That is coming eventually but only just started on it really 😁. This is more “swiggery”
08.08.2025 20:24 — 👍 0 🔁 0 💬 0 📌 0
Something like that 😁!
08.08.2025 15:14 — 👍 1 🔁 0 💬 1 📌 0
It’s Defcon travel day today! Mega excited for an enormous number of reasons. If all goes well, many of them will become apparent roughly two weeks after it all ends…
06.08.2025 07:39 — 👍 1 🔁 0 💬 1 📌 0
I imagine smashing the state machine was pretty rough for that 😅?
30.07.2025 11:11 — 👍 0 🔁 0 💬 1 📌 0
I've gotten so lost in working on detection techniques that I've forgotten about a few very valid looking cases I found with the initial probe. 😄 Good news is, the tool looks like it might actually be useful regardless of what happens. But I guess I should focus on getting some exploits...
30.07.2025 07:03 — 👍 3 🔁 0 💬 1 📌 0
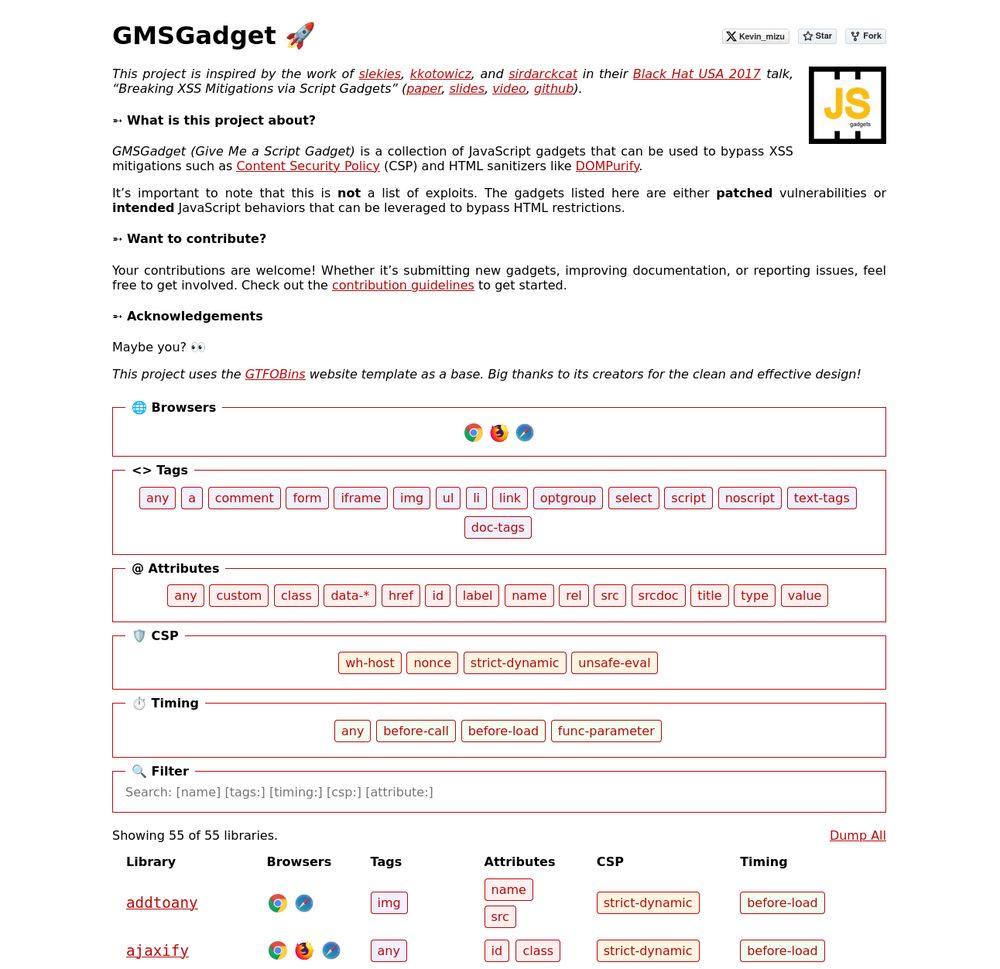
I'm happy to release a script gadgets wiki inspired by the work of @slekies, @kkotowicz, and @sirdarckcat in their Black Hat USA 2017 talk! 🔥
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
24.07.2025 15:31 — 👍 22 🔁 13 💬 1 📌 0
Not yet sure on how API access works yet, but a new online subdomain lookup service has arrived. subintel.tushal.io, seems pretty great!
24.07.2025 06:53 — 👍 0 🔁 0 💬 0 📌 0
Faaaantastic! 🔥
23.07.2025 14:59 — 👍 1 🔁 0 💬 0 📌 0
Everything I do leads me back to param-miner 😁. What a tool ⛏️
23.07.2025 07:46 — 👍 1 🔁 0 💬 0 📌 0
This is pretty cool. Things start getting really confusing when you look into the chunk extensions so... this is a huge help!
22.07.2025 14:00 — 👍 2 🔁 1 💬 0 📌 0
This has GOT to be as sticker?!
18.07.2025 13:01 — 👍 2 🔁 0 💬 1 📌 0
You're not ready for how powerful Custom Actions are.
You can now build your own AI hacking sidekicks that rewrite requests for you.
Forget typing payloads - just let your assistant do it.
🔥 Welcome to the future of offensive automation.
Get the source code:
github.com/PortSwigger/...
17.07.2025 13:44 — 👍 5 🔁 3 💬 1 📌 0
What on earth is this wizardry 🧙!
17.07.2025 13:57 — 👍 0 🔁 0 💬 1 📌 0
Manual testing doesn't have to be repetitive.
Meet Repeater Strike - an AI-powered Burp Suite extension that turns your Repeater traffic into a scan check.
Source code:
github.com/hackvertor/r...
Blog post:
portswigger.net/research/rep...
15.07.2025 13:48 — 👍 8 🔁 2 💬 0 📌 0
Submitted a second case based on the same research lead, this time using a technique I've not personally seen before to achieve a desync and a completely accidental exploit chain to achieve impact. Should make for a fun story even if this lead doesn't continue to produce results 🔥
14.07.2025 07:40 — 👍 2 🔁 0 💬 0 📌 0
This feels like a possible T-Shirt using the "I reported X and all I got was this lousy X" template.
11.07.2025 12:27 — 👍 1 🔁 0 💬 0 📌 0

Modeling CORS frameworks with CodeQL to find security vulnerabilities
Discover how to increase the coverage of your CodeQL CORS security by modeling developer headers and frameworks.
🧠 CORS misconfigurations are sneaky. Want to catch them with static analysis?
Kevin Stubbings from GitHub Security Lab shows how to model CORS middleware in CodeQL—using Go’s Gin framework as a case study.
Great insights for researchers & devs:
github.blog/security/app...
10.07.2025 19:31 — 👍 3 🔁 2 💬 0 📌 0


🔥 Want to think like a hacker and truly understand JavaScript?
💻 JavaScript for Hackers is your guide to breaking, bending, and mastering the language like never before.
09.07.2025 17:11 — 👍 16 🔁 6 💬 1 📌 0
Close enough! AMA: docs.google.com/forms/d/e/1F...
I'll do a live stream answering questions some time soon :)
08.07.2025 13:24 — 👍 6 🔁 4 💬 0 📌 1
I noticed in my latest post that a lot of the initial traffic was mobile. And later on it’s been desktop and others. Thank god someone told me to check the mobile view for all the markdown code 😂
07.07.2025 15:17 — 👍 0 🔁 0 💬 0 📌 0
Gooood to know 😁 thanks!
07.07.2025 12:08 — 👍 1 🔁 0 💬 0 📌 0
Did you add this in because of your research? 🤔 just came across it in the wild.
05.07.2025 19:38 — 👍 1 🔁 0 💬 1 📌 0

New video! Getting Into Cybersecurity - An Interview with James Kettle!
In this episode, James Kettle talks about how he got started in security research, and how you can pivot into this rare but worthwhile role.
Watch now: youtu.be/S64Eq0Y3SrY
Listen on Spotify: open.spotify.com/show/5m5711J...
02.07.2025 14:49 — 👍 9 🔁 2 💬 0 📌 0
YouTube video by Tib3rius
Getting Into Cybersecurity - An Interview with James Kettle!
Interested in pushing hacking techniques beyond the state of the art, or breaking into full-time security research? I recently had a great chat with Tib3rius on the topic! Watch it here:
www.youtube.com/watch?v=S64E...
02.07.2025 14:56 — 👍 11 🔁 3 💬 1 📌 2
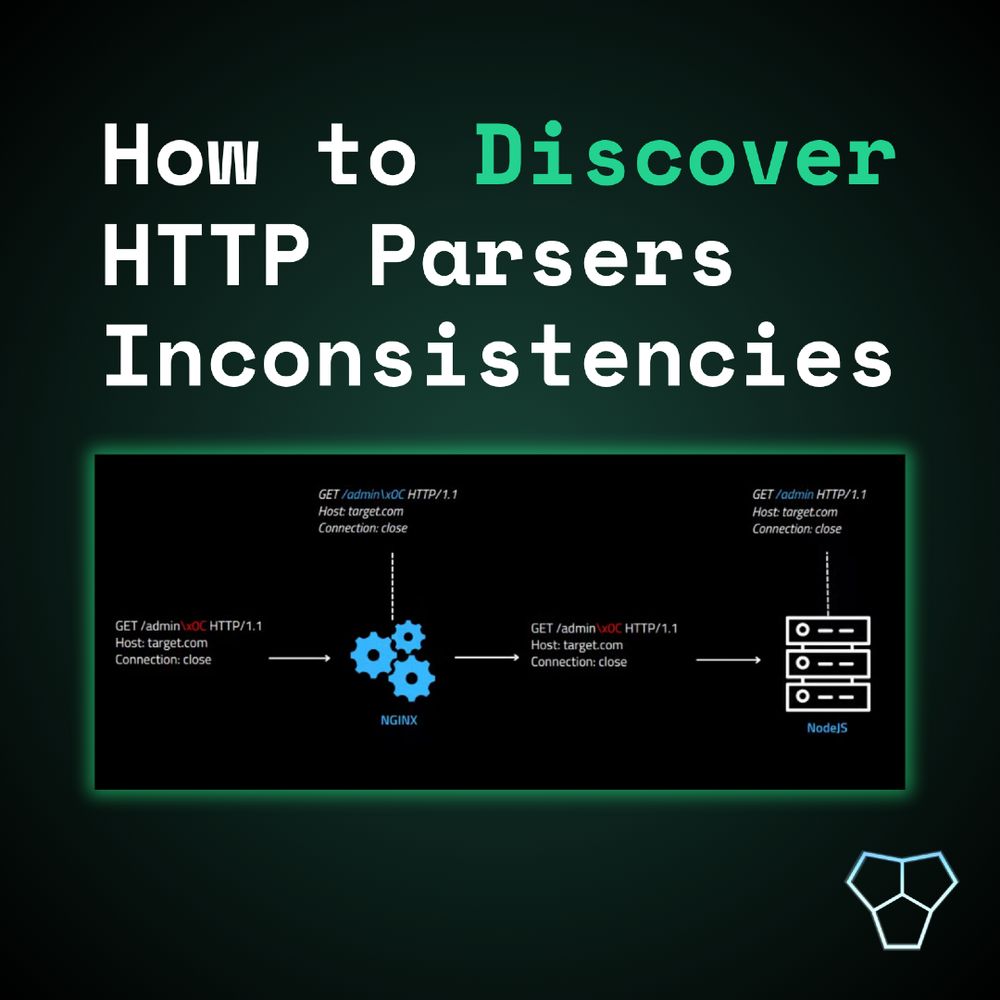
Nginx normalizes paths (/../, %2e, etc.) before applying access rules like: location = /admin { deny all; }
But backends like Node.js or PHP handle decoding again, and differently.
02.07.2025 08:21 — 👍 8 🔁 2 💬 1 📌 0
Building detection techniques is an underrated part of research for me. I imagine working on solid detection code for a DAST scanner would be fun. Today I made a small change based on a particularly sensitive header and suddenly a bunch of new cases popped up in, critically, a different tech stack.
27.06.2025 08:03 — 👍 4 🔁 0 💬 0 📌 0
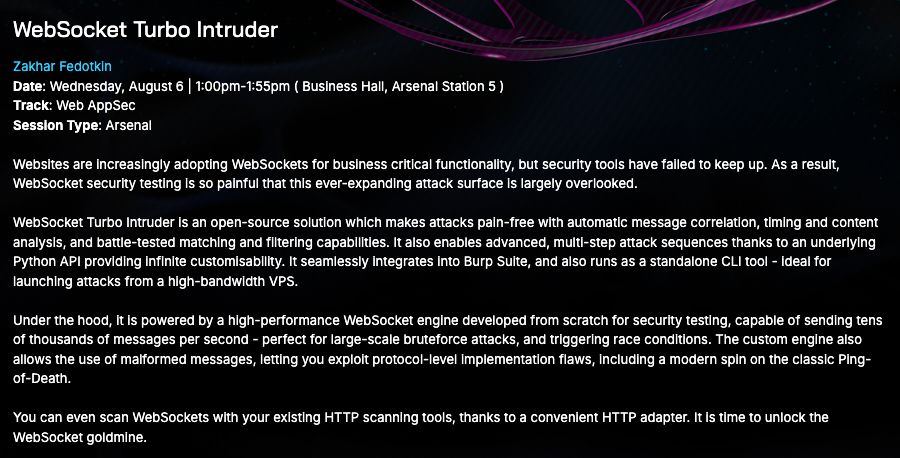
Thrilled to announce: I’ll be presenting a major new version of WebSocket Turbo Intruder at Black Hat Arsenal 2025! This open-source toolkit makes high-speed, advanced WebSocket attacks practical and painless.
26.06.2025 13:56 — 👍 9 🔁 3 💬 1 📌 0
💻 hacker / relapsed bug bounty hunter
💤 mostly tired of tech
✍️ occasional blogger
🎵 amateur jazz pianist
⁉️ chess enthusiast
🤿 daydreaming of scuba diving
🌐 https://honoki.net
Staff Security Researcher @datadoghq | DEF CON/Black Hat USA main stage speaker | he/him | OSCP OSWE | I turned hacking AWS into a career | Tweets are my own | Created https://hackingthe.cloud
🇪🇪🏳️⚧️ | Archivist | 9 CVEs in Chrome | MapartCraft | Horse | rebane2001#3716 | Lyra 🦊
she/her
https://lyra.horse/
@rebane2001@infosec.exchange
CTF player with The Flat Network Society - bug bounty & web security research
Creators of BloodHound | Experts in Adversary Tradecraft | Leaders in Identity Attack Path Management
Hacker, Bug Bounty Hunter, Pentester,...
From Namur, BE.
websec obsessed
https://sebsrt.xyz
Cutting-edge security research by
Sonar to educate the world about code security across all software.
We're also at @SonarResearch@infosec.exchange 🦣 and @Sonar_Research 🐦
Securing open source software, together
Paw / Pwn / Purr
@nbk_2000
Aspiring Bug Bounty Hunter & dev of tools: GAP, xnLinkFinder & waymore, featured in "Bug Hunter’s Methodology: Application Analysis v1" by JHaddix 🤘
RTFM🧐
Hacker grinding for L1gh7 and Fr33dφm, straight outta the cosmic realm.
Co-founder @ethiack.com
https://0xacb.com
CTF / Bugbounty / Web Guy
Infosec professional, beverage snob, and fantasy book consumer. Vice President @ Atredis Partners. Forever terrified of Kithicor.
Web security fiddler. Bug bounty bastard. Sometimes I cut shapes.
Web Security Expert | Bug Hunter | Käferjäger
Infosec addicted IT guy 🕵️♂️👨💻 | HTB Guru | Researcher & Pentester 🖊️ | White-Hat 🎩 | Bugs find me 🪲 | Part of the awesome #kaeferjaeger crew 💥