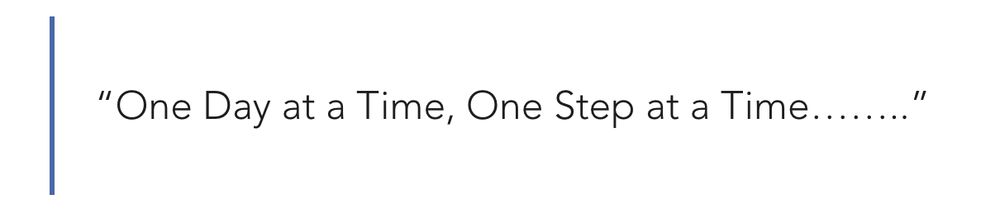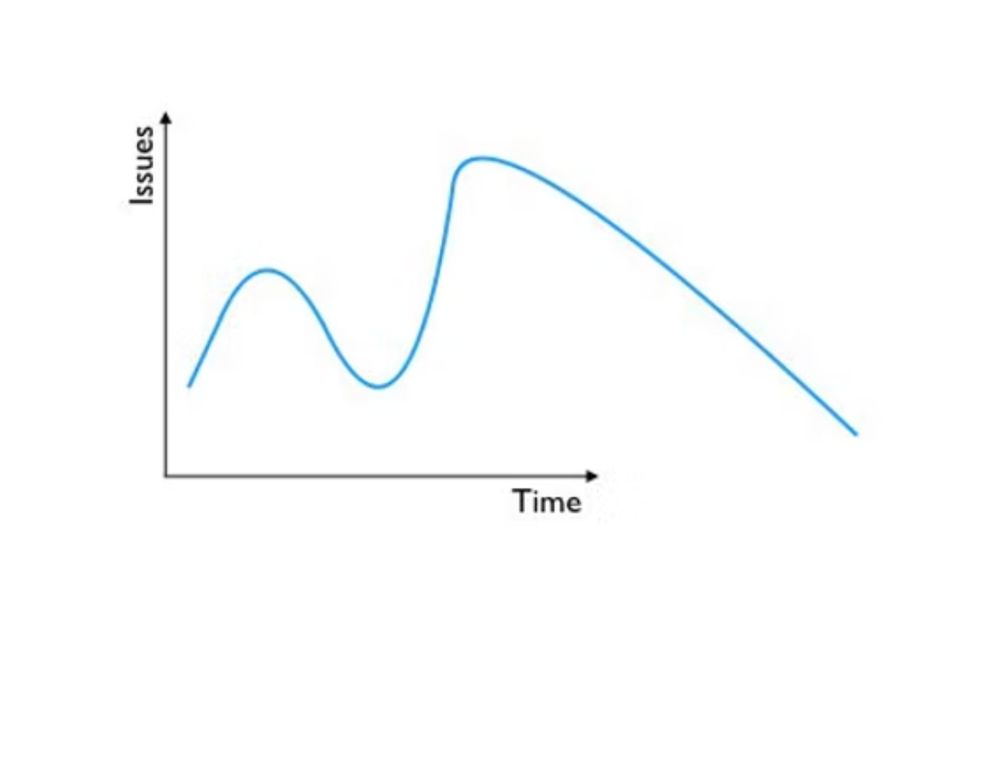
The Don't Fire Me Chart
A lot of premature CISO turnover is caused by the security program uncovering previously unknown risks and issues. So, paradoxically, the best CISOs make the situation *seem* worse before it then *actually* gets better.
www.philvenables.com/post/career-...
12.07.2025 14:42 — 👍 2 🔁 1 💬 0 📌 0

Cyber Insights Needed & Delivered
My analysis of the recent Cyentia Institute report. Things are getting worse in absolute terms but it’s not clear (my take) they are getting worse relative to what the situation might be.
www.philvenables.com/post/cyber-i...
28.06.2025 13:59 — 👍 1 🔁 1 💬 0 📌 0
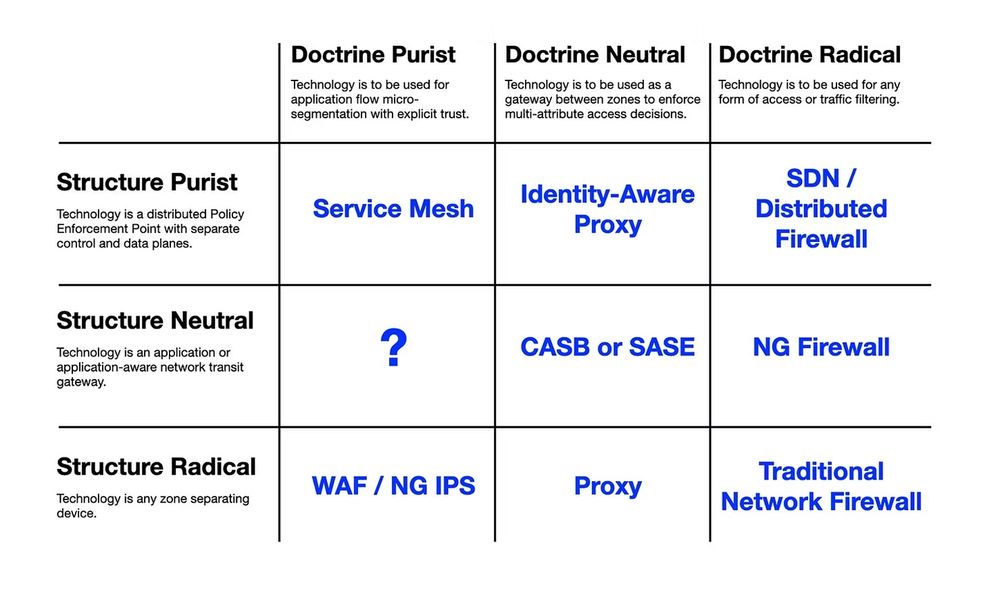
Segmentation Technologies / Zero Trust
Thinking about doctrine vs. structure is a useful mental model to validate a technology’s adequacy for a particular task. In short, to know whether we are jamming a square peg into a round hole.
www.philvenables.com/post/segment...
14.06.2025 15:44 — 👍 2 🔁 0 💬 0 📌 0
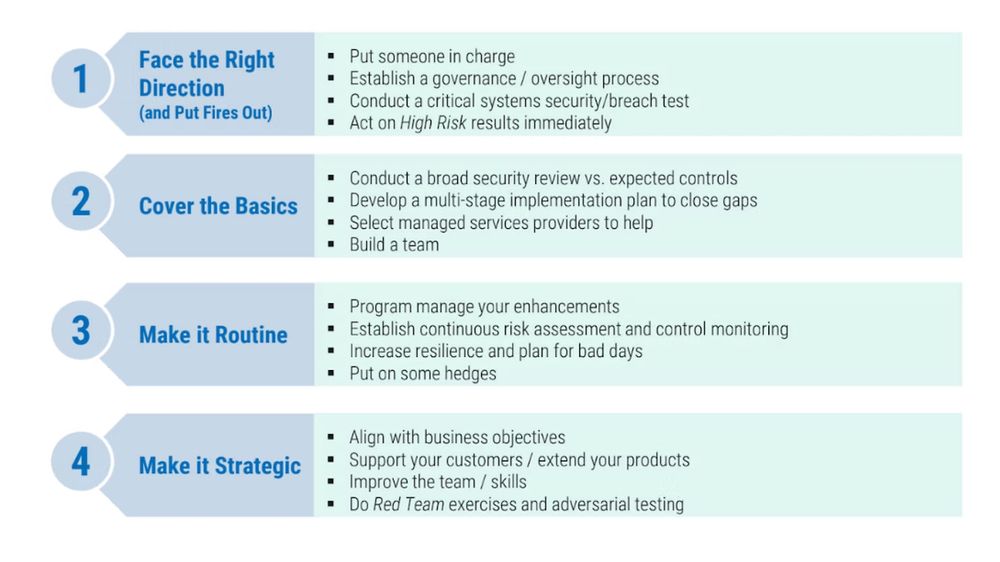
Starting a Security Program from Scratch (or re-starting).
www.philvenables.com/post/startin...
17.05.2025 17:05 — 👍 3 🔁 0 💬 0 📌 0

Security Leaders’ Reading List
Not many security books. Security leader challenges are mostly, well, leadership along with a healthy dose of program mgmt, culture, attention to detail, risk mgmt and more.
www.philvenables.com/post/leaders...
22.03.2025 17:35 — 👍 7 🔁 1 💬 0 📌 1
Turning the Security Flywheel
This post explores the "flywheel" concept and its application to security, demonstrating how to create self-reinforcing cycles that improve effectiveness.
www.philvenables.com/post/turning...
08.03.2025 15:44 — 👍 5 🔁 3 💬 0 📌 1

Keys to Career Success
www.philvenables.com/post/keys-to...
11.01.2025 16:19 — 👍 1 🔁 1 💬 0 📌 1

Want to know more about cyber-physical resilience & why leading indicators like software reproducibility & cold-restart time are more effective than just focusing on lagging indicators?
Then take a listen to the 2024 season finale of the cloud security podcast.
cloud.withgoogle.com/cloudsecurit...
24.12.2024 14:46 — 👍 3 🔁 1 💬 0 📌 1

Remember, as security professionals we are defending the free flow of ideas and capital that are essential for human progress. Defending lives and livelihoods. That's the mission. Happy Holidays.
sketchplanations.com/the-three-br...
22.12.2024 15:17 — 👍 1 🔁 0 💬 0 📌 0
Leadership: One Day at a Time, One Step at a Time.
www.philvenables.com/post/leaders...
14.12.2024 15:36 — 👍 0 🔁 0 💬 0 📌 0

Cloud CISO Perspectives: Our 2025 Cybersecurity Forecast report | Google Cloud Blog
Google Cloud security experts don their forecasting hats to gauge what’s coming in 2025, in our newest CISO newsletter.
Cloud CISO Perspectives for early Dec '24 is up covering:
- Forecasting 2025: Notes from the Field
- Open source security patch validation
- C2 in browser isolation environments
- Every CTO should be a CTSO
- and more......
cloud.google.com/blog/product...
10.12.2024 18:12 — 👍 1 🔁 0 💬 0 📌 0

The “Eureka!” Moment
We asked 20 scientists and thought leaders to recall when they realized AI had the potential to change the world.
How has the development and adoption of AI changed over the last year? Dive into the current landscape in this issue of the Dialogues magazine, from @Google and @atlanticrethink for insightful perspectives on the transformative power of AI.
Read here: www.theatlantic.com/sponsored/go...
02.12.2024 16:43 — 👍 0 🔁 0 💬 0 📌 0

Lessons in Crisis Management - Top 10 Disaster Movies
Which ones am I missing?
www.philvenables.com/post/lessons...
16.11.2024 15:35 — 👍 1 🔁 0 💬 0 📌 0
6 Truths of Cyber Risk Quantification
I wrote the original version of this post over 4 years ago. In revisiting this it is interesting to note that not much has actually advanced in the field. Yes, there have been more products and tools ...
6 Truths of Cyber Risk Quantification
1. Risk Quant vs. Risk Comms
2. Risk = Hazard + Outrage
3. Experience and Judgement Eats Data for Breakfast
4. A Tree Falls in the Forest
5. All Risk Quantification is Wrong
6. Multi-Disciplinary or Nothing
www.philvenables.com/post/6-truth...
07.09.2024 17:33 — 👍 2 🔁 0 💬 0 📌 0
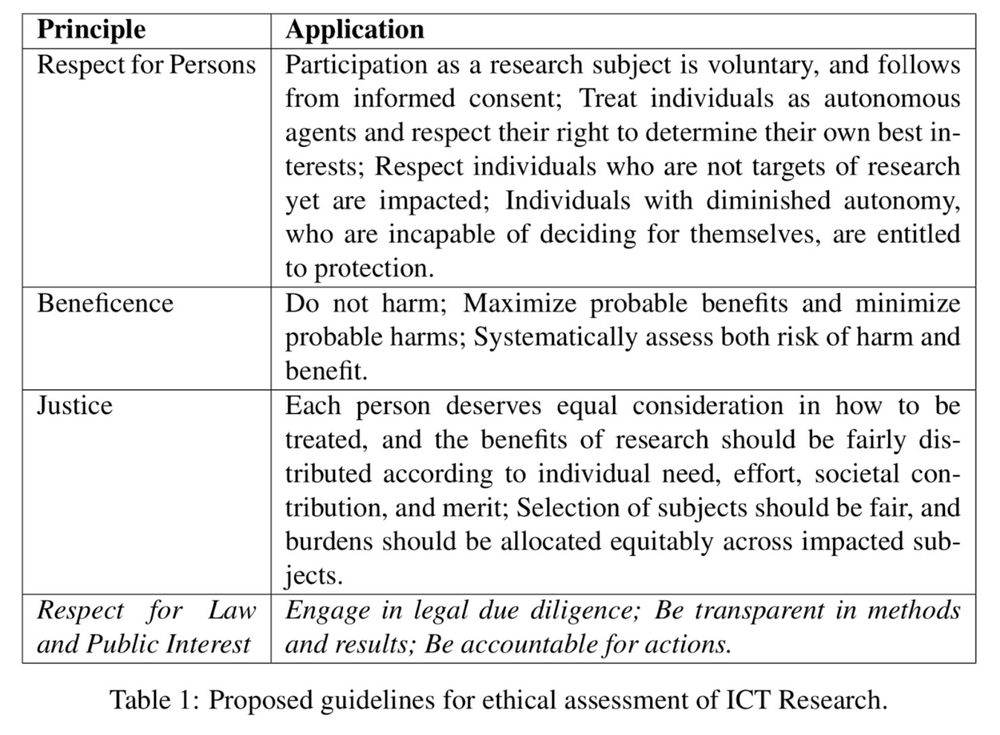
Ethics and Computer Security Research
- Stakeholder Perspectives and Considerations
- Respect for Persons and Informed Consent
- Beneficence
- Justice
- Respect for Law and Public Interest
www.philvenables.com/post/ethics-...
24.08.2024 14:20 — 👍 1 🔁 0 💬 0 📌 0