CastleLoader in the wild! Four distinct activity clusters, sector-specific targeting of logistics, and high-end tooling like Matanbuchus and CastleRAT.
09.12.2025 15:43 — 👍 3 🔁 2 💬 0 📌 0

Recorded Future’s Insikt Group uncovered four GrayBravo activity clusters. TAG-160 impersonates logistics firms, while TAG-161 impersonates Booking.com, employing ClickFix to deliver CastleLoader and Matanbuchus. www.recordedfuture.com/research/gra...
09.12.2025 11:25 — 👍 6 🔁 5 💬 0 📌 0

2/ Our latest analysis uncovered four distinct activity clusters within GrayBravo’s ecosystem, all leveraging the group’s #CastleLoader malware. Each cluster uses different tactics, techniques, and targets, reinforcing the assessment that GrayBravo runs a #MaaS model.
09.12.2025 08:24 — 👍 3 🔁 1 💬 1 📌 0

GrayBravo’s CastleLoader Activity Clusters Target Multiple Industries
1/ @whoisnt.bsky.social, Marius, and I just published a report on #GrayBravo (formerly TAG-150), a highly adaptive, sophisticated threat actor that we first identified in Sept 2025. It uses a multi-layered infrastructure and responds quickly to exposure: www.recordedfuture.com/research/gra...
09.12.2025 08:24 — 👍 10 🔁 6 💬 1 📌 1
A good piece highlighting the EU's continued inaction following recent sanctions, essentially allowing these enablers to continue their operations.
05.12.2025 19:35 — 👍 1 🔁 0 💬 0 📌 0

🚨 - New report by Haaretz, Inside Story, Inside-IT and Amnesty International release the Intellexa Leaks. Which exposes Intellexa support staff had access through Teamviewer to customer deployments and confirms found IOC's in the past by civil society. 🧵👇
04.12.2025 11:37 — 👍 9 🔁 16 💬 1 📌 3

Intellexa’s Global Corporate Web
1/ Today we release a new report exposing previously undisclosed entities connected to the wider #Intellexa ecosystem as well as newly identified activity clusters in Iraq and indications of activity in Pakistan: www.recordedfuture.com/research/int...
04.12.2025 04:17 — 👍 26 🔁 18 💬 2 📌 4
3/ As long as the same LIRs and the same bad actors are able to maintain control of their RIPE resources, the problem will never stop.
26.11.2025 14:12 — 👍 0 🔁 0 💬 0 📌 0

2/ The case of fraud relating to metaspinner GmbH really does spell out the severity of the problem...
26.11.2025 14:11 — 👍 0 🔁 0 💬 1 📌 0

‘Neutral’ internet governance enables sanctions evasion
Internet service providers and hosting companies enable cybercrime and cyber operations. Why don’t sanctions stop them?
1/ It's nice to see the topic of bulletproof hosters and Threat Activity Enablers gaining more mainstream attention; however, a bigger problem than endless shell companies exists, and that is RIPE RIR policy. bindinghook.com/neutral-inte...
26.11.2025 14:11 — 👍 2 🔁 1 💬 1 📌 1
NSA Joins CISA and Others to Release Guidance on Mitigating Malicious Activity from Bulletproof Hosting Provider Infrastructure
November 19, 2025, NSA/CSS
www.nsa.gov/Press-Room/P...
20.11.2025 12:03 — 👍 4 🔁 3 💬 1 📌 0
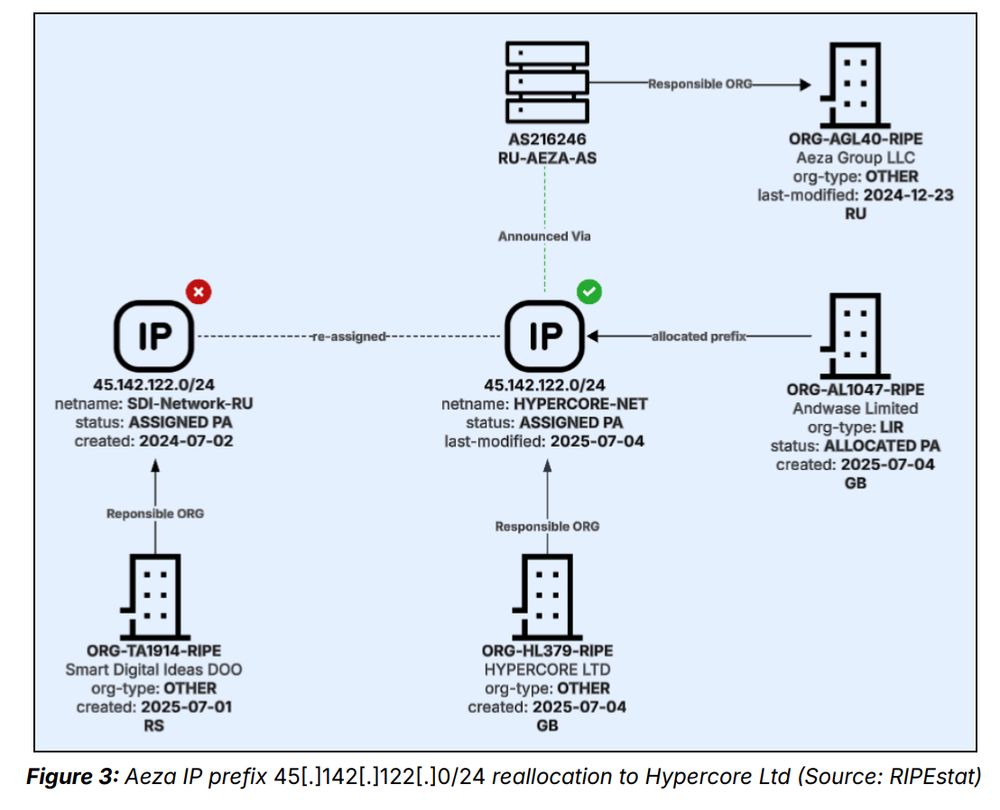

3/
19.11.2025 17:19 — 👍 2 🔁 0 💬 0 📌 0
1/ United States, Australia, and United Kingdom sanction Russian threat activity enabler Media Land (Yalishanda) and follow up on recent designations targeting Aeza. ofac.treasury.gov/recent-actio...
19.11.2025 17:17 — 👍 3 🔁 3 💬 1 📌 0
This is highly likely CrazyRDP :)
16.11.2025 19:58 — 👍 2 🔁 0 💬 0 📌 0
3/ metaspinner net GmbH (Hamburg, Germany) has no affiliation with #AS209800, Virtualine Technologies, or any related malicious activity associated with that network.
12.11.2025 21:52 — 👍 0 🔁 0 💬 0 📌 0
2/ A falsified RIPE end-user agreement provided to Insikt Group highlights how a basic verification check against publicly accessible company registration documents could have prevented the fraudulent registration.
12.11.2025 21:52 — 👍 0 🔁 0 💬 1 📌 0
1/ [UPDATE] As of November 10, 2025, metaspinner net GmbH has provided substantial evidence confirming Insikt Group’s original assessment that their identity was unlawfully and fraudulently used in the registration of #AS209800.
12.11.2025 21:51 — 👍 2 🔁 1 💬 1 📌 0
Malicious Infrastructure Finds Stability with aurologic GmbH
Malicious Infrastructure Finds Stability with aurologic GmbH
07.11.2025 11:24 — 👍 1 🔁 1 💬 0 📌 0

German ISP Aurologic GmbH has Become a Central Nexus for Hosting Malicious Infrastructure
German ISP Aurologic GmbH has Become a Central Nexus for Hosting Malicious Infrastructure
08.11.2025 00:41 — 👍 2 🔁 3 💬 0 📌 0

9/Aeza Group continues to rely on aurologic for a large share of its connectivity, announcing roughly half of its IP space, despite recent sanctions by the US and the UK.
06.11.2025 11:33 — 👍 4 🔁 0 💬 1 📌 0
Threat Research @ Recorded Future
Investigative journalist @investigacecz.bsky.social
Přinášíme investigativní kauzy o organizovaném zločinu a jeho dopadech na Českou a Slovenskou republiku. Píšeme o praní peněz, mafii i korupci. | Členové OCCRP a VSquare Project
🔎 Investigating Central Europe | We are a non-profit investigative journalism platform: https://vsquare.org
Support us: https://vsquare.org/donate/
KC8RNV - Tech engineer and aesthetic nomad. Intolerant of fascism and nihilism. Listener of crows. Driven by literature, tangled in philosophy, and fractured by everything beautiful.
News, tech, cybercrime, Russia
You have precious little privacy in this global networked world; don't throw it away for a few clicks and likes.
Your weekly go-to cybersecurity newsletter, curated and commented on by our senior analysts, in your mailbox soon...
https://x.com/IntCyberDigest
https://infosec.exchange/@InternationalCyberDigest
I do threat intel things. Former Activision Blizzard // Epic Games. Currently putting the G in 5G. Kinda passionate and extremely okay. Opinions are my own. He/him/#FSD 🦆
IT Security / Cyber Security: Aktuelle Infos, Fachbeiträge, Studien, Video-Podcasts, News weltweit etc.
Infosec lurker. Occasional poster. Mostly blog stuff.
https://mattysplo.it
editor @bindinghook.bsky.social / freelance editor & writer (oxford analytica, brill yearbook of muslims in europe 2022-present, eater, eurasianet, oc media, saveur, the moscow times, etc)
based in oegstgeest
also: birds, bikes, georgian, snacks, trains
Critical Infrastructure | Threat Research | Intelligence Analysis
Bridging the gap between org objectives and technical security.
Always learning, always collaborating.
#InfoSec #CyberSecurity #ThreatIntel
Virtual Routes tackles the impact of digital and emerging technologies on global affairs. Also check out @bindinghook.bsky.social, our media outlet.
Reverse Engineering and Malware Analysis
Technologies, Defense, Electro, Boardgames & e-Sport ! Add some humour and a touch of cynism
Independent EU-focused NGO whose mission is to raise awareness on #disinformation & contribute to a better information landscape.
journalist on correctiv’s fact-checking teamㅣDowJones & WSJ alumㅣprevious work Lighthouse Reports, DW, Guardian, Wired and othersㅣOSINT, disinformation
DFIR - Guy that never sleeps 🔍


















