Hi
11.09.2025 13:09 — 👍 0 🔁 0 💬 0 📌 0Haag
@mhaggis.bsky.social
Just a person hacking away.
@mhaggis.bsky.social
Just a person hacking away.
Hi
11.09.2025 13:09 — 👍 0 🔁 0 💬 0 📌 0
🚨 Still on your journey to mastering ASR rules?
Don’t sleep on ASRGEN 🛡️💥
⚡ Point. Click. Generate ASR rules.
🔍 Learn + test safely with built-in atomic simulations
📦 Export to Intune/GPO-ready formats
🎯 Built for defenders, by defenders
👀🔥
👉 asrgen.streamlit.app
📚 github.com/MHaggis/ASRGEN

🆕🐇 Just dropped a 1-hour rabbit hole dive into API playgrounds, mocks, & random nerdy finds 🤓
We started with ClickGrab, but then it turned into:
🐝 Beeceptor
🛠️ Mockbin
🧩 Zudoku
🔍 VirusTotal hunts
🤖 ChatGPT making OpenAPI bins & routes
Chaotic, nerdy, fun. Come hang out 👉 youtu.be/j7QE-6p9Y9Q
Minted narwhal!
I am/was burnt sienna goose

🚨 New ASR rules are now GA:
❌ Block rebooting in Safe Mode
🕵️♂️ Block copied/impersonated system tools
ASRGEN had these since preview. 😎
Want to:
⚡ Quickly create Intune-ready ASR policies
🧪 Simulate and understand rule impacts
Check → asrgen.streamlit.app
Be proactive. Be precise.

💰 The hunt begins…
The first drops for PowerShell-Hunter: Season 2 are coming SOON.
New tools. Smarter hunting. Sexier telemetry.
This isn’t just DFIR—it’s an evolution.
⚔️ Hunt smarter. Hunt harder.
⭐ github.com/MHaggis/Powe...

🚨 PowerShell-Hunter Season 2 is coming 🚨
💥 More atomic tools
🧬 Smarter, faster log analysis
🤖 Machine learning meets lateral movement
😈 PowerShell so slick it should be illegal
You’re not ready—but you should be.
⭐ Star the repo or miss the magic:

🎉 Exciting News: PCA Analyzer is now part of the PowerShell-Hunter suite! 🚀
Check it out on GitHub: github.com/MHaggis/PowerShell-Hunter 💻
📺

🎥 Want a deeper dive? Check out Atomics on a Friday, where we introduce SDDLMaker!
▶️ https://www.youtube.com/watch?v=uSYvHUVU8xY
🔄 RT/Reshare if you find this useful! 🚀
#WindowsSecurity #SDDL #Cybersecurity #Splunk #AtomicRedTeam
🛠️ Splunk Security Content:
🔗 https://research.splunk.com/stories/defense_evasion_or_unauthorized_access_via_sddl_tampering/
🧠 Mind Map:
🔗 https://github.com/MHaggis/SDDLMaker/tree/main/MindMap
🧵 (5/)

💡 Need to decode or generate SDDL? Try SDDLMaker 🔧
👉 https://thesddlmaker.streamlit.app/
📜 Read the full blog:
🔗 https://www.splunk.com/en_us/blog/security/windows-security-sddl-guide-access-control.html
🧵 (4/)
Top 3 Things You'll Learn:
1️⃣ How attackers exploit SDDL—event log tampering, service hardening, & more
2️⃣ How to decode SDDL strings & analyze permissions, DACLs, and ACEs
3️⃣ How to defend against SDDL abuse with detections & Atomic Red Team tests
🧵 (3/)
In our latest blog, we break down SDDL: 🔹 How it structures Windows security
🔹 How attackers—from LockBit to RomCom—manipulate it for privilege escalation & defense evasion
🔹 How to detect & defend 🛡️
🧵 (2/)
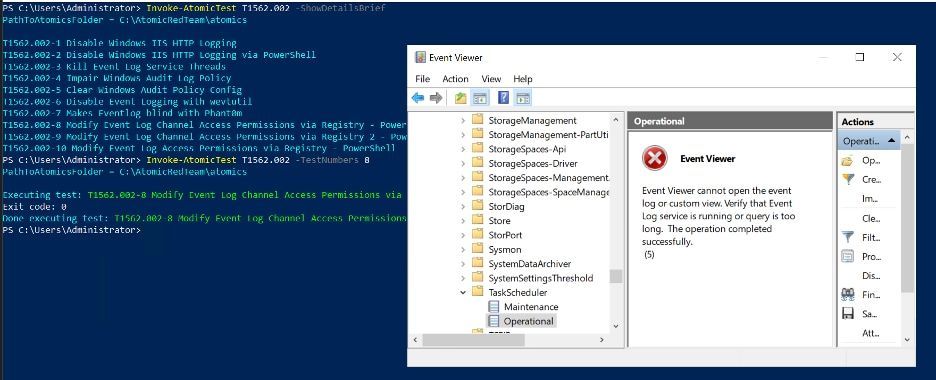
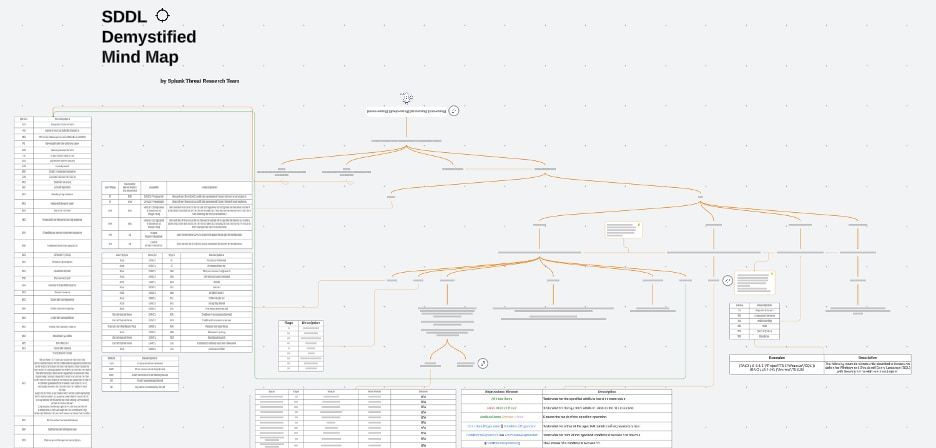
🔐 Windows Security and SDDL: What You Need to Know 🔐
Windows permissions misconfigurations are a goldmine for attackers. SDDL (Security Descriptor Definition Language) remains overlooked yet highly exploitable. 🚨
@nasbench.bsky.social and I break it down -->
🧵 (1/)
Tomorrow, join us for a legendary episode of Atomics on a Friday featuring Jonathan Johnson (@jsecurity101) as we dive deep into JonMon—the tool redefining Windows telemetry!
24.01.2025 03:02 — 👍 1 🔁 0 💬 0 📌 0
🎄 Twas the night before JonMon, and all through the net,
🔍 Defenders were stirring, their systems to vet.
🛠️ The telemetry was hung in EventViewer with care,
✨ In hopes that Jonny Johnson soon would be there.
📅 Friday, January 24th
⏰ 11 AM MST | 1 PM EST
📺
YouTube: youtube.com/watch?v=CqEhtg…
I got you!
13.12.2024 01:18 — 👍 0 🔁 0 💬 0 📌 0
Down to the end of my last Christmas blend, what do you recommend this holiday season? I typically get Red Rooster or Atomic.
www.redroostercoffee.com/products/goo...
atomicroastery.com/products/mer...

Happy Monday
02.12.2024 18:04 — 👍 2 🔁 0 💬 0 📌 0
🔥 Tools for Testing:
➡️ Apache Builder: https://buff.ly/4fOt8F9
➡️ IIS Builder: https://buff.ly/4fLGySm
Empower your security team to hunt, detect, and patch gaps before attackers exploit them. 🛡️
Test, learn, and refine! #CyberSecurity #ThreatHunting #WebShellDetection

💻 How to Use:
1️⃣ Deploy your favorite tools (Sysmon, EDR, XDR, etc.)
2️⃣ Grab a webshell of choice, upload it, and start testing!
3️⃣Observe logs, alerts, and behaviors to identify gaps in your coverage.

🔍 Detection Opportunities:
Use these servers to validate analytic coverage for:
🗂️ File modifications (webshell uploads)
⚙️ Process executions (commands from shells)
🎯 Suspicious behaviors triggered by shells


💡 Webshell Testing for Defenders 💡
Having automated tools to spin up web servers isn’t just convenient—it’s a game-changer for defenders. Here's why:

🚨 Unlocking the Secrets of Braodo Stealer! 🚨
Dive into our latest blog where the Splunk Threat Research Team dissects the elusive Python malware and its sneaky obfuscated loader! 🐍🔍✨
🔓 Cracking the code of Braodo Stealer's obfuscation

"Things that get built on a Monday... 🤔
"'Haag do you have a easy way to build a Apache|NGINX|IIS server to easy simulate webshells?'
Hold my coffee... ☕
• 5-min Apache+PHP setup 🚀
• Drop-in webshell support 🎯
See you Tuesday! 😎

⚛️ Blast from the past Atomics on a Friday ⚛️
Attackers are weaponizing IIS modules for persistence, post-exploitation, and data theft.
Check out the blog + AOAF for more 🔥:
https://buff.ly/40UUWAI
Don’t wait—watch to strengthen your defenses:

🌟 Living off GitHub: The Stargazers Ghost Network!🌐
🔥 I somehow missed this, but WOW—what a fascinating deep dive into a DaaS operation! 🚀 Fully automated, primed for quick Ops, and makes you wonder about the ones we haven’t uncovered yet. 👀
https://buff.ly/3LCYEIP 🚨