
On using LLMs for research (beyond basic prompts). Section 3.2 is specifically about catching a bug in a recent SNARG paper
arxiv.org/abs/2602.03837
@nmohnblatt.me.bsky.social
picious until proven otherwise. Cryptography research and auditing at zkSecurity. Recurring co-host on the ZKPodcast. nmohnblatt.me

On using LLMs for research (beyond basic prompts). Section 3.2 is specifically about catching a bug in a recent SNARG paper
arxiv.org/abs/2602.03837
Amazing work from Yoichi giving a Lean proof of my recent FRI security paper (w/ Albert Garreta and Benedikt Wagner)
Super interesting workflow as well, combining TeX-to-Lean models with regular coding agents. I think we'll see a lot more of this moving forward!
I haven't had a look actually. But I suspect that's the only viable option for now
24.12.2025 15:03 — 👍 1 🔁 0 💬 0 📌 0
Great short article from Moxie. Right in time for family dinners and questions about AI and privacy
confer.to/blog/2025/12...

Abstract. In outsourcing computation to untrusted servers, one can cryptographically ensure privacy using Fully Homomorphic Encryption (FHE) or ensure integrity using Verifiable Computation (VC) such as SNARK proofs. While each is practical for some applications in isolation, efficiently composing FHE and VC into Verifiable Computing on Encrypted Data (VCoED) remains an open problem. We introduce Laminate, the first practical method for adding integrity to BGV-style FHE, thereby achieving VCoED. Our approach combines the blind interactive proof framework with a tailored variant of the GKR proof system that avoids committing to intermediate computation states. We further introduce variants employing transcript packing and folding techniques. The resulting encrypted proofs are concretely succinct: 270kB, compared to 1TB in prior work, to evaluate a batch of B = 2¹⁴ instances of size n = 2²⁰ and depth d = 32. Asymptotically, the proof size and verifier work is O(dlog (Bn)), compared to Ω(BNlog n) in prior work (for ring dimension N). Unlike prior schemes, Laminate utilizes the full SIMD capabilities of FHE for both the payload circuit evaluation and proof generation; adds only constant multiplicative depth on top of payload evaluation while performing Õ(n) FHE operations; eliminates the need for witness reduction; and is field-agnostic. The resulting cost of adding integrity to FHE, compared to assuming honest evaluation, is ∼ 12× to ∼ 36× overhead (for deep multiplication-heavy circuits of size 2²⁰), which is > 500× faster than the state-of-the-art.

Image showing part 2 of abstract.
Laminate: Succinct SIMD-Friendly Verifiable FHE (Kabir Peshawaria, Zeyu Liu, Ben Fisch, Eran Tromer) ia.cr/2025/2285
22.12.2025 17:27 — 👍 4 🔁 2 💬 0 📌 0agreed. Although I would love to see it run in a TEE, same way Signal are doing theirs. Otherwise, we are still uploading our contacts to an untrusted server
17.12.2025 06:09 — 👍 0 🔁 0 💬 0 📌 0Also wrote a blog post that explains the proof in a shorter format and with less formality
blog.zksecurity.xyz/posts/fri-se...
Trying to reduce some headaches!
30.10.2025 13:24 — 👍 1 🔁 0 💬 0 📌 0It’s time to reveal the ZK Whiteboard S3 Module 1... because it's LIVE!
🥁🥁🥁🥁
How to Build Hash Functions, with Jean-Philippe (JP) Aumasson @aumasson.jp & @nicomnbl.bsky.social
Watch the full module here: zkhack.dev/whiteboard/s...
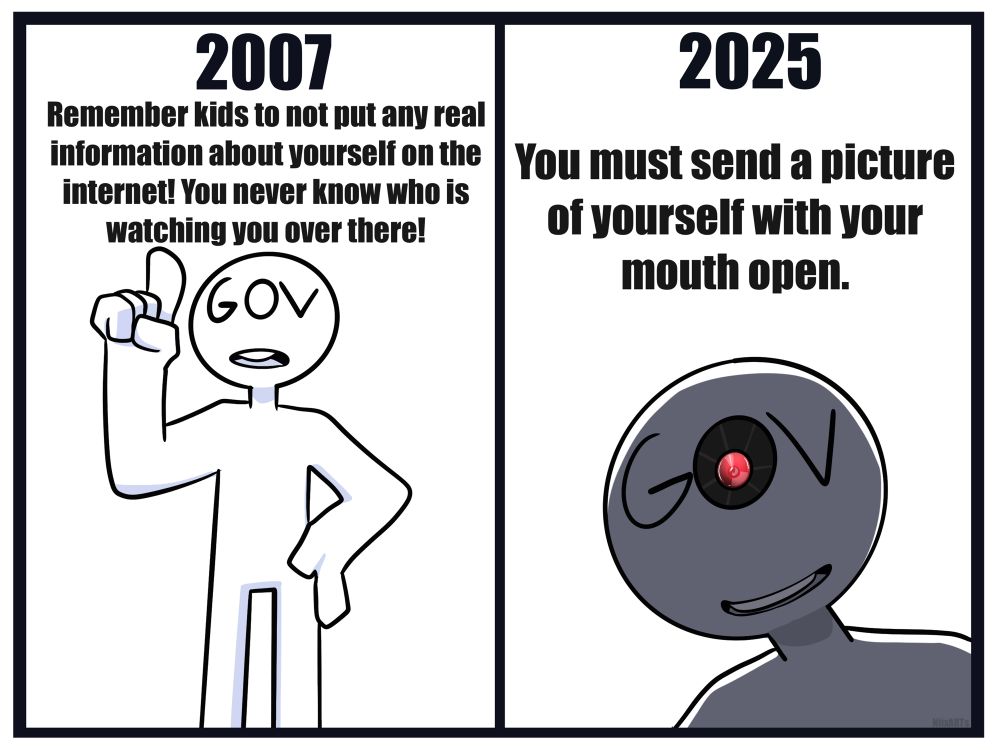
Time has changed
01.08.2025 08:15 — 👍 13895 🔁 5086 💬 70 📌 55
The ZK Podcast released an episode on local-first software this week!
@arro.bsky.social and @nicomnbl.bsky.social chat w @grjte.sh & @goblinoats.com about the foundations of local-first architecture, CRDTs and how ZK can be incorporated into these models.
zeroknowledge.fm/podcast/367/
Is this available on iOS too?
23.06.2025 19:50 — 👍 0 🔁 0 💬 1 📌 0Don't think this was the case for everyone but for me it was about keeping my phone number private (before Signal introduced usernames)
23.06.2025 19:45 — 👍 2 🔁 0 💬 0 📌 0I'm kind of conflicted over this.
Up to now my Signal has been almost exclusively for personal use and Telegram exclusively for connecting at conferences. And I've come to value this clean separation
To the point where I have said no to connecting over Signal

2/ As such, I wrote a research note to help cryptography engineers fully understand both techniques: baincapitalcrypto.com/a-deep-dive-...
11.06.2025 00:40 — 👍 3 🔁 1 💬 1 📌 0
I'm happy to finally open-source lattirust, a library for lattice-based zero-knowledge/succinct arguments! Lattirust is somewhat like arkworks, but for lattices; and like lattigo, but for arguments.
➔ github.com/lattirust
I wrote a thing on my colleagues Andrija and Guille's latest work
09.05.2025 16:09 — 👍 2 🔁 0 💬 0 📌 0Video or it didn't happen 👀
07.05.2025 12:28 — 👍 0 🔁 0 💬 0 📌 0Story of the ZK whiteboard series S2! The grant that supported it, how we came up with the topics, participation of our esteemed speakers, some crazy editing and how the bonus modules came to be
03.03.2025 18:49 — 👍 2 🔁 0 💬 0 📌 0But this might not work in your case depending on how strict you want to be on the caveat you mentioned
28.02.2025 14:30 — 👍 3 🔁 0 💬 0 📌 0The usual pattern is:
1. arrange the keys into a Merkle tree and give each signer their authentication path in that tree
2. signer produces a signature on the data
3. signer produces a ZKP that signature verifies against some public key, and that this public key is included in the Merkle tree
Part 2 starts with important terminology (pre-quantum vs post-quantum vs quantum). Or then explains how to make Bitcoin and Ethereum post-quantum secure via signature lifting and then talks about using quantum computers to make digital money
zeroknowledge.fm/podcast/297/
2/2
from the archive: Or Sattath came on the ZKPodcast to discuss quantum computing and its impact on cryptography. These two are some of my 𝐟𝐚𝐯𝐨𝐮𝐫𝐢𝐭𝐞 episodes of the show.
Part 1 covers the computation model, why it breaks some cryptography and effects on mining
zeroknowledge.fm/podcast/288/
1/2
A step towards fixing the recent attack on a Fiat-Shamir'd variant of GKR.
Tl;dr: do proof-of-work before deriving the FS challenge, this will make the hash prohibitively expensive to compute in-circuit.
Caveat: they only prove the security of their transform for 1-round protocols

sigh
23.02.2025 01:20 — 👍 5 🔁 2 💬 0 📌 0Correct!
22.02.2025 10:13 — 👍 1 🔁 0 💬 1 📌 0Terrible news
21.02.2025 16:31 — 👍 2 🔁 0 💬 0 📌 0Sublinear prover?!?! Incredible result!
17.02.2025 06:52 — 👍 7 🔁 1 💬 0 📌 0Bit of a tradeoff. We have O(1) proofs and verifiers using univariate polynomials, whereas sumcheck gives at best O(log(circuit))
07.02.2025 23:42 — 👍 1 🔁 0 💬 1 📌 0It replaces the "quotient polynomial". This was the method used to succinctly check that all the Plonk contraints or AIR rows are satisfied.
The advantage is that with sumcheck the prover no longer needs to perform polynomial division and therefore can run in linear time