
What an honor to share our talk on “In-the-Wild Abuse of App Misconfigs” at @districtcon.bsky.social year 0! So much talent in one place, and massive kudos to the organizers for creating such an epic event and overcoming an entire-block power outage. Looking forward to next year! 🪩✨🌸
24.02.2025 15:33 — 👍 9 🔁 2 💬 1 📌 0
Moreover, I’ve come across these misconfigs in prod envs - this is far from hypothetical.
Exposed secrets like cloud keys or DB credentials are practically gift-wrapped for attackers. And since using valid creds doesn’t raise alarms, these threats quietly slip under the radar.
16.12.2024 20:14 — 👍 0 🔁 0 💬 1 📌 0

Exposed env endpoint – the following example shows exposed env endpoint leaking DB login credentials and endpoint information:
16.12.2024 20:14 — 👍 0 🔁 0 💬 1 📌 0

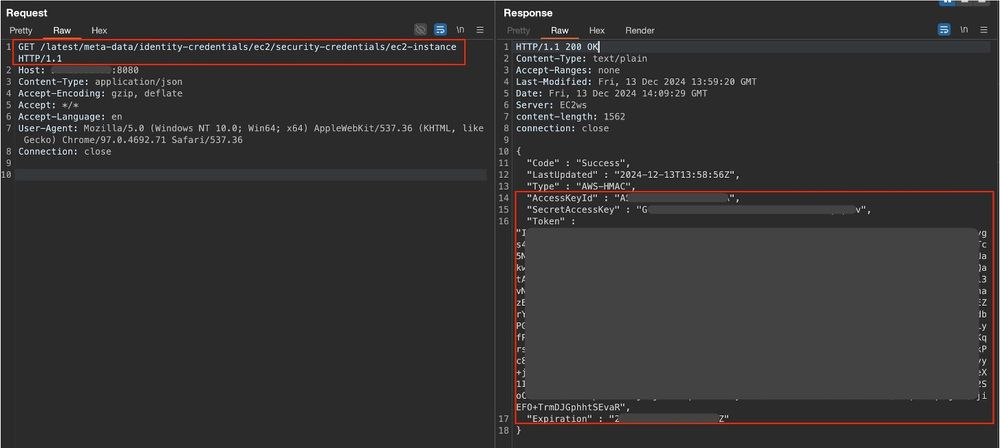
Even without CVE-2022-22947, exposing the gateway endpoint leads to SSRF by design, as it allows creating new routes. This enables attackers to access for example - cloud metadata services (IMDSv1), and other sensitive resources.
Here's an SSRF example with IMDSv1 configured VM:
16.12.2024 20:14 — 👍 0 🔁 0 💬 1 📌 0


Spring Cloud Gateway versions 3.1.0, 3.0.0–3.0.6, and older are vulnerable to RCE (CVE-2022-22947). According to Wiz data, 28% of cloud environments using Spring Cloud Gateway are at risk. Exploitation requires misconfiguration exposing the gateway endpoint.
16.12.2024 20:14 — 👍 0 🔁 0 💬 1 📌 0

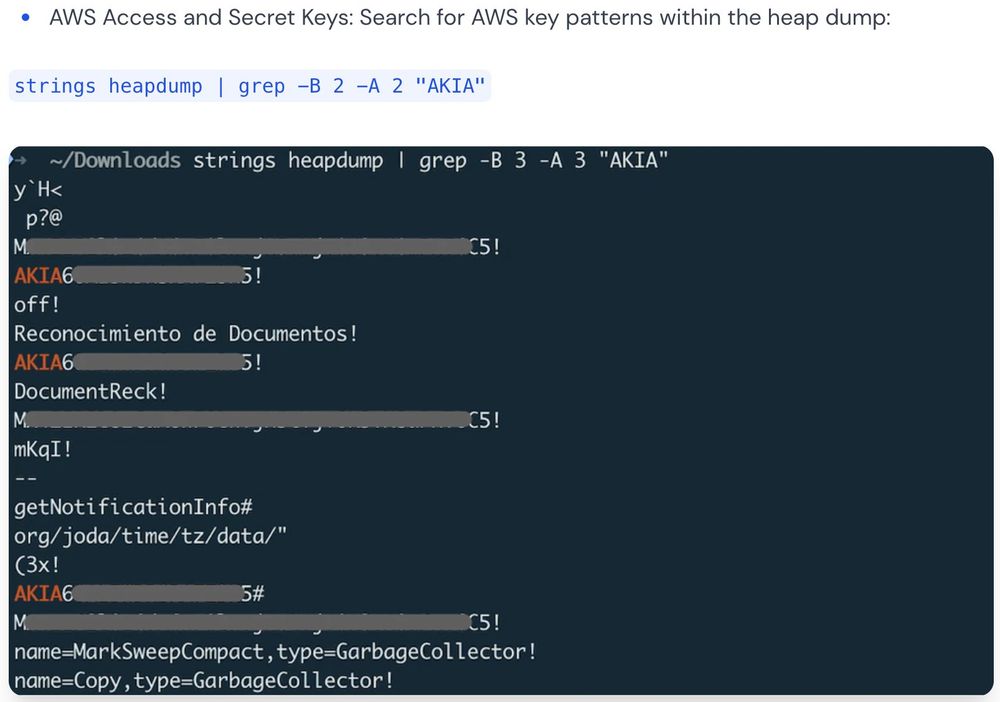
The heapdump endpoint is designed to capture the current state of the Java heap - if sensitive information is loaded into the memory of a Java application’s JVM during its runtime, these might be included in the heap dump. Here's an example of a heap dump showing a leaked JWT.
16.12.2024 20:14 — 👍 1 🔁 0 💬 1 📌 0
Spring Boot Actuator is a key observability tool for Java apps, found in 60% of cloud envs. When misconfigured to expose sensitive endpoints it al leak data (API key, tokens, passwords) or even allow RCE. Watch out for exposed endpoints like: heapdump, env and gateway
16.12.2024 20:14 — 👍 1 🔁 0 💬 1 📌 0
I was looking into how organizations deploy Spring Boot Actuator in the cloud and found 1 in 4 exposed Actuators had security flaws leading to data leaks or RCE. These risks are more common than you'd think..⚠️
16.12.2024 20:14 — 👍 6 🔁 2 💬 1 📌 0
Now Google Threat Intelligence & doing fun things at DistrictCon, fmrly GreyNoiseIO and RecordedFuture, SAISHopkins MASCI alumna | ♡s & rts are my own, my employer definitely doesn’t like Taylor Swift that much
A new DC hacker conference: Bringing together builders, breakers, and fixers to do cool shit.
Jan. 24-25, 2026
districtcon.org
Staff Security Researcher @datadoghq | DEF CON/Black Hat USA main stage speaker | he/him | OSCP OSWE | I turned hacking AWS into a career | Tweets are my own | Created https://hackingthe.cloud
Snarkmonger. Chief Cloud Economist at The Duckbill Group.
he/him.
Get my opinionated take on AWS news: http://lastweekinaws.com/t/
Signal: 833-AWS-BILL (833-297-2455)
personal website @ cloudcurio.us ✦ researching @ Wiz Security (threats.wiz.io) 🐞 maintaining @ cloudvulndb.org 🎙️ podcasting @ cryingoutcloud.io 🗺️ pivoting @ Pivot Atlas (gopivot.ing)








