Threat actors are increasingly evolving their attack chains in an attempt to bypass detections and obtain access to organizations.
See our blog for full campaign details and impersonation examples. We also included tips on how to defend against hybrid (email and cloud) threats.
31.07.2025 23:44 — 👍 0 🔁 0 💬 0 📌 0
We first observed this activity in early 2025, and it remains ongoing.
Notably, in July 2025, MSFT announced it is updating M365 default settings in response to the threat. We expect the update will have a positive impact and will disrupt threat actors that use this technique.
31.07.2025 23:44 — 👍 0 🔁 0 💬 1 📌 0
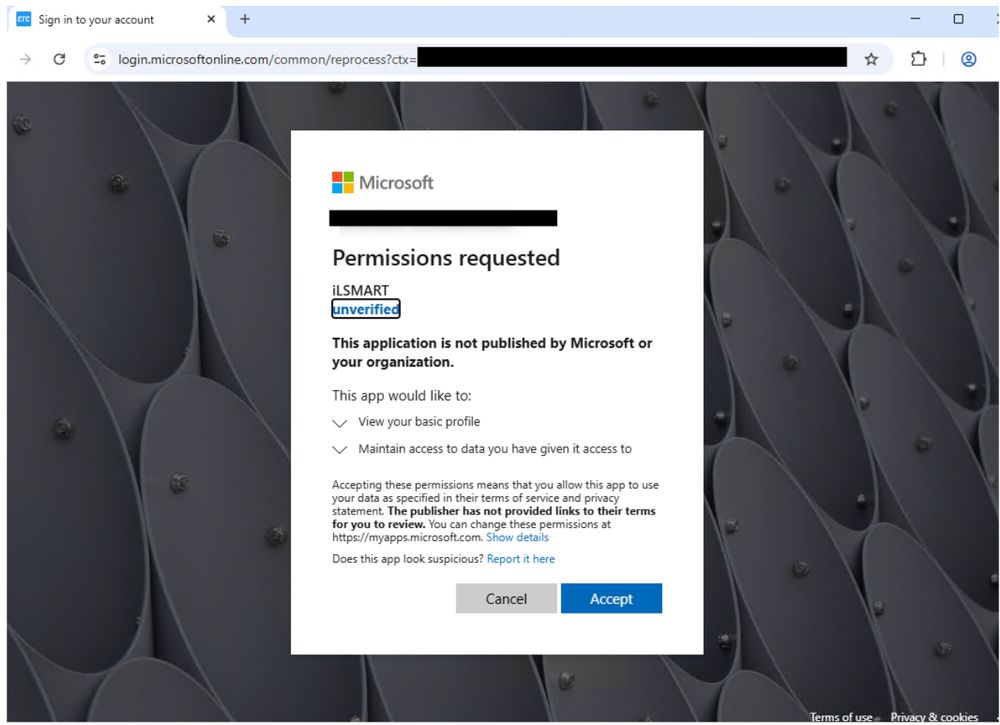
Landing page for requested permissions from malicious OAuth app.
In the email campaigns tracked by Proofpoint, messages are often sent from compromised email accounts and include subjects related to request for quotes or business contract agreements. The campaigns typically include thousands of messages and impact hundreds of customers.
31.07.2025 23:44 — 👍 0 🔁 0 💬 1 📌 0
The goal of the campaigns is to use OAuth applications as a gateway lure to conduct other activities that result in information gathering, lateral movement, follow-on malware installation, or to conduct additional phishing campaigns from compromised accounts.
31.07.2025 23:44 — 👍 0 🔁 0 💬 1 📌 0

Microsoft OAuth App Impersonation Campaign Leads to MFA Phishing | Proofpoint US
Key findings Threat actors are impersonating various enterprises with fake Microsoft OAuth applications to steal credentials. These campaigns bypass multifactor authentication
In a new technical blog, Proofpoint threat researchers detailed their observations of threat actors impersonating well-known enterprises with fake #Microsoft #OAuth applications that redirect to malicious URLs, enabling credential phishing. brnw.ch/21wUA69
31.07.2025 23:44 — 👍 0 🔁 0 💬 1 📌 0

Each threat actor has its own tactics, techniques, and procedures (TTPs).
On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L
29.07.2025 18:46 — 👍 0 🔁 0 💬 0 📌 0
Job seekers are advised to be vigilant about this threat and pay extra attention to the names and sender domains of people contacting them, as they could be impersonated.
If you’re sent an executable file or URL leading to one, it is likely a scam.
24.07.2025 15:41 — 👍 0 🔁 0 💬 0 📌 0
RMM/RAS tooling has become very popular as a first stage payload. Instead of delivering RATs or infostealers, threat actors may use RMMs instead as they can blend in with legitimate traffic. Then, they can steal your money, information, or install more malware.
24.07.2025 15:41 — 👍 0 🔁 0 💬 1 📌 0
This activity is part of a broader set of email campaigns that distribute RMM or remote access software (RAS) tools. We’ve seen emails impersonating U.S. government agencies, party invitations, financial institutions, and more.
24.07.2025 15:41 — 👍 0 🔁 0 💬 1 📌 0
The threat actors may be obtaining target lists in multiple ways: creating fake job postings to collect emails; compromising inboxes or social media of recruiters or hiring managers; or working off a list of previously stolen emails.
24.07.2025 15:41 — 👍 1 🔁 0 💬 1 📌 0
We observed that email address in fraudulent emails sent to people who apparently applied to the job. The person identified the hack and removed the fraudulent posting prior to Proofpoint’s identification.
24.07.2025 15:41 — 👍 0 🔁 0 💬 1 📌 0
In at least one case, Proofpoint found evidence of a hacked LinkedIn account that posted a job description and included a Gmail address impersonating the compromised individual.
24.07.2025 15:41 — 👍 0 🔁 0 💬 1 📌 0
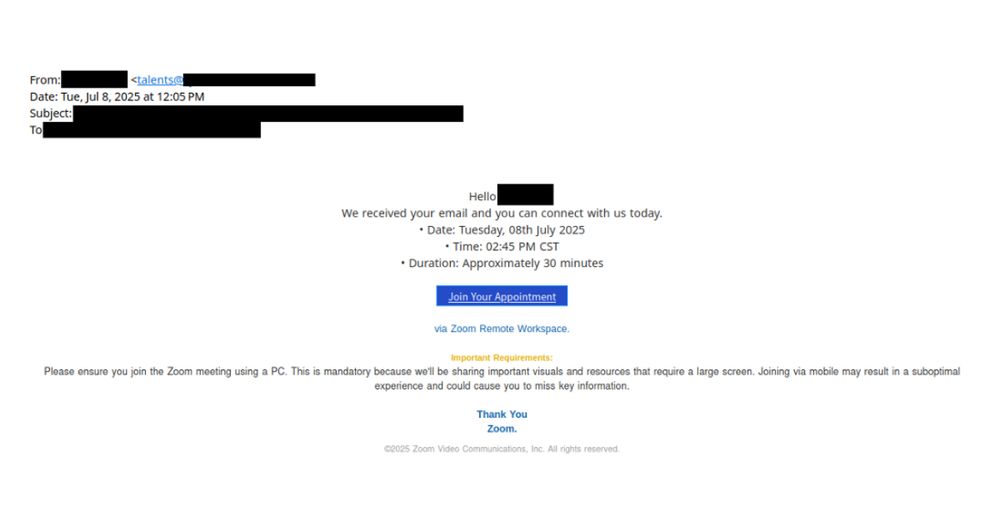
In recent campaigns, emails may be compromised or impersonate real firms. Senders have names associated w/ recruiters or company employees. Email bodies relate to job apps. We were able to identify multiple jobs named in the scam emails that were posted by the impersonated or compromised companies.
24.07.2025 15:41 — 👍 0 🔁 0 💬 1 📌 0
Proofpoint has identified multiple campaigns sending fraudulent emails impersonating job interview invites.
The emails appear to be invitations to a Zoom or Teams call to discuss a job opportunity but really lead to a remote management tool like SimpleHelp, ScreenConnect, or Atera.
24.07.2025 15:41 — 👍 0 🔁 0 💬 1 📌 0
🚨 Job seekers, watch out! 🚨
Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware.
24.07.2025 15:41 — 👍 3 🔁 2 💬 1 📌 1
See our blog for full details on the attack chain and ways to spot a Net RFQ scam.
@threatinsight.proofpoint.com continues to track and block emails associated with these groups, and has partnered with the Proofpoint Takedown Team to remove 19 domains associated with this specific activity.
22.07.2025 15:05 — 👍 0 🔁 0 💬 0 📌 0
The most frequently used companies appear to be shipping forwarding services that specialize in sending goods to West African countries like Nigeria and Ghana.
We also observed these fraudsters utilizing residential addresses to take delivery of the stolen goods.
22.07.2025 15:05 — 👍 0 🔁 0 💬 1 📌 0
We observed that these Net RFQ scams always inquire about Net 15/30/45-day financing.
When a threat actor gets a response from a target, they send all the info needed to process the net financing request.
Multiple attackers offered to truncate the order to speed up the process.
22.07.2025 15:05 — 👍 0 🔁 0 💬 1 📌 0
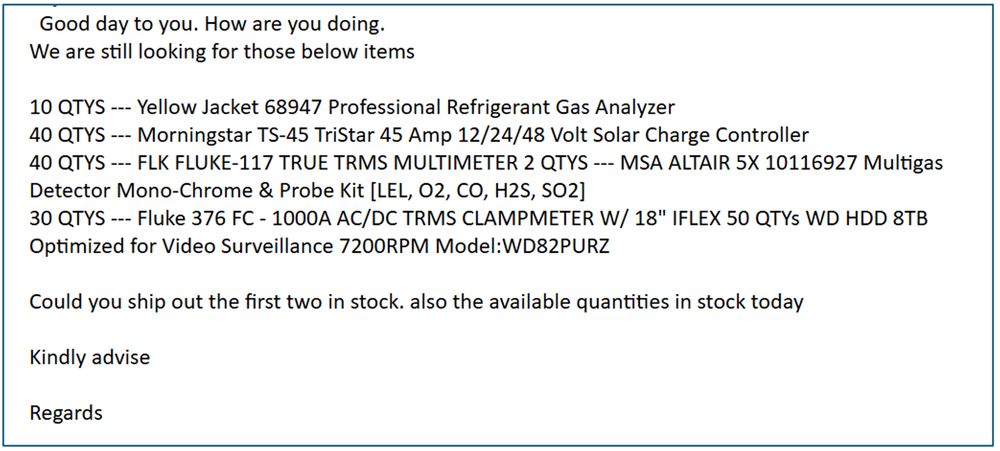
Example item list.
To understand how the scam works, we posed as suppliers with lax #finance departments and engaged directly w/ threat actors.
Many sent quote requests from #freemail accounts, but some used lookalike domains.
The emails typically requested highly specific items (example below).
22.07.2025 15:05 — 👍 0 🔁 0 💬 1 📌 0

NET RFQ: Request for Quote Scammers Casting Wide Net to Steal Real Goods | Proofpoint US
Key findings Request for Quote scammers are using vendor supplied financing to steal physical goods. They utilize email and legitimate online quote request forms to reach
Threat researchers at Proofpoint released new details on a widespread Request for Quote (RFQ) scam that involves leveraging common Net financing options to steal a variety of high-value electronics and goods.
Blog: brnw.ch/21wUkQ8
#shipment #RFQ #finance #scam
22.07.2025 15:05 — 👍 1 🔁 0 💬 1 📌 0
While many established China-aligned threat actors have shifted tactics, techniques and procedures (TTPs) towards the exploiting of edge devices and other initial access vectors, the activity reported shows an influx of new China-aligned clusters into the phishing landscape.
16.07.2025 21:09 — 👍 0 🔁 0 💬 0 📌 0
The infection chains across campaigns were varied, but most used a favorite of Chinese espionage threat groups: DLL sideloading.
Subsequently, custom malware including Voldemort and HealthKick were loaded.
16.07.2025 21:09 — 👍 0 🔁 0 💬 1 📌 0
The campaigns used a mix of lures: fake job offers, phony collaboration proposals, and security alerts.
Attackers often relied on compromised university accounts and custom Adversary-in-the-Middle (AiTM) frameworks to bypass defenses.
16.07.2025 21:09 — 👍 0 🔁 0 💬 1 📌 0
Between March and June 2025, at least three distinct China-aligned threat actors—UNK_FistBump, UNK_DropPitch, and UNK_SparkyCarp—conducted targeted phishing campaigns against chip manufacturers, testing facilities, design firms, supply chain vendors, and investment banks.
16.07.2025 21:09 — 👍 1 🔁 0 💬 1 📌 0
NEW ‼️ Researchers at @Proofpoint revealed an increase in China-aligned cyber #espionage targeting Taiwan’s #semiconductor industry—a sector critical to the global tech #supplychain.
At least 3️⃣ distinct China-aligned threat actors are behind the efforts. brnw.ch/21wUctY
16.07.2025 21:09 — 👍 8 🔁 5 💬 1 📌 1
⚠️ This real-world #phishing example shows how attackers attempt to masquerade as reputable entities to mislead users into performing specific actions.
Proofpoint cybersecurity experts recommend training users to recognize the warning signs to defend against phishing.
01.07.2025 16:30 — 👍 0 🔁 0 💬 0 📌 0
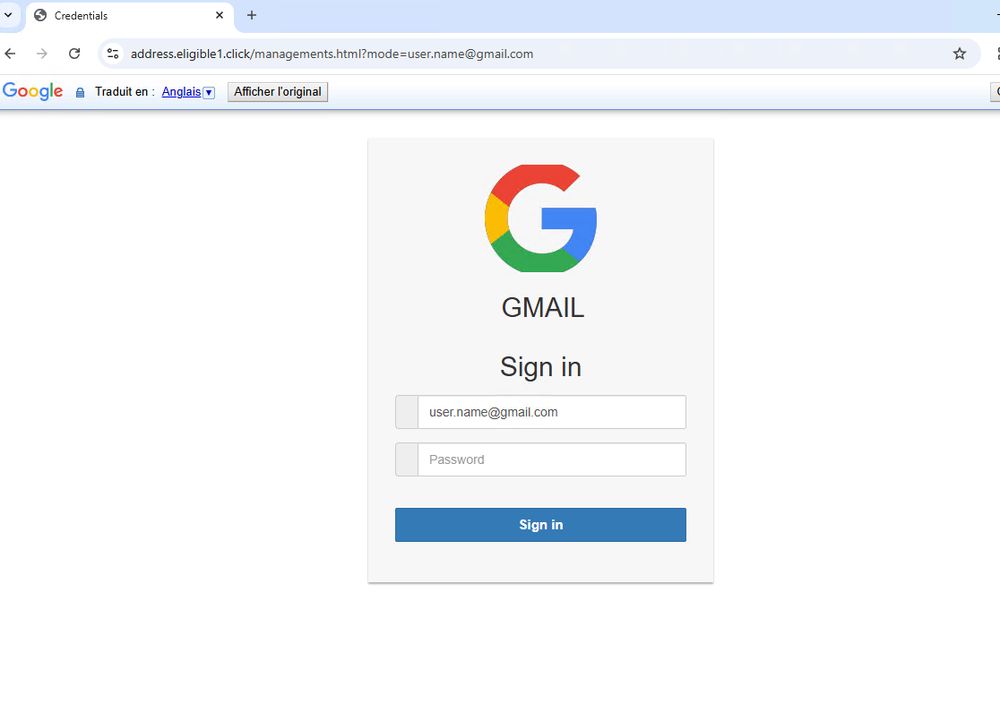
Example of credential harvesting page
Below the sender’s signature is hyperlinked text purporting to be an “unsubscribe” option for recipients to remove themselves from the mailing list.
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
01.07.2025 16:30 — 👍 0 🔁 0 💬 1 📌 0
In early May, Proofpoint researchers observed a campaign purporting to be from an asset management firm in Hong Kong.
The message called for opportunities for private loans and capital partnerships, and invited recipients to respond, if interested.
01.07.2025 16:30 — 👍 0 🔁 0 💬 1 📌 0
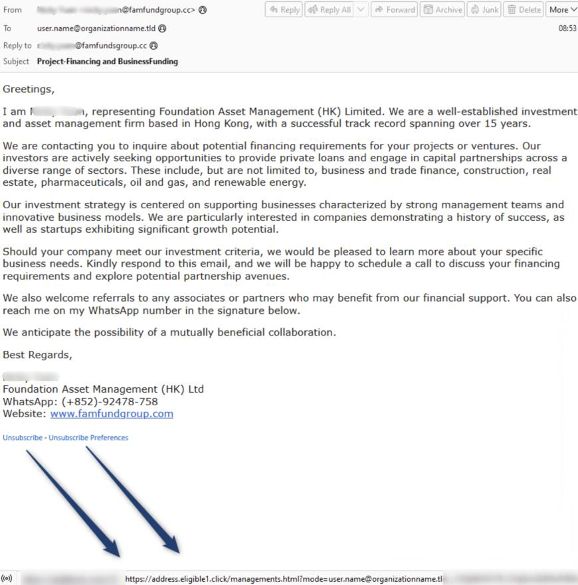
Message sample showing "unsubscribe" link in signature
Confirm before you click! 🖱️
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
01.07.2025 16:30 — 👍 1 🔁 1 💬 1 📌 0








