Linux Reverse Shell in x86 Assembly : rootfu.in/linux-revers...
21.05.2025 13:32 — 👍 6 🔁 2 💬 0 📌 1Linux Reverse Shell in x86 Assembly : rootfu.in/linux-revers...
21.05.2025 13:32 — 👍 6 🔁 2 💬 0 📌 1300 Milliseconds to Admin: Mastering DLL Hijacking and Hooking to Win the Race (CVE-2025-24076 and CVE-2025-24994) : blog.compass-security.com/2025/04/3-mi...
20.05.2025 07:24 — 👍 4 🔁 2 💬 0 📌 0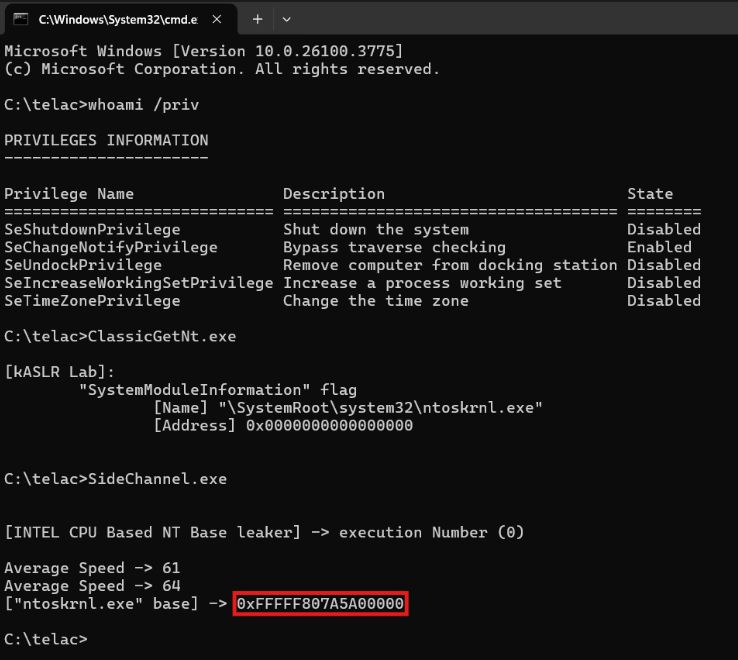
Bypassing kASLR via Cache Timing : r0keb.github.io/posts/Bypass...
kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
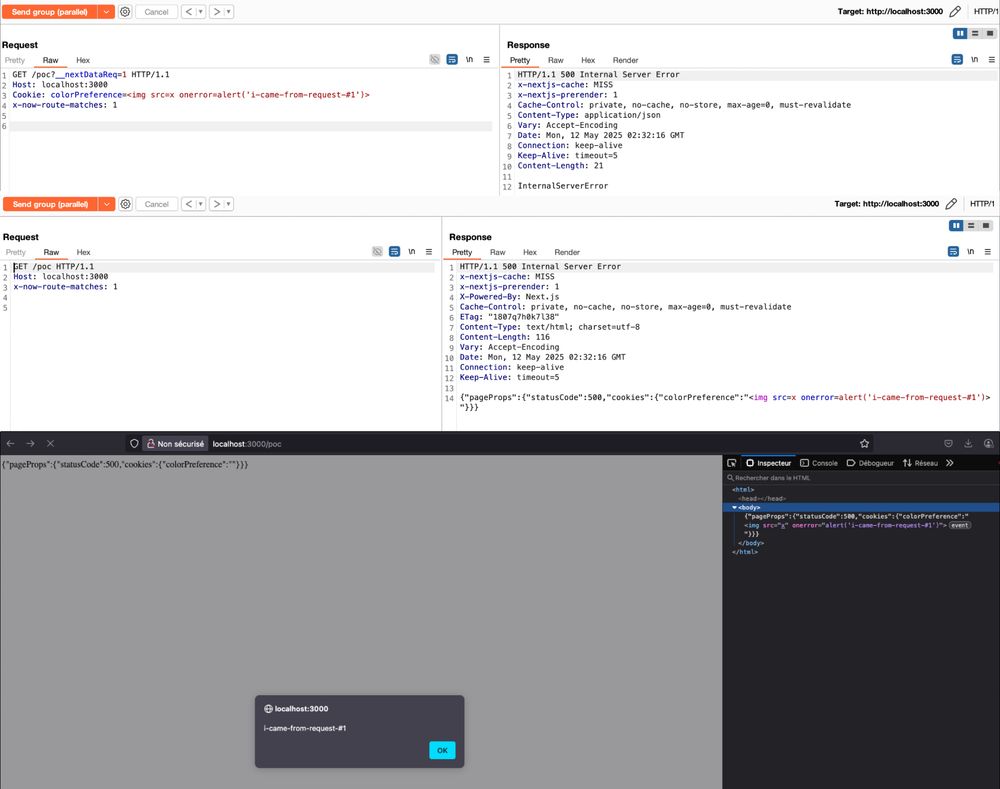
Cache poisoning via race-condition in Next.js : zhero-web-sec.github.io/research-and... credits @zhero___
20.05.2025 06:14 — 👍 2 🔁 2 💬 0 📌 0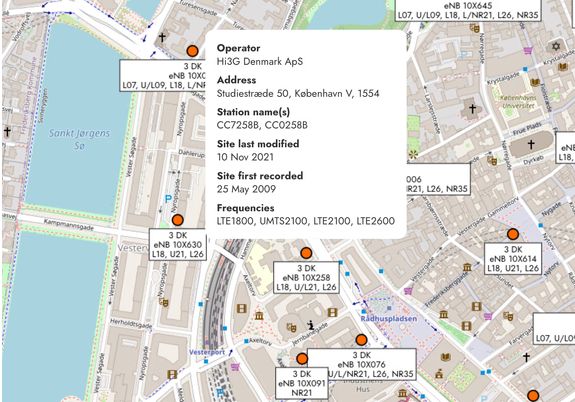
O2 VoLTE : Locating any customer with a phone call : mastdatabase.co.uk/blog/2025/05...
20.05.2025 06:05 — 👍 2 🔁 1 💬 0 📌 0
Bypassing Web Filters (Part 4) : Host Header Spoofing & Domain Fronting Detection Bypasses : blog.compass-security.com/2025/03/bypa...
3 : Domain Fronting : blog.compass-security.com/2025/03/bypa...
2 : Host Header Spoofing : blog.compass-security.com/2025/03/bypa...
Game Hacking : Part 1 - Land Of The PEB - Modules and DLLs : codeneverdies.github.io/posts/lotp-1/
Part 2 : Running from the debugger : codeneverdies.github.io/posts/lotp-2/
Part 3: BakkesMod : codeneverdies.github.io/posts/gh-1/
4 : Valve Anti-Cheat (VAC) : codeneverdies.github.io/posts/gh-2/
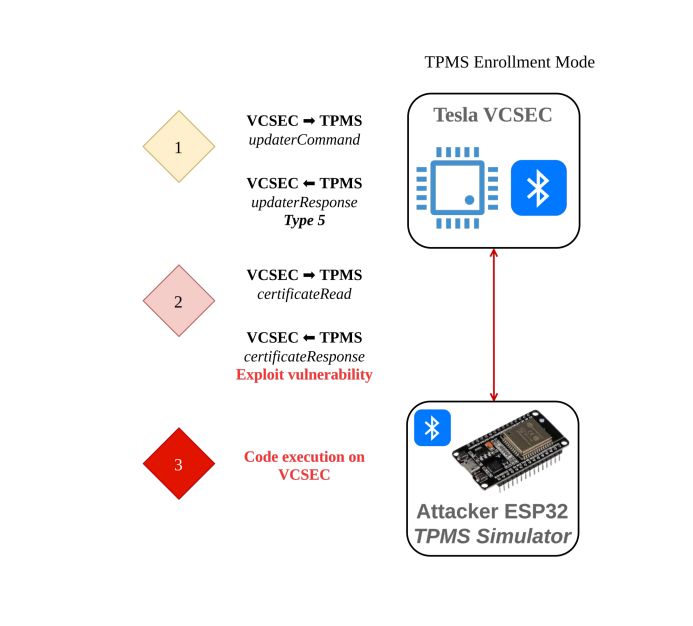
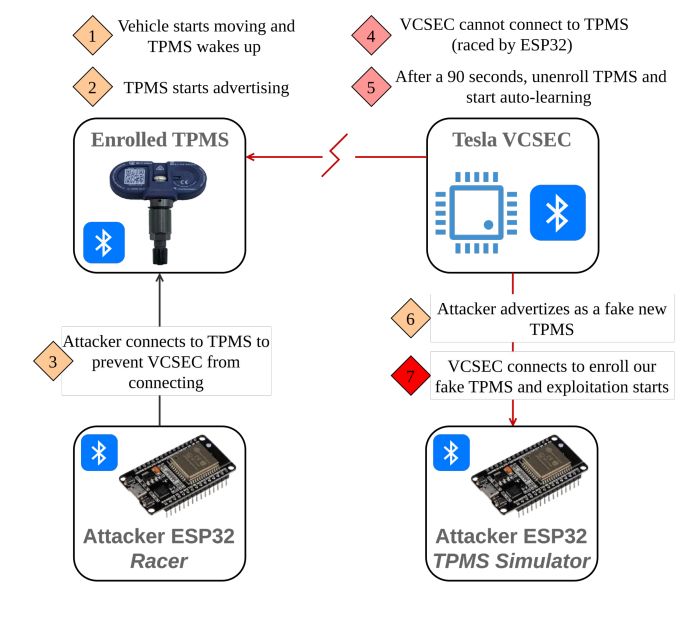
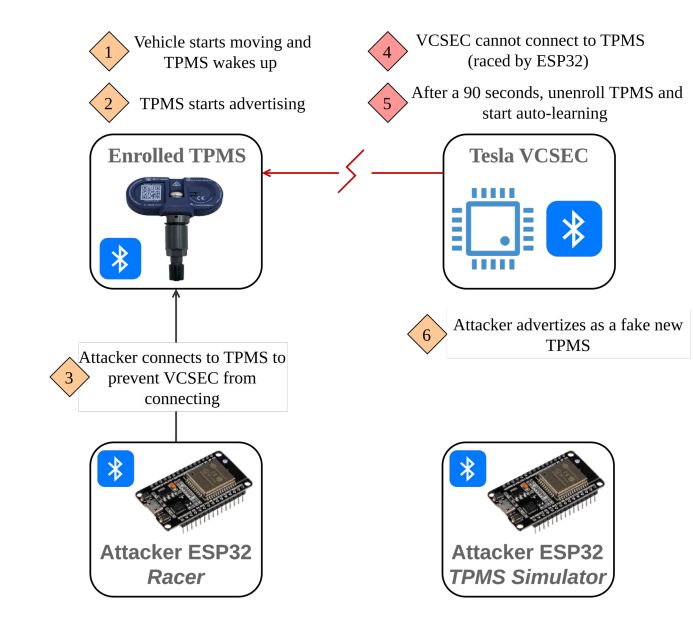
0-click RCE on Tesla Model 3 through TPMS Sensors : www.synacktiv.com/sites/defaul... credits @masthoon @vdehors
18.05.2025 11:34 — 👍 10 🔁 10 💬 1 📌 2
PE32 Ransomware : A New Telegram-Based Threat on the Rise : any.run/cybersecurit... credits @MauroEldritch
17.05.2025 13:11 — 👍 2 🔁 0 💬 0 📌 0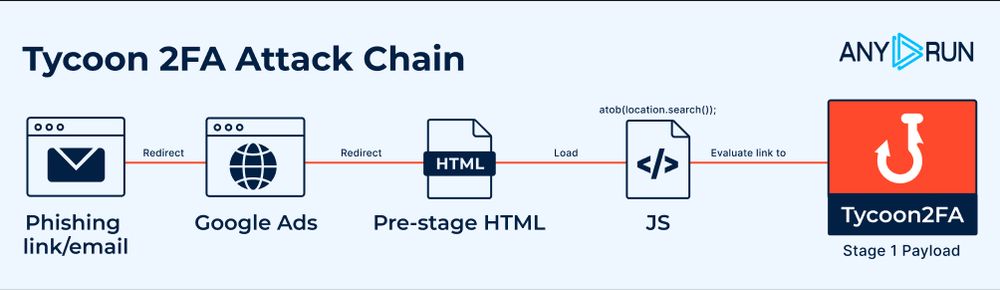
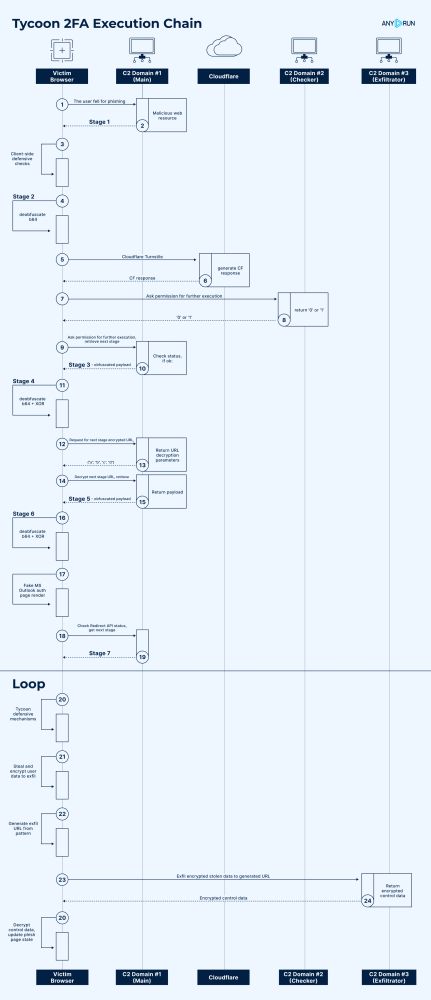
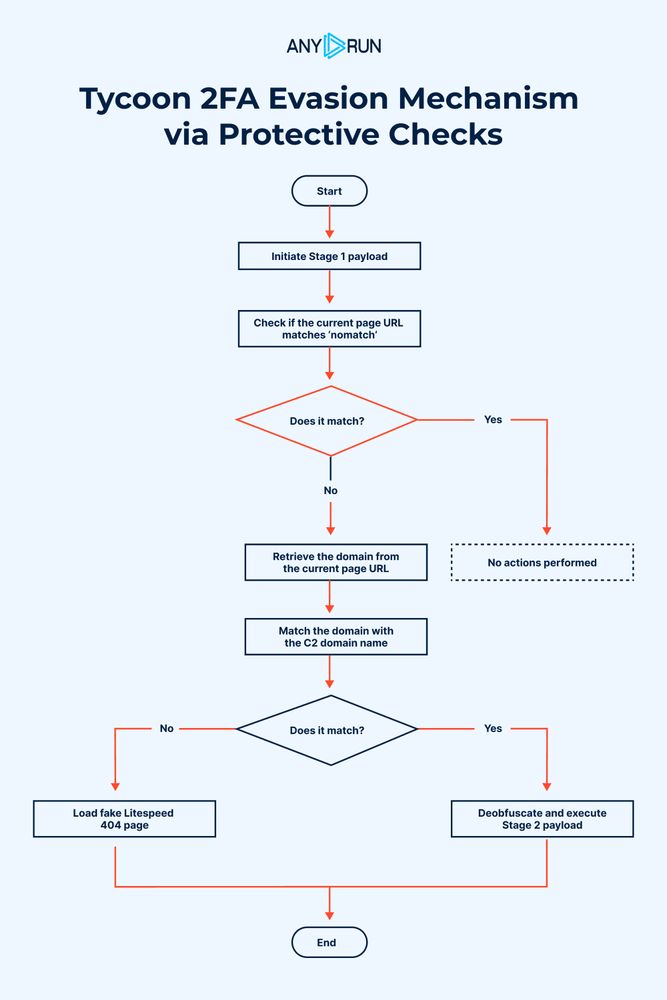
Evolution of Tycoon 2FA Defense Evasion Mechanisms : Analysis and Timeline : any.run/cybersecurit...
17.05.2025 12:59 — 👍 2 🔁 0 💬 0 📌 0HTML to PDF Renderer : A tale of local file access and shellcode execution : neodyme.io/en/blog/html...
17.05.2025 12:55 — 👍 1 🔁 0 💬 0 📌 0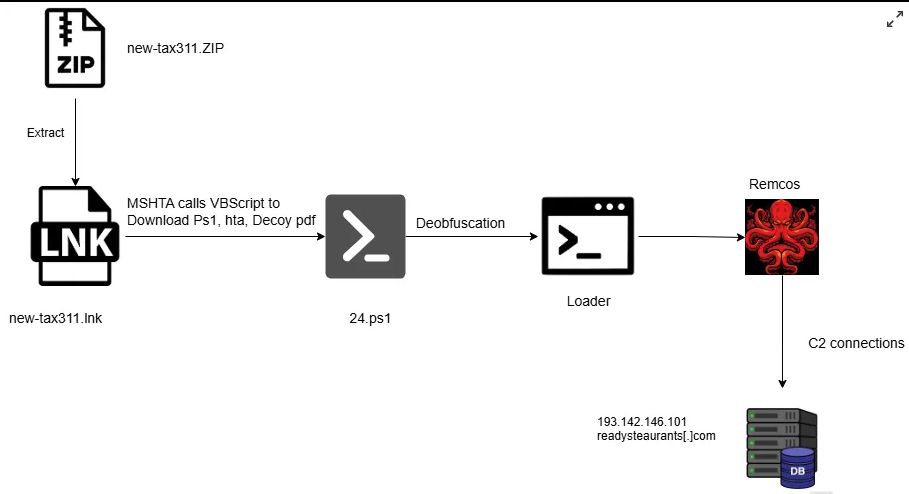
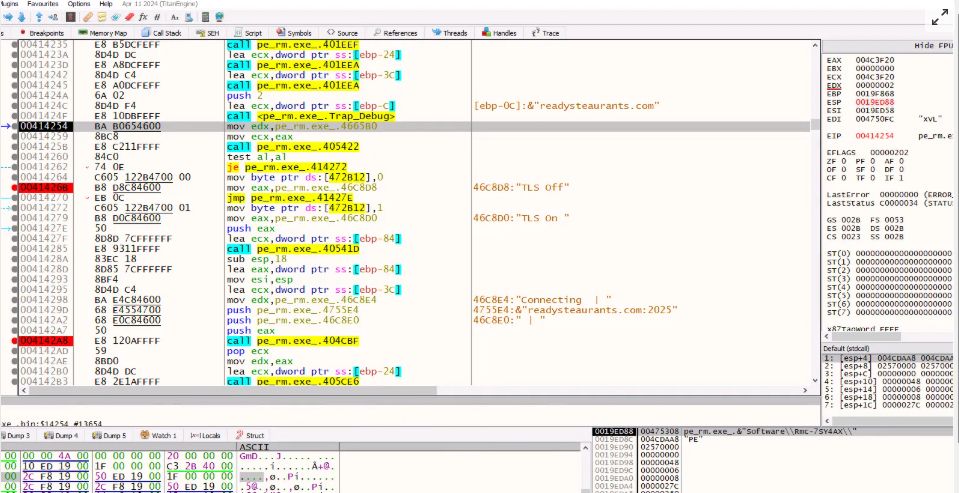
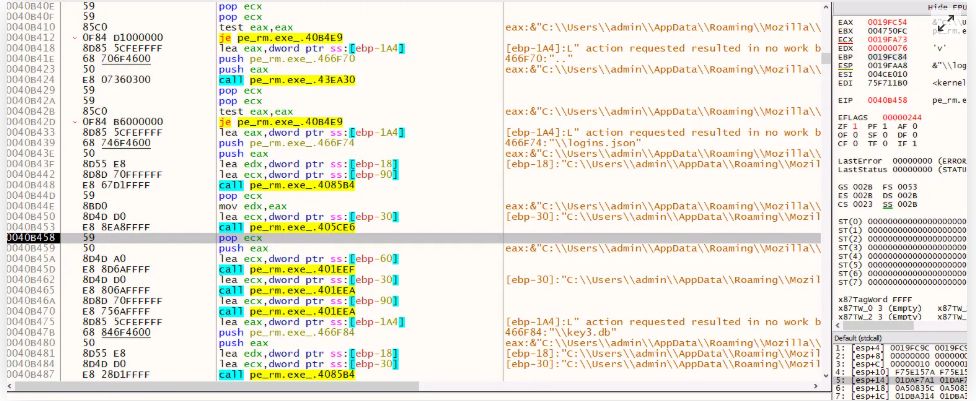
Fileless Execution : PowerShell Based Shellcode Loader Executes Remcos RAT : blog.qualys.com/vulnerabilit...
17.05.2025 09:16 — 👍 0 🔁 2 💬 0 📌 0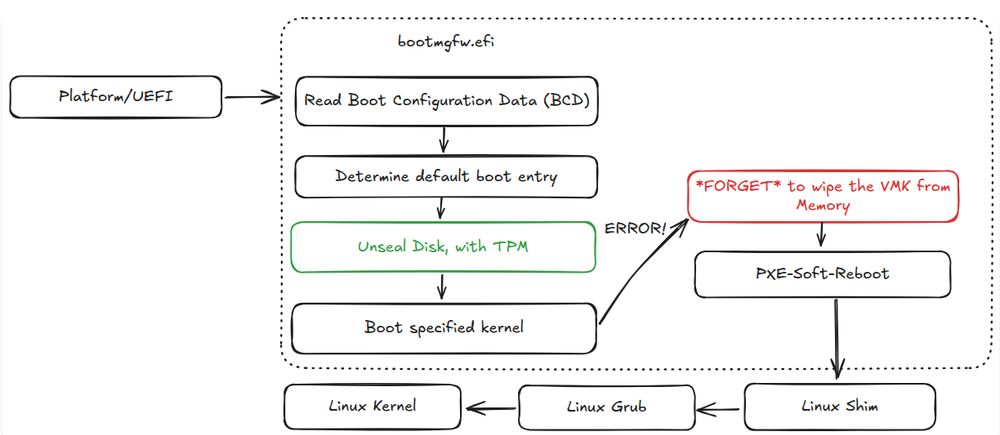
Breaking up-to-date Windows 11 BitLocker encryption -- on-device but software-only : neodyme.io/en/blog/bitl...
17.05.2025 09:04 — 👍 3 🔁 0 💬 0 📌 0
Researchers Expose New Intel CPU Flaws Enabling Memory Leaks and Spectre v2 Attacks : ethz.ch/en/news-and-...
Ref :
*Speculative calculations open a backdoor to information theft (*2022) : ethz.ch/en/news-and-...
RETBLEED : www.usenix.org/system/files...
Mastering Rate Limit Bypass Techniques : infosecwriteups.com/mastering-ra...
17.05.2025 08:22 — 👍 1 🔁 0 💬 0 📌 0
Hacking Casino - How Math Beats the Casino Odds : www.youtube.com/watch?v=87Fg...
Shuffle Up and Deal: Analyzing the Security of Automated Card Shufflers : i.blackhat.com/BH-US-23/Pre...
How To Rob a Casino : 0x00sec.org/t/how-to-rob...

Writing a Self-Mutating Malware : 0x00sec.org/t/writing-a-...
Metamorphic Code Examples : stackoverflow.com/questions/10...

How To Rob a Casino : 0x00sec.org/t/how-to-rob...
17.05.2025 07:26 — 👍 1 🔁 0 💬 0 📌 0
macOS Malware Development (Part 2) : 0x00sec.org/t/macos-malw...
Part 1 : 0x00sec.org/t/macos-malw...
Ref :
Inside a Hello World executable on OS X : adrummond.net/posts/macho
The Mystery of Mach-O Object Structure : alexdremov.me/mystery-of-m...
www2.cs.arizona.edu/~collberg/Te...
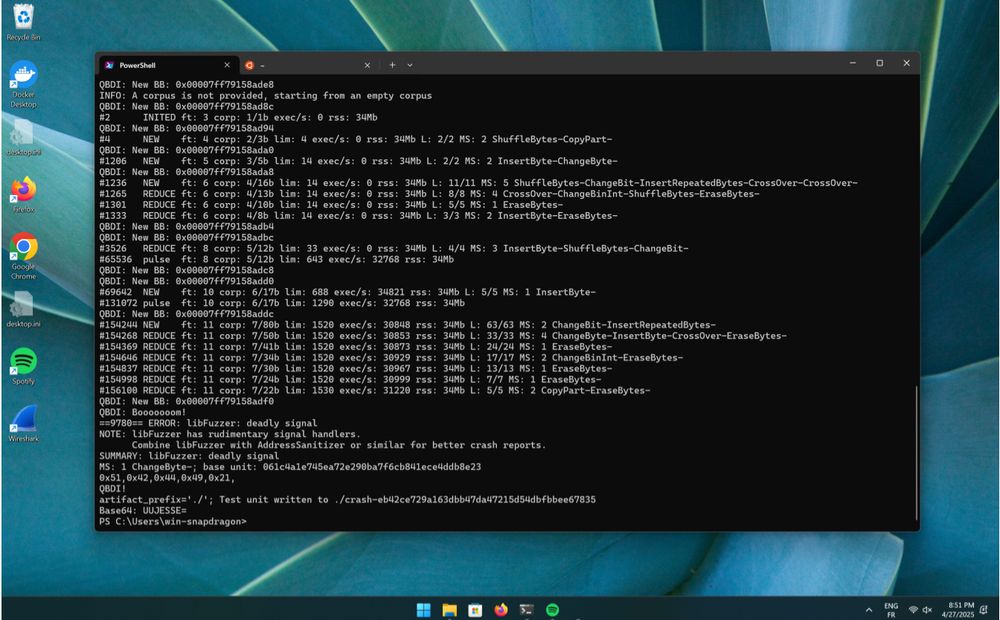
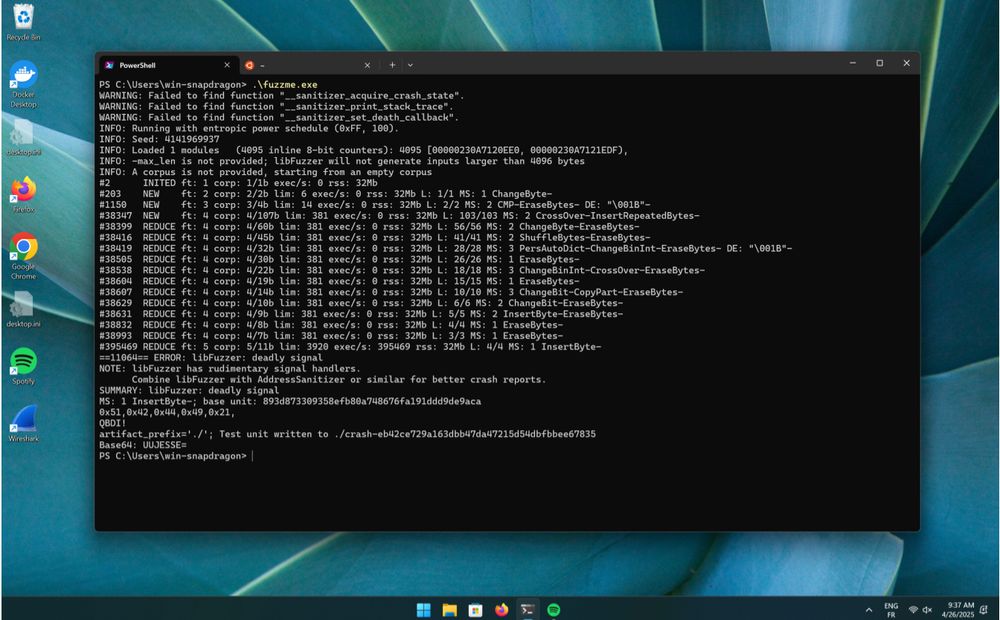
Fuzzing Windows ARM64 closed-source binary : www.romainthomas.fr/post/25-04-w...
17.05.2025 06:15 — 👍 3 🔁 1 💬 0 📌 0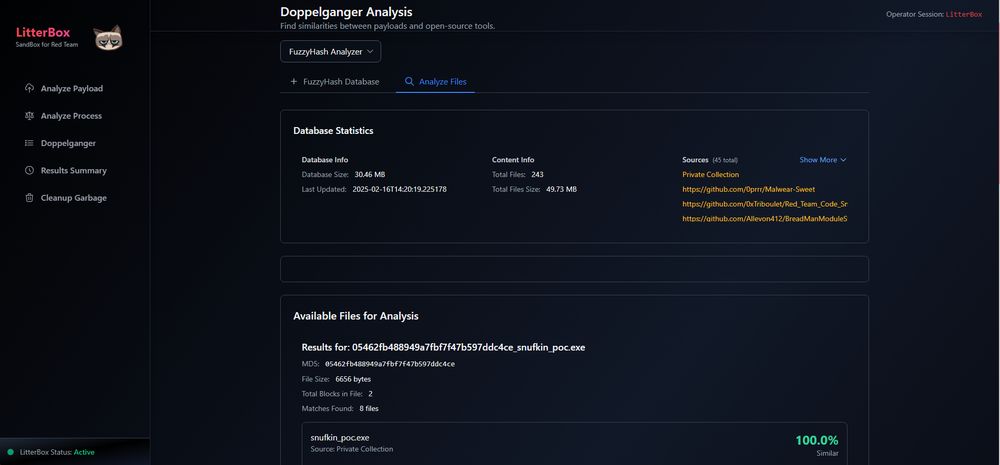
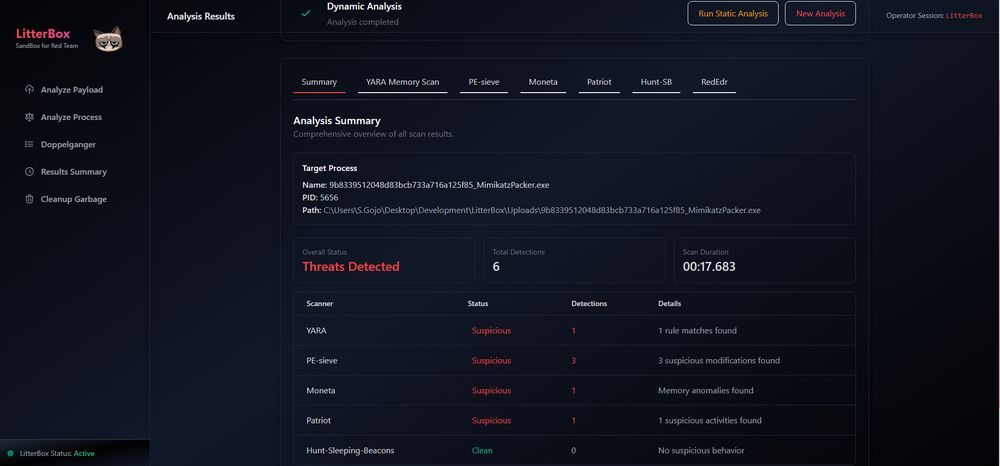
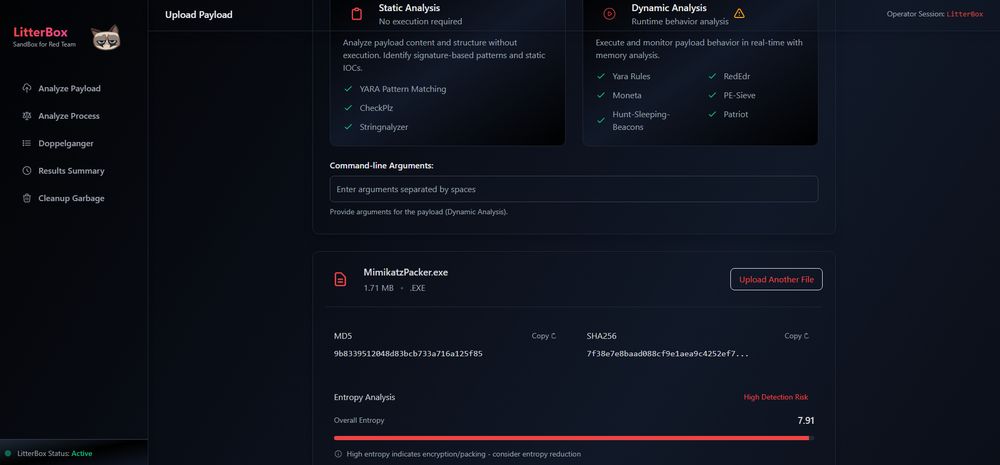
Litterbox : Sandbox approach for malware developers and red teamers to test payloads against detection mechanisms before deployment : github.com/BlackSnufkin...
17.05.2025 06:03 — 👍 0 🔁 0 💬 0 📌 0Pupkin : a deceptively simple .NET-based stealer designed to harvest browser passwords, Discord tokens, and Telegram sessions — all controlled silently through a Telegram C2 : muff-in.github.io/blog/pupkin-...
02.05.2025 16:25 — 👍 2 🔁 1 💬 0 📌 0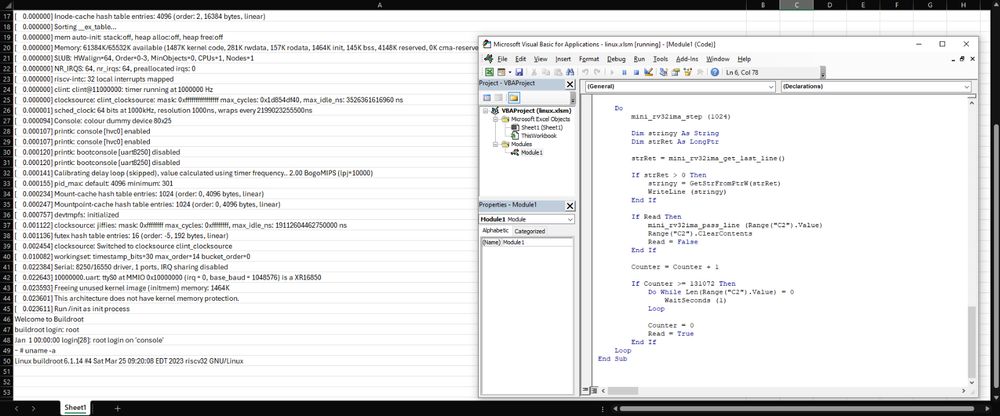
Linux running in Excel : github.com/NSG650/Linux...
02.05.2025 15:46 — 👍 1 🔁 0 💬 0 📌 0felix86 : Run x86-64 programs on RISC-V Linux : github.com/OFFTKP/felix86
02.05.2025 15:37 — 👍 1 🔁 0 💬 0 📌 0LigerLabs - Educational Modules for (Anti-)Reverse Engineering : ligerlabs.org
01.05.2025 15:53 — 👍 0 🔁 0 💬 0 📌 0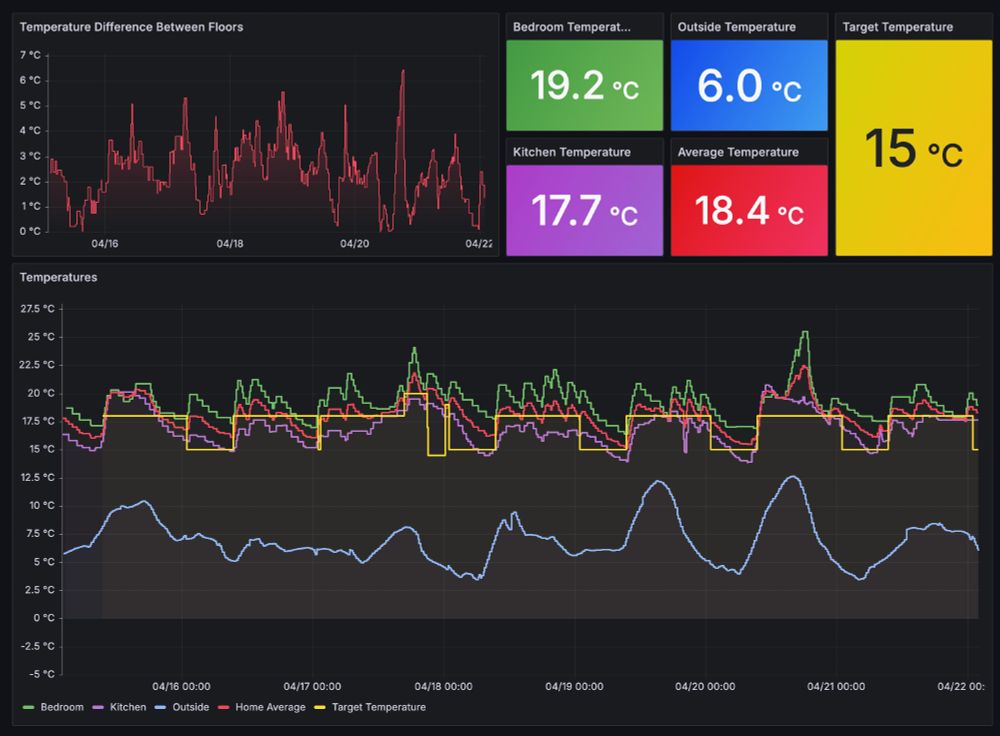
Attacking My Landlord's Boiler : blog.videah.net/attacking-my...
01.05.2025 15:51 — 👍 1 🔁 0 💬 0 📌 0
How I Found Malware in a BeamNG Mod : lemonyte.com/blog/beamng-...
01.05.2025 15:46 — 👍 1 🔁 0 💬 0 📌 0
How I made $64k from deleted files — a bug bounty story : medium.com/@sharon.briz...
01.05.2025 15:44 — 👍 2 🔁 1 💬 0 📌 0
How a Single Line Of Code Could Brick Your iPhone : rambo.codes/posts/2025-0...
01.05.2025 15:39 — 👍 0 🔁 0 💬 0 📌 0AirBorne : Wormable Zero-Click RCE in Apple AirPlay Puts Billions of Devices at Risk : www.oligo.security/blog/airborne
01.05.2025 15:37 — 👍 1 🔁 2 💬 0 📌 0