Dangerous Invitations: Russian Threat Actor Spoofs European Security Events in Targeted Phishing Attacks
In early 2025, Volexity published two blog posts detailing a new trend among Russian threat actors targeting organizations through the abuse of Microsoft 365 OAuth and Device Code authentication workf...
@volexity.com tracks a variety of threat actors abusing Device Code & OAuth authentication workflows to phish credentials, which continue to see success due to creative social engineering. Our latest blog post details Russian threat actor UTA0355’s campaigns impersonating European security events.
04.12.2025 18:36 —
👍 10
🔁 8
💬 0
📌 0

Earth Estries and Earth Naga malware links

List of Earth Estries and Earth Naga targets, classified by targeted industry and location

Collaboration types and the related MITRE tactic stage where such collaboration occurs

Earth Estries and Earth Naga malware toolkits
We saw Earth Estries, an advanced #APT intrusion set, sharing its access to Earth Naga (Flax Typhoon). We introduce the term "Premier Pass" to describe this behavior, and propose a four-tier classification framework for collaboration types among advanced groups www.trendmicro.com/en_us/resear...
22.10.2025 09:18 —
👍 20
🔁 14
💬 2
📌 1

APT Meets GPT: Targeted Operations with Untamed LLMs
Starting in June 2025, Volexity detected a series of spear phishing campaigns targeting several customers and their users in North America, Asia, and Europe. The initial observed campaigns were tailor...
APT meets GPT: @volexity.com #threatintel is tracking #threatactor UTA0388's spear phishing campaigns against targets in North America, Europe & Asia, appearing to use LLMs to assist their ops. Letting #AI run your espionage operations? What could go wrong?
08.10.2025 12:35 —
👍 3
🔁 3
💬 0
📌 0
📣 Oops!... They did it again!!!
61 Talks submitted and so many too good that, once again, we had to increase a bit the number of accepted talks.🔥
#PIVOTcon25 Agenda is finally here, and the caliber is insane!!! Check it out➡️ pivotcon.org/agenda-2025/
#CTI #ThreatIntel
Talks and presenters in🧵⬇️ 1/18
07.03.2025 14:42 —
👍 20
🔁 14
💬 1
📌 5

"Edge Devices Investigation"
Paul Rascagneres, Principal Threat Researcher, Volexity (@r00tbsd , @r00tbsd.bsky.social , @r00tbsd@infosec.exchange)
5/18
07.03.2025 14:42 —
👍 8
🔁 3
💬 1
📌 0
This talk is a great way to watch/listen to the details behind the work @stevenadair.bsky.social, @5ck.bsky.social, @tlansec.bsky.social + Volexity’s #threatintel & IR teams did to investigate the Nearest Neighbor Attack. The related blog post is here: www.volexity.com/blog/2024/11...
13.12.2024 13:58 —
👍 8
🔁 6
💬 0
📌 0
We were happy to have @volexity.com's @stevenadair.bsky.social & @5ck.bsky.social present “The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access” for the #FTSCon Keynote in October. The video of their talk is available here: youtu.be/qSNlDCg-IOM.
#dfir
13.12.2024 13:38 —
👍 9
🔁 6
💬 0
📌 2
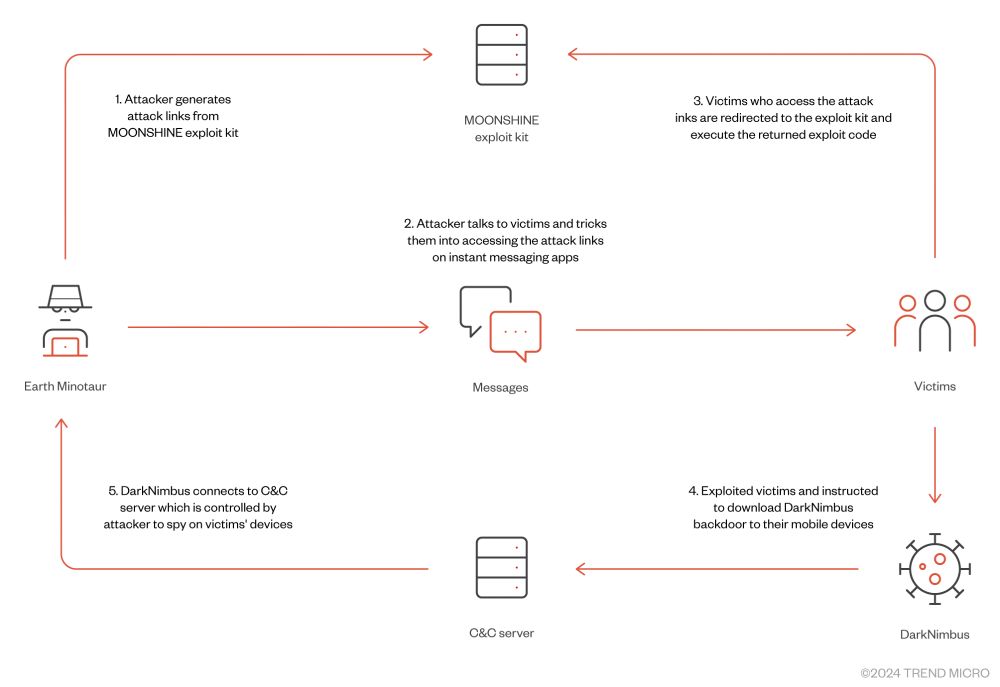
Attack chain showing attacker generating link on Moonshine, then sending it through targeted application to the victim, which after clicking the links gets compromised and delivered the DarkNimbus backdoor
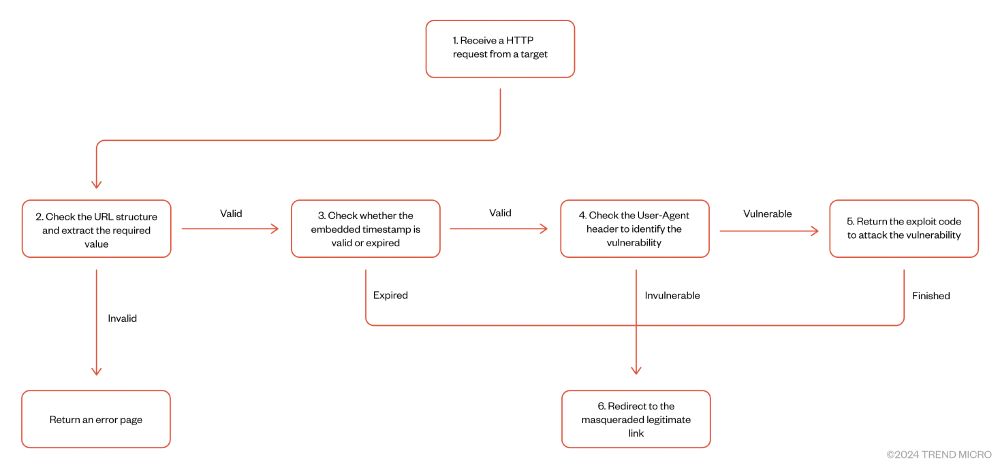
Validation flow that fingerprints the target by looking at user agent and delivering the proper exploit
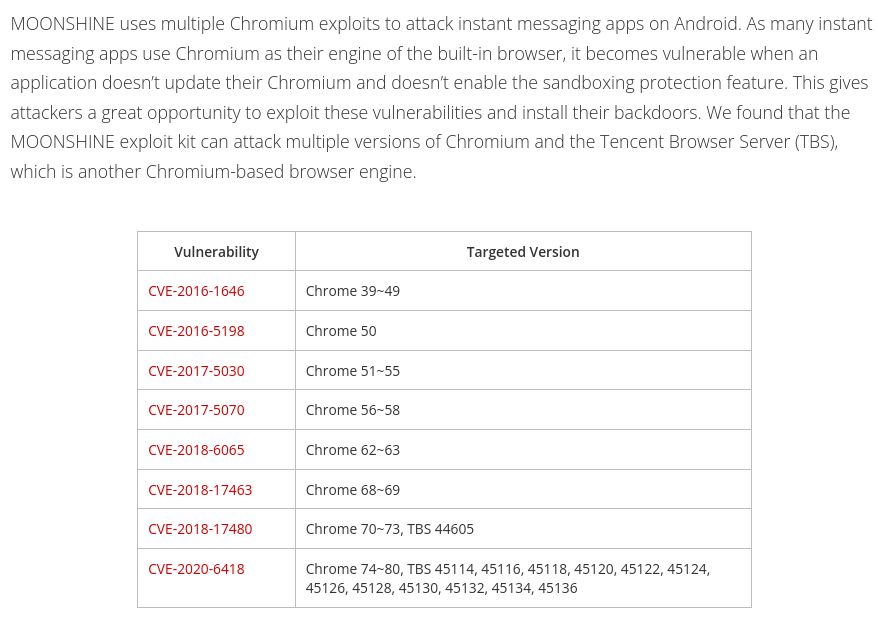
multiple Chrome vulnerabilities exploited in the third-party applications
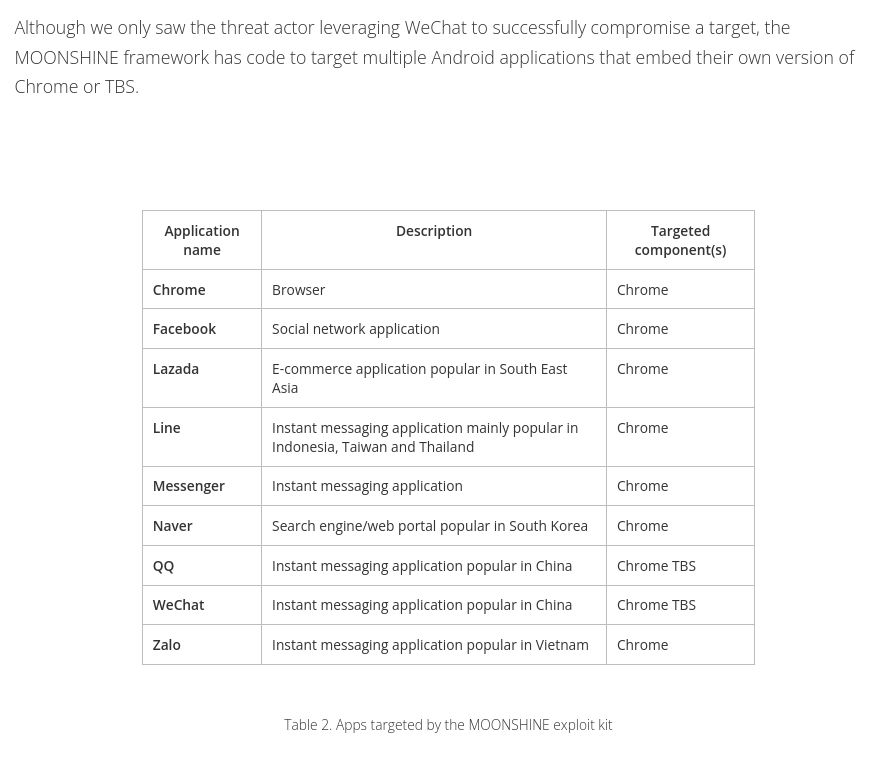
List of Android applications being targeted
Most are very popular in South East Asia
Our latest report presents Earth Minotaur, a threat actor targeting Tibetans and Uyghurs using Moonshine, an exploitation framework for Android apps described in 2019 by
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
05.12.2024 08:48 —
👍 12
🔁 7
💬 0
📌 2

#PIVOTcon25 #CfP is open and you can submit your proposals till 7 FEB 2025
Remember
- one track,30m
- no recording/streaming/tweeting. U should feel comfy to share more
- No TLP:WHITE
- Original content only
Let us guide u through with a little meme-thread
#CTI #ThreatIntel 1/10
27.11.2024 15:11 —
👍 31
🔁 18
💬 1
📌 4
GitHub - volexity/hwp-extract: A library and cli tool to extract HWP files.
A library and cli tool to extract HWP files. Contribute to volexity/hwp-extract development by creating an account on GitHub.
@Volexity.com has developed a new open-source tool, “HWP Extract”, a lightweight Python library & CLI for interacting with Hangul Word Processor files. It also supports object extraction from password-protected HWP files. Download here: github.com/volexity/hwp...
27.11.2024 11:53 —
👍 12
🔁 6
💬 0
📌 0

two men are standing next to each other with the words " we open it up " on the screen
ALT: two men are standing next to each other with the words " we open it up " on the screen
#PIVOTcon25 registration is now OPEN 🤟📥📥📥
pivotcon.org
#CTI #ThreatResearch #ThreatIntel
Please read carefully the whole 🧵 for the rules about invite -> registration (1/5)
19.11.2024 14:00 —
👍 42
🔁 22
💬 2
📌 11
Let’s try here and see how it goes ;)
24.11.2024 20:29 —
👍 3
🔁 0
💬 0
📌 0