
Did Huawei with it's HarmonyOS finally managed to move away from the Android Open Source Project (AOSP) code? 🤔
#infosec #technology #engineering #google #opensource #boredtoolbox
@boredtoolbox.bsky.social

Did Huawei with it's HarmonyOS finally managed to move away from the Android Open Source Project (AOSP) code? 🤔
#infosec #technology #engineering #google #opensource #boredtoolbox

4. Detection and Response / Red Teaming
5. Adjacent Benefits Risk Assessment Cycle
6. Continuous Control Monitoring
7. Federated Security Teams - Pull not Push
Subscribe to my newsletter: newsletter.boredtoolbox.pw
🚨 Security Engineering TIP:
Jim Collins' Flywheel concept to amplifying the effects of security programs:
1. Raise the Baseline by Reducing Control Costs
2. Threat Intelligence
3. From Inventories to Digital Twins: managed configurations for your assets
#security #engineering #infosec #technology

Latest confluence exploit Leads to LockBit Ransomware!
Read more and get TTPs here: boredtoolbox.pw/security-bul...
Subscribe to my newsletter: newsletter.boredtoolbox.pw
#lockbit #ransomware #malware #zeroday #bug #infosec #security #engineering #technology #boredtoolbox
This heavily exploited Windows vulnerability (tracked as ZDI-CAN-25373) allows attackers to exploit how Windows displays shortcut (.LNK) files to evade detection and execute code. Threat actors hide malicious command-line arguments within .LNK shortcut files
#infosec #security #engineering

I am option 4!
But option 9 gives me the willies! How are you able to do that on a daily basis? 😆
What about you?
#screens #coding #coder #github #programming #technology #engineer #boredtoolbox

🚨 Most of the Whatsapp zero click exploit via adding users to groups can be protected against by enabling extra protection ✅
Seetings > Privacy > Groups and chose who can add you to groups 👍
#security #exploit #bug #malware #zeroday #engineering #technology #boredtoolbox

When you finally catch the bug in your code and it's Friday!
Subscribe to my newsletter: https://buff.ly/4goEsHm
#infosec #security #engineering #technology #boredtoolbox

Real life photo of a "pre-hacked" cyber security of a company!
Subscribe to my newsletter: https://buff.ly/4goEsHm
#infosec #security #engineering #technology #boredtoolbox

When the Secure Intrusion Detection System worked and you block the attack! 😎 🖖
Subscribe to my newsletter to learn how: https://buff.ly/4goEsHm
#infosec

You selected computers because you were bad in language skills. But you joined a company and its...
Subscribe to my newsletter if your communication skills is just as bad as mine:
https://buff.ly/3ZiCdjE
#systemdesign #security #infosec #security #engineering #technology #boredtoolbox

Fingerprints, facial recognition and other personal information from Biostar 2, a biometrics based physical security company, discovered on publicly accessible database.
Security team:
Please rotate your credentials!
Subscribe to my newsletter: https://buff.ly/4goEsHm
#infosec
I saw a very weird person today at Starbucks. He had no smartphone, tablet or laptop. He just sat there drinking his coffee. What a psychopath!
#infosec
An amazing newsletter to go with your morning cup o' Joe:
https://buff.ly/4goEsHm
Shortcut to Secure System Design
- Walk to the coffee place
- Finish your coffee
- Walk back to the coffee place, to refill your coffee
☕
#infosec

Number of days without seeing some CEO talk about Deepseek in my feed:
Subscribe to my newsletter: https://buff.ly/4goEsHm
#deepseek #ai #llm #chatgpt #engineering #technology #boredtoolbox
Promise I use very less emojis in my newsletter:
https://buff.ly/4goEsHm
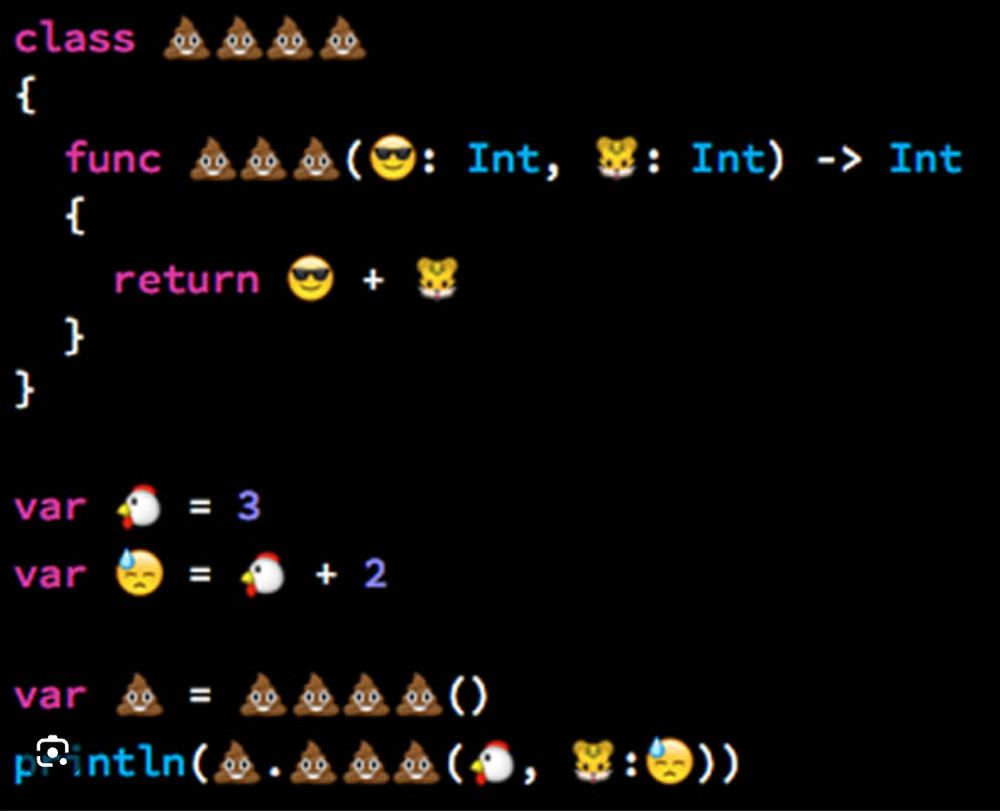
All the project needs now is a code review
The code:
#infosec
and subscription to an amazing newsletter like mine:
https://buff.ly/4goEsHm

All you need is a laptop and an internet connection!
#infosec
Subscribe to my newsletter and leave an honest review:
https://buff.ly/4goEsHm

Remember when game ratings matched user experience!
How can a game with an average 9 rating have such low audience rating?
#infosec
Read this before you start your infosec project 👉
https://buff.ly/3PXgc4x

🤔 What you should remember before you start your Cybersecurity project
✅ Check the comments
#infosec #career #cybersecurity #boredtoolbox
Way better than paid learning:
https://buff.ly/3WK7o5N

🔥 My list of free resources to upskill your Cyber Security Career
#career #infosec

My New Security Engineering Newsletter is also 🔥
https://buff.ly/3Eu163R

Heard the latest Sequoia (macOS 15) updated was 🔥
#infosec

OpenAI and Microsoft accuse Deepseek of stealing training data!
Deepseek:
#techmeme

Pros:
Have fun with computer codes ❤️
Cons:
4:43 AM
#techmeme