FIRST Ever Online Mobile Hacking Conference.
Free, worldwide online event bringing the mobile security community together for sessions on mobile hacking, AI, malware, forensics, live mobile‑focused CTF with prizes!
When: March 3 and 4, 2026
Register here: www.mobilehackinglab.com/mobile-hacki...
04.02.2026 10:20 — 👍 0 🔁 0 💬 0 📌 0

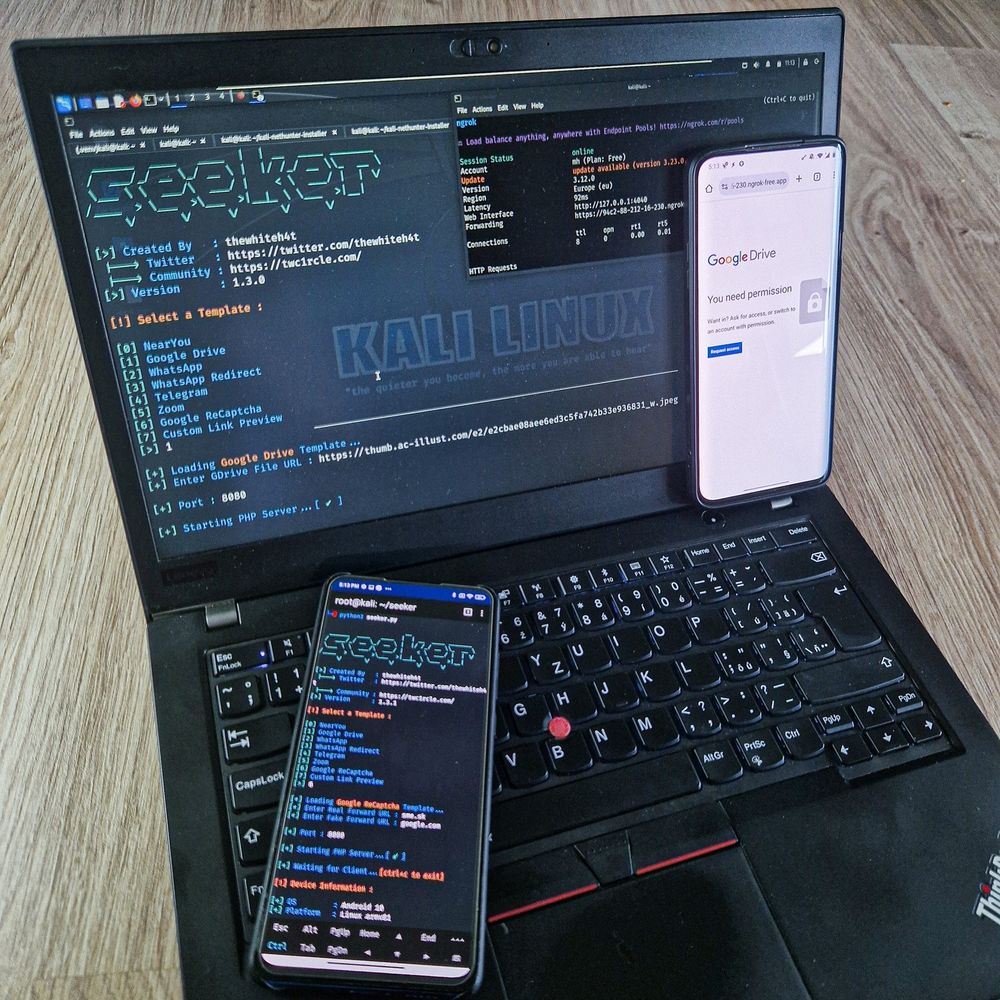
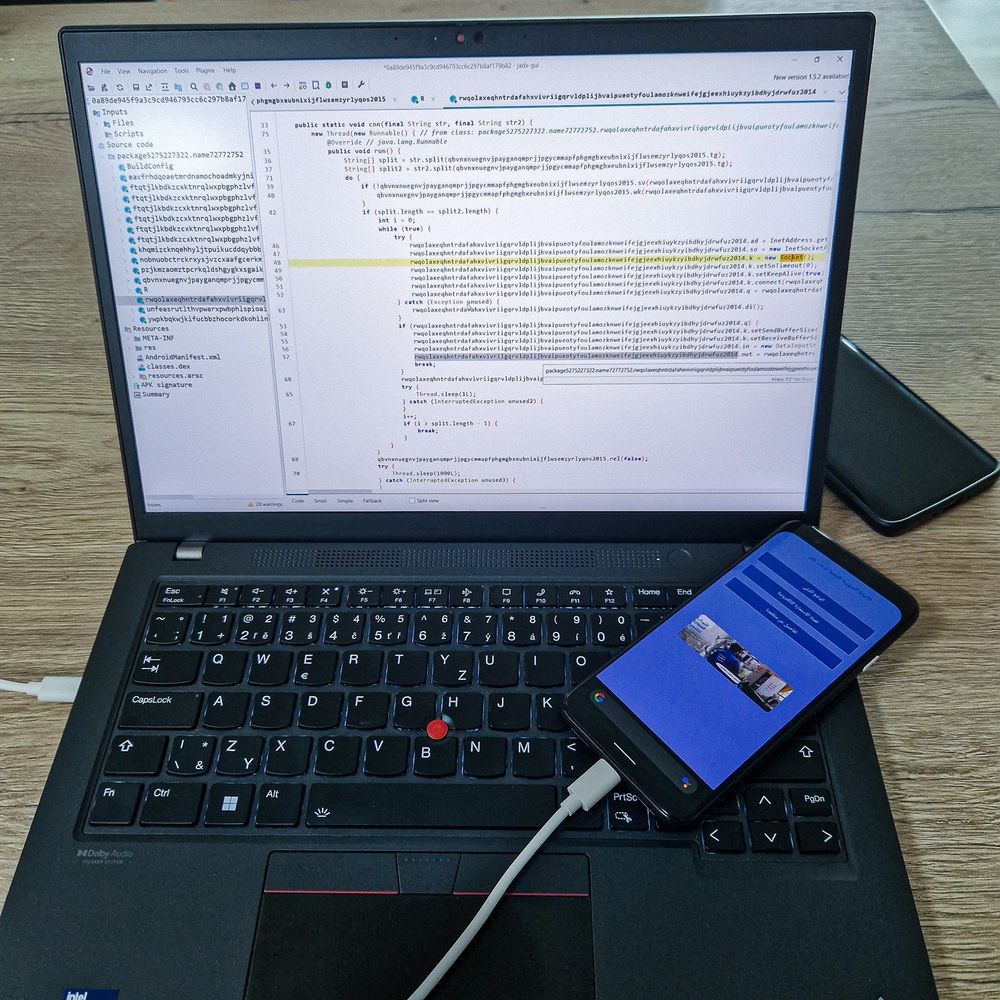
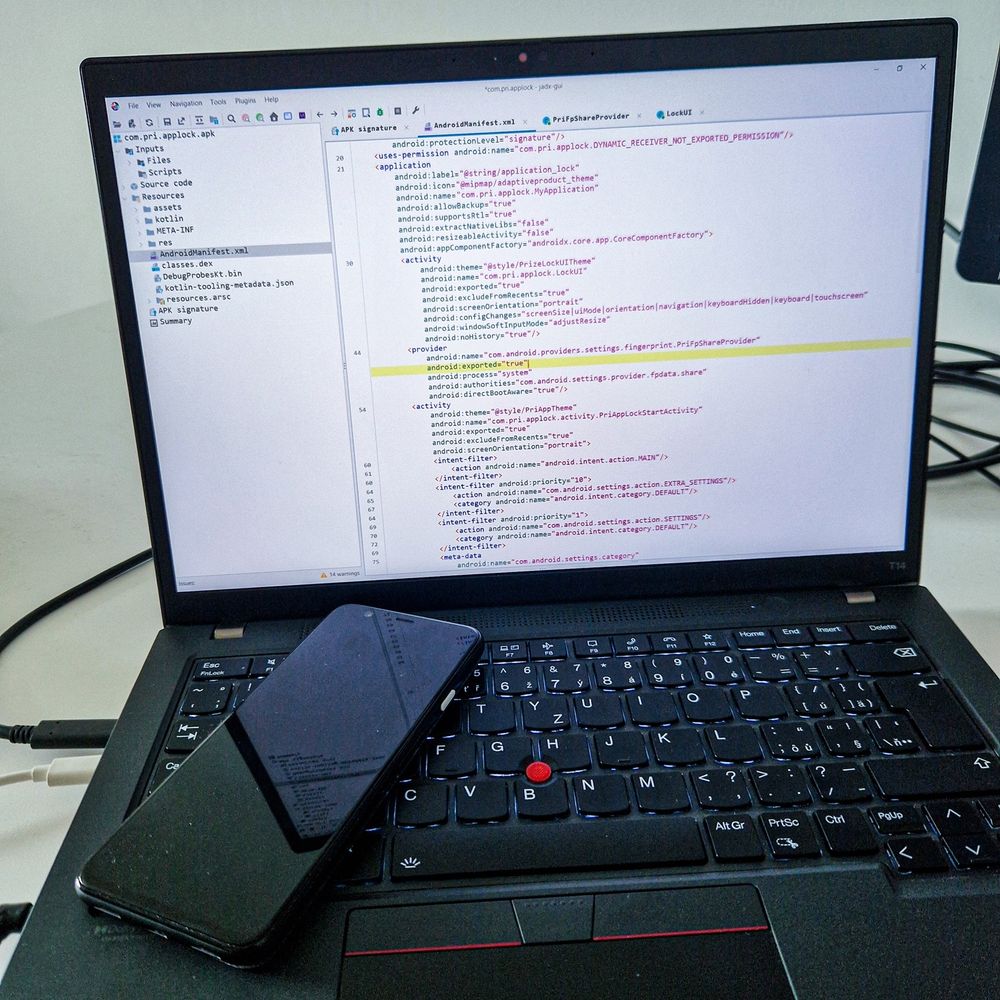
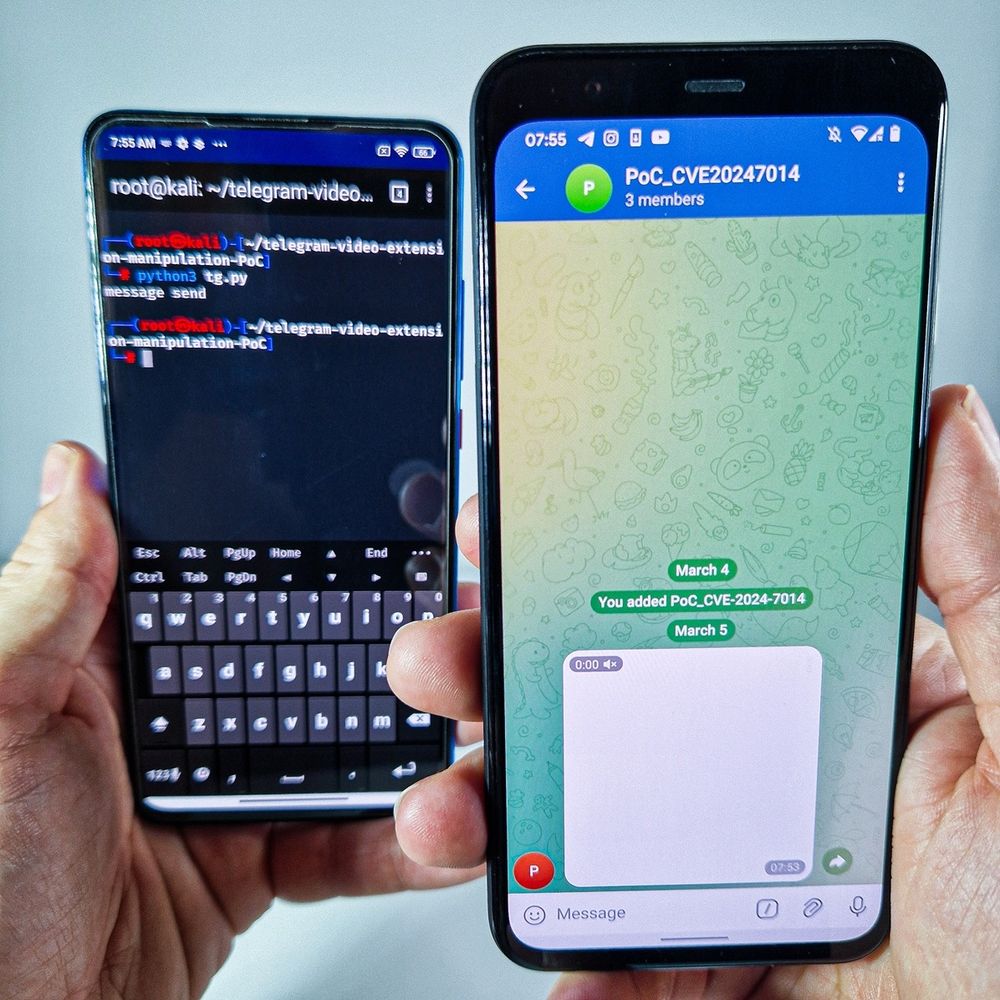
CVE-2025-10184 is permission bypass that affects multiple OnePlus devices running OxygenOS 12–15 (NOT FIXED) with PoC
This vulnerability allows any application installed on the device to read SMS/MMS without permission, user interaction, or consent.
www.rapid7.com/blog/post/cv...
25.09.2025 12:55 — 👍 0 🔁 0 💬 0 📌 0

How to Install Gemini CLI on Android using Termux
www.mobile-hacker.com/2025/07/09/h...
09.07.2025 07:31 — 👍 0 🔁 0 💬 0 📌 0

Vibe Hacking with Nmap using Android
www.mobile-hacker.com/2025/07/07/v...
07.07.2025 08:57 — 👍 0 🔁 0 💬 0 📌 0
It is lilygo t-dongle
24.01.2025 15:06 — 👍 1 🔁 0 💬 1 📌 0
Boost Flipper Zero with FEBERIS: 3-in-1 SubGhz, NRF24, and WiFi board
www.mobile-hacker.com/2025/01/09/b...
09.01.2025 08:43 — 👍 4 🔁 0 💬 0 📌 0
Explore #Marauder firmware on Cheap Yellow Display with all of its features 👇
www.mobile-hacker.com/2024/12/23/e...
03.01.2025 11:51 — 👍 1 🔁 0 💬 0 📌 0
Install and run any firmware (Marauder, Bruce, Ghost ESP...) on ESP32 devices without using computer with M5Stick Launcher
www.mobile-hacker.com/2024/12/29/r...
29.12.2024 14:06 — 👍 9 🔁 2 💬 0 📌 0