Have you installed Microsoft.Graph.Authentication 2.27.0? Could you run Get-MgUser or Get-MgGroup now?
#PowerShell
Peter Lorenzen
@theheatdk.bsky.social
Azure cloud architect from Denmark
@theheatdk.bsky.social
Azure cloud architect from Denmark
Have you installed Microsoft.Graph.Authentication 2.27.0? Could you run Get-MgUser or Get-MgGroup now?
#PowerShell

We finally have some news. PowerShell 7.4 support is schedule for June 15 - github.com/PowerShell/P...
19.04.2025 11:59 — 👍 0 🔁 0 💬 2 📌 0I assume Policy.Read.ApplicationConfiguration is the reason.
The not supported for Delegated (work or school account) confuses me? :-)

learn.microsoft.com/en-us/powers...
14.03.2025 10:11 — 👍 0 🔁 0 💬 1 📌 0Application Administrator or Cloud Application Administrator...
14.03.2025 09:55 — 👍 0 🔁 0 💬 1 📌 0merill.net - After using Update-MgPolicyDefaultAppManagementPolicy on 6 tenants multiple times my conclusion is that the documentation is wrong :-)
You need Security Administrator + Application Administrator for it to work. If you only have Security Administrator you get an 403 error.
Ok. Thanks for answering :-)
08.03.2025 14:42 — 👍 0 🔁 0 💬 0 📌 0Sorry I missed the blue box :-( Thanks for answering!
06.03.2025 20:34 — 👍 1 🔁 0 💬 1 📌 0Thanks, @merill.net - Is the Global Admin role required to update the tenant app management policy, or will some other role suffice?
05.03.2025 22:15 — 👍 0 🔁 0 💬 1 📌 0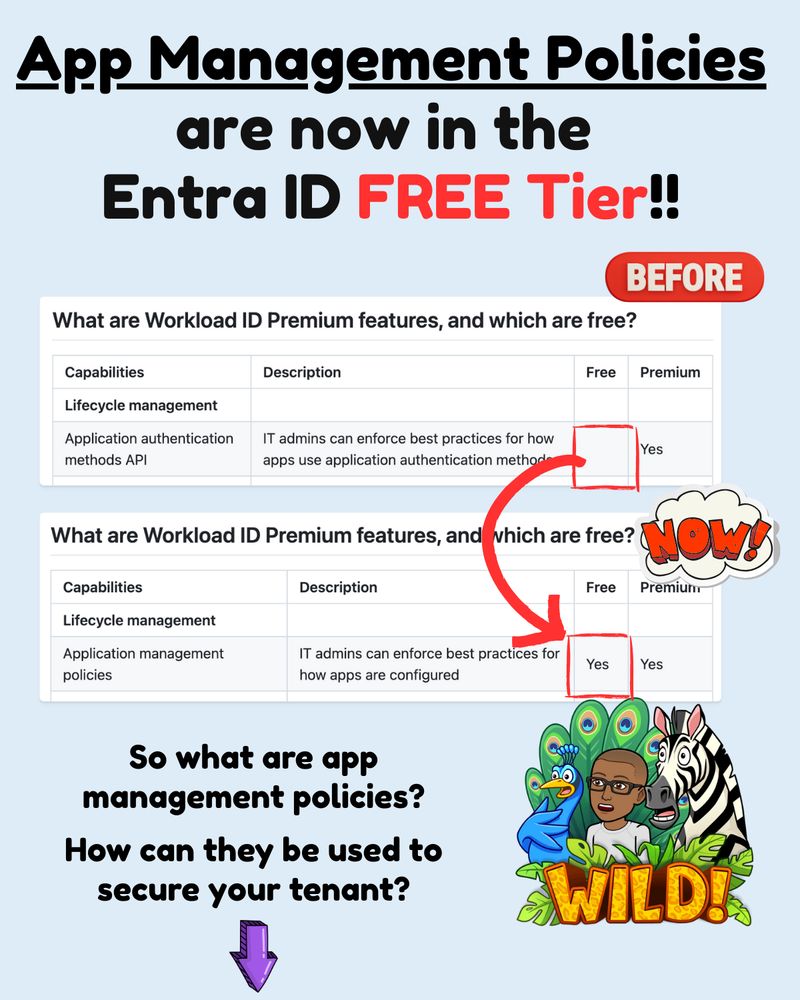
App Management Policies are now in the Entra ID FREE Tier!! So what are app management policies? How can they be used to secure your tenant?
This doesn't happen everyday folks!!
Entra ID application management policies no longer require a Workload ID Premium license! 👏🎁🍾🥳🎊
This change happened back in October last year and I somehow missed it.
Here's a complete walkthrough 🧵👇
✳️ Bookmark this.
Congrats. Any tips for good prep material?
02.03.2025 15:43 — 👍 0 🔁 0 💬 1 📌 0CC: @alexandair.bsky.social, @jeftek.com
03.12.2024 15:04 — 👍 0 🔁 0 💬 0 📌 0Ok. Thanks for taking time to answer 👍
16.11.2024 05:58 — 👍 0 🔁 0 💬 0 📌 0I get that it is possible to steal tokens so if the role is active for 1 hour and somebody steals the MFA tokens they have one hour with access but that is the same for cloud only account.
We have a lot of discussions around this a the moment, so I would very much like to understand it! :-)
Sorry if I am a little dense :-) Users are in AD. In Entra they have MFA configured. The PIM setting require them to sign-in and use MFA when a role is activated. If they are compromised on-prem only their password is compromised not their MFA method. So how can anybody get around the MFA policy?
15.11.2024 21:16 — 👍 0 🔁 0 💬 1 📌 0Hi Jef,
I am surprised about this. If you on PIM role activation require reauthentication via CA authentication context so users has to do sign-in + MFA every time they activate a privilege Entra role, why is it still a non-no to use synced users?
Starter pack
12.11.2024 15:20 — 👍 2 🔁 0 💬 0 📌 0