
CVE-2025-11371 - Overview, Insights & Trends
Get the latest on CVE-2025-11371, including risk score and recommendations. Vulnerability intelligence on trending CVEs from multiple sources.
CVE-2025-11371 might score 6.2 (Medium) - but it’s anything but medium risk.
It lets attackers steal machine keys & access system files, leading to RCE. Exploitation has already been seen in the wild.
Get the full analysis: cvemon.intruder.io/cves/CVE-202...
13.10.2025 15:06 — 👍 0 🔁 0 💬 0 📌 0
GregAI: Your Intruder AI Security Analyst
We’re excited to introduce GregAI, your AI security analyst copilot that streamlines security workflows by prioritizing issues, validating findings, and more.
Meet GregAI - your new #AI security analyst copilot. 🤖
With knowledge of your entire Intruder account, he helps you validate and prioritize issues, remediate with confidence, create clear stakeholder updates, and more.
Learn more: www.intruder.io/blog/greg-ai...
30.07.2025 15:30 — 👍 0 🔁 0 💬 0 📌 0
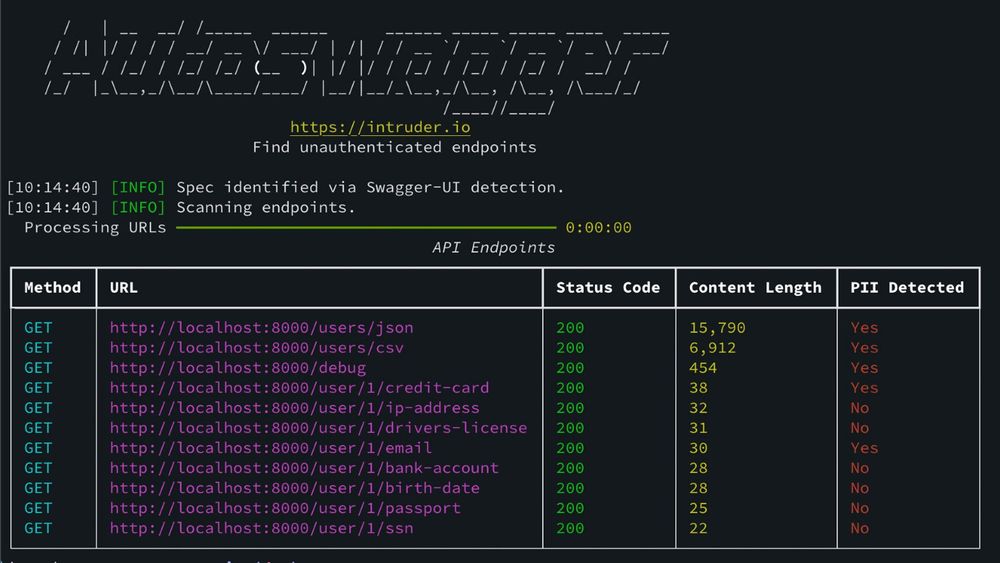
Broken API authorization is still exposing sensitive data - so we built a free tool to find it.⚡
Available on GitHub, Autoswagger is our free, open‑source tool that finds unauthenticated #APIs leaking sensitive data like credentials or PII.
Learn more: www.intruder.io/research/bro...
#APISecurity
25.07.2025 15:00 — 👍 1 🔁 1 💬 0 📌 0

A critical RCE vulnerability in on-prem #Microsoft #SharePoint (CVE-2025-53770) is being actively exploited.
Intruder is the first VM solution we’re aware of to release an active check.
👉 Start a free trial to detect vulnerable SharePoint instances: portal.intruder.io/free_trial
22.07.2025 14:02 — 👍 0 🔁 0 💬 0 📌 0

#GladinetCentreStack users - you can now check for CVE-2025-30406 with Intruder ✔️
Our active check is live, so you can find out fast if you're at risk.
👉 Sign up for free to scan your environment today: portal.intruder.io/free_trial
15.04.2025 17:02 — 👍 0 🔁 0 💬 0 📌 0

CVE-2025-30406 is a critical (CVSS 9.8) #vulnerability in #GladinetCentreStack.
The issue is caused by the installer using hardcoded values for the validation and decryption key.
Get the latest from our security team: intel.intruder.io/cves/CVE-202...
14.04.2025 15:38 — 👍 0 🔁 0 💬 0 📌 0

🚨 Next.js Vulnerability (CVE-2025-29927)
🔴 CVSS: Critical (9.1)
📈 intel.intruder.io hype score: 99 ("it's getting all log4shell")
The advice? Patch now. Get the latest commentary from Intruder’s security team: intel.intruder.io/cves/CVE-202...
24.03.2025 11:01 — 👍 0 🔁 0 💬 0 📌 0
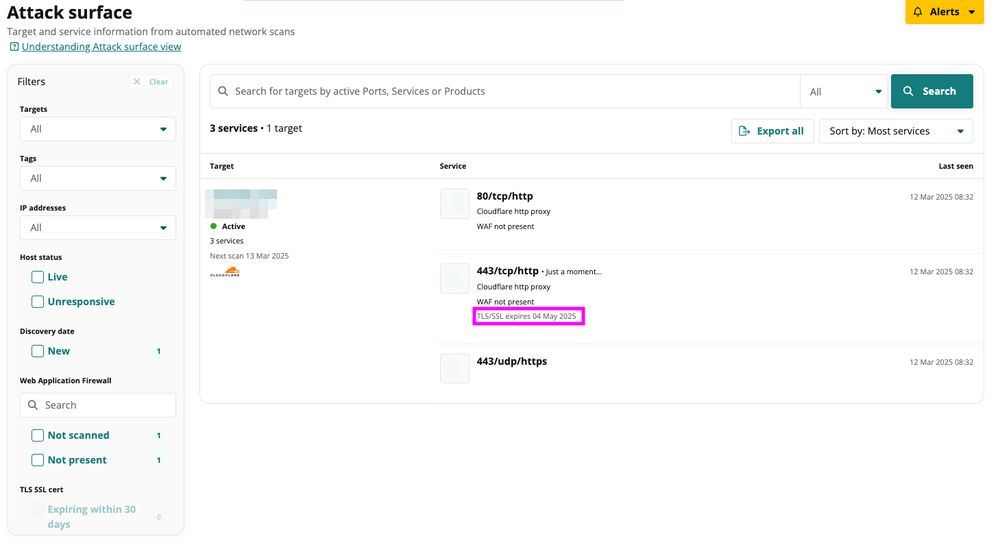
Another day, another expiring SSL certificate…
With SSL certificate expirations making headlines, it’s a reminder of how important it is to have a reliable way to track renewals.
Want to see how easy it is with Intruder? Try it for free:
portal.intruder.io/free_trial
12.03.2025 18:16 — 👍 0 🔁 0 💬 0 📌 0

We discovered CVE-2025-0589 in Octopus Deploy - a vulnerability that exposes sensitive Active Directory user details.
Our research shows broken authentication issues in APIs are far more common than you’d think, with some bugs going undetected for years.
Read more: www.intruder.io/research/oct...
11.03.2025 14:02 — 👍 0 🔁 0 💬 0 📌 0

AWS Security Services: What They Do and Don’t Do
AWS security services help protect your cloud, but they don’t secure everything. See what’s missing and how Intruder goes further to simplify cloud security.
☁️ Cloud security is coming soon to Intruder...
But how will this compare to #AWS security services like GuardDuty, Inspector, and Config?
Learn more and signup to be the first to know when cloud security launches: www.intruder.io/blog/aws-sec...
07.03.2025 09:16 — 👍 0 🔁 0 💬 0 📌 0

CVE-2025-0108 - Overview, Insights & Trends
Get the latest on CVE-2025-0108, including risk score and recommendations. Intel provides vulnerability intelligence on trending CVEs from multiple sources.
🚨 CVE-2025-0108 is a high-severity (CVSS 8.8) vulnerability affecting Palo Alto Networks’ PAN-OS, allowing attackers to bypass authentication and execute certain PHP scripts.
👉 See our latest analysis on Intel: hubs.li/Q036zXVf0
13.02.2025 16:12 — 👍 0 🔁 0 💬 0 📌 0
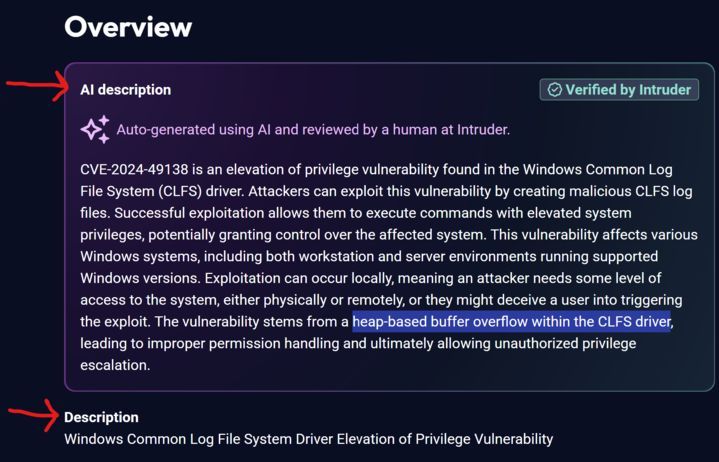
Ever wished NVD descriptions actually explained the vuln? Meet Intruder’s new AI Summaries—turning often lacking CVE jargon into plain English so you can focus on patching, not parsing.
Check it out👉 intel.intruder.io
#VulnerabilityIntelligence #CVE #CyberSecurity
04.02.2025 10:10 — 👍 0 🔁 1 💬 0 📌 0

CVE-2024-55591 - Overview, Insights & Trends
Get the latest on CVE-2024-55591, including risk score and recommendations. Intel provides vulnerability intelligence on trending CVEs from multiple sources.
More details are emerging on #CVE-2024-55591 today - our customers are already ahead of the curve 🚀
We quickly assessed the threat and developed an active check - before one was available from our underlying scanners.
Stay ahead of the latest developments: intel.intruder.io/cves/CVE-202...
16.01.2025 12:22 — 👍 0 🔁 0 💬 0 📌 0

CVE-2024-55591 - Overview, Insights & Trends
Get the latest on CVE-2024-55591, including risk score and recommendations. Intel provides vulnerability intelligence on trending CVEs from multiple sources.
#CVE-2024-55591 is a critical vulnerability in FortiOS and FortiProxy under active exploitation. 🚨
The #vulnerability allows unauthenticated attackers to create administrative accounts. #Fortinet has released IoCs to help identify suspicious activity.
intel.intruder.io/cves/CVE-202...
15.01.2025 10:24 — 👍 0 🔁 0 💬 0 📌 0

CVE-2025-0282 - Overview, Insights & Trends
Get the latest on CVE-2025-0282, including risk score and recommendations. Intel provides vulnerability intelligence on trending CVEs from multiple sources.
CVE-2025-0282 is a critical buffer overflow vulnerability in #Ivanti Connect Secure.
We recommend prioritizing it over other criticals, but due to its complexity, don't expect widespread exploitation.
Get the latest from our Security Team: intel.intruder.io/cves/CVE-202...
#CyberSecurity #InfoSec
09.01.2025 15:05 — 👍 0 🔁 0 💬 0 📌 0

CVE-2024-49112 - Overview, Insights & Trends
Get the latest on CVE-2024-49112, including risk score and recommendations. Intel provides vulnerability intelligence on trending CVEs from multiple sources.
SafeBreach released a writeup on Jan 1st linking CVE-2024-49112 to a DoS exploit. However, the original researcher who reported the bug to Microsoft disagrees.
Find out more: intel.intruder.io/cves/CVE-202...
#CyberSecurity #CVE202449112 #InfoSec #Microsoft
03.01.2025 14:08 — 👍 0 🔁 0 💬 0 📌 0

When PoC exploit code for Mitel MiCollab vulns dropped, Intruder helped a customer reduce exposure within 24hrs:
☁️ Auto-discovered the system via our cloud connector
✅ Deployed a check before our underlying scanners
🚨 Notified the customer so they could fix the issue
Learn more: shorturl.at/lf8wW
12.12.2024 15:57 — 👍 0 🔁 0 💬 0 📌 0

CVE-2024-50623 - Cleo remote code execution - second unauthenticated RCE
Attackers are actively exploiting CVE-2024-50623 to gain remote code execution (RCE) on affected #Cleo servers.
It was initially thought that the patch was insufficient due to ongoing exploitation, but it turns out there is a second unauthenticated RCE.
More info: intel.intruder.io/cves/CVE-202...
11.12.2024 16:21 — 👍 0 🔁 0 💬 0 📌 0
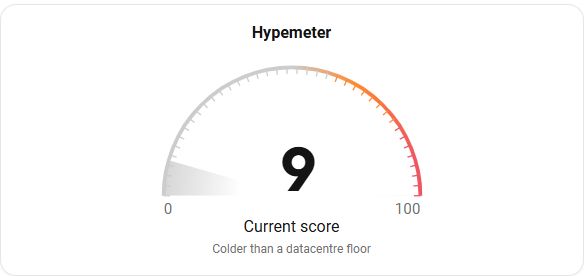
Hypemeter gauge displaying a score of 9 out of 100, with the caption 'Colder than a datacentre floor.' The gauge transitions from gray (low scores) to red (high scores).
Today's hype score: Colder than a datacentre floor ❄️
CVE-2024-42327, a critical vulnerability in #Zabbix, has received the most buzz in the last 24hrs. But with a hype score of 9/100, it's looking like a calm day in the threat landscape so far.
Check it out: intel.intruder.io
#CVE #CyberSecurity
29.11.2024 10:06 — 👍 0 🔁 0 💬 0 📌 0
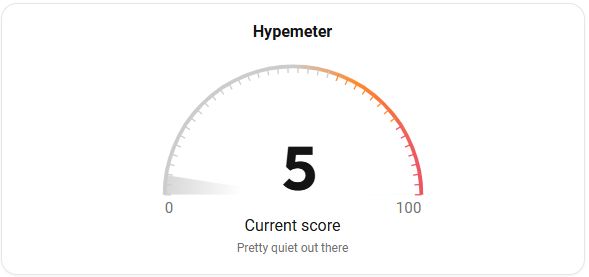
Intel's Hypemeter - 5 out of 100
What's the threat landscape like today?
CVE-2024-5921, a high-severity flaw in the #PaloAlto Networks GlobalProtect app, has received the most buzz in the last 24hrs. But with a hype score of 5 / 100, it's pretty quiet out there.
Stay ahead with Intel: intel.intruder.io/trends
#CVE #CyberSecurity
27.11.2024 16:27 — 👍 2 🔁 0 💬 0 📌 0
it's a website (and a podcast, and a newsletter) about humans and technology, made by four journalists you might already know. like and subscribe: 404media.co
At wired.com where tomorrow is realized || Sign up for our newsletters: https://wrd.cm/newsletters
Find our WIRED journalists here: https://bsky.app/starter-pack/couts.bsky.social/3l6vez3xaus27
Cloudflare is the world’s leading connectivity cloud, and we have our eyes set on an ambitious goal — to help build a better Internet.
Your favorite enterprise technology news vultures, flying high in the Bluesky – On the web since 1998 – More here: https://www.theregister.com/
My work account, focused on cybersecurity. I'm the managing editor, content operations, at Dark Reading, part of Informa TechTarget.
Cybersecurity Economist @ ReturnOnSecurity.com
☆ Cybersecurity reporter
★ Newsletters at Risky Business
#infosec #cybersecurity
https://risky.biz
Author of the Seriously Risky Business cyber security newsletter



















