
The disruption of the XSS cybercrime forum marked one of the most significant events in cybercrime in 2025. Here's an assessment its future from Intel 471's research and analysis teams:
www.intel471.com/blog/after-d...
@intel471.bsky.social
Intel 471 specializes in delivering intelligence related to threat actors, threat hunting, financial cybercrime, ransomware, vulnerabilities, malware and underground marketplaces. Listen to our podcast, Cybercrime Exposed, on Spotify and Apple. #infosec

The disruption of the XSS cybercrime forum marked one of the most significant events in cybercrime in 2025. Here's an assessment its future from Intel 471's research and analysis teams:
www.intel471.com/blog/after-d...

A new episode of our Cybercrime Exposed podcast is out! DukeEugene is a Russian Android malware dev who has a big problem, and he puts everything on the line to solve it. Link to pod here: www.intel471.com/resources/po...
20.08.2025 03:12 — 👍 1 🔁 0 💬 0 📌 0
Jacob Larsen is an #infosec pro who was involuntarily pulled into the dark world of doxing. Intel 471's latest Studio 471 podcast speaks with Jacob about doxing's effects, how sites like Doxbin exploit legal loopholes and how to defend against being doxed.
www.youtube.com/watch?v=y5AO...

Pro-Russian hacktivism campaigns continue to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks. #infosec intel471.com/blog/pro-rus...
04.07.2025 14:20 — 👍 0 🔁 0 💬 0 📌 0
The Black Basta ransomware gang contracted a person with the nickname Tinker. Tinker came from Conti and had a knack for running call centres, writing phishing emails and ransom negotiations. More here from Intel 471's Adversary Intelligence team. intel471.com/blog/a-look-...
23.06.2025 08:15 — 👍 1 🔁 2 💬 0 📌 0
Law enforcement has smashed DanaBot, a data-stealing workhorse administered in Russia and sold to cybercriminals that also had a second, side version likely used for nation-state cyberespionage. Here's Intel 471's in-depth look at its operations. #infosec
intel471.com/blog/danabot...

Russian man Andrei Tarasov was indicted on cybercrime charges related to the Angler exploit kit. He was arrested in Germany but slipped away to Russia — despite his anti-Russian views. Research by @intel471.bsky.social #infosec intel471.com/blog/how-an-...
15.05.2025 23:11 — 👍 0 🔁 0 💬 0 📌 0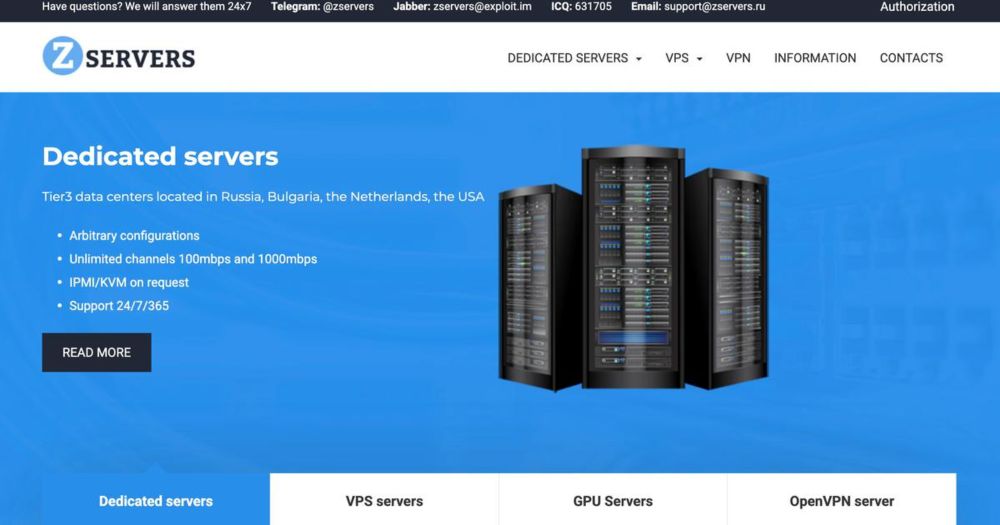
Russia-based bulletproof hosting service Zservers was breached, doxxed and sanctioned, but there are signs this cybercrime and ransomware service provider may not be finally done. New research from Intel 471. #infosec intel471.com/blog/zserver...
12.03.2025 01:04 — 👍 3 🔁 4 💬 0 📌 0Cheers, Davey!
01.03.2025 06:43 — 👍 1 🔁 0 💬 0 📌 0
The Black Basta data leak exposed critical details about how this damaging ransomware gang operated, including how its top member claims to have eluded law enforcement. New blog here: intel471.com/blog/black-b... #infosec
01.03.2025 06:41 — 👍 1 🔁 1 💬 0 📌 1
DeepSeek is just the start. China has approved more than 117 LLMs since August 2023 that are all rapidly maturing in capability. Intel 471's Analysis and Cyber Geopolitical Intelligence teams explain here what this means for enterprise risk. #infosec intel471.com/blog/does-de...
10.02.2025 21:43 — 👍 2 🔁 0 💬 0 📌 0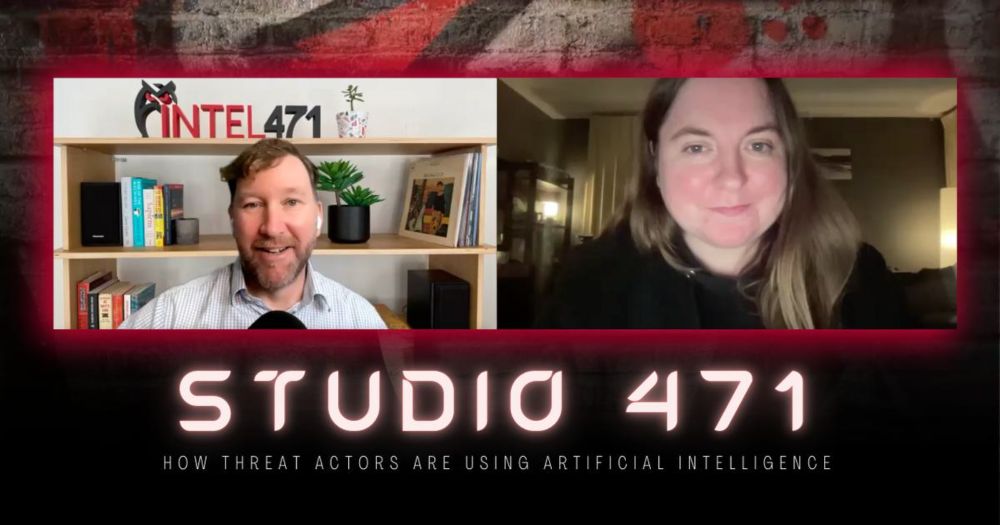
Intel 471's very own Senior Intelligence Analyst Ashley Jess has been closely following cybercriminal use and interest in AI. This was a pre-record before DeepSeek popped but it is a great discussion about the potential threats and risks. #infosec intel471.com/blog/how-thr...
10.02.2025 21:07 — 👍 3 🔁 0 💬 0 📌 0Clop, a ransomware/extortion group that targets file transfer systems, revealed the names of 59 businesses that allegedly were impacted by the Cleo vulnerabilities and refused to pay. The group claimed their data will be publicly released on Saturday, with another list to come on Tuesday. #infosec
15.01.2025 23:33 — 👍 0 🔁 0 💬 0 📌 0
Ep. 8 of @intel471.bsky.social's Cybercrime Exposed podcast covers Raccoon Stealer, which was a popular and damaging infostealer. But its operator made a critical OPSEC error. Thanks to @crep1x.bsky.social of @sekoia.io. #infosec Full series on Apple and Spotify.
intel471.com/resources/po...
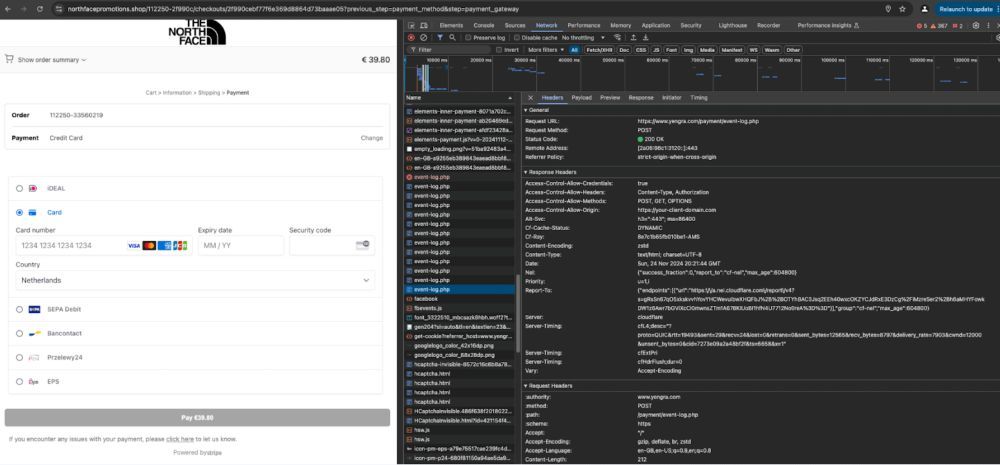
These phishing sites, which then harvest personal and financial data, lure people with too-cheap products. Intel 471 saw one campaign that created at least 20 fake sites for a major outdoor retailer. Entered data is sent off to a domain registered with a Chinese registrar. #infosec
29.11.2024 07:25 — 👍 3 🔁 0 💬 0 📌 0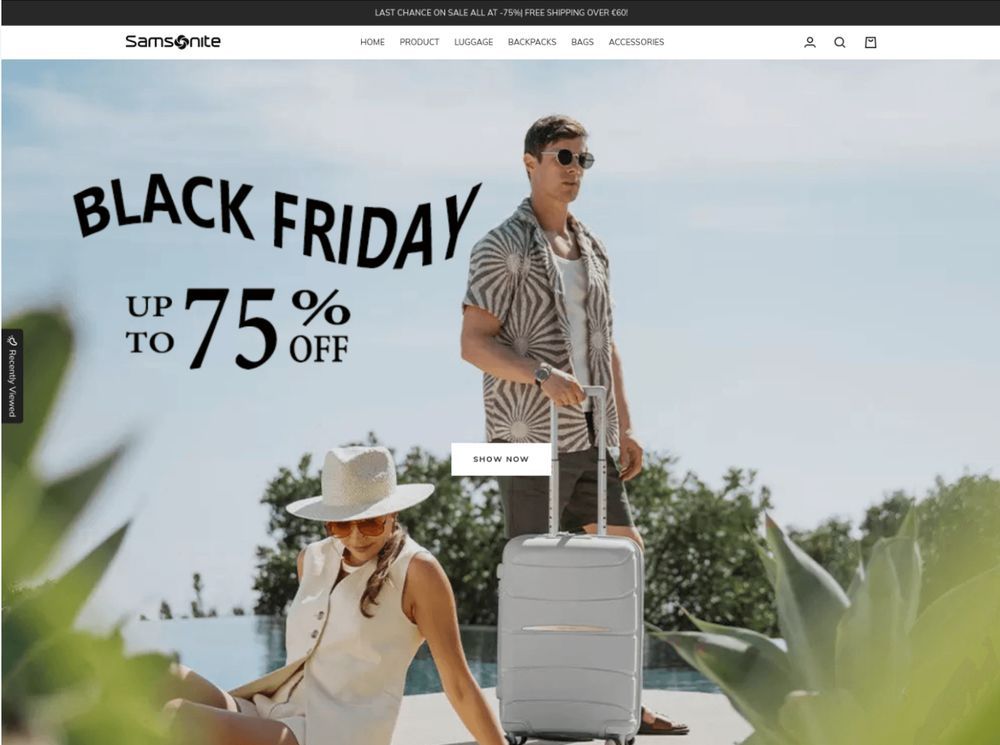
Hundreds of fake websites have been registered over the last few days spoofing real brands containing "Black Friday" related keywords. These sites are often promoted through SEO tricks and search engine/social media ads. This one was at samsoniteblackfriday[.]shop.
#infosec

The breaches linked to customers of Snowflake marked one of the largest data breach waves of 2024. One of the alleged threat actors has been arrested in Canada. This blog is a deep dive into the Com-related threat actor "waifu" or @judische. #infosec
intel471.com/blog/how-to-...

Adversaries try to hide malicious components by renaming them as legitimate Windows binaries. This technique has been used by the Turla threat actor group and others. Here's how to threat hunt for this behavior. #infosec intel471.com/blog/threat-...
28.11.2024 05:27 — 👍 1 🔁 0 💬 0 📌 0
Will processing cyber threat intelligence become illegal? Here's a discussion with professor Peter Swire about how data protection schemes can potentially clash with better cybersecurity defences. This is part of @intel471.bsky.social's interview series. #infosec intel471.com/blog/will-pr...
23.10.2024 22:36 — 👍 0 🔁 0 💬 0 📌 0
We're fielding questions about how Telegram's pledge to turn over phone numbers and IP addresses under valid legal orders will impact visibility into cybercrime. Here's our assessment: intel471.com/blog/are-tel... #infosec
02.10.2024 23:29 — 👍 0 🔁 0 💬 0 📌 0
Russia is a hotbed of cybercriminal activity. Intel 471's Studio 471 podcast spoke with Alec Jackson, an analyst for the U.S. Department of Defense, about why and what the West could do to try to deter it. His answers may surprise.
intel471.com/blog/why-rus...

Here is Intel 471's analysis of what effect France's action against Telegram will have on cybercriminal use of the platform, which has been rising for a number of years for a number of reasons. #infosec
intel471.com/blog/france-...

@intel471.bsky.social's Cybercrime Exposed podcast is back! It's a wild episode about Vyacheslav Penchukov aka "Tank," a Ukrainian threat actor who ran a gang that made at least $70 million through truly organized cybercrime. intel471.com/blog/cybercr...
20.08.2024 05:09 — 👍 0 🔁 0 💬 0 📌 0
Intel 471 collaborated with great minds in the CTI industry to develop the Cyber Threat Intelligence Capability Maturity Model. It's a methodical way to build a CTI program that establishes focus, satisfies stakeholders and improves security outcomes. intel471.com/blog/introdu...
08.08.2024 04:19 — 👍 1 🔁 0 💬 0 📌 0
Intel 471 analyzed recent phishing campaigns by ATLAS LION, a group that specializes in compromising companies gift-card issuing systems. This group is skilled at attacker-in-the-middle phishing, spoofing IDPs and navigating cloud infrastructure.
intel471.com/blog/threat-...

Our intelligence analysis team has written a cyber threat assessment of the Paris Olympic Games, covering how the Games could be impacted hacktivism, nation-state actors, ongoing geopolitical turmoil and financially motivated threat actors.
intel471.com/blog/cyber-t...
What lies ahead now after law enforcement's epic p0wning of LockBit, the No. 1 ransomware gang? Here's an analysis from Intel 471's great intelligence team. #infosec
intel471.com/blog/what-li...

Australia accused 33-year-old Russian Aleksandr Ermakov of the Medibank data breach and extortion attempt. Intel 471 has compiled a profile of Ermakov and his long-known links to cybercrime and ransomware. It's a good read. #infosec
intel471.com/blog/mediban...

@x25princess.bsky.social is a social engineer and red teamer. She does discreet Wi-Fi scans, tries to get into buildings and does USB drops. Would you fall for the tricks? Listen to Ep. 3 of @intel471.bsky.social's Cybercrime Exposed podcast. #infosec
intel471.com/blog/cybercr...

Malaysian police have disrupted a massive phishing-as-a-service operation that was the focus of Ep. 1 of our Cybercrime Exposed podcast. Here's the low-down on the threat it posed for enterprise security. #infosec intel471.com/blog/malaysi...
09.11.2023 22:41 — 👍 1 🔁 1 💬 0 📌 0