
S3 File ACL Persistence - Hacking The Cloud
Maintain access to S3 resources by configuring Access Control Lists associated with S3 Buckets or Objects.
Maintain access to S3 resources without creating new users by using S3 ACLs to backdoor key objects and buckets in AWS. This method allows read/write access for external accounts, even without public exposure alerts. Dive into how subtle ACL configurations can achieve persistence!
05.08.2025 14:40 — 👍 0 🔁 0 💬 0 📌 0

Bypass GuardDuty Tor Client Findings - Hacking The Cloud
Connect to the Tor network from an EC2 instance without alerting GuardDuty.
Explore how to connect your EC2 instance to the Tor network without setting off GuardDuty alarms. By utilizing Tor Bridges and obfs4proxy, bypass the UnauthorizedAccess:EC2/TorClient finding seamlessly. Enhance privacy and conceal your traffic's origin. Dive in here:
30.07.2025 14:03 — 👍 0 🔁 0 💬 0 📌 0

Steal IAM Credentials and Event Data from Lambda - Hacking The Cloud
Leverage file read and SSRF vulnerabilities to steam IAM credentials and event data from Lambda.
Discover common vulnerabilities in AWS Lambda that allow attackers to access IAM credentials and event data. These incidents often exploit file read and SSRF vulnerabilities. Learn how attackers can leak sensitive information and how to protect your environments. Read more:
24.07.2025 14:02 — 👍 1 🔁 1 💬 0 📌 0

Survive Access Key Deletion with sts:GetFederationToken - Hacking The Cloud
Use sts:GetFederationToken to maintain access, even if the original IAM credentials are revoked.
Ever wonder how bad actors can still access AWS after access keys are revoked? They might use sts:GetFederationToken for temporary credentials. Learn how this sneaky trick works and how defenders can combat it by monitoring and controlling the use of this API. More details:
22.07.2025 14:05 — 👍 0 🔁 0 💬 0 📌 0

Modify GuardDuty Configuration - Hacking The Cloud
Modify existing GuardDuty configurations in the target account to hinder alerting and remediation capabilities.
In the event of a compromised AWS account, attackers can manipulate GuardDuty configs to avoid detection. By modifying, not deleting, settings, they can evade alerts without raising suspicion. Key tweaks involve IP lists, CloudWatch rules, and suppression tactics. Read more:
15.07.2025 14:06 — 👍 1 🔁 0 💬 0 📌 0
Introduction to the Instance Metadata Service - Hacking The Cloud
An introduction to the Instance Metadata Service and how to access it.
With credentials for IAM roles, it’s crucial to know the Instance Metadata Service's role in security. Learn the differences between IMDSv1 and IMDSv2, and why IMDSv2’s added security layers are a game-changer for protecting your cloud resources.
09.07.2025 14:09 — 👍 0 🔁 0 💬 0 📌 0

Abusing Elastic Container Registry for Lateral Movement - Hacking The Cloud
With ECR permissions you can easily distribute a backdoor to production servers, developer's laptops, or CI/CD pipelines and own the environment by gaining privileged permissions.
When improperly secured, AWS's Elastic Container Registry (ECR) can be a vector for attacks. By exploiting ECR permissions, malicious actors can plant backdoors across cloud environments. Tighten IAM controls and secure your CI/CD pipelines to mitigate risks. Learn more:
03.07.2025 14:06 — 👍 0 🔁 0 💬 0 📌 0

Discover secrets in public AMIs - Hacking The Cloud
How to find public AMIs and get stored secrets.
AMIs in AWS can be public, exposing sensitive data. Discover how to identify and exploit these AMIs by searching for credentials and secrets using AWS commands. Learn manual and automated techniques to dig deeper. Stay informed on cloud security risks! Learn more:
01.07.2025 14:08 — 👍 1 🔁 0 💬 0 📌 0

Connection Tracking - Hacking The Cloud
Abuse security group connection tracking to maintain persistence even when security group rules are changed.
AWS Security Groups can track connections, which could be exploited to maintain connections even after changing Security Group rules. If a connection is active before the rules change, it can persist, posing potential security concerns.
25.06.2025 14:04 — 👍 1 🔁 0 💬 0 📌 0

AWS Organizations Defaults & Pivoting - Hacking The Cloud
How to abuse AWS Organizations' default behavior and lateral movement capabilities.
Discover how AWS Organizations' defaults can impact security. Misconfigured roles and default access can lead to organization-wide breaches if not monitored. Learn about potential risks and the importance of securing management accounts. Ensure your defenses are robust. Read more: buff.ly/SKYpm7j
19.06.2025 14:06 — 👍 2 🔁 0 💬 0 📌 0

Unauthenticated Enumeration of IAM Users and Roles - Hacking The Cloud
Discover how to exploit cross-account behaviors to enumerate IAM users and roles in another AWS account without authentication.
Explore the fascinating ways to enumerate IAM users and roles in another AWS account using no access! Discover methods involving resource-based policies and tools like Quiet Riot for enumeration across AWS, Azure, and Google. Dive into our latest insights today! Link:
17.06.2025 14:07 — 👍 2 🔁 0 💬 0 📌 0

Get IAM Credentials from a Console Session - Hacking The Cloud
Convert access to the AWS Console into IAM credentials.
Turn AWS Console access into IAM credentials using CloudShell! If you have session cookies from a developer’s browser, you can extract IAM credentials through an undocumented endpoint. Perfect for pen tests where direct credentials aren't available. Dive in for more details.
11.06.2025 14:06 — 👍 2 🔁 1 💬 0 📌 0

Unauthenticated Enumeration of Google Workspace Email Addresses - Hacking The Cloud
Discover how to exploit information disclosure configurations in Google Workspace to enumerate valid email addresses.
Discover how to enumerate Google Workspace email addresses with Quiet Riot, potentially aiding password spraying attacks. This could lead to unauthorized access and even help identify AWS Root User accounts. Learn more here:
05.06.2025 14:06 — 👍 1 🔁 0 💬 0 📌 0

User Data Script Persistence - Hacking The Cloud
Maintain access to an EC2 instance and it's IAM role via user data scripts.
Explore how to maintain persistence on an EC2 instance using user data scripts. These scripts, often run as root, can be modified to include backdoors, ensuring continued access. Even if you can't change the script, altering resources they access might do the trick. Learn more:
03.06.2025 14:05 — 👍 2 🔁 0 💬 0 📌 0
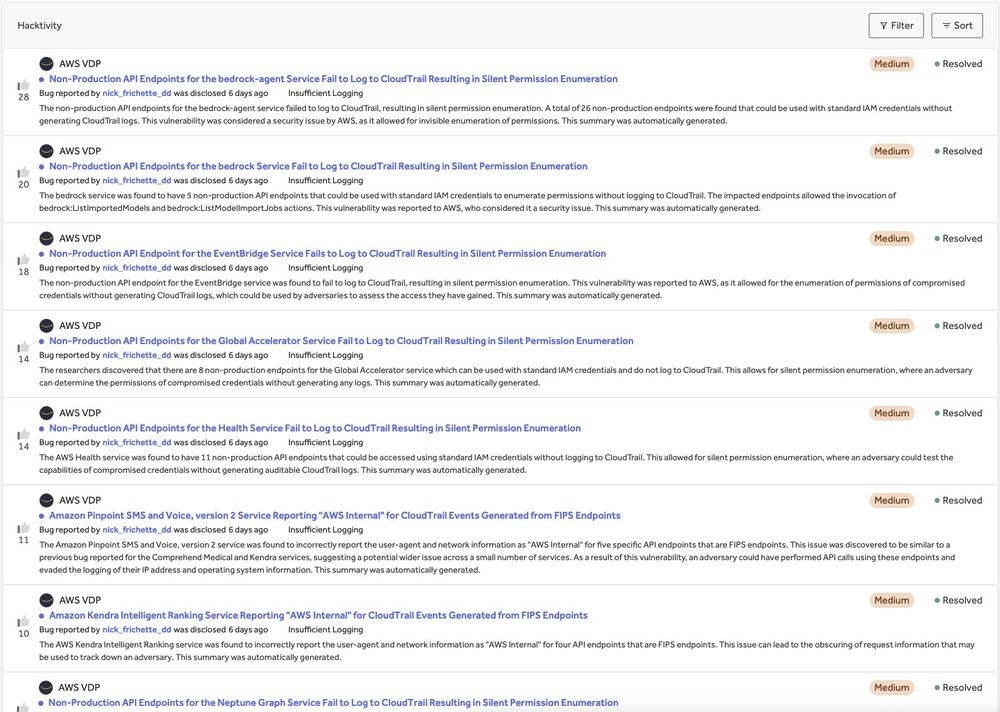
A little over a year ago I published research on how you could leverage non-production AWS API endpoints to enumerate permissions without logging to CloudTrail. A year later...I'm still finding them. Red Teamers, these can be super useful and really up your game!
02.06.2025 13:35 — 👍 5 🔁 2 💬 1 📌 0

Run Command Abuse - Hacking The Cloud
Utilise Azure RunCommands for execution and lateral movement.
Ever wondered about Azure's Run Command feature? It's a potent tool for executing scripts, but it can also pose security risks. Our latest post explores how Run Command can be abused for lateral movement within cloud environments, and how to detect such activities. Let's dive in!
28.05.2025 14:06 — 👍 1 🔁 1 💬 0 📌 0

Anonymous Blob Access - Hacking The Cloud
Finding and accessing files stored in Azure Storage Accounts without authentication.
Explore how Azure's Blob Storage permissions can lead to anonymous access, allowing data retrieval without authentication. Discover how simple misconfigurations can expose sensitive files. Learn more about security in Azure with practical examples and tips.
22.05.2025 14:05 — 👍 0 🔁 0 💬 0 📌 0
Eduard Agavriloae delves into exploiting misconfigured Terraform Cloud OIDC AWS IAM roles. Discover why adding the "app.terraform.io:sub" condition is crucial and learn how these misconfigurations can be exploited—or prevented—using Resource Control Policies. Dive into the details: buff.ly/JJ0VHNV
20.05.2025 14:12 — 👍 0 🔁 0 💬 0 📌 0

Lambda Persistence - Hacking The Cloud
How to establish persistence on a Lambda function after getting remote code execution.
Unlock the secrets of Lambda persistence with our latest blog! After finding remote code execution vulnerabilities, discover how to establish persistence on AWS Lambda functions using Python and Ruby runtimes. Read more about these techniques and their applications:
14.05.2025 14:04 — 👍 0 🔁 0 💬 0 📌 0

Download Tools and Exfiltrate Data with the AWS CLI - Hacking The Cloud
Using the AWS CLI as a LOLScript to download and exfiltrate data.
Threat actors use the AWS CLI to evade detection and exfiltrate data. By leveraging existing tools on Amazon Linux servers, they avoid common monitoring targets like curl and Wget. This post explores how attackers utilize AWS CLI with S3-compatible backends to move data. Learn more:
08.05.2025 14:04 — 👍 0 🔁 0 💬 0 📌 0

IAM unique identifiers - Hacking The Cloud
Chart of the IAM unique ID prefixes.
Understanding IAM unique identifiers in AWS is crucial for security. Check out the significance of prefixes like 'AKIA' for long-lived keys and 'ASIA' for temporary keys. These play a vital role in managing access securely within your cloud infrastructure.
06.05.2025 14:05 — 👍 0 🔁 0 💬 0 📌 0

Tag Your Way In - GCP Privilege Escalation Using Tags - Hacking The Cloud
A new privilege escalation technique in Google Cloud that leverages tag bindings to bypass IAM conditions and gain unauthorized access to sensitive resources.
🚨 New on Hacking the Cloud: Discover how misconfigured tagBindings.create permissions in GCP can lead to privilege escalation. Learn how attackers can exploit tags to gain elevated access. Stay informed and secure your cloud infrastructure.
Read more: hackingthe.cloud/gcp/exploita...
02.05.2025 14:00 — 👍 4 🔁 2 💬 0 📌 0

Introduction to User Data - Hacking The Cloud
An introduction to EC2 User Data and how to access it.
Dive into EC2 User Data! It’s a vital resource for configuring environments but often contains sensitive info like credentials. Learn how attackers can access User Data through internal URLs and APIs, and understand the importance of safeguarding it. More at:
30.04.2025 14:05 — 👍 1 🔁 0 💬 0 📌 0

Steal EC2 Metadata Credentials via SSRF - Hacking The Cloud
Old faithful; How to steal IAM Role credentials from the EC2 Metadata service via SSRF.
Discover how attackers exploit AWS EC2's Metadata Service to steal IAM credentials via SSRF or XXE vulnerabilities. Ensure your cloud security is airtight by enforcing IMDSv2 across instances to mitigate these risks. Stay informed and protected. Link for deeper insight:
24.04.2025 14:04 — 👍 1 🔁 0 💬 0 📌 0

Enumerate Root User Email Address from the AWS Console - Hacking The Cloud
Identify if an email address belongs to the root user of an AWS account.
Discover if an email address is tied to an AWS root account by entering it in the AWS Console. A valid email prompts for a password, while an invalid one shows an error message. Simple yet effective to check account ownership! Find out more:
22.04.2025 14:03 — 👍 2 🔁 0 💬 0 📌 0

CVE-2024-28056: Exploit an AWS Amplify Vulnerability in Same-Account Scenarios - Hacking The Cloud
An in-depth explanation of how to still abuse CVE-2024-28056, a vulnerability in AWS Amplify that exposed IAM roles to takeover.
AWS Amplify's vulnerability CVE-2024-28056 involves IAM roles susceptible to same-account exploitation due to misconfigured policies. Despite AWS's partial fix, a potential breach could occur if a basic authflow identity pool is misconfigured. Learn how to protect your resources.
01.04.2025 14:00 — 👍 2 🔁 0 💬 0 📌 0

Enumerate AWS Account ID from an EC2 Instance - Hacking The Cloud
With access to an ec2 instance, you will be able to identify the AWS account it runs in.
Got shell access to an AWS EC2 instance? You can find the account ID with aws sts get-caller-identity or by querying instance metadata. Handy for audits, investigations, or just understanding your environment. Details + commands here:
26.03.2025 14:00 — 👍 0 🔁 0 💬 0 📌 0
@hackingthe.cloud has crossed the 2,000 stargazers mark on GitHub! Thank you so much to everyone who has supported and contributed to the project over the years. I have much more content on the way!
22.03.2025 16:31 — 👍 6 🔁 1 💬 0 📌 0

Data Exfiltration through S3 Server Access Logs - Hacking The Cloud
Exfiltrate data via S3:GetObject and S3 server access logs.
Ever thought of using S3 server access logs for data exfiltration? If you can make GetObject requests, even denied ones, you might be able to leak data into a logging bucket you control. It's sneaky, but it has its challenges. Full breakdown here:
20.03.2025 14:01 — 👍 0 🔁 0 💬 0 📌 0




























