
My #Hexacon talk with Etienne on exploiting the Bluetooth stack (fluoride) is now available on YouTube
youtu.be/wYulofbUDqY?...
@cleptho.bsky.social
Offensive Security | Вічна пам'ять / Вечная память https://twitter.com/cleptho | https://infosec.exchange/@cleptho

My #Hexacon talk with Etienne on exploiting the Bluetooth stack (fluoride) is now available on YouTube
youtu.be/wYulofbUDqY?...

New Blog Post: Seth Jenkins broke kASLR by doing … nothing 😩
googleprojectzero.blogspot.com/2025/11/defe...
🎥 Eyes wide shut! David Berard of @synacktiv.com just breached the @Ubiquiti AI Pro surveillance system at #Pwn2Own. He also serenaded us with round of "Baby Shark" played through the speaker. He's off to the disclosure room with an ear worm and the details.
23.10.2025 11:10 — 👍 3 🔁 4 💬 0 📌 0

Confirmed! The team from @synacktiv.com used a buffer overflow to exploit the Phillips Hue Bridge. Their unique bug earns them $20,000 and 4 Master of Pwn points. #Pwn2Own
22.10.2025 17:11 — 👍 8 🔁 4 💬 0 📌 0
New blog post: Exploiting the Synology TC500 at Pwn2Own Ireland 2024
We built a format string exploit for the TC500 smart cam. It didn’t get used, but it made for a fun case study.
blog.infosectcbr.com.au/2025/08/01/e...
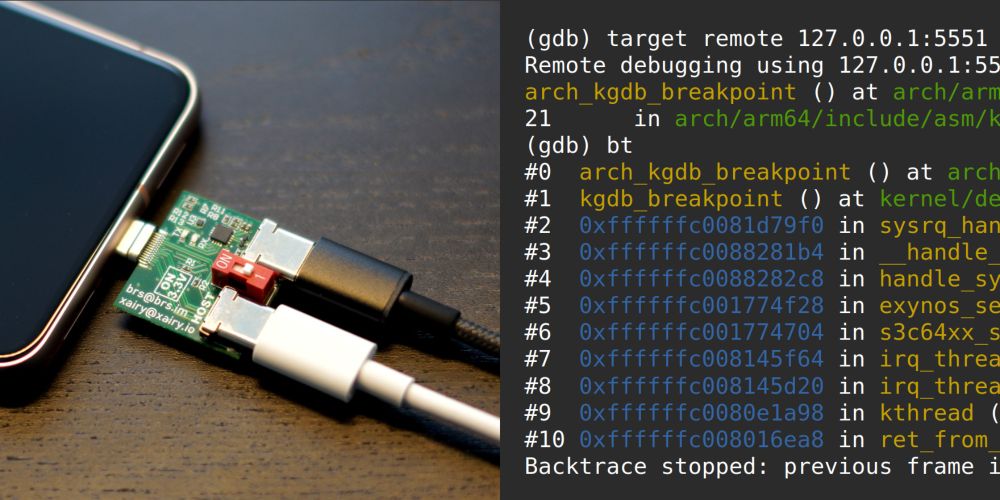
Documented instructions for setting up KGDB on Pixel 8.
Including getting kernel log over UART via USB-Cereal, building/flashing custom kernel, breaking into KGDB via /proc/sysrq-trigger or by sending SysRq-G over serial, dealing with watchdogs, etc.
xairy.io/articles/pix...
Dumping firmware from JieLi chips
JieLi chips are fairly common in Bluetooth audio devices, but they are also becoming more common in miscellaneous devices. Fortunately, retrieving the firmware is mostly straightforward.
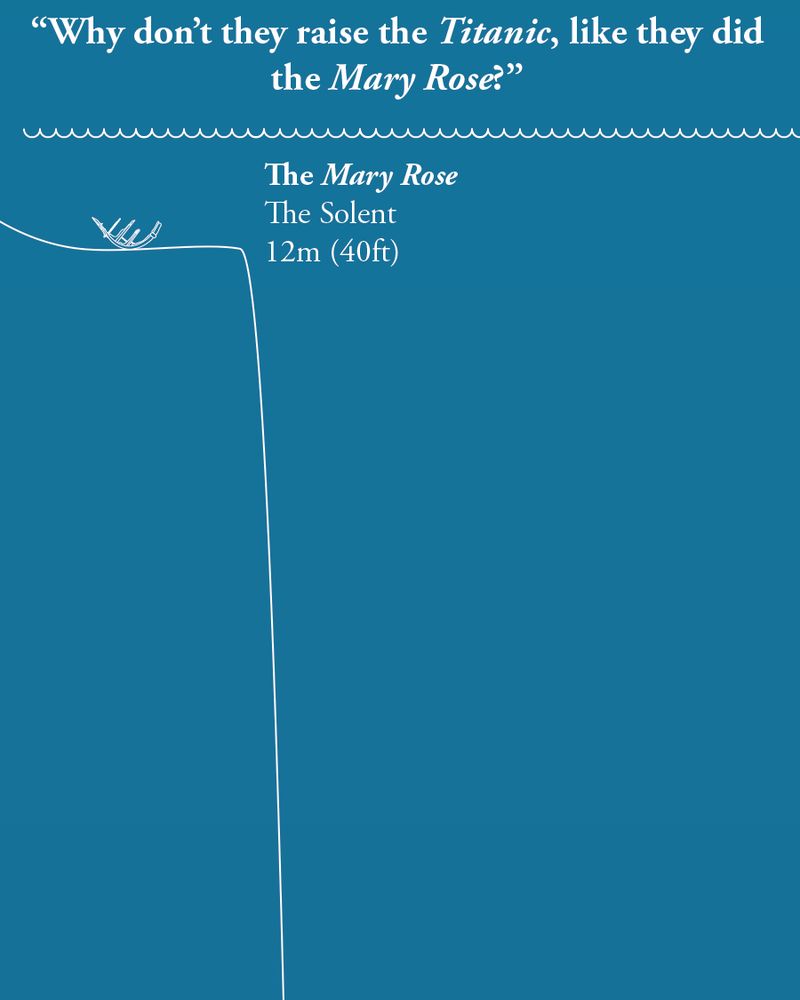
A light blue diagram depicting the sea, with the water's surface at the top, and just below it is an outline of the Mary Rose, with the depth (12m, 40ft or 6.7 fathoms). There is a line showing the seabed, which takes a rapid dive into the vertical...
On the anniversary of the sinking of the Titanic, we thought we'd answer a question that's often asked,
"If they raised the Mary Rose, why not raise the Titanic?"
Allow our scaled diagram to explain...

A lamppost covered in dark vines that resemble a creature with long hair bent over. When the light is on, it looks like the head/skull is glowing.
I grew up on a diet of Scary Stories to Tell in the Dark... I swear these vines covering a lamppost in Wroclaw, Poland are straight out of my childhood nightmares.
10.04.2025 07:27 — 👍 3543 🔁 615 💬 56 📌 45
v happy to finally share my slides for my @reconmtl.bsky.social 2024 talk “GOP Complex: Image parsing bugs, EBC polymorphic engines and the Deus ex machina of UEFI exploit dev.” Really proud of this talk + v grateful to the amazing REcon team for another incredible con 🖤
github.com/ic3qu33n/REc...
This is fake but if we boost it enough someone from the administration will claim it’s true during the congressional hearings so you know what to do
27.03.2025 09:47 — 👍 23 🔁 5 💬 0 📌 0
simpsons image. march yelling "war thunder no!" then bart, labelled "war thunder" says "what?" the marge says "sorry, force of habit"
24.03.2025 22:23 — 👍 6 🔁 2 💬 0 📌 0
Flyer for the Phrack 40th anniversary edition CFP. It contains the text of the CFP at phrack.org, with additional text "CFP EXTEND!! Papers due June 15 2025" and "Phrack Since 1985"
We heard you needed some more time, so we wanted to let you cook.
We decided to push the Phrack 72 CFP deadline back until June 15th.
Stay tuned for upcoming Phrack events.
Print this flyer out and give it to someone IRL!!
For $20,000/month, I will personally google stuff and paraphrase it for you into mostly-accurate answers.
05.03.2025 18:57 — 👍 58 🔁 7 💬 6 📌 2Pumpkin (@u1f383 on X) does cool work. Here is another cool read about an interesting race condition involving signal handling
u1f383.github.io/linux/2025/0...

Announcing #Pwn2Own Berlin! We're moving our enterprise-focused event to @offensivecon.bsky.social and introducing an AI category. More than $1,000,000 in cash & prizes (Incl. a Tesla) are available to win. Check out the details at www.zerodayinitiative.com/blog/2025/2/...
24.02.2025 16:48 — 👍 11 🔁 7 💬 0 📌 1
I made an ImHex pattern file for the ftab file format used for Apple C1 firmware and Apple accessories
gist.github.com/matteyeux/d1...
OpenSSH 9.9p2 has just been released with fixes for two security problems reported by the Qualys Security Advisory Team: a denial-of-service in the default configuration and a host impersonation by on-path attackers when VerifyHostKeyDNS is enabled (off by default).
www.openssh.com/releasenotes...
Microsoft's own research confirms something that was already pretty obvious: relying on a text generating machine to come up with answers erodes critical thinking, and is a method favoured by those who never liked doing critical thinking in the first place
advait.org/files/lee_20...
They found a way to litter from space
06.02.2025 00:16 — 👍 2827 🔁 896 💬 66 📌 28for anyone interested in linux kernel or android security research, i'm experimenting with a custom feed here bsky.app/profile/did:...
03.12.2024 19:45 — 👍 5 🔁 2 💬 0 📌 0
Earlier this year, I used a 1day to exploit the kernelCTF VRP LTS instance. I then used the same bug to write a universal exploit that worked against up-to-date mainstream distros for approximately 2 months.
osec.io/blog/2024-11...
New platform, who dis? It me, and @johnnyspandex.bsky.social dropping some VPN client exploit freshness! 🌮🔒
Today, we're releasing NachoVPN, our VPN client exploitation tool, as presented at SANS HackFest Hollywood. Get it on the @amberwolfsec.bsky.social blog:
blog.amberwolf.com/blog/2024/no...
Interesting paper by Erin Avllazagaj to automatically find Linux kernel objects being potentially useful for privilege escalation, tool is called SCAVY. www.usenix.org/system/files...
22.11.2024 09:44 — 👍 5 🔁 2 💬 0 📌 0Qualys is at it again:
https://seclists.org/oss-sec/2024/q4/108
LPEs in needrestart (CVE-2024-48990, CVE-2024-48991, CVE-2024-48992,
CVE-2024-10224, and CVE-2024-11003)
Original post

A view from a lake in the mountains
Touching grass
What else to remain sane?
Patch your crap
14.11.2024 20:14 — 👍 1 🔁 1 💬 0 📌 0It would be really nice to be able to click on a starter pack and instead of just doing “follow all”, turn it instantly into a pinned feed
10.11.2024 16:45 — 👍 2516 🔁 222 💬 73 📌 38OpenSSH 9.6 has just been released: openssh.com/releasenotes...
Among other things, this release contains a fix for the so-called Terrapin Attack (terrapin-attack.com)