![Abstract. We initiate the study of basing the hardness of hinted ISIS problems (i.e. with trapdoor information, or ‘hints’) on the previously conjectured space-time hardness of lattice problems without hints. We present two main results.
1. If there exists an efficient algorithm for hinted ISIS that outputs solutions a constant factor longer than the hints, then there exists a single-exponential time and polynomial memory zero-centred spherical Gaussian sampler solving hinted SIS with norm a constant factor shorter than the hints.
2. Assume the existence of a chain of algorithms for hinted ISIS each taking as input Gaussian hints whose norms decrease by a constant factor at each step in the chain, then there exists a single-exponential time and polynomial memory algorithm for SIS with norm a quasilinear factor from optimal.
The existence of such hinted ISIS solvers implies single-exponential time and polynomial memory algorithms for worst-case lattice problems, contradicting a conjecture by Lombardi and Vaikuntanathan (CRYPTO’20) and all known algorithms. This suggests that hinted ISIS is hard.
Apart from advancing our understanding of hinted lattice problems, an immediate consequence is that signing the same message twice in GPV-style [Gentry–Peikert–Vaikuntanathan, STOC’08] schemes (without salting or derandomisation) likely does not compromise unforgeability. Also, cryptanalytic attempts on the One-More-ISIS problem [Agrawal–Kirshanova–Stehlé-Yadav, CCS’22] likely will need to overcome the conjectured space-time hardness of lattices.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreib5oxxsmuh3zvn7oz6c2bhusztjf5oyp4aqzn7w7m6kpbphrokiou@jpeg)
Abstract. We initiate the study of basing the hardness of hinted ISIS problems (i.e. with trapdoor information, or ‘hints’) on the previously conjectured space-time hardness of lattice problems without hints. We present two main results.
1. If there exists an efficient algorithm for hinted ISIS that outputs solutions a constant factor longer than the hints, then there exists a single-exponential time and polynomial memory zero-centred spherical Gaussian sampler solving hinted SIS with norm a constant factor shorter than the hints.
2. Assume the existence of a chain of algorithms for hinted ISIS each taking as input Gaussian hints whose norms decrease by a constant factor at each step in the chain, then there exists a single-exponential time and polynomial memory algorithm for SIS with norm a quasilinear factor from optimal.
The existence of such hinted ISIS solvers implies single-exponential time and polynomial memory algorithms for worst-case lattice problems, contradicting a conjecture by Lombardi and Vaikuntanathan (CRYPTO’20) and all known algorithms. This suggests that hinted ISIS is hard.
Apart from advancing our understanding of hinted lattice problems, an immediate consequence is that signing the same message twice in GPV-style [Gentry–Peikert–Vaikuntanathan, STOC’08] schemes (without salting or derandomisation) likely does not compromise unforgeability. Also, cryptanalytic attempts on the One-More-ISIS problem [Agrawal–Kirshanova–Stehlé-Yadav, CCS’22] likely will need to overcome the conjectured space-time hardness of lattices.

Image showing part 2 of abstract.
Hardness of hinted ISIS from the space-time hardness of lattice problems (Martin R. Albrecht, Russell W. F. Lai, Eamonn W. Postlethwaite) ia.cr/2026/187
06.02.2026 11:11 — 👍 1 🔁 1 💬 0 📌 0

Inside Reform’s plans for a fascist takeover
In today's article shado editor Elia Ayoub discusses Reform’s “Operation Restore Justice”, the risks of a British ICE and how we can resist.
Apropos of nothing, here's a piece on Reform's plans for a British ICE: shado-mag.com/articles/opi...
Here's the policy document: web.archive.org/web/20260127...
Here's a piece on the Labour Government's practice of emulating the US' celebration of brutality: www.theguardian.com/politics/202...
01.02.2026 14:52 — 👍 2 🔁 1 💬 0 📌 0
Isn't it the IACR via Kevin eprint-admin@iacr.org?
28.01.2026 08:30 — 👍 1 🔁 0 💬 1 📌 0
YouTube video by Seth Moulton
ICE is full of COWARDS. They are all absolute, pathetic, untrained COWARDS. DEFUND AND PROSECUTE.
This is right. This is the message. This is the urgency.
Minneapolis and so many other places are living under paramilitary occupation and tyranny by out of control, unaccountable federal thugs. This cannot stand.
www.youtube.com/shorts/hyqtA...
24.01.2026 21:58 — 👍 6 🔁 1 💬 0 📌 0

We're hosting an Autumn School in London, UK, from 15 to 17 September 2026, to bring together ethnographers and cryptographers to discuss ways in which the two fields can be meaningfully brought into conversation.
This is also the premise of our Social Foundations of Cryptography project: to ground cryptography in ethnography. Here, we rely on ethnographic methods, rather than our intuition, to surface security notions that we then formalise and sometimes realise using cryptography.
Our intention is to 'flip' the typical relationship between the computer and social sciences, where the latter has traditionally ended up in a service role to the former. Rather, we want to put cryptography at the mercy of ethnography.
But how do we do this? How do we as cryptographers interact with and make sense of ethnographic field data? How can we refine, improve or extend this interaction? What obstacles do we face when we make cryptography rely on ethnographic data which is inherently 'messy'? How do we handle that cryptographic notions tend to require some form of generalisation but ethnographic findings can only be particular?
How do ethnographers retain the richness of ethnographic field data in conversations with cryptographic work? Indeed, our project has already highlighted some limitations of our approach. It has brought to the fore concrete challenges in 'letting the ethnographic data speak' while still making it speak to cryptography.
The Autumn School is an opportunity to explore these questions jointly across ethnography and cryptography, through a series of talks, group discussions and activities.
We say a bit more about the programme and registration for the Autumn School here.
Social Foundations of Cryptography: Autumn School
London, UK | 15 to 17 September 2026
social-foundations-of-cryptography.gitlab.io/school
13.01.2026 16:30 — 👍 9 🔁 6 💬 1 📌 0
And now we are famous: www.nytimes.com/2025/11/21/w... - congratulations to all colleagues who made the NYT (both through quotes, by playing a role, or by being on this picture)
22.11.2025 05:35 — 👍 43 🔁 11 💬 2 📌 4

Pressure prompts universities to revise EDI recruitment ads
Universities change job requirements after free speech groups raise concerns following new legislation
Two stories from King's College London:
1/ A student is at risk of losing their visa over their Palestine activism www.cage.ngo/articles/leg...
2/ Equality, Diversity and Inclusion removed from job ads: www.timeshighereducation.com/news/pressur...
Does that remind you of anything?
23.10.2025 11:52 — 👍 8 🔁 1 💬 0 📌 0
You may think of a mode of operation as a way of constructing an encryption algorithm from a PRP. So, in particular: "AES" is not an encryption algorithm but "AES-GCM" is an encryption algorithm (achieving IND-CCA security).
Similarly, "RSA" is not an encryption algorithm, but "RSA-OAEP" is.
23.10.2025 08:08 — 👍 1 🔁 0 💬 0 📌 0
Sorry for being so opaque! AES is a block cipher which is modelled as pseudorandom permutation (PRP) or a strong pseudorandom permutation (SPRP). The usual way you are taught that these are not encryption schemes is: "the penguin", see Example 2 in malb.io/7CCSMATC/lec...
22.10.2025 07:53 — 👍 3 🔁 0 💬 1 📌 0
Allan Steel's Homepage
I believe the big pioneer here was Allan Steel magma.maths.usyd.edu.au/users/allan/
21.10.2025 20:39 — 👍 1 🔁 0 💬 1 📌 0
Tools for exact linear algebra
Home page for project LinBox, a library for high-performance exact linear algebraic computations.
Yup, Magma, LinBox, M4RI(E) et al are all running Strassen in dimensions of the hundreds or thousands linalg.org github.com/malb/m4ri but last time I checked this is a no go for floating point matrices due to numerical stability issues with the asymptotically fast algorithms.
21.10.2025 20:38 — 👍 2 🔁 0 💬 1 📌 0
Go ask a room full of cryptography-adjacent practitioners if "AES" or "RSA" are encryption algorithms, I bet you'll hear a lot of "yes" (at least that was the outcome for me today). How many university modules even teach that falsehood? What a failure of our field.
21.10.2025 19:27 — 👍 4 🔁 0 💬 0 📌 0
I was today's years old when I realised that "we" give developers an object called the Advanced Encryption Standard which is not an encryption algorithm (but a pseudorandom permutation) and then we are shocked when we encounter yet another ECB mode in the wild. 🙃
21.10.2025 19:23 — 👍 18 🔁 2 💬 3 📌 0

The Discord Hack is Every User’s Worst Nightmare
A hack impacting Discord’s age verification process shows in stark terms the risk of tech companies collecting users’ ID documents. Now the hackers are posting peoples’ IDs and other sensitive informa...
Discord user IDs getting leaked is the entirely predictable consequence of requiring platforms to do age verification. That data never goes away, it spreads. In this case, into appeals in a breached customer support database. And predictably, it can get worse. www.404media.co/the-discord-...
09.10.2025 19:59 — 👍 6 🔁 4 💬 1 📌 0
On the Virtues of Information Security in the UK Climate Movement | USENIX
New ethnographic work with @rikkebjerg.bsky.social and @malb.bsky.social on information security in the UK climate movement -- accepted and presented recently at USENIX Security ’25 in Seattle 🌱 www.usenix.org/conference/u...
26.08.2025 14:23 — 👍 2 🔁 1 💬 0 📌 0

Screenshot of https://uk-crypto-day.github.io/2025/09/11/uk-crypto-day/ with text:
Rikke Bjerg Jensen & Martin Albrecht: At-Compromise Security: The Case for Alert Blindness
We start from the observation (Blanchette’12) that cryptography broadly intuits security goals – as modelled in games or ideal functionalities – while claiming realism. This stands in contrast to cryptography’s attentive approach towards examining assumptions and constructions through cryptanalysis and reductions. To close this gap, we introduce a technique for determining security goals. Given that games and ideal functionalities model specific social relations between various honest and adversarial parties, our approach is grounded in a careful social science methodology for studying social relations in their contexts: ethnography. As a first application of this technique, we study security at-compromise (neither pre- nor post-) and introduce the security goal of alert blindness. Specifically, as observed in our 2024/2025 ethnographic fieldwork with protesters in Kenya, alert blindness captures a security goal of abducted persons who were taken by Kenyan security forces for their presumed activism. It may have applications elsewhere.
Joint work with Simone Colombo and Benjamin Dowling.
See also: Social Foundations of Cryptography
Bios. Rikke Bjerg Jensen is a Professor in the Information Security Group at Royal Holloway, University of London. Her work is ethnographic and grounded in explorations of information security practices and needs among groups of people living and working at the margins of societies.
Martin Albrecht is a Professor of Cryptography at King’s College London. He works broadly across the field of cryptography but focuses on the analysis of deployed or soon-to-be deployed cryptographic solutions and on analysing the security of lattice-based cryptography against classical and quantum computers.
11 Sep UK Crypto Day in Manchester: uk-crypto-day.github.io/2025/09/11/u...
Together with @rikkebjerg.bsky.social I'll be talking about our upcoming work with @bedow.bsky.social and Simone Colombo: At-Compromise Security: The Case for Alert Blindness
13.08.2025 11:21 — 👍 3 🔁 2 💬 0 📌 0
Slides of my talk titled "Lattices give us KEMs and FHE, but where are the efficient lattice PETs? -- By Example of (Verifiable) Oblivious PRFs" given at spiqe-workshop.github.io are here: github.com/malb/talks/b...
Thanks @kennyog.bsky.social and @jurajsomorovsky.bsky.social for inviting me.
24.06.2025 09:56 — 👍 12 🔁 4 💬 0 📌 0

Abstract. The Unbalanced Oil and Vinegar construction (UOV) has been the backbone of multivariate cryptography since the fall of HFE-based schemes. In fact, 7 UOV-based schemes have been submitted to the NIST additional call for signatures, and 4 of these made it to the second round. For efficiency considerations, most of these schemes are defined over a field of characteristic 2. This has as a side effect that the polar forms of the UOV public maps are not only symmetric, but also alternating.
In this work, we propose a new key-recovery attack on UOV in characteristic 2 that makes use of this property. We consider the polar forms of the UOV public maps as elements of the exterior algebra. We show that these are contained in a certain subspace of the second exterior power that is dependent on the oil space. This allows us to define relations between the polar forms and the image of the dual of the oil space under the Plücker embedding. With this, we can recover the secret oil space using sparse linear algebra.
This new attack has an improved complexity over previous methods and reduces the security by 4, 11, and 20 bits for uov-Ip, uov-III, and uov-V, respectively. Furthermore, the attack is applicable to MAYO₂ and improves on the best attack by 28 bits.

Image showing part 2 of abstract.
Wedges, oil, and vinegar – An analysis of UOV in characteristic 2 (Lars Ran) ia.cr/2025/1143
19.06.2025 00:26 — 👍 6 🔁 4 💬 0 📌 1
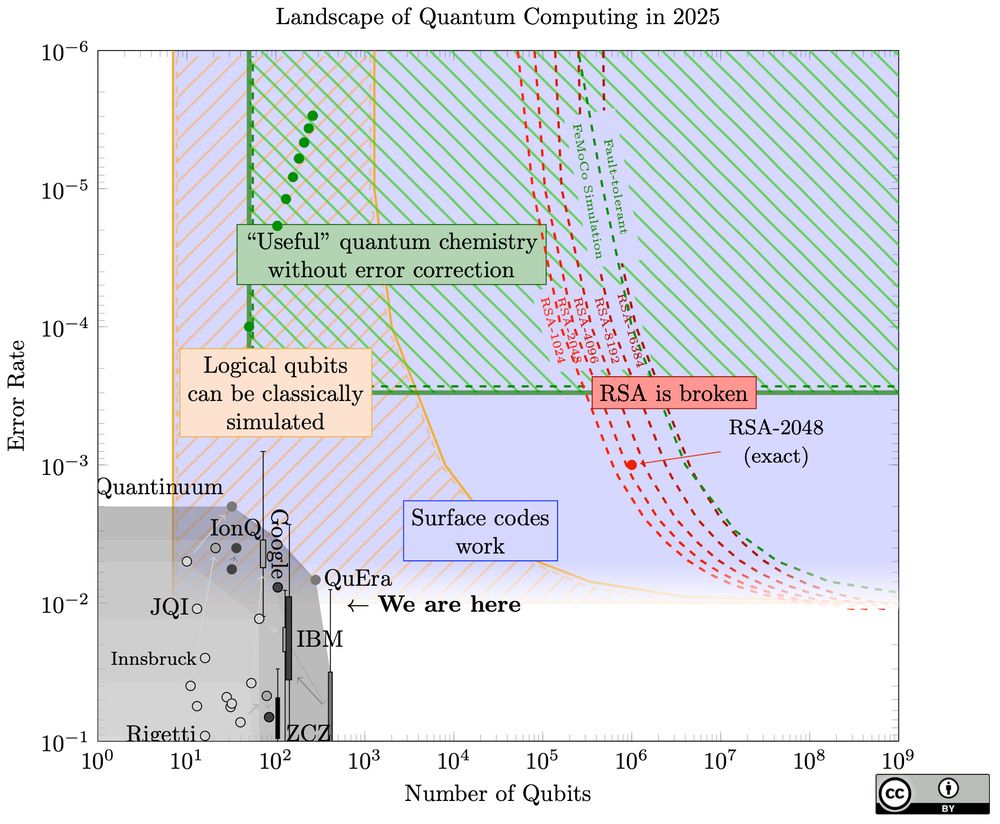
A chart for quantum computers, of number of qubits versus error rate, on a logarithmic scale. Broadly it shows a large gap between current quantum computers in the bottom left, and a curve in the top right of the resources they need to break RSA.
An out-of-schedule update to my quantum landscape chart: sam-jaques.appspot.com/quantum_land..., prompted by
@craiggidney.bsky.social 's new paper: arxiv.org/abs/2505.15917.
A startling jump (20x) in how easy quantum factoring can be!
Also: much improved web design!
19.06.2025 18:52 — 👍 61 🔁 26 💬 3 📌 0
GitHub - malb/lattice-estimator: An attempt at a new LWE estimator
An attempt at a new LWE estimator. Contribute to malb/lattice-estimator development by creating an account on GitHub.
Eamonn and I received a Zama Cryptanalysis Grant to help with the lattice estimator github.com/malb/lattice.... We hope to hire interns to work on the estimator over two periods over the next 18 months.
Zama are still taking applications for this grant, see here: www.zama.ai/post/announc...
04.06.2025 08:26 — 👍 11 🔁 4 💬 1 📌 0
10 June: Jean-François Blanchette Talk and Discussion on "Burdens of Proof" in London
martinralbrecht.wordpress.com/2025/04/15/1...
15.04.2025 19:13 — 👍 1 🔁 3 💬 1 📌 0
Isn't the answer mostly Heartbleed?
15.05.2025 10:09 — 👍 0 🔁 0 💬 1 📌 0
Dan wrote a nice thread about our work on WhatsApp presented at Eurocrypt earlier today and discussed in @dangoodin.bsky.social's article linked below.
08.05.2025 22:07 — 👍 1 🔁 0 💬 0 📌 0
Reporter covering AI for The Guardian. Senior Tarbell Fellow @ Tarbell Center for AI Journalism. SABEW award for international reporting, 2024.
Computer Scientist with particular interest in cyber security & quantum technology.
I work on foundations of #Cryptography at @IRIF in #Paris
Also Free Software Person, #Debian Developer
and long-time #CTF player with #FAUST
[bridged from https://toot.kif.rocks/@siccegge on the fediverse by https://fed.brid.gy/ ]
Professor at Paderborn University, co-founder of Hackmanit. Used to break XML, now playing with TLS and crypto. Co-author of DROWN, EFAIL, and TLS-Attacker.
Cryptography and Privacy @tugraz
heimberger.xyz
Ethnography | Information Security | Interpretivism
Ethnographer exploring contemporary social movements, protest and activism. PhD candidate on the Social Foundations of Cryptography project @royalholloway.bsky.social and
@kingscollegelondon.bsky.social
Website https://cbcrypto.org
Fediverse https://ioc.exchange/@cbcrypto
Vice President/Principal (International) @kingscollegelondon.bsky.social | Professor of Peace, Security, Leadership and Internationalisation of Education | Founding Director of African Leadership Centre @ King's | PhD in War Studies @ King's
Academic @york.ac.uk interested in security & privacy
www.cs.york.ac.uk/~siamak
Board Director @Bigbrotherwatch.bsky.social. ex-Chief Operating Officer @OpenRightsGroup.org. All views my own.
https://www.alghaff.org
I'm a tempura shrimp and you can't catch me! | 🐢 Terrapin Attack | 🦙 ALPACA Attack | 🦝 Raccoon Attack | 😈 DEMONS Attack | @lambdafu@mastodon.social
PhD Student at ETH Zurich, Cryptography and more
Cryptography professor at the University of Waterloo
https://www.douglas.stebila.ca/
【DΞCOMPILΞ NΣVΞR】
Android Red Team @google
Fuzzing @aflplusplus.bsky.social
CTF @enoflag
(opinions my own)
![Abstract. We initiate the study of basing the hardness of hinted ISIS problems (i.e. with trapdoor information, or ‘hints’) on the previously conjectured space-time hardness of lattice problems without hints. We present two main results.
1. If there exists an efficient algorithm for hinted ISIS that outputs solutions a constant factor longer than the hints, then there exists a single-exponential time and polynomial memory zero-centred spherical Gaussian sampler solving hinted SIS with norm a constant factor shorter than the hints.
2. Assume the existence of a chain of algorithms for hinted ISIS each taking as input Gaussian hints whose norms decrease by a constant factor at each step in the chain, then there exists a single-exponential time and polynomial memory algorithm for SIS with norm a quasilinear factor from optimal.
The existence of such hinted ISIS solvers implies single-exponential time and polynomial memory algorithms for worst-case lattice problems, contradicting a conjecture by Lombardi and Vaikuntanathan (CRYPTO’20) and all known algorithms. This suggests that hinted ISIS is hard.
Apart from advancing our understanding of hinted lattice problems, an immediate consequence is that signing the same message twice in GPV-style [Gentry–Peikert–Vaikuntanathan, STOC’08] schemes (without salting or derandomisation) likely does not compromise unforgeability. Also, cryptanalytic attempts on the One-More-ISIS problem [Agrawal–Kirshanova–Stehlé-Yadav, CCS’22] likely will need to overcome the conjectured space-time hardness of lattices.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreib5oxxsmuh3zvn7oz6c2bhusztjf5oyp4aqzn7w7m6kpbphrokiou@jpeg)














