No. Senate Republicans refuse to extend ACA subsidies unless they get a nationwide abortion ban.
12.11.2025 01:37 — 👍 0 🔁 0 💬 0 📌 0
Dems in ARRAY
05.11.2025 01:55 — 👍 8433 🔁 1132 💬 120 📌 47
This! I'm so embarrassed for her. Anton sucks.
02.10.2025 04:16 — 👍 1 🔁 0 💬 1 📌 0
Ew Leo?!??! That guy was so gross.
02.10.2025 03:13 — 👍 1 🔁 0 💬 0 📌 0
I am not sure if I'm overreacting but Anton not looking back at Ali and instead chugging alcohol made me so embarrassed for her. I've never seen a contestant act like that before.
02.10.2025 03:03 — 👍 1 🔁 0 💬 1 📌 0
Curious to hear your thoughts on episode 2 when Anton and Ali meet.
02.10.2025 02:33 — 👍 1 🔁 0 💬 1 📌 0
"Plans to expand presidential power ... and erode checks and balances" he's breaking the impoundment act. Its illegal. Don't act like he's some brilliant mastermind. He's a criminal.
29.09.2025 16:33 — 👍 5 🔁 0 💬 0 📌 0
Not sure if Stephen Miller or Russell Vought is the most evil of this administration.
29.09.2025 16:31 — 👍 3 🔁 0 💬 0 📌 0
The host and judges aren't it. Shows alright but its not Top Chef and it wants to be Top Chef so bad.
20.09.2025 04:32 — 👍 0 🔁 0 💬 0 📌 0
I miss who I was a week ago when I didn't know what a groyper, fem boy, or transmaxxing is.
16.09.2025 23:36 — 👍 1 🔁 0 💬 0 📌 0
No not Maru 😭
11.09.2025 03:00 — 👍 3 🔁 0 💬 0 📌 0
You are under no obligation to mourn the death of people who would’ve celebrated yours.
10.09.2025 20:56 — 👍 23228 🔁 7877 💬 102 📌 118

100% true.
10.09.2025 20:34 — 👍 10705 🔁 3331 💬 314 📌 128

I am sure that Trump will now send the National Guard into that lawless and bastion of left-wing ideology, Utah, following the shooting of Charlie Kirk, right?
10.09.2025 20:26 — 👍 3 🔁 2 💬 0 📌 0
I have never seen a "journalist" be so antagonistic. Clearly has no integrity and no ethics. Unfollowing wired for giving her a platform.
31.08.2025 18:25 — 👍 0 🔁 0 💬 0 📌 0
Allegedly he hasnt been seen since 8/26 😅
30.08.2025 02:08 — 👍 4 🔁 0 💬 0 📌 0
I assume Jake Tapper is camped out in the front of the White House demanding answers.
30.08.2025 02:06 — 👍 1330 🔁 152 💬 26 📌 0
"I would do it if I were Tom. I think it's great" -- Trump endorses the arrest of Gov. Gavin Newsom
09.06.2025 16:59 — 👍 2471 🔁 739 💬 639 📌 467
One of my Trump voting coworkers shared a Go Fund Me for someone they know, pleading for people to donate. But yet they themselves didn't donate. Ain't that something.
31.05.2025 15:48 — 👍 1 🔁 0 💬 0 📌 0

Tonight, while we sleep, Republicans will pass the biggest transfer of wealth from the bottom to the top in our history. 🇺🇸
Tax cuts for them, health care cuts for you.
21.05.2025 02:21 — 👍 1119 🔁 512 💬 60 📌 33
I was told to take Tylenol before my IUD insertion and given nothing else. It was the most excruciating pain I have ever experienced.
20.05.2025 13:59 — 👍 1 🔁 0 💬 1 📌 0
Walz: When did government get to tell you how many dolls your child has? Government just big enough to fit in your bedroom, your womb, and apparently now in your toy chest.
08.05.2025 01:24 — 👍 42185 🔁 10409 💬 666 📌 492
Yesterday's win was so important. Gives Steph some time to heal up.
07.05.2025 14:51 — 👍 0 🔁 0 💬 0 📌 0
The perfect time to delete this was when you posted it. The second perfect time is now.
07.05.2025 14:50 — 👍 0 🔁 0 💬 0 📌 0
Democrats should have a public website listing 1) all his impeachable offenses and 2) at running count of "days without a Trump impeachable offense"
06.05.2025 02:30 — 👍 2 🔁 0 💬 1 📌 0

Trump's polling has already collapsed
It took under 100 days for buyer's remorse to set in.
In just 100 days:
Measles outbreaks
Tariffs costing us $5k each
Gutting healthcare
Thousands of veterans fired
Abducting immigrants
Concentration camps
Deporting citizens
Legalized discrimination
Texted war plans
Alienated allies
Took bribes
Sold Teslas
29.04.2025 11:37 — 👍 1138 🔁 401 💬 73 📌 11
It’s ant season. Don’t ask me how I know.
25.04.2025 20:20 — 👍 721 🔁 18 💬 80 📌 6
This is so brutal. Didn't ge just come back from a clotting issue? This may be the end of his career 😭
28.04.2025 18:42 — 👍 3 🔁 0 💬 1 📌 0
Do you know if Jimmy is playing tonight?
26.04.2025 22:56 — 👍 0 🔁 0 💬 0 📌 1
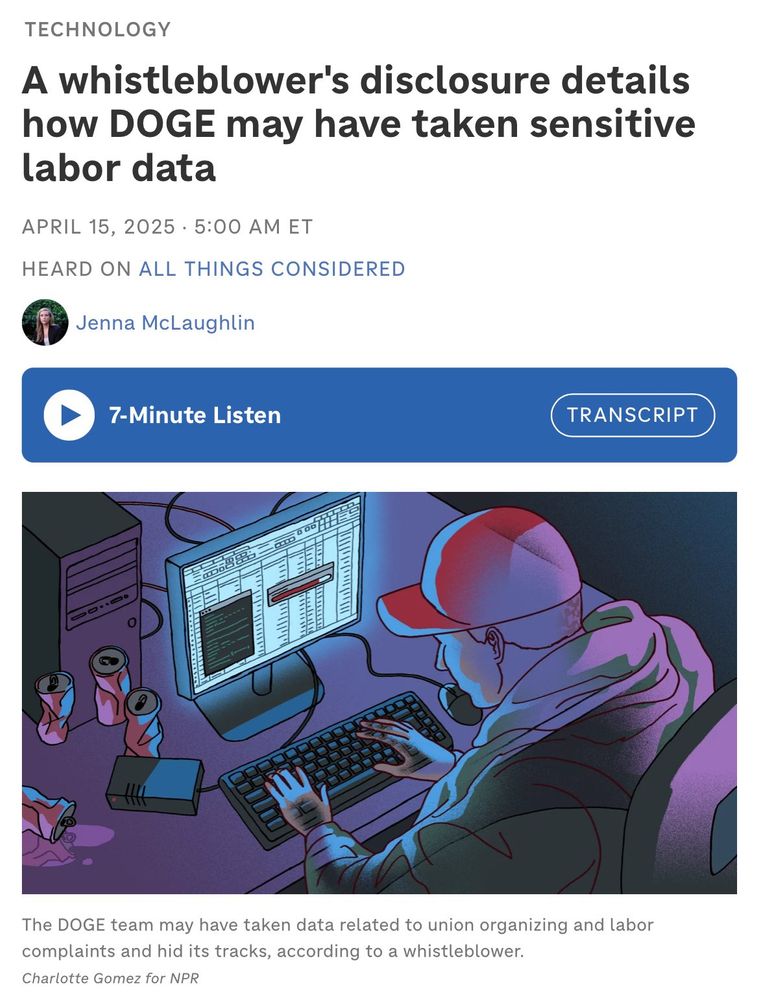
A whistleblower's disclosure details how DOGE may have taken sensitive labor data

The IT team met to discuss insider threats - namely, the DOGE engineers, whose activities it had little insight into or control over. "We had no idea what they did," he explained. Those conversations are reflected in his official disclosure.
They eventually launched a formal breach investigation, according to the disclosure, and prepared a request for assistance from the Cybersecurity and Infrastructure Security Agency (CISA). However, those efforts were disrupted without an explanation, Berulis said. That was deeply troubling to Berulis, who felt he needed help to try to get to the bottom of what happened and determine what new vulnerabilities might be exploited as a result.
In the days after Berulis and his colleagues prepared a request for CISAs help investigating the breach, Berulis found a printed letter in an envelope taped to his door, which included threatening language, sensitive personal information and overhead pictures of him walking his dog, according to the cover letter attached to his official disclosure. It's unclear who sent it, but the letter made specific reference to his decision to report the breach. Law enforcement is investigating the letter.
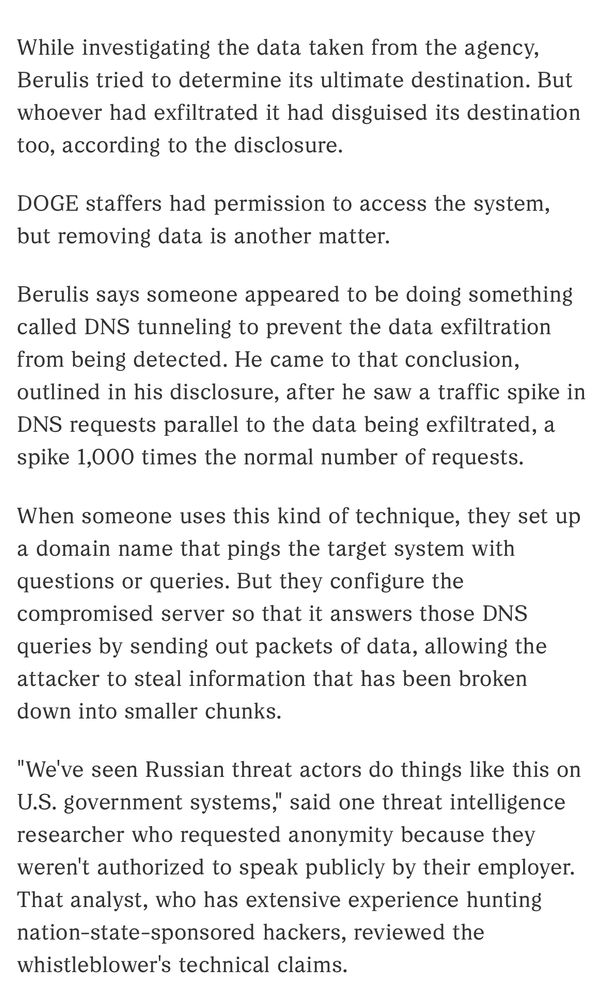
While investigating the data taken from the agency, Berulis tried to determine its ultimate destination. But whoever had exfiltrated it had disguised its destination too, according to the disclosure.
DOGE staffers had permission to access the system, but removing data is another matter.
Berulis says someone appeared to be doing something called DNS tunneling to prevent the data exfiltration from being detected. He came to that conclusion, outlined in his disclosure, after he saw a traffic spike in DNS requests parallel to the data being exfiltrated, a spike 1,000 times the normal number of requests.
When someone uses this kind of technique, they set up a domain name that pings the target system with questions or queries. But they configure the compromised server so that it answers those DNS queries by sending out packets of data, allowing the attacker to steal information that has been broken down into smaller chunks.
"We've seen Russian threat actors do things like this on
U.S. government systems," said one threat intelligence researcher who requested anonymity because they weren't authorized to speak publicly by their employer.
That analyst, who has extensive experience hunting nation-state-sponsored hackers, reviewed the whistleblower's technical claims.
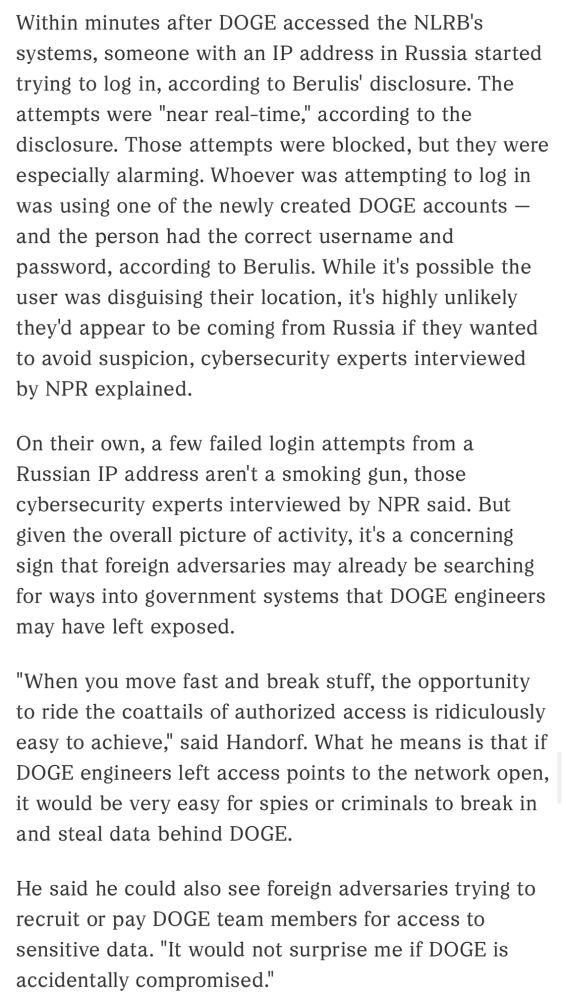
Within minutes after DOGE accessed the NLRB's systems, someone with an IP address in Russia started trying to log in, according to Berulis' disclosure. The attempts were "near real-time," according to the disclosure. Those attempts were blocked, but they were especially alarming. Whoever was attempting to log in was using one of the newly created DOGE accounts - and the person had the correct username and password, according to Berulis. While it's possible the user was disguising their location, it's highly unlikely they'd appear to be coming from Russia if they wanted to avoid suspicion, cybersecurity experts interviewed by NPR explained.
On their own, a few failed login attempts from a Russian IP address aren't a smoking gun, those cybersecurity experts interviewed by NPR said. But given the overall picture of activity, it's a concerning sign that foreign adversaries may already be searching for ways into government systems that DOGE engineers may have left exposed.
"When you move fast and break stuff, the opportunity to ride the coattails of authorized access is ridiculously easy to achieve," said Handorf. What he means is that if DOGE engineers left access points to the network open, it would be very easy for spies or criminals to break in and steal data behind DOGE.
He said he could also see foreign adversaries trying to recruit or pay DOGE team members for access to sensitive data. "It would not surprise me if DOGE is accidentally compromised."
Musk’s DOGE involved in what appears to be a foreign espionage operation and data theft. They also have death threatened US federal whistleblowers and disabled security systems, deliberately allowing Russian IPs to access sensitive US federal government systems.
www.npr.org/2025/04/15/n...
16.04.2025 10:29 — 👍 4828 🔁 2627 💬 226 📌 252
Mayor-Elect of New York City
North Carolina Supreme Court Justice. Former civil rights attorney.
https://linktr.ee/riggsforourcourts
Appellate lawyer at Wright, Close & Barger in Houston, with a Fifth Circuit and TX appellate practice. So-called Dean, #appellatetwitter. Host of The Appellate Wanderer podcast
Tracking the latest polls in US politics
Pretty much the same as I ever was. CA, MI, NC, SE PA now. UNC for a while in the 1970s. Lefty in almost all things because I try to do what’s right. Now known as Grandpa to three little ones.
Still trying to find hope for our country.
Setting my hair on fire for fun and profit. Disabled in a particularly shitty way. I know everything about everything, plus some other stuff.
They/them.
Also, I'm a duck.
Cash app: $OGMcDuck
Paypal: Mieskie@neo.rr.com
(☝️☝️Search my feed for cancer $$)
Rock n’ Roll Expat in Mexico; Upper Michigander; ex-New Yorker; ex-Minnesotan; ex-Wisconsinite; drummer, guitarist, singer, songwriter; ex-drummer for bands who opened for many you’ve heard of; vinyl junkie; sensible progressive; Gen X; avid wiseass
A Freight Relocation Specialist and a member of the Democratic Party! Dig it!💙👊🏾
#GoBills #BillsMafia 🦬
McKinney, TX 🔵dot
Mom. Combat Veteran. Blackhawk pilot. U.S. Senator. Illinoisan.
- Metabolism, energy, & sustainable weight loss
- Helped 100+ so far
- NC, USA📍
- No-Cook Fat Loss Plan → https://www.etsy.com/listing/4319160377/lazy-fat-loss-meal-plan-high-protein-no?etsrc=sdt
🔥Side Quest Sundays: @sidequestsun.bsky.social
NYT best-selling author of 10 books. The Press Box Chronicles, my YouTube show, is riiiiight here: https://www.youtube.com/@pressboxchronicles
Navy combat veteran and retired NASA astronaut. Husband to @GabbyGiffords.bsky.social. United States Senator for the great state of Arizona.
The 2025 election proved what’s possible when we turn out to vote. Stay engaged, talk to your friends and neighbors about things that impact their lives, and we will build a coalition of pissed but decent people who will boot these MF-ers out in 2026!
Polls, Data, Shitposts, Opinions, Personal Account // Email or DM About Promotions // Support Me: http://ko-fi.com/polling 🇺🇸🇺🇦🏳️⚧️
Backsliding Methodist, follower of Jesus, Tarheel, musician, lifelong Democrat, mountain mama, cook, decorator, believer in my country and the people in it.
Temerty Professor of Modern European History, Munk School, University of Toronto; Permanent Fellow, IWM Vienna; Emeritus Levin Professor, Yale. Author of "On Freedom," "On Tyranny," "Our Malady," "Road to Unfreedom," "Black Earth," and "Bloodlands"
Non-partisan analysis featuring the trusted voices of Amy Walter, David Wasserman, Jessica Taylor, Erin Covey and Matthew Klein. The right analysis for getting it right. Learn more: cookpolitical.com/subscribe
Husband, dad, veteran, writer, and proud Midwesterner. 19th US Secretary of Transportation and former Mayor of South Bend.
Congressman for California's 2nd District. Posts are from my personal/campaign account. For official account please follow @RepHuffman









