
As you're planning your week, be sure to sign up for our Red Canary webinar on initial access to hear about common adversary techniques and what to do about them. redcanary.com/resources/we... Don't miss it!
27.05.2025 13:17 — 👍 6 🔁 1 💬 0 📌 0@forensicitguy.bsky.social
Recovering sysadmin that now chases adversaries instead of uptime. Sr Malware Analyst @redcanary

As you're planning your week, be sure to sign up for our Red Canary webinar on initial access to hear about common adversary techniques and what to do about them. redcanary.com/resources/we... Don't miss it!
27.05.2025 13:17 — 👍 6 🔁 1 💬 0 📌 0
Do you miss "@cobaltstrikebot"? If so, here's a blog post showing how you can pull Cobalt Strike SpawnTo and watermark info with @shodanhq.bsky.social and some PowerShell: forensicitguy.github.io/squeezing-co...
19.05.2025 01:38 — 👍 11 🔁 6 💬 0 📌 0
A fun yearly endeavor for me is contributing to the Red Canary Threat Detection Report, and the 2025 edition is out today! distilled into one report!
Get your free copy of our 2025 Threat Detection Report now. ⬇️
#ThreatReport #SecOps #ThreatIntel
redcanary.com/threat-detec...
"For what it's worth, the curl by itself is likely safe. It's the chmod and nohup bash after it that are the problem"
I saw this on a forum post today, and I swear it's the macOS/Linux version of "it's not the fall that kills, it's the impact"
I am working on a public platform to make it even easier for people to report code-signing certificates.
My goal is to continue to raise awareness on the abuse and the impact revocation has on malware distributors. Keep an eye on my socials for more news.
New blog post for #100DaysofYARA , in this one I look at a VenomRAT sample and create rules based on PE metadata and an encryption salt value.
forensicitguy.github.io/exploring-ve...
#malware
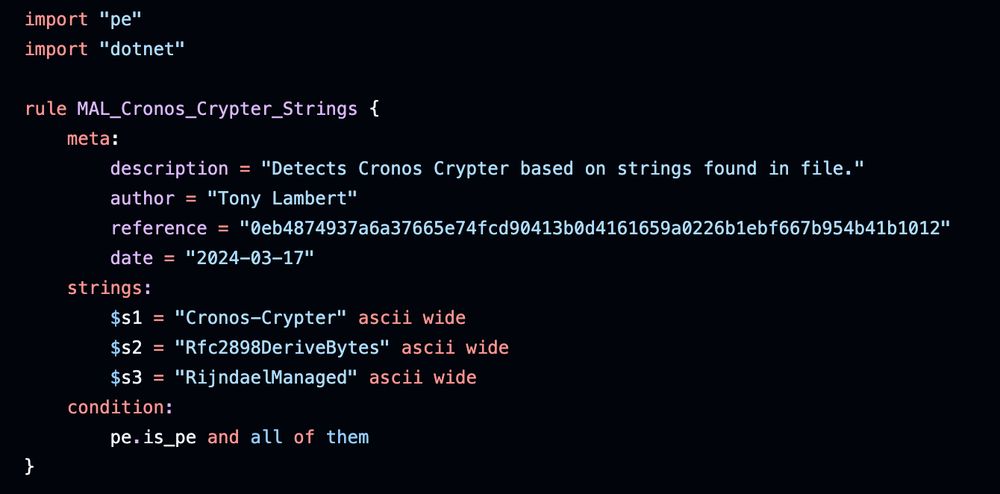
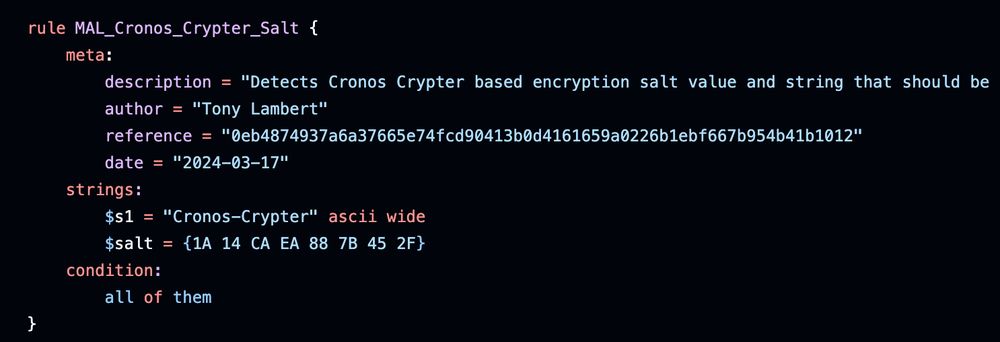
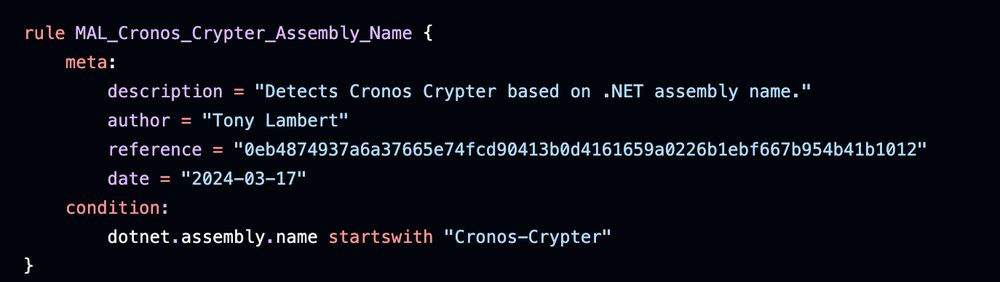
#100daysofyara I like taking the approach of having multiple YARA rules to detect the same thing from different perspectives, like these rules for Cronos Crypter. One looks for just strings, another a string + encryption salt, 3rd for assembly name
02.01.2025 04:30 — 👍 8 🔁 3 💬 0 📌 0
Mastercard Completes Acquisition of Cybersecurity Firm Recorded Future for $2.6 Billion
21.12.2024 19:56 — 👍 5 🔁 3 💬 0 📌 1



2024-12-13 (Friday): www.anceltech[.]com compromised with #SmartApeSG leading to #NetSupport #RAT 2 injected scripts. jitcom[.]info and best-net[.]biz.
Pivoting on best-net[.]biz in URLscan show signs of six other compromised sites: urlscan.io/search/#best...
#NetSupportRAT

Malicious Google ad for PayPal
⚠️
https[:]//sites[.]google.com/view/pay-pal-helpcustomerservic/
#malvertising

Join @olafhartong.nl in his journey down the rabbit hole in search of new detection opportunities in the #Zeek telemetry embedded in Microsoft's EDR #MDE! Detection engineering is sometimes hard … 😎
falconforce.nl/detection-en...
#detectionengineering #kql #blueteam

Hackers Use Corrupted ZIPs and Office Docs to Evade Antivirus and Email Defenses
04.12.2024 05:45 — 👍 5 🔁 2 💬 0 📌 0
Veeam Issues Patch for Critical RCE Vulnerability in Service Provider Console
04.12.2024 05:45 — 👍 1 🔁 1 💬 0 📌 0
China-linked APT Gelsemium uses a new Linux backdoor dubbed WolfsBane
23.11.2024 13:21 — 👍 5 🔁 1 💬 0 📌 0certReport 3.1.4
Bugfix - indicators could be printed in duplicate
certReport makes reporting code-signing certs easy. No-one likes spending time reading or writing reports. That is: I just noticed the problem. Maybe someone else did. I don't know. It is gone now.

More PRC telecom shenanigans. I'd love to say that this sector is so hot right now, but it's always been hot. www.crowdstrike.com/en-us/blog/l...
19.11.2024 17:16 — 👍 20 🔁 4 💬 1 📌 0Reminder that in Feb I will teach a special, extended version of my #CTI + #DetectionEngineering & #ThreatHunting course with #OTsecurity examples and case studies at the #S4x25 conference!
s4xevents.com/s4x25-traini...

May 13, 2024 blogpost
It is common for malware to be signed with code signing certificates.
How is this possible? Impostors receive the cert directly and sign malware.
In this blog-post, we look at 100 certs used by #Solarmarker #malware to learn more.
squiblydoo.blog/2024/05/13/i...

Smokeloader keeps crawling its way back into the limelight. If you want a primer on it, I gave a public talk on it 2 years ago
www.youtube.com/watch?v=O69e...
@volexity.bsky.social has published a blog post detailing variants of LIGHTSPY & DEEPDATA malware discovered in the summer of 2024, including exploitation of a vulnerability in FortiClient to extract credentials from memory. Read more here: www.volexity.com/blog/2024/11...
15.11.2024 20:02 — 👍 37 🔁 27 💬 0 📌 1