
Our threat research team details KiwiStealer's capabilities and a malware analysis of how it exfiltrates data via HTTP POST requests in our latest blog: blog.pulsedive.com/unpacking-ki...
13.08.2025 17:06 — 👍 0 🔁 0 💬 0 📌 0@pulsedive.com.bsky.social
Frictionless threat intelligence solutions for growing teams. On-demand searching, scanning & enrichment for the security community. Dive right in at pulsedive.com.

Our threat research team details KiwiStealer's capabilities and a malware analysis of how it exfiltrates data via HTTP POST requests in our latest blog: blog.pulsedive.com/unpacking-ki...
13.08.2025 17:06 — 👍 0 🔁 0 💬 0 📌 0
Where do IPs and domains have a place in CTI workflows?
What can and should you do with them?
Here's our take: blog.pulsedive.com/collection-t...
Community Resource Share: "Ransomch(.)at"
ransomch.at
A collection of real-world ransomware negotiations in support of analysis, data-driven insights, and industry collaboration.
The existing collection of chats from 23 ransomware brands so far include:
Akira
BlackBasta
Conti
Hive
Lockbit
REvil

Newest threat research blog out now: Albabat 2.0.0 Decoded
We dig into Albabat's config file, executed ransomware commands, and ransom note.
Read: blog.pulsedive.com/albabat-2-0-...

Just added 1.4K+ IOCs related to phishing kit Oriental Gudgeon, primarily targeting Japanese financial services cos.
Investigate shared properties & attributes:
pulsedive.com/threat/Orien...
Explore IOCs: pulsedive.com/explore/?q=t...
Credit to the urlscan team: urlscan.io/blog/2025/05...
Learn more:
US DOJ Release: www.justice.gov/opa/pr/justi...
Threat Profile: pulsedive.com/threat/Earth...

In March, the US DOJ unsealed an indictment against 12 Chinese nationals for involvement in global espionage operations, including 8 i-Soon employees. Operations were related to and some attacks attributed to Earth Lusca, also known as FishMonger and Aquatic Panda, amongst other aliases.
31.03.2025 18:31 — 👍 0 🔁 0 💬 1 📌 0
Related Threats: Hellcat & Morpheus
pulsedive.com/threat/Hellc...
pulsedive.com/threat/Morph...
- Recent growth in activity for both RaaS brands
- Identical payloads suggest shared codebase
- Differing victims and contact details

This analysis covers the three known mechanisms for delivery (including PPT, Twitter, Google Ads lures) as well as the complete intrusion chain.
21.03.2025 15:27 — 👍 0 🔁 0 💬 0 📌 0
New analysis of Rilide delivery methods and intrusion chain out now: blog.pulsedive.com/rilide-an-in...
First reported in April 2023, Rilide is an information stealer masquerading as a browser extension targeting Chromium-based browsers.
Community Share: "Black Basta Chat Leak - Organization & Infrastructure" by Cyber_0leg / Cybercrime Diaries
www.cybercrimediaries.com/post/black-b...
This blog examines exposed details of Black Basta, including its leadership hierarchies, business model, and technical infrastructure.

New research on the PolarEdge botnet:
- Targeting edge devices (Cisco, QNAP, Synology, ASUS)
- Active since at least Q4 2023
- Compromised 2K+ unique IP addresses
- Report and analysis by Sekoia.io: lnkd.in/g4Wfi2Vt
- Pulsedive profile: pulsedive.com/threat/Polar...

Browser extensions are commonly used, but present a significant security risk as a growing threat vector.
Our newest blog looks at examples from January 2025, including Cyberhaven and GraphQL Network Inspector, to discuss how threat actors compromise extensions.
blog.pulsedive.com/compromised-...
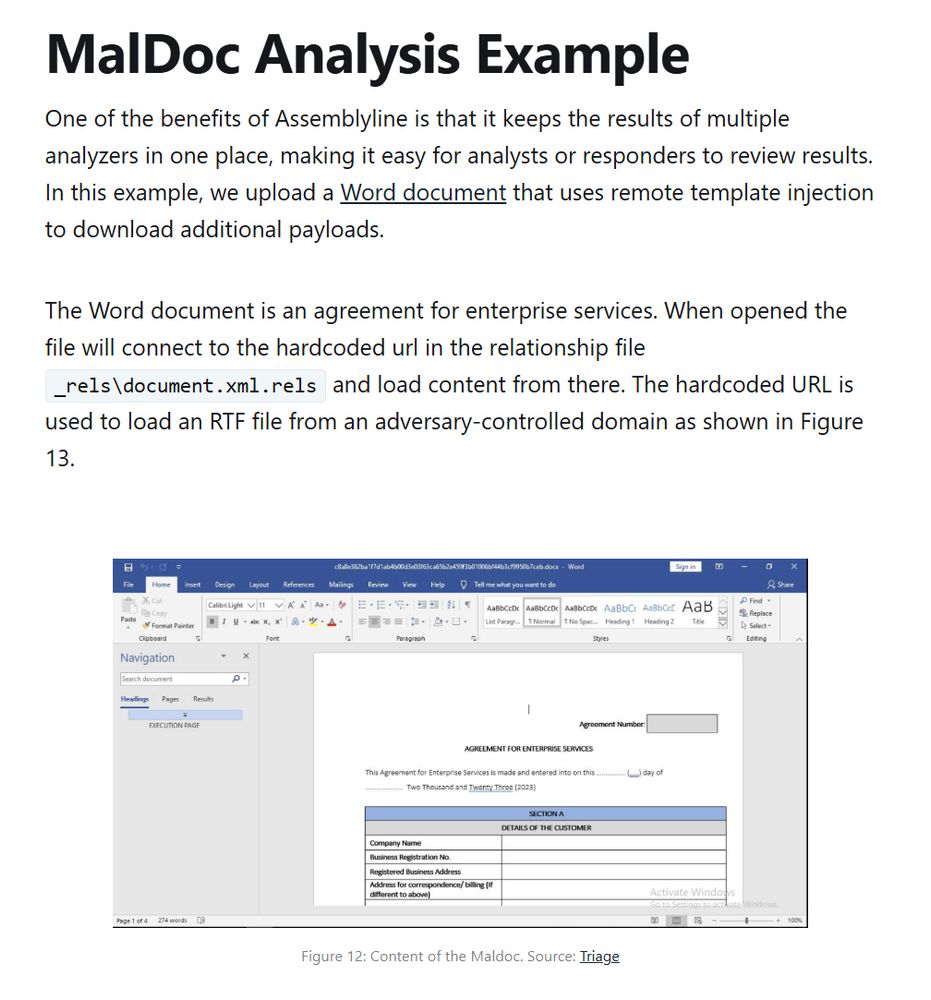
Our guide includes how to install and use Assemblyline, an example walkthrough, and helpful resources.
07.01.2025 18:27 — 👍 0 🔁 0 💬 0 📌 0The tool is ideal for blue teams, CTI researchers, and IR professionals looking to automate and streamline malware samples processing. It is especially helpful for security teams handling large volumes of malware and seeking a scalable, customizable solution for efficient triage.
07.01.2025 18:26 — 👍 0 🔁 0 💬 1 📌 0
Just published a 101 guide on how to use Assemblyline, the open-source malware triage tool created by the Canadian Centre for Cyber Security.
Read: blog.pulsedive.com/assemblyline...
 30.12.2024 16:52 — 👍 0 🔁 0 💬 0 📌 0
30.12.2024 16:52 — 👍 0 🔁 0 💬 0 📌 0



Plus, catch a rewind of Pulsedive at the end, including most read blogs and product updates.
30.12.2024 16:51 — 👍 1 🔁 0 💬 1 📌 0
Our recap of 2024:
- Key exploited vulnerabilities
- Top malware
- Outages
- Law enforcement actions
- Looking ahead to 2025
Read: blog.pulsedive.com/2024-in-revi...
just pushed an update to @pulsedive.com, should improve scan performance and Analyze bulk scan hangs.
10.12.2024 00:15 — 👍 2 🔁 2 💬 0 📌 0
With 3 weeks left in 2024, we wanted to thank you for all you do in the security community.
So we're hosting a year-end sticker giveaway through Dec. 21- no purchase necessary.
To participate:
- Like this post 👍
- Fill out: forms.gle/nxLQQxNtRahS...

Places to find infosec Black Friday deals:
"The Big List for Infosec" github.com/0x90n/InfoSe...
"For Security Professionals and Developers" github.com/davidalex89/...
"Tagged, Searchable, and All Year Round"
training.dfirdiva.com/current-disc...