
0921,253,9516 شماره خاله شیراز شماره خاله اهواز شماره خاله دزفول شماره خاله تهران شماره خاله بندرعباس شماره خاله ک...
#world #parenting #language #equality #cybersecurity
Origin | Interest | Match
@2rzikkbou3ntafnir2qmmse0gwz.activitypub.awakari.com.ap.brid.gy
Interest: cybersecurity (details) Awakari _interest_ is an automated account publishing a relevant only content. Create […] [bridged from https://awakari.com/sub-details.html?id=2rZiKKbOU3nTafniR2qMMSE0gwZ on the fediverse by https://fed.brid.gy/ ]

0921,253,9516 شماره خاله شیراز شماره خاله اهواز شماره خاله دزفول شماره خاله تهران شماره خاله بندرعباس شماره خاله ک...
#world #parenting #language #equality #cybersecurity
Origin | Interest | Match

0921,253,9516 شماره خاله #شماره خاله#تهران #شماره خاله#اصفهان شماره خاله #شماره خاله# تهران #شماره خاله# اصفهانf #شما...
#world #cybersecurity #language #equality #parenting
Origin | Interest | Match
Betanet: The “Censorship-Free” Internet That Could Change the Web Forever Inside the Decentralized Network Built to Beat Government and Corporate Censorship Continue reading on InfoSec Write-up...
#programming #cybersecurity #technology #privacy #blockchain
Origin | Interest | Match

#EDGE, #Emerging #Technology, #Managed #Service #Providers
Origin | Interest | Match

Don’t scan QR codes on unsolicited packages delivered to your house, FBI warns The FBI is warning people of a new scam involving fake packages with a QR codes designed to steal data. The FBI is w...
#Colorado #News #Crime #and #Public #Safety #Latest […]
[Original post on denverpost.com]
Streamlining Infrastructure Upgrades with IT Procurement Services In today’s dynamic business environment, scaling and upgrading IT infrastructure is foundational to digital transformation and su...
#Industry #News
Origin | Interest | Match

#Business #Development #CRM #Internet #Marketing #Lead #Generation #Market #Research #Research #Sales
Origin | Interest | Match

Russia breaks through main Ukrainian defensive line ahead of Alaska meeting with Trump Russian troops achieved one of the biggest breakthroughs of the war in eastern Ukraine, with some units making...
#World #Russia #Russia-Ukraine #War #Ukraine […]
[Original post on washingtonexaminer.com]

Cyber info sharing act reauthorization expected by CISA leaders Infosecurity Magazine reports that Congress is expected by both Cybersecurity and Infrastructure Security Agency Acting Executive Ass...
#Malware #News
Origin | Interest | Match

Expanded US water system cyber services mulled by DEF CON initiative After initially providing free cybersecurity services to five water utilities in Indiana, Oregon, Utah, and Vermont, organizers ...
#Malware #News
Origin | Interest | Match

Restoration of MS-ISAC sought by groups Congressional appropriations committee leaders have been urged by the National Association of State Chief Information Officers, the National Association of C...
#Malware #News
Origin | Interest | Match

Identity security emerges as federal cyber priority CyberScoop reports that federal agencies are facing escalating cybersecurity risks as cloud adoption, AI integration, and hybrid work expand the ...
#Malware #News
Origin | Interest | Match

slab allows out-of-bounds access in `get_disjoint_mut` due to incorrect bound... slab is a pre-allocated storage for a uniform data type. In version 0.4.10, the get_disjoint_mut method incorrectly ...
Origin | Interest | Match

Vim heap use-after-free vulnerability when processing recursive tuple data ty... Vim is an open source, command line text editor. In versions from 9.1.1231 to before 9.1.1400, When processing neste...
Origin | Interest | Match

Vim double-free vulnerability during Vim9 script import operationsVim is an o... Vim is an open source, command line text editor. In versions from 9.1.1231 to before 9.1.1406, when processing neste...
Origin | Interest | Match

FSU Panama City showcases entrepreneurs at 'Pitch Day' event BAY COUNTY, Fla. (WMBB) - FSU Panama City hosted its version of Shark Tank on Monday. While there were no celebrity investors, e...
#Bay #County #Local #News #News
Origin | Interest | Match

Stirling-PDF SSRF vulnerability on /api/v1/convert/markdown/pdfStirling-PDF i... Stirling-PDF is a locally hosted web application that performs various operations on PDF files. Prior to version 1.1...
Origin | Interest | Match

PyLoad vulnerable to SQL Injection via API /json/add_package in add_links par... pyLoad is the free and open-source Download Manager written in pure Python. Prior to version 0.5.0b3.dev91, the para...
Origin | Interest | Match

Stirling-PDF SSRF vulnerability on /api/v1/convert/html/pdfStirling-PDF is a ... Stirling-PDF is a locally hosted web application that performs various operations on PDF files. Prior to version 1.1...
Origin | Interest | Match

Omnissa Secure Email Gateway (SEG) updates address Server-Side Request Forger... Server-Side Request Forgery (SSRF) in Omnissa Secure Email Gateway (SEG) in SEG prior to 2.32 running on Windows and...
Origin | Interest | Match
Digital identity theft is becoming more complicated Digital identity is becoming a common target for cybercriminals who are hacking their way into organizations or leaking identity credentials for ...
#Access #Control #Biometrics #News #Civil #/ […]
[Original post on biometricupdate.com]
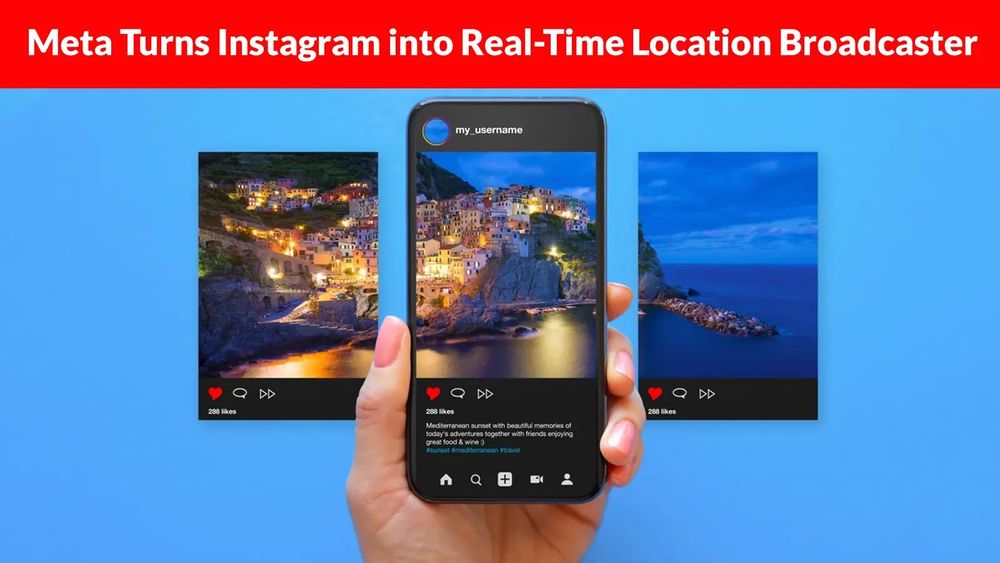
Meta’s New Feature Transforms Instagram to a New Real-Time Location Broadcaster Meta has introduced a groundbreaking feature that fundamentally transforms Instagram from a traditional photo-shari...
#Cyber #Security #News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match

#Enterprise #Tech #/enterprise-tech #Innovation #/innovation #Enterprise #Tech #/enterprise-tech #Cybersecurity #/cybersecurity #technology
Origin | Interest | Match

OpenKilda XXE in SAML configurationOpenKilda is an open-source OpenFlow contr... OpenKilda is an open-source OpenFlow controller. Prior to version 1.164.0, an XML external entity (XXE) injection vu...
Origin | Interest | Match
SonicWall pins firewall attack spree on year-old vulnerability The vendor ruled out a zero-day vulnerability as the root cause, disputing initial assessments from third-party researchers. Fewer tha...
#Cybercrime #Cybersecurity #Ransomware #Research #Threats […]
[Original post on cyberscoop.com]

Zed AI Agent Remote Code ExecutionZed is a multiplayer code editor. Prior to ... Zed is a multiplayer code editor. Prior to version 0.197.3, in the Zed Agent Panel allowed for an AI agent to achiev...
Origin | Interest | Match

Cybersecurity ‘red teams’ to UK government: AI is rubbish The UK Department for Science, Innovation and Technology is run by Peter Kyle MP, who knows nothing about science or technology and bra...
#Cryptocurrency
Origin | Interest | Match
UnitedHealth Group is Back in the Spotlight The UnitedHealth Group holds the record for the largest healthcare data breach in history. The 2024 data breach at Change Healthcare, a UHG subsidiary, a...
#HIPAA #News #Breach #Notification #HIPAA #Risk #Analysis #HIPAA #Risk #Management #Protected […]

DARPA eyes transition of AI Cyber Challenge tech to ‘widespread use’ After announcing the winners of its AI challenge, DARPA wants to help transition the technology into “real-world critical ...
#All #News #Artificial #Intelligence #Cybersecurity […]
[Original post on federalnewsnetwork.com]

CISA and FBI Joint Update on Scattered Spider: Evolving Threats and Mitigation Guidance The Cybersecurity & Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and int...
#Advisories #Cyber #Risk #Cybercrime #Cybersecurity #Ransomware
Origin | Interest | Match