
But I thought Microsoft said it wasn't worth fixing? "Microsoft classified this as low severity and this will not be patched in the immediate future." arcticwolf.com/resources/bl...
30.10.2025 19:42 — 👍 4 🔁 5 💬 0 📌 0
But I thought Microsoft said it wasn't worth fixing? "Microsoft classified this as low severity and this will not be patched in the immediate future." arcticwolf.com/resources/bl...
30.10.2025 19:42 — 👍 4 🔁 5 💬 0 📌 0
I've done small (but fun) .NET Framework research, and I found a new exploitation primitive (vulnerable behavior). In many cases, it may directly lead to RCE.
I'll discuss it during Black Hat EU and I'll drop a paper afterwards 🫡
www.blackhat.com/eu-25/briefi...
Research is fun. One month ago, I thought that I'll never again make a research as good as my .NET deserialization one.
Here I am today, writing a new whitepaper. You never know the day 😅

My Sitecore CMS pre-auth RCE chain blog is public now. Enjoy 🫡
labs.watchtowr.com/is-b-for-bac...

I did my first 1daying ride with my friend Sonny. Enjoy🫡
Ivanti EPMM: CVE-2025-4427 and CVE-2025-4428 pre-auth RCE chain.
labs.watchtowr.com/expression-p...
Some serious question about a larg-scale usage of AI in Vuln Research.
Aren't you afraid of missing some key datails by outsourcing huge tasks to AI? I am.
If you rely on a tool, you're as good as your tool. If AI screws in a huge project, you probably won't even notice that.
😉
28.03.2025 19:38 — 👍 1 🔁 0 💬 0 📌 0
It seems that our Veeam CVE-2025-23120 post is live.
I would never do this research without @SinSinology He insisted a lot, thx man. 😅
If you know CVE-2024-40711, this vuln can be patch-diffed and exploit armed in 5 minutes. Unfortunately, it's super simple.
labs.watchtowr.com/by-executive...

My first watchTowr post is out! It was my first take on a CMS solution and I was able to get some interesting pre-auth RCE chains on Kentico Xperience. 😎
labs.watchtowr.com/bypassing-au...

Great news: I got invited to Microsoft Zero Day Quest onsite event.
Bad news: It overlaps with my kid's estimated due date 😅
Happy hacking to all of you who's planning to go to Redmond 😎
How long does it take for MITRE to reserve a CVE now?
I haven't done that for several years, and it seems that the wait time is much bigger nowadays 🤔

I had a blast during my first month at watchTowr :)
28.01.2025 15:47 — 👍 2 🔁 0 💬 0 📌 0
This year again, I am lucky enough to get nominated twice for the Top Ten Hacking Techniques, for my research on iconv and PHP, and lightyear. This time feels a bit special however, as these are my last blog posts on ambionics.
www.ambionics.io/blog/iconv-c...
www.ambionics.io/blog/lightye...
I'm happy to be on the nominations list second year in the row! This time, it's with "Half Measures and Full Compromise: Exploiting Microsoft Exchange PowerShell Remoting" research and some nice RCE chains on Exchange:)
chudypb.github.io/exchange-powershell.html
I'm happy to announce that I have recently joined watchTowr as a Principal Vulnerability Researcher. The break is over, it's time to do some new research 🫡
07.01.2025 13:08 — 👍 8 🔁 2 💬 1 📌 0
Does anyone use 34" 21:9 screen?
Does it work for a setup with a VM on a half of the screen and browser/IDE on the second half?🤔
After amazing (almost) 3 years, this is my last day at @thezdi.bsky.social. Huge thanks to the entire team, it was an honour to work with you folks!
New challenges and adventures are starting in 2025 :)
PS. Watch out for the ZDI blog, as several of my posts should appear there in 2025.
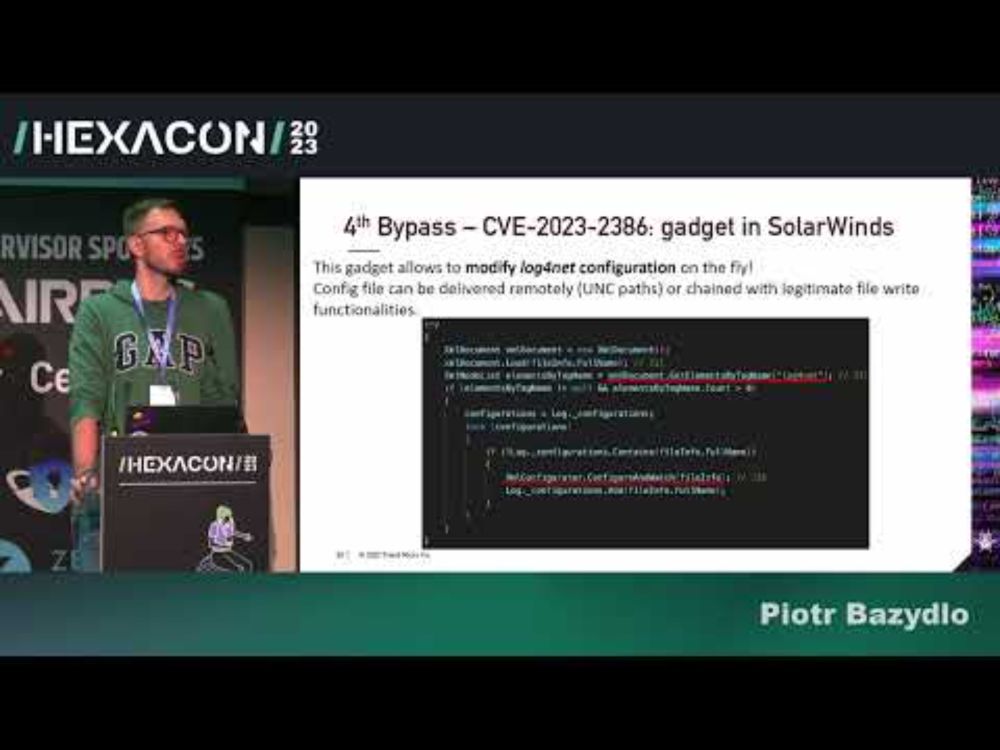
[4/n] My Hexacon 2023 talk about .NET Deserialization. New gadgets, insecure serialization (RCE through serialization) and custom gadgets found in the products codebase.
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...

[3/n] I've followed OffensiveCon talk with a series of 4 blog posts. The most interesting one describes a nice chain of 3 gadgets:
- Arbitrary File Write to drop DLL.
- Arbitrary FIle Read to leak DLL drop location
- DLL load gadget.
www.zerodayinitiative.com/blog/2024/9/...
[2/n] My OffensiveCon 2024 talk about Exchange PowerShell Remoting. It includes details concerning PowerShell Remoting deserialization and custom Exchange converters.
Several RCE chains included.
www.youtube.com/watch?v=AxNO...

[1/n] I want to kick off my profile here a little bit, thus I'll post several fun projects that I've made last year.
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...
You can use it for the NTLM Relaying, but I guess the success depends on the AD environment etc :)
13.12.2024 05:41 — 👍 1 🔁 0 💬 1 📌 0I wrote a fun, little blog post. Remote pre-auth file deletion in SolarWinds ARM allowed to achieve LPE on AD machines 🙃
12.12.2024 18:03 — 👍 9 🔁 6 💬 1 📌 0Rapid7 has disclosed the vulns from our exploit chain targeting the Lorex 2K Indoor Wi-Fi Security Camera, which we entered at this year's Pwn2Own Ireland. A 2 phase exploit, built upon 5 vulns - phase 1 is an auth bypass, whilst phase 2 is RCE. Disclosure, analysis and exploit here: t.co/J9VDwMDRsI
04.12.2024 09:32 — 👍 15 🔁 8 💬 1 📌 0Great post! BTW, thanks for the shout-out Steven :)
29.11.2024 18:48 — 👍 3 🔁 0 💬 1 📌 0