YouTube video by Synacktiv
[Le Big Bang de l’Économie - Le Figaro] Cybersécurité : sommes-nous vraiment prêts ?
🇫🇷 During "Le Big Bang de l’Économie" by #LeFigaro, @kevintell.bsky.social gave a live pentest demo, showing how easily data can be exposed when systems aren’t properly secured: youtu.be/XVJUF1zt1FE
👉 Watch the whole show: video.lefigaro.fr/figaro/econo...
06.11.2025 14:56 — 👍 2 🔁 2 💬 0 📌 0

Catching Credential Guard Off Guard - SpecterOps
Uncovering the protection mechanisms provided by modern Windows security features and identifying new methods for credential dumping.
Credential Guard was supposed to end credential dumping. It didn't.
Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm
23.10.2025 17:45 — 👍 17 🔁 11 💬 0 📌 0

The Phantom Extension: Backdooring chrome through uncharted pathways
The Phantom Extension: Backdooring chrome through uncharted pathways
How safe is your browser?
Our ninja, Riadh Bouchahoua, uncovers how attackers can exploit Chromium extension loading to steal data, maintain persistent access, and breach confidentiality on Chromium-based browsers.
Read more here ⬇️
www.synacktiv.com/en/publicati...
26.09.2025 10:29 — 👍 3 🔁 2 💬 0 📌 0

DCOM Again: Installing Trouble - SpecterOps
DCOM lateral movement BOF using Windows Installer (MSI) Custom Action Server - install ODBC drivers to load and execute DLLs
Lateral movement getting blocked by traditional methods?
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
29.09.2025 19:00 — 👍 9 🔁 3 💬 0 📌 0


🧑🎓 Boost your offensive Active Directory skills with our Entry & Advanced trainings. Hands-on labs with dozens of machines + latest research from DEFCON, x33fcon & more! Seats are limited, don’t miss out!
🔗 Entry: www.synacktiv.com/en/offers/tr...
🔗 Advanced: www.synacktiv.com/en/offers/tr...
12.09.2025 11:13 — 👍 4 🔁 2 💬 0 📌 0

DCOM is everywhere, but its inner workings feel like black magic. 🪄 Unveil the mystery with @kevintell.bsky.social's new article on DCOM basics. Trust us, it's way cooler than it sounds!
www.synacktiv.com/en/publicati...
16.09.2025 13:12 — 👍 8 🔁 3 💬 0 📌 0

Should you trust your zero trust? Bypassing Zscaler posture checks
Introduction Posture checks are a key component of zero trust architectures.
🔒 Can you really trust your zero trust? We (re)discovered a vulnerability in Zscaler Client Connector that allowed bypassing device posture checks, and it was still exploitable in the wild. Full technical deep dive + remediation tips 👉 www.synacktiv.com/en/publicati...
08.08.2025 12:56 — 👍 5 🔁 4 💬 0 📌 0

🚨 Still a few days to register for our Azure Intrusion for Red Teamers training at #BHUSA! Very hands-on, full kill chain from zero to Global Admin with stealth in mind. Secure your seat now! www.blackhat.com/us-25/traini...
02.07.2025 09:26 — 👍 5 🔁 6 💬 0 📌 0
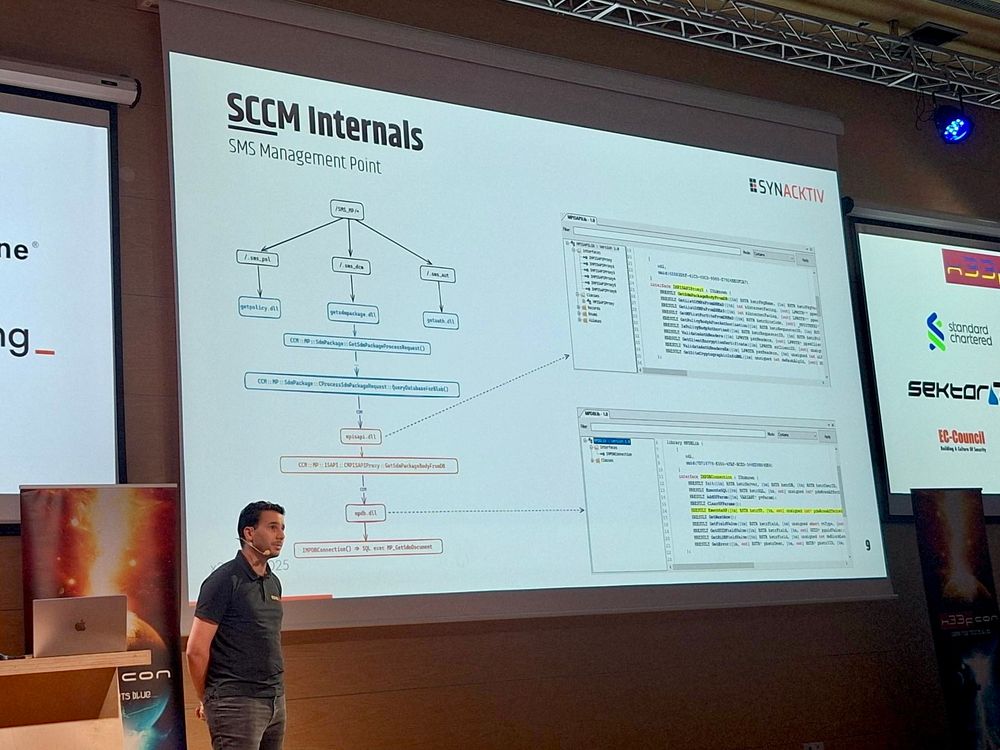
Our ninja @kalimer0x00.bsky.social is now on stage at #x33fcon to talk about his journey from dissecting SCCM until the discovery of the critical CVE-2024-43468 and the post-exploitation opportunities🔥
13.06.2025 14:46 — 👍 8 🔁 6 💬 0 📌 0

Azure intrusion for red teamers
by Paul Barbé & Matthieu Barjole
www.hexacon.fr/trainer/barb...
15.04.2025 14:46 — 👍 8 🔁 8 💬 0 📌 1
Responsable équipe reverse engineering
Synacktiv is looking for an additional team leader in Paris for its Reverse-Engineering Team!
Find out if you are a good candidate by reading our offer (🇫🇷).
www.synacktiv.com/responsable-...
28.03.2025 16:25 — 👍 7 🔁 6 💬 0 📌 0
It's great ! But would you consider a local alternative as sending customer data to a third party service during engagement is a big turn off for me
29.03.2025 09:44 — 👍 0 🔁 0 💬 1 📌 0
I had the privilege to attend this training at Synacktiv and it might be the best training you can get when it comes to Azure given by two guy who does Red Team all year round on this subject. Don't wait !
21.03.2025 18:03 — 👍 0 🔁 1 💬 0 📌 0
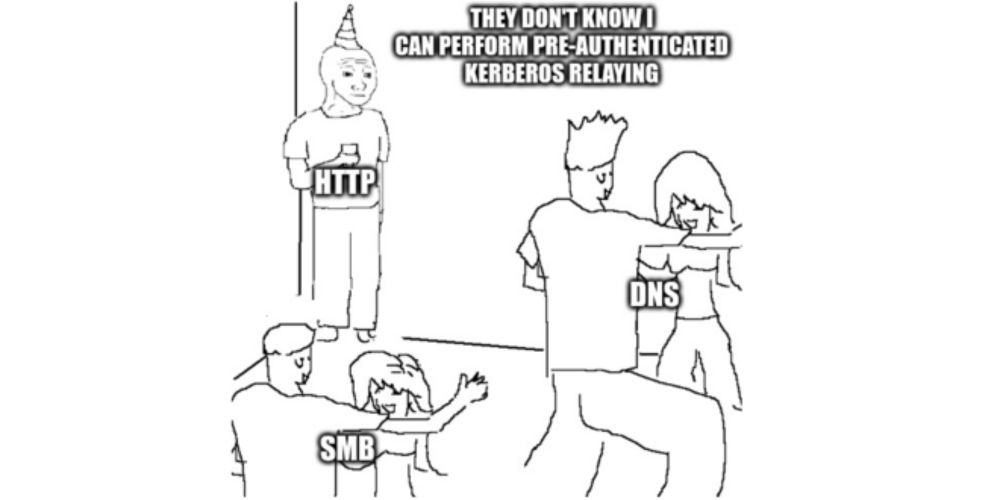
Abusing multicast poisoning for pre-authenticated Kerberos relay over HTTP with Responder and krbrelayx
In our latest article, @croco_byte proposes an implementation of a trick discovered by James Forshaw in his research regarding Kerberos relaying. Discover how to perform pre-authenticated Kerberos relay over HTTP with our Responder and krbrelayx pull requests!
www.synacktiv.com/publications...
27.01.2025 12:06 — 👍 16 🔁 12 💬 0 📌 1
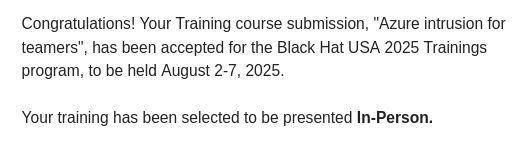
Yay! Our offensive Azure training was accepted at BlackHat USA 2025 🥳 Can't wait to see you there and share cutting-edge techniques for attacking Azure environments!
20.01.2025 09:24 — 👍 9 🔁 7 💬 0 📌 0
GreyNoise analyzes Internet background noise. Use GreyNoise to remove pointless security alerts, find compromised devices, or identify emerging threats.
Red Team / Security researcher at @synacktiv.com
linktr.ee/rustyphasm
Security Researcher @ Datadog. 🐶 Head in the (Azure) clouds.
Sometimes blogging, always curious. Aim to be, rather than to seem.
Blogs at https://kknowl.es.
Reverse engineer @synacktiv.com. I appreciate Android related stuff
VR team tech lead @synacktiv.com
Security expert @Synacktiv
Security enthusiast: RE, VR, exploits and stuff
VR @ Synacktiv, low level security enthusiast
https://voydstack.re/
About me?
| Website: https://mizu.re
| Tool: https://github.com/kevin-mizu/domloggerpp
| Teams: @rhackgondins, @FlatNetworkOrg, @ECSC_TeamFrance
| From: https://twitter.com/kevin_mizu
Security researcher @Synacktiv.com ⛩️
#RE #Pwn #FPV ~ Learning is endless ~ 🇫🇷 ~ @Synacktiv.com
![[Le Big Bang de l’Économie - Le Figaro] Cybersécurité : sommes-nous vraiment prêts ?](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:f66ty74va5ti7faiq5ezuncy/bafkreihnldzcpa25lkatr57j4e32fpszpg5d3asqro4ra7blpixegrnbse@jpeg)