Burp collaborator just got a bunch a new features. Credits go to our @compass-security.com Basel team member, Andreas 🙏
15.07.2025 06:29 — 👍 6 🔁 1 💬 0 📌 0
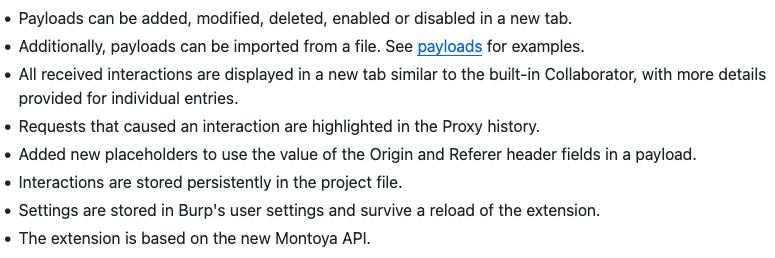
We've just released a massive update to Collaborator Everywhere! This is a complete rewrite by @compass-security.com which adds loads of features including in-tool payload customization. Massive thanks to Compass for this epic project takeover. Check out the new features:
14.07.2025 14:51 — 👍 19 🔁 7 💬 1 📌 1
Thanks a lot for the mention, @jameskettle.com! Really appreciate your attribution. Huge kudos to the team for the research, dedication, and collaboration that went into this work. Proud to see your efforts recognized. #AppSec #WebSecurity #Pentesting @burpsuite.bsky.social FTW!
15.07.2025 06:25 — 👍 2 🔁 0 💬 0 📌 0

LLM-based vuln hunting just leveled up with xvulnhuntr - a fork of vulnhuntr with support for: C#, Java, Go. Read @rationalpsyche.bsky.social's blog post and go grab the project on GitHub.
blog.compass-security.com/2025/07/xvul...
08.07.2025 08:41 — 👍 3 🔁 2 💬 0 📌 0
Indeed. 😀
27.06.2025 08:11 — 👍 0 🔁 0 💬 0 📌 0

Exploiting the @ubiquiti.bsky.social AI Bullet camera for #Pwn2Own made us sweat more than once.
But persistence paid off. Our detailed blog post is now live: blog.compass-security.com/2025/06/pwn2...
#penetrationtest #pentest #iot #embedded #cybersecurity
www.compass-security.com/en/services/...
26.06.2025 14:38 — 👍 5 🔁 2 💬 1 📌 0

Azure IAM is meant to protect your infrastructure. But misconfigurations do the opposite.
5 critical IAM & Entra ID risks - and how to mitigate them: blog.compass-security.com/2025/06/the-...
25.06.2025 12:18 — 👍 2 🔁 0 💬 0 📌 0

High-resolution photo of Compass Security’s IoT and industrial penetration-testing workspace: on a light wooden workbench a large-lens, black surveillance camera sits half-disassembled beside its white Synology® housing, revealing the internal printed-circuit board, image sensor and ribbon connectors targeted during firmware extraction and vulnerability analysis. A chaotic web of multicolored diagnostic leads, Ethernet patch cables, alligator clips, UART/serial breakout wires and power adapters snakes across the table, illustrating real-world hardware hacking, fault-injection and secure-boot bypass techniques used in red-team assessments of networked CCTV, smart-factory and critical OT devices. The blue pentagonal TROOPERS25 shield logo occupies the upper-right corner, signalling that this lab scene supports Compass Security’s conference presentation on Pwn2Own-grade research into surveillance-camera exploits, remote-code-execution vectors and zero-day discovery. The image underscores expert penetration-testing methodology—threat modeling, reverse engineering, embedded Linux analysis, secure-element probing and API fuzzing.
Thrilled for #TROOPERS25 Thursday! Emanuele & @yvesbieri.bsky.social share #Pwn2Own wins on #surveillance cams. Method, #exploit, lessons. Drop in, trade war-stories!
Talk: troopers.de/troopers25/t...
Compass pentest: www.compass-security.com/en/services/... #cybersecurity #iot #hw #fw #ot
25.06.2025 05:59 — 👍 8 🔁 5 💬 0 📌 0

LinkedIn: your job history and your attacker’s roadmap. In his latest blog post, Ivano Somaini shows how malicious actors could mine profiles, badges, and more. Learn from our experienced Social Engineer: blog.compass-security.com/2025/06/link...
11.06.2025 12:20 — 👍 1 🔁 0 💬 0 📌 0

Primate traits run deep at Teleboy smart, curious, and always evolving. If that sounds like you, challenge the boundaries of their infra and secure streaming, internet, and phone experience of 400'000+ users. #bugbounty #ethicalhacking #cybersecurity bugbounty.compass-security.com/bug-bounties...
02.06.2025 07:41 — 👍 3 🔁 1 💬 0 📌 0

Many CI/CD tools promise to keep your dependencies up to date - but if misconfigured, they can expose your organization. From token leaks to MR hijacks, Jan's latest blog post shows how bad configuration can turn a security tool into an attack vector. 🛠️💣
blog.compass-security.com/2025/05/reno...
27.05.2025 07:24 — 👍 6 🔁 3 💬 0 📌 0
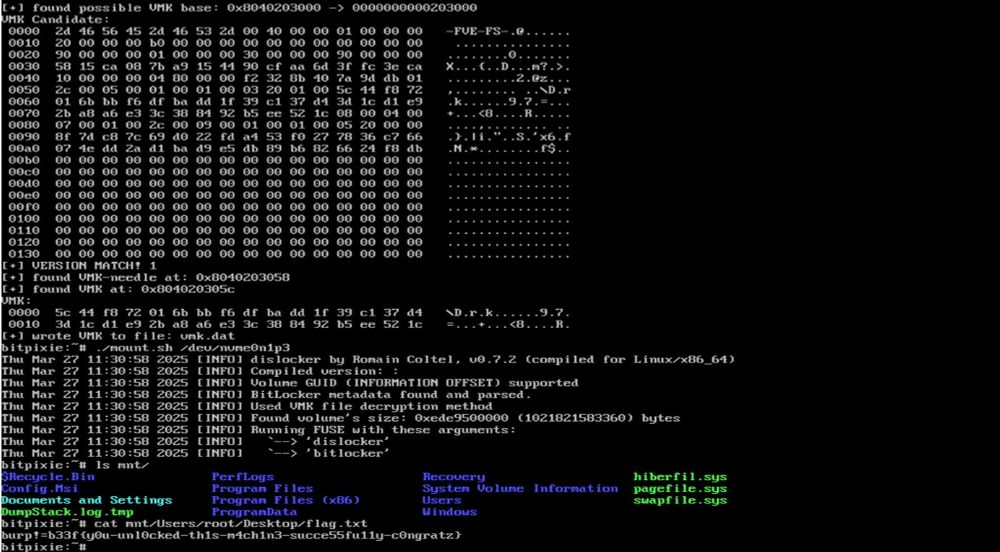
In his latest blog post, Marc Tanner @brain-dump.org shows how to bypass BitLocker using BitPixie (CVE-2023-21563) and signed Microsoft components only. Check out the blog post for a PoC and a demo. #BitLocker #RedTeam
blog.compass-security.com/2025/05/bypa...
13.05.2025 12:38 — 👍 9 🔁 5 💬 0 📌 1

Tired of sifting through Entra ID manually? EntraFalcon is a PowerShell tool that flags risky objects configs & privileged role assignments with ⚡ Scoring model 📊 HTML reports 🔒 No Graph API consent hassle. Get it now: blog.compass-security.com/2025/04/intr...
#EntraID #IAM
29.04.2025 11:08 — 👍 6 🔁 5 💬 0 📌 0
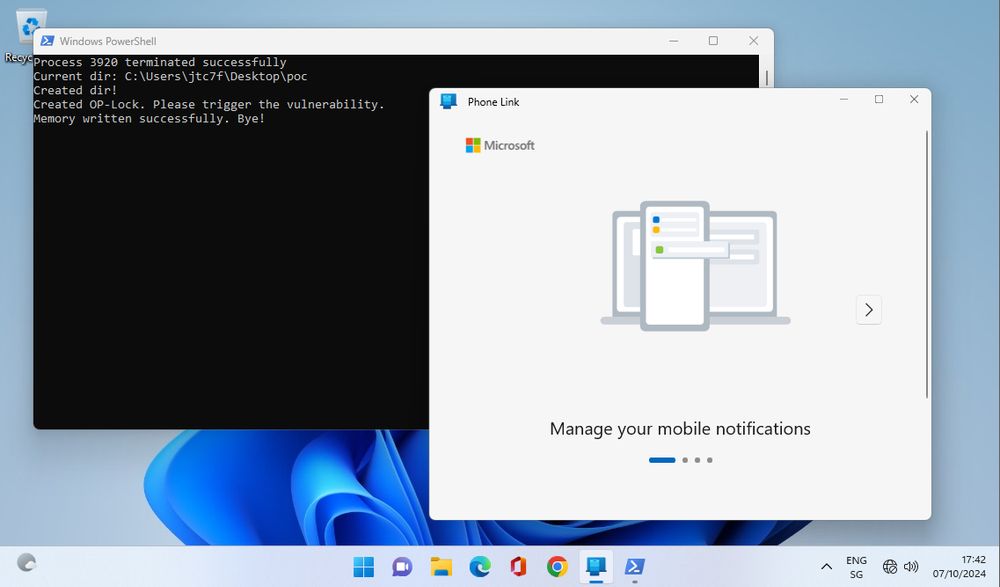
3 milliseconds to admin — Our analyst John Ostrowski turned a DLL hijacking into a reliable local privilege escalation on Windows 11. He chained opportunistic locks, and API hooking to win the race to CVE-2025-24076 & CVE-2025-24994. Read his blog post: blog.compass-security.com/2025/04/3-mi...
15.04.2025 09:00 — 👍 21 🔁 5 💬 0 📌 0

How can I become a Red Team Operator? – Yours sincerely, A recent graduate.
We break down what it takes and why there's no shortcut, and why pentesting is the place to start: blog.compass-security.com/2025/04/i-wa...
#redteam #infosec #pentest #career
02.04.2025 07:09 — 👍 0 🔁 0 💬 0 📌 0

Dear #bughunter, gear up! dEURO launches its program. Hunt for vulnerabilities, secure the oracle-free #stablecoin, and get rewarded. #API, mobile apps and solidity contract in scope. Max. bounty at CHF 10'000. Ready to mint your victory? 🚀 #DeFi bugbounty.compass-security.com/bug-bounties...
26.03.2025 13:14 — 👍 3 🔁 1 💬 0 📌 0
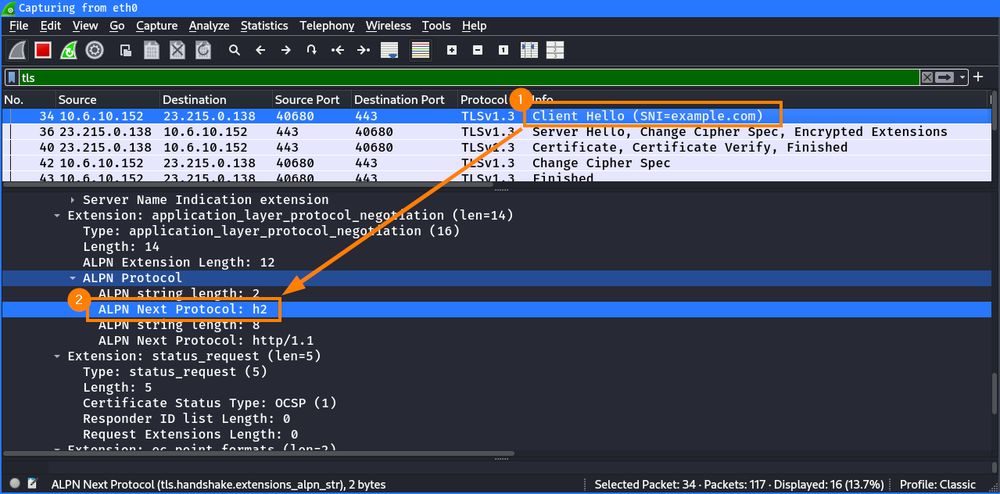
No system is perfect!
In part 4 of his blog series, @emanuelduss.ch shows how detection mechanisms of web filters can be bypassed: blog.compass-security.com/2025/03/bypa...
#pentest #network
20.03.2025 09:49 — 👍 5 🔁 3 💬 0 📌 0
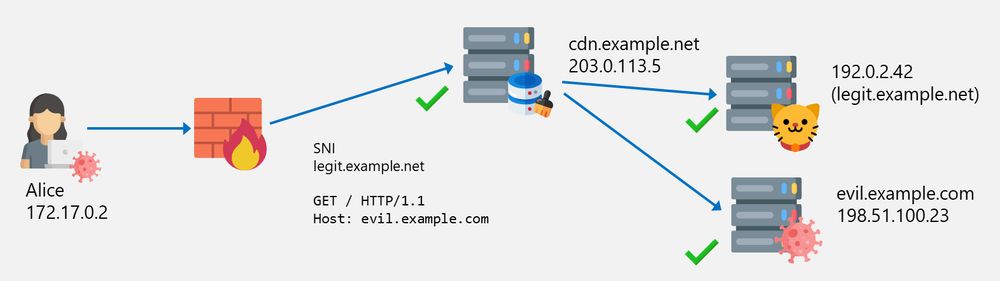
Web filters can often be bypassed in various ways. In part 3 of his blog series, @emanuelduss.ch explains how Domain Fronting works, how attackers use it to evade restrictions and how you can detect it.
Read the blog post to find out: blog.compass-security.com/2025/03/bypa...
#pentest #network
18.03.2025 08:02 — 👍 4 🔁 1 💬 0 📌 0

IT-Security kann stressig sein – wir sorgen für Entspannung! Besuchen Sie uns auf der #secIT2025 und holen sich eine kleine Auszeit.
#CyberSecurity #ITSecurity #secit #StaySafe
17.03.2025 08:29 — 👍 0 🔁 0 💬 0 📌 0
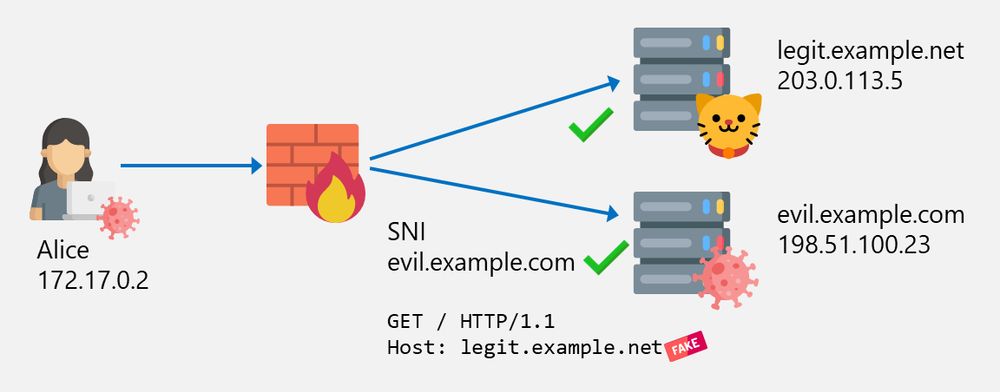
Still think your web filter is secure? Host Header Spoofing might prove otherwise. In part 2 of his post series, @emanuelduss.ch breaks down this bypass technique - how it works and how to stop it. Check it out: blog.compass-security.com/2025/03/bypa...
#pentest #network
13.03.2025 08:04 — 👍 4 🔁 0 💬 0 📌 0
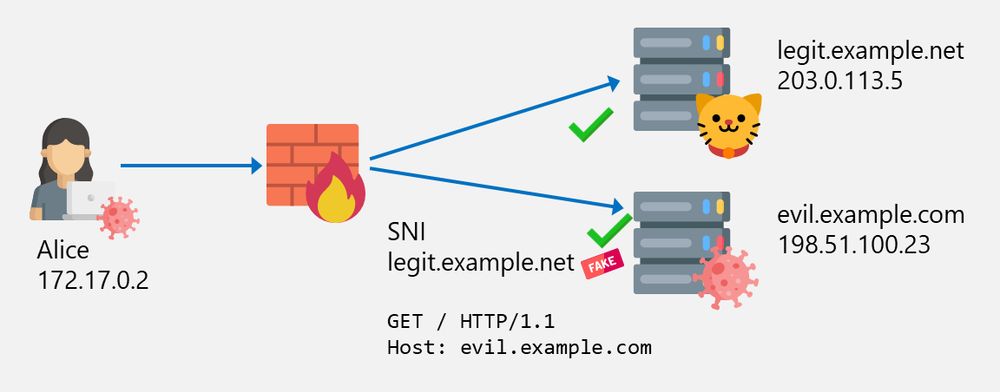
Think your web filter is foolproof? Think again. Our blog series explores SNI spoofing, Host header spoofing, and Domain Fronting—techniques attackers use to slip past restrictions. Learn how they work and how to stop them!
blog.compass-security.com/2025/03/bypa...
11.03.2025 11:03 — 👍 5 🔁 2 💬 0 📌 1

Passwords are a thing of the past! Dario Caluzi’s latest blog post explains why passkeys are the future of authentication. They offer a faster, more secure way to log in - no passwords, no phishing risks, just seamless authentication.
blog.compass-security.com/2025/02/pass...
#Passkeys #Passwordless
25.02.2025 08:44 — 👍 3 🔁 0 💬 0 📌 0

Avoid LDAP monitoring by leveraging local registry data with certipy parse! Check out our latest pull request and read Marc Tanner’s (@brain-dump.org) blog post: blog.compass-security.com/2025/02/stea...
11.02.2025 12:28 — 👍 7 🔁 4 💬 0 📌 1

Die Kunst des Penetrationstests: Von der Risikobewertung über die Planungsphase und die rechtlichen Rahmenbedingungen bis hin zur Interpretation der Testberichte - Erfahre, wie du die IT-Sicherheit durch gezielte Tests stärkst. Live auf der secIT. 👉 Gleich anmelden: secit-heise.de/tickets#kaufen
07.02.2025 07:05 — 👍 1 🔁 1 💬 0 📌 0

Unlock the power of BloodHound Community Edition! 🚀 We’ve updated our custom queries to help you uncover misconfigurations and attack paths in AD. Read @emanuelduss.ch’s blog post for tips and tricks to get started.
blog.compass-security.com/2025/01/bloo...
#BloodHoundCE #ActiveDirectory
28.01.2025 15:20 — 👍 11 🔁 3 💬 0 📌 0

The Compass #Pwn2Own team will be targeting the Alpine iLX-507 In-Vehicle Infotainment at Pwn2Own Automotive #P2OAuto in Tokyo. Turns out it’s a popular target and our colleagues were drawn by @thezdi.bsky.social to attempt an exploit as 8th out of 10 groups targeting the device. Schedule tba
21.01.2025 06:10 — 👍 10 🔁 2 💬 0 📌 0
vegan btw. appsec @ mandiant/google cloud. opinions my own etc
Hacker of Planets and Things
ヾ(⌐■_■)ノ♪
https://tommyboyhacking.github.io
Hacker / Farmer / Builder / Breaker
Prev: Code4rena, Okta, Auth0, GitHub, npm, ^lift, &yet, Symantec.
Pioneered BlindXSS & DVCS Pillaging
npm audit is my fault. More info: https://evilpacket.net
Just a passionate dev, learning from this community daily.
✨ Sharing the entire journey - bugs, breakthroughs, and banter. 🚀
Degenerate Artist / Sysadmin / Cybersecurity
Swiss Penetration Tester & Red Teamer, Password Cracker, Team HashMob
Infosec analyst.
"La bêtise c'est quelqu'un qui vit et qui dit ça me suffit" - Jacques Brel.
Los "-ismos" me parecen una perdida de tiempo.
Langweile mich nicht bitte 😎
💙🌊🗽🏳️⚧️🏳️🌈🇪🇸🇩🇪🇫🇷🇵🇸🇺🇦💻✈️🎸👽
Maester is your Microsoft Security test automation framework!
Maester is a PowerShell based test automation framework to help you stay in control of your Microsoft security configuration.
Learn more → maester.dev
Azure cloud architect from Denmark
red & purple team operations,*nix plumber,bass,org-(mode/roam),🇨🇭🇿🇦,🌶 & 🎶 addict. SMI²LE. Herbivore.
Opinions my own, not that of my employer
Hacker & CEO @SocialProofSec security awareness/social engineering training, videos, talks | 3X @DEFCON🥈 | Chair @WISPorg | @CISAgov Technical Advisory Council under Director Jen Easterly
I teach cryptography at Johns Hopkins. https://blog.cryptographyengineering.com
*Can’t decide my path—there’s just too much to protect.*
Forever learning, always adapting. 💻✨
#CyberSecurity #ThreatHunter #InfoSec
Automotive Security, Pentesting, Embedded | Pwn2Own Automotive 2024
Embedded device security researcher / #VR / #Pwn2Own / #RE
There's no crying in baseband. Security researcher, !SpamAndHex CTF player, Pwn2Own winner, founder of TASZK Security Labs.

























