
Microsoft's legal team seizes 256 domains used by the ONNX phishing service
blogs.microsoft.com/on-the-issue...
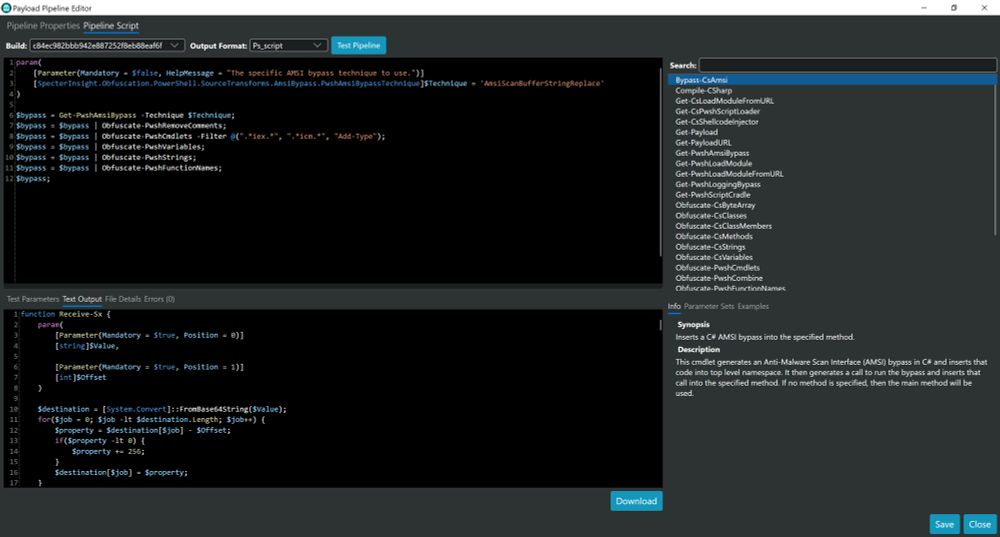
Check out this new AMSI bypass released with SpectersInsight 4.0.0! This technique enables loading of .NET binaries without detection. Implementations in C, C#, and PowerShell provided.
practicalsecurityanalytics.com/new-amsi-byp...

Tools
Cloud Auditing Tool - github.com/nccgroup/ScoutSuite
Post-Exploitation toolset
github.com/dafthack/GraphRunner
Find gaps within Azure MFA requirements.
github.com/absolomb/FindMeAccess
BloodHound github.com/BloodHoundAD/AzureHound
Azure AD hacking & admin
github.com/Gerenios/AADInternals

A photograph of the keyboard from an ADM-3A terminal. Arrows can be seen on the H, J, K, and L keys; left, down, up, and right arrows respectively
If you ever wondered why vi uses h, j, k, and l for cursor movement: it's because it was written using an ADM-3A terminal, which had a keyboard that looked like this
20.11.2024 00:11 — 👍 107 🔁 28 💬 7 📌 2Hello World!
20.11.2024 00:13 — 👍 2 🔁 0 💬 1 📌 0