the site has come back up, and vulnerabilities that used to be fixed are now no longer fixed for some reason so there's even more ways to steal twexit accs now compared to when he shut the site down
12.08.2024 20:17 — 👍 6 🔁 0 💬 1 📌 0
i found multiple xss bugs just about daily (so i could steal the twexit cookies of anyone who clicked on the twexit link i had a spambot post), and then retr0id (and later me) found some sql injection bugs and adrianus shut the site down
12.08.2024 20:15 — 👍 5 🔁 0 💬 2 📌 0
oh wow, twexit's back, i sure hope adrianus has done literally anything to improve his website's security
12.08.2024 19:36 — 👍 6 🔁 0 💬 1 📌 1

This virtual session is intended for McDonald's Employees, Market Staff and Suppliers. If you were not invited, please disconnect now.
08.06.2024 21:25 — 👍 0 🔁 0 💬 1 📌 0
Pro tip: you can send messages from banned accounts, and people will still receive it (although the message is only visible in the preview)
26.05.2024 09:29 — 👍 1 🔁 0 💬 0 📌 0
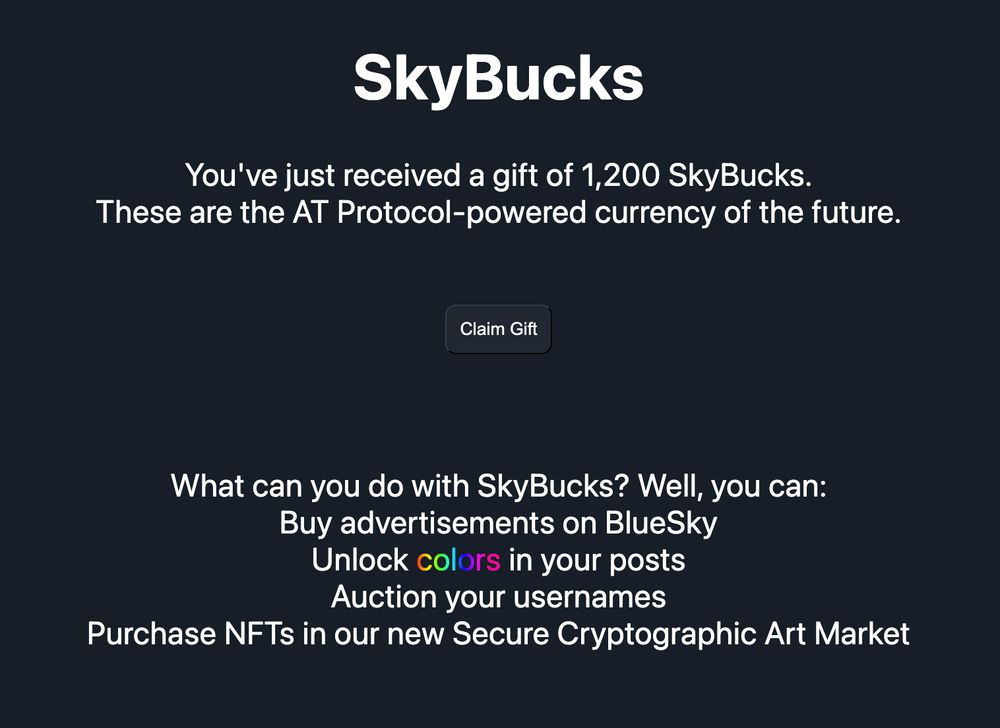
SkyBucksというスパムDMが一部で横行しているようです。コードのコメントを見る限りイタズラっぽいんですが、リンク先には飛ばないようにしましょう(キーストロークなどもトラッキングされているようなのでアカパスとか入力しちゃダメ)。ちなみにClaim Giftすると「Blueskyに広告を出稿したりポストに色を付けられる」らしいです。すごいね
26.05.2024 01:24 — 👍 146 🔁 231 💬 0 📌 5

Here's a screenshot of BitView's admin panel.
09.03.2024 21:05 — 👍 3 🔁 0 💬 3 📌 0
Skyname is back online.
Please read below for a detailed postmortem of the incident:
darn.blog/2024-01-14-s...
16.01.2024 03:12 — 👍 20 🔁 7 💬 0 📌 1
Skyname experienced a brief incident today where a malicious third party was able to overwrite DNS records pointing to registered usernames.
All usernames have been successfully restored, and you should expect to see yours update in 24-48 hours if you're still seeing Invalid Handle.
14.01.2024 23:35 — 👍 11 🔁 1 💬 1 📌 1

A log output showing various usernames on skyna.me being redirected to richardwrites672.bsky.social.

The skyname web portal, showing richardwrites672.bsky.social having 846 usernames linked to the account.
I now control every skyname handle :)
(Well, every skyname handle that has appeared in plc.directory/export )
14.01.2024 20:31 — 👍 3 🔁 1 💬 0 📌 0

mayhaps
14.01.2024 20:04 — 👍 0 🔁 0 💬 1 📌 0
 28.12.2023 06:14 — 👍 0 🔁 0 💬 0 📌 0
28.12.2023 06:14 — 👍 0 🔁 0 💬 0 📌 0
@twexit.nl @adrianus.twexit.nl Check your twitter DMs
28.12.2023 06:04 — 👍 0 🔁 0 💬 1 📌 0

The database for the Adrianus site RealTopTweeps.com (and also twintov.com)

The database for the Adrianus site yalphax.com

The database for the Adrianus site simplegymtracker.com

The database for the Adrianus site twuizzle.com (and also worldtoptweets.com)
By the way, this isn't just twexit and mastochist. Every single website that Adrianus has ever made is vulnerable to SQLi.
26.12.2023 07:25 — 👍 49 🔁 9 💬 4 📌 5

It is an adrianus project, yes. The domains (mastochist.com and mastochist.nl ) don't resolve but you can still access it by setting an /etc/hosts entry with the IP of the twexit server.
26.12.2023 06:02 — 👍 15 🔁 0 💬 0 📌 0



 25.12.2023 21:40 — 👍 10 🔁 0 💬 2 📌 0
25.12.2023 21:40 — 👍 10 🔁 0 💬 2 📌 0
Merry christmas.
mastodon.nl/@adrianus/11...
archive.is/kwqQB
25.12.2023 20:56 — 👍 4 🔁 0 💬 0 📌 0
To make my point clearer:
If I had just reported the bugs to you, nothing would have changed. There would be more bugs to take their place, and people who didn't want to make it as public as I did would have taken advantage of them. It's likely some already have.
Instead, your websites are down.
25.12.2023 01:06 — 👍 4 🔁 1 💬 0 📌 0
Because given your other posts about how having common bugs in your app "ruined your reputation", I doubt it.
Do you think no one took advantage of the SQL injection vulnerabilities present in your older project Twopcharts? Because I heavily doubt that as well.
25.12.2023 00:42 — 👍 5 🔁 0 💬 1 📌 0
I've never tried to frame my actions as being "absolutely fine" and I'm not sure why you're attempting to say that.
I do want to ask you: If I had just privately reported the issues to you, would you have made people aware that their information was at risk from using your service?
25.12.2023 00:41 — 👍 5 🔁 0 💬 1 📌 0
Emails and bluesky login tokens were out in the open though, which absolutely is a real concern.
24.12.2023 19:20 — 👍 17 🔁 0 💬 2 📌 0
There it is. Seems like twexit is actually dead now-- no page is working anymore.
twexit.nl
archive.is/LJnFd
(For clarity's sake-- I am not the one that put the image on the website. That seems to have been the action of the actual admin of the site.)
22.12.2023 15:24 — 👍 7 🔁 0 💬 0 📌 1

Bingo.
22.12.2023 14:55 — 👍 2 🔁 0 💬 0 📌 0
The main issue with this one is that it's injection into an order by/limit query, and the only exploitation strategy I could find for it was very restrictive and seemingly didn't allow for select statements.
I've found a (potentially) better sqli method that I'm still investigating though.
22.12.2023 14:46 — 👍 1 🔁 0 💬 0 📌 0
Finally, here's XSS in twexit post-shutdown
6v.pages.dev/final
:)
22.12.2023 13:29 — 👍 1 🔁 0 💬 0 📌 0
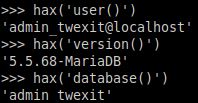
Alright, looking into it more it seems the sql injection bug I found isn't actually exploitable in terms of getting database contents, just calling some functions. Could be wrong, though.
If anyone else wants to give it a try:
POST twexit.nl/js_output_te...
w/ data first=0(sql here)
22.12.2023 12:16 — 👍 3 🔁 0 💬 1 📌 1
I think your website has some sort of bug in it.
22.12.2023 11:07 — 👍 2 🔁 0 💬 0 📌 0
database() like 'admin_twexit'
(this bug is very annoying to exploit)
22.12.2023 11:00 — 👍 1 🔁 0 💬 0 📌 0
not particularly, no :)
22.12.2023 10:59 — 👍 1 🔁 0 💬 0 📌 0






 28.12.2023 06:14 — 👍 0 🔁 0 💬 0 📌 0
28.12.2023 06:14 — 👍 0 🔁 0 💬 0 📌 0








 25.12.2023 21:40 — 👍 10 🔁 0 💬 2 📌 0
25.12.2023 21:40 — 👍 10 🔁 0 💬 2 📌 0

