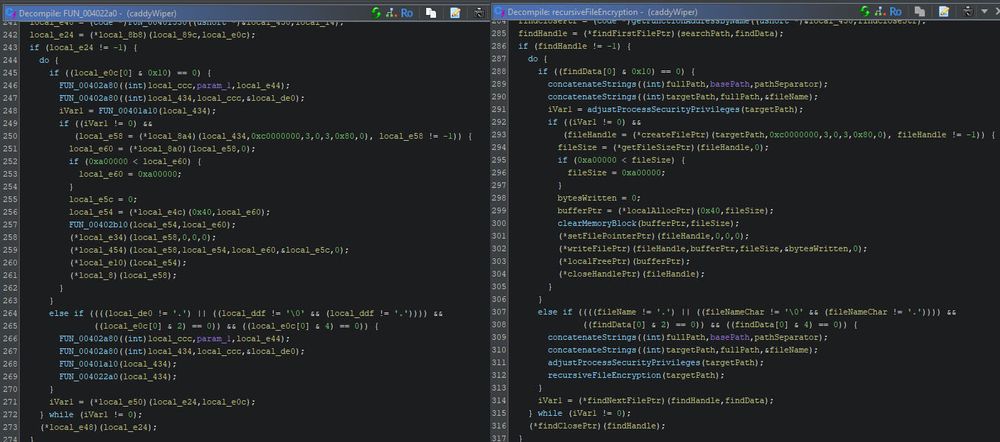
New heuristic in my #BinaryNinja plugin obfuscation_detection:
Duplicated Subgraphs uses iterative context hashing to spot repeated multi-block code. We merge each block’s signature with its successors over multiple rounds for efficiency.
Link: github.com/mrphrazer/ob...
14.03.2025 02:46 —
👍 9
🔁 6
💬 1
📌 0
RE//verse training registration closes today! Have to finalize count for the hotel. If you still want to join after registration closes, contact us ASAP as some extra slots may be available. https://re-verse.io/#trainings
18.02.2025 17:29 —
👍 2
🔁 2
💬 0
📌 0

My class on code deobfuscation at REcon Montreal (June 24-27) is now open for registration! Learn how to analyze obfuscated code and break it by writing custom tools using symbolic execution, SMT solving, and program synthesis.
Details & Register: recon.cx/2025/trainin...
18.02.2025 02:39 —
👍 9
🔁 1
💬 0
📌 2
YouTube video by emproof
Webinar: Software Protection -- Safeguarding Code Against Reverse Engineering
Last Thursday, I gave a webinar on anti-reverse engineering techniques like obfuscation, anti-debug, anti-tamper etc, including practical examples. Recording, slides and examples are now available.
Recording: www.youtube.com/watch?v=Ie1e...
Slides, Code & Samples: github.com/emproof-com/...
27.01.2025 12:52 —
👍 5
🔁 1
💬 1
📌 0
The line-up for @re-verse.io is impressive, but one talk I’m particularly excited about is from Vikas Gupta and Peter Garba:
“Standing on the Shoulders of Giants: De-Obfuscating WebAssembly using LLVM”
re-verse.sessionize.com/session/763329
10.01.2025 11:48 —
👍 4
🔁 0
💬 0
📌 0
The schedule of RE//verse is out now and contains some pretty interesting talks on reverse engineering and code (de)obfuscation!
I'll also give my deobfuscation training there: shop.binary.ninja/products/re-...
09.01.2025 22:53 —
👍 9
🔁 3
💬 0
📌 0















