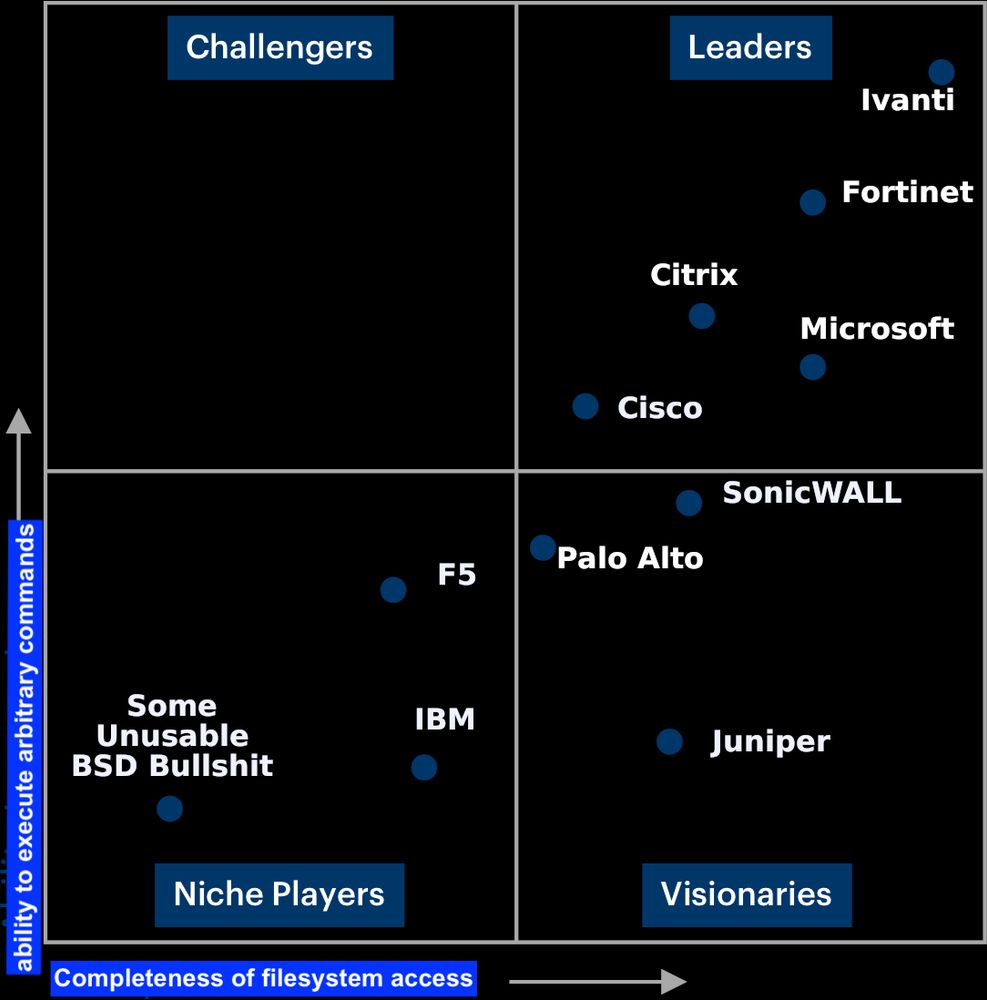
Funny magic cadrant ;-)
Finally a useful magic quadrant
Thanks to @wendynather for the discovery.
#cybersecurity #vulnerability
@raptor.infosec.exchange.ap.brid.gy
When cryptography is outlawed, bayl bhgynjf jvyy unir cevinpl. [bridged from https://infosec.exchange/@raptor on the fediverse by https://fed.brid.gy/ ]

Funny magic cadrant ;-)
Finally a useful magic quadrant
Thanks to @wendynather for the discovery.
#cybersecurity #vulnerability

A top-level overview of the presentation presented as a grid of thumbnails, showing 42 slides.
Thank you to everyone who made it out for my DEF CON 33 presentation, "Shaking Out Shells With SSHamble", you can find the materials online at https://hdm.io/decks/MOORE%20-%20Shaking%20Out%20Shells%20With%20SSHamble.pdf
This deck includes some […]
[Original post on infosec.exchange]
If you want an ebook of some public domain work, either:
1. Check standardebooks.org before Gutenberg. They clean up books from Gutenberg with sane typography and print design.
2. Consider buying a "Dover Thrift Editions" version of the ebook. Many fly-by-night ebook "publishers" are turning a […]
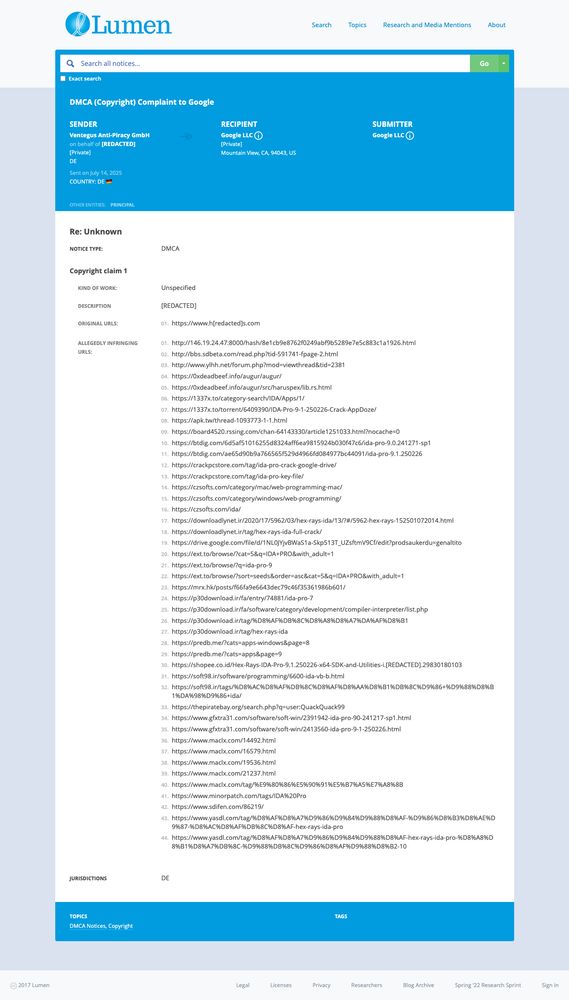
Full screenshot of https://lumendatabase.org/notices/54378675
#TIL that last month some dimwits at Ventegus Anti-Piracy GmbH (likely on behalf of Hex-Rays?) submitted a #DMCA (Copyright) Complaint to #Google to remove these two pages from search results:
https://0xdeadbeef.info/augur/augur/ […]
[Original post on infosec.exchange]
CVE-2025-48708: #ghostscript can embed plaintext #password in encrypted #PDFs 😶
https://www.openwall.com/lists/oss-security/2025/05/23/2
Another elegant #vulnerability #advisory by @qualys that was published a few months back
Local information disclosure in #apport and #systemd- #coredump
(CVE-2025-5054 and CVE-2025-4598)
https://www.qualys.com/2025/05/29/apport-coredump/apport-coredump.txt

Another fun #vulnerability writeup with a cool tcpdump GTFOBin trick
#FiberGateway GR241AG - Full #Exploit Chain
https://r0ny.net/FiberGateway-GR241AG-Full-Exploit-Chain/

CVE 2025 31200 #Apple #CoreAudio #vulnerability analysis 🤯
https://blog.noahhw.dev/posts/cve-2025-31200/

#Rust #Hypervisors for Memory Introspection and #ReverseEngineering
https://secret.club/2025/06/02/hypervisors-for-memory-introspection-and-reverse-engineering.html
https://github.com/memN0ps/illusion-rs
https://github.com/memN0ps/matrix-rs

Turin's radio tower with radome and radio bridge. Apparently this is used by the national TV broadcasters as a high capacity link for TV and radio, not as a radar for the Caselle Airport as I initially thought
#torino #turin #italy #moon #astro #radio #tower #radome

@disasmwinnie yeah, see also for additional details https://www.upwind.io/feed/cve-2024-12718-path-escape-via-pythons-tarfile-extraction-filters
09.08.2025 10:54 — 👍 0 🔁 0 💬 0 📌 0
Another fresh #Python #tarfile #vulnerability
Python TarFile.extractall(..., filter='tar') arbitrary file chmod
https://github.com/python/cpython/issues/127987
A nice series of inspiring logic #bugs! I somewhat pioneered timing leaks and it doesn’t surprise me at all that they are still around and kicking by the way ⏱️
Cracking the Vault: how we found zero-day flaws in authentication, identity, and authorization in #HashiCorp Vault […]

I 💚 format string #bugs! 🐞
Exploiting the #Synology TC500 at #Pwn2Own Ireland 2024 by @infosect
https://blog.infosectcbr.com.au/2025/08/01/exploiting-the-synology-tc500-at-pwn2own-ireland-2024/
@FritzAdalis ohh happy to see I’m not the only one who read it this way 😅
08.08.2025 13:24 — 👍 0 🔁 0 💬 0 📌 0
A couple other fun bugs 🐛
#Python - #Tarfile Realpath Overflow #Vulnerability
https://github.com/google/security-research/security/advisories/GHSA-hgqp-3mmf-7h8f
#Python #Tar Filter Bypass #Vulnerability
https://github.com/google/security-research/security/advisories/GHSA-7fj8-pjw2-r9vh
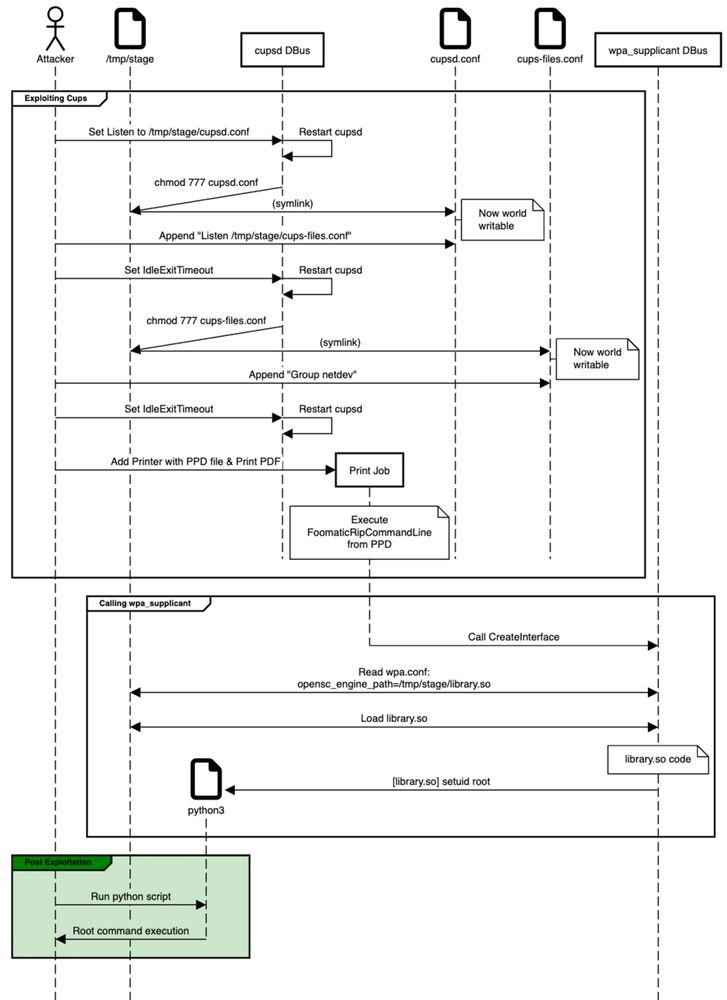
A depiction of the exploit chain
Here’s another fun one by @snyk! I’ve really enjoyed the clever building of the #exploit chain ✊
Abusing #Ubuntu 24.04 features for root privilege escalation
https://labs.snyk.io/resources/abusing-ubuntu-root-privilege-escalation/
A couple notable related writeups
A great primer on #dbus and #polkit that clearly shows how brittle they are
https://u1f383.github.io/linux/2025/05/25/dbus-and-polkit-introduction.html
An amazing #linux #kernel #vulnerability research and #exploit development writeup […]
Still catching up with older writeups… Loved this one by @qualys ✊
CVE-2025-6018: #LPE from unprivileged to allow_active in *SUSE 15's #PAM
CVE-2025-6019: #LPE from allow_active to root in #libblockdev via #udisks
https://cdn2.qualys.com/2025/06/17/suse15-pam-udisks-lpe.txt
Always happy news to see my work spark new joy. In this case, my @semgrep ruleset at https://github.com/0xdea/semgrep-rules. Congrats to @trailofbits and best wishes for a wonderful career to Will 👍
https://infosec.exchange/@trailofbits/114975919399280105

Yet another example of a “security product” causing more harm than good 🤦
CVE-2025-4660: #Forescout SecureConnector #RCE
https://www.netspi.com/blog/technical-blog/red-teaming/cve-2025-4660-forescout-secureconnector-rce/

Catching up with older writeups, this one stands out for #exploitation
Pre-Auth SQL Injection to RCE - #Fortinet FortiWeb Fabric Connector (CVE-2025-25257)
https://labs.watchtowr.com/pre-auth-sql-injection-to-rce-fortinet-fortiweb-fabric-connector-cve-2025-25257/

Embedded device #hacking 101 💚
#Exploiting #0days in abandoned #hardware by @trailofbits
https://blog.trailofbits.com/2025/07/25/exploiting-zero-days-in-abandoned-hardware/
I love this kind of #bugs, especially when they are features 🤣
#arm64: Linear mapping is mapped at the same static virtual address
https://project-zero.issues.chromium.org/issues/434208461
Today, I’m celebrating 1000 days in the #fediverse! Happy to have found such a wonderful home 🥳 :1000:
04.08.2025 02:08 — 👍 0 🔁 0 💬 1 📌 0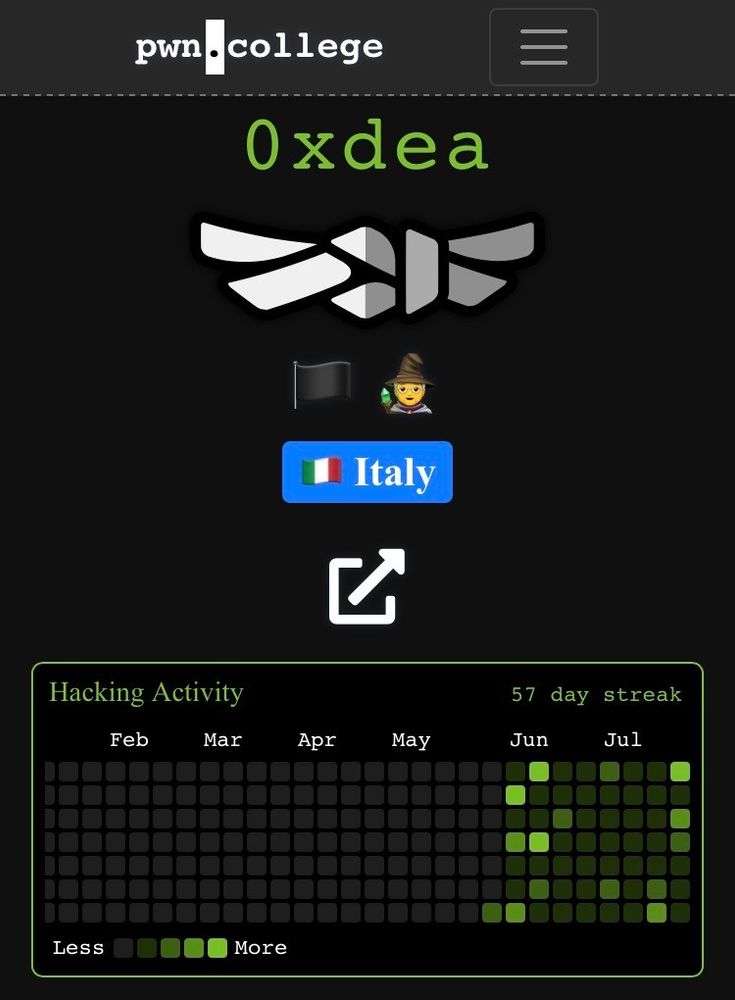
My pwn.college hacking activity dashboard showing a 57 day streak
Not long ago I posted about https://pwn.college. I got hooked up with it myself, and I almost got my yellow belt 💛 almost, ‘cause I still have some of the earlier/easier challenges left 😅 I’ll tackle them after the holidays 🏝️ before looking at the more […]
[Original post on infosec.exchange]
“Beginning today, within one week of reporting a vulnerability to a vendor, we will publicly share that a vulnerability was discovered.
We will share:
The vendor or open-source project that received the report.
The affected product.
The date the report was filed, and when the 90-day disclosure […]
In our last post, @apps3c shares some #PoCs of #GenAI/ #LLM security issues found in real-world assessments conducted for corporate clients, with a focus on #vulnerabilities that can be exploited to gain unauthorized access to data, resources, and services […]
29.07.2025 12:35 — 👍 0 🔁 2 💬 0 📌 0
Multiple serial offenders. Modems through the ages. A collection...
Multiple serial offenders. Modems through the ages. A collection...
These are all the modems I've owned, ranging from a 2400 baud Amstrad modem funded by working for and with Acorn, right up to my first DSL modem. Notable is the one in black, also a 2400 […]
[Original post on infosec.exchange]
“We are now living in a global state that has been structured for the benefit of non-human entities with non-human goals. They have enormous media reach, which they use to distract attention from threats to their own survival. They also have an enormous ability to support litigation against […]
24.07.2025 05:18 — 👍 0 🔁 0 💬 0 📌 0