The worst bugs are the ones where the code mostly works. Low-level AI coding is so complex that I (an the AI that I write code with), produce an annoying number of them.
10.05.2025 00:32 — 👍 25 🔁 4 💬 2 📌 1
You asked, we delivered: Binary Ninja 5.0 brings major iOS reversing upgrades! DYLD Shared Cache is now a first-class feature, with up to 18x faster performance and way smarter analysis across the board. binary.ninja/2025/04/23/5...
24.04.2025 19:44 — 👍 12 🔁 5 💬 1 📌 0
 01.04.2025 02:46 — 👍 37 🔁 7 💬 2 📌 0
01.04.2025 02:46 — 👍 37 🔁 7 💬 2 📌 0
 01.04.2025 04:11 — 👍 14 🔁 2 💬 0 📌 0
01.04.2025 04:11 — 👍 14 🔁 2 💬 0 📌 0

Fileless lateral movement with trapped COM objects | IBM
New research from IBM X-Force Red has led to the development of a proof-of-concept fileless lateral movement technique by abusing trapped Component Object Model (COM) objects. Get the details.
[Blog] This ended up being a great applied research project with my co-worker Dylan Tran on weaponizing a technique for fileless DCOM lateral movement based on the original work of James Forshaw. Defensive recommendations provided.
- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...
25.03.2025 21:21 — 👍 15 🔁 11 💬 0 📌 1
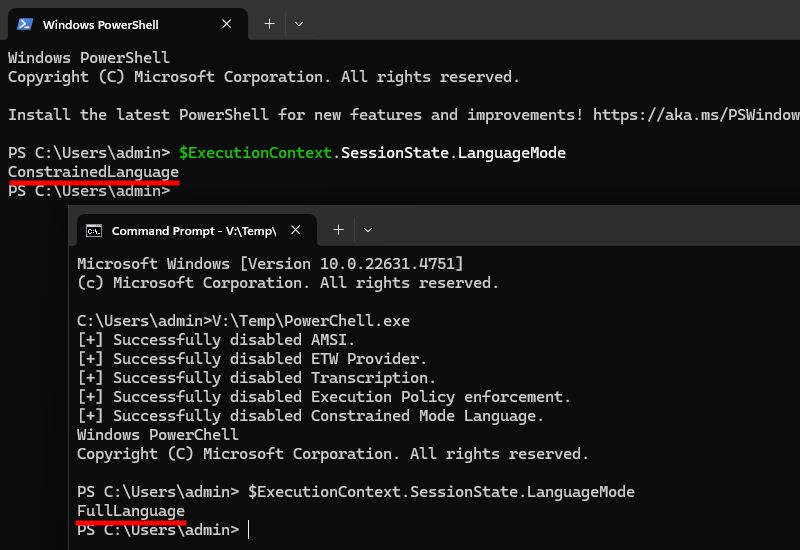
Screenshot showing the execution of the proof-of-concept named PowerChell in comparison to a typical PowerShell prompt. In particular, it shows that PowerChell is able to bypass the Constrained Language Mode (CLM).
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
19.02.2025 09:13 — 👍 43 🔁 19 💬 2 📌 2
I’m very excited to announce that we at V8 Security have finally published our first version of Fuzzilli that understands Wasm!
Go check it out at https://github.com/googleprojectzero/fuzzilli.
While we still have a way to go in improving it, we think it shows a promising approach!
04.02.2025 19:34 — 👍 31 🔁 16 💬 1 📌 1

Profile Explorer is a tool for viewing CPU profiling traces collected through the Event Tracing for Windows (ETW) infrastructure on machines with x64 and ARM64 CPUs
github.com/microsoft/pr...
24.01.2025 21:05 — 👍 16 🔁 6 💬 3 📌 0
Lots of questions about the new admin protection feature in Windows so the MORSE team decided to do a writeup. Working on part 2 now, should be done in a day or two. techcommunity.microsoft.com/blog/microso...
23.01.2025 23:09 — 👍 10 🔁 7 💬 0 📌 0
Project Zero
Just unrestricted an issue that shows a fun new attack surface. Android RCS locally transcribes incoming media, making vulnerabilities audio codecs now fully-remote. This bug in an obscure Samsung S24 codec is 0-click
project-zero.issues.chromium.org/issues/36869...
10.01.2025 00:08 — 👍 38 🔁 16 💬 1 📌 2
Kids these days don't even know how much opportunity they have to learn hacking from actual pros.
I know there is a lot of content out there, so it can be hard to find the good stuff. But 10 years ago you had to be lucky to find at least something.
Anyway, watch this 👇
31.12.2024 10:10 — 👍 61 🔁 8 💬 2 📌 0
Stability in AFL++/LibAFL is quantified by the percentage of edges in the target that are considered “stable”. If repeatedly sending identical inputs results in the data traversing the same path through the target each time, then the stability is determined to be 100%.
24.12.2024 21:18 — 👍 1 🔁 1 💬 1 📌 0
YouTube video by Microsoft Security Response Center (MSRC)
BlueHat 2024: S09: Pointer Problems – Why We’re Refactoring the Windows Kernel
Important news: Microsoft is working to bring SMAP into Windows
www.youtube.com/watch?v=-3jx...
Great talk by Joe Bialek from MORSE team
16.12.2024 04:29 — 👍 18 🔁 7 💬 1 📌 0
GitHub - microsoft/markitdown: Python tool for converting files and office documents to Markdown.
Python tool for converting files and office documents to Markdown. - microsoft/markitdown
Microsoft just released a tool that lets you convert Office files to Markdown. Never thought I'd see the day.
Google also added Markdown export to Google Docs a few months ago.
github.com/microsoft/markitdown
13.12.2024 20:25 — 👍 529 🔁 127 💬 24 📌 24

Cover for the book "Building a Debugger" from No Starch Press. A robot sits at a drafting table drawing a complex machine. In the top-right corner of the table, there is a post-it note with a bug drawn on it and crossed out
The cover for my book on how debuggers work is here!
Preorders are still 25% off: nostarch.com/building-a-d...
14.12.2024 00:05 — 👍 182 🔁 37 💬 9 📌 3

4 panel of a comic style drawing. First panel has a T-rex doing a standup comic routine with a speech bubble containing the words "What's the difference between a light bulb and a cybersecurity professional?" Second panel has these words in the speech bubble "A light bulb stops working when it burns out." Third panel has a drawing of sad looking dinosaurs while the fourth panel has the T-rex stand up comedian with tears on its eyes.
This is my annual reminder to y'all wonderful folks in infosec: please take care & you're important. Your physical & mental health are important aspects of your life. The work we do & the environments we work in can significantly impact these. There is no shame in taking care of yourself first.💜
12.12.2024 01:00 — 👍 126 🔁 24 💬 1 📌 4

Originally the default wallpaper of Microsoft's Windows XP, this photo shows green rolling hills with a vibrant blue sky and white clouds in the background. Charles O'Rear took the photo in California, USA.
We've always been a fan of blueskies.
04.04.1975 12:00 — 👍 11866 🔁 2119 💬 653 📌 657

Binary Ninja - internship-2025
Binary Ninja is a modern reverse engineering platform with a scriptable and extensible decompiler.
Want to help build Binary Ninja this summer? Our 2025 summer internship application process is live!
02.12.2024 19:13 — 👍 9 🔁 8 💬 0 📌 0

A squirrel perched on a thin tree branch surrounded by yellow leaves, holding a small piece of food in its front paws. The squirrel faces the camera directly, with its bushy tail visible behind it. The background shows a clear blue sky.
Chunky boi
02.12.2024 12:50 — 👍 231 🔁 13 💬 7 📌 2

Microsoft using yugioh card on hacker "that's not a security boundary"
01.12.2024 16:02 — 👍 176 🔁 17 💬 6 📌 1
Project Zero and High+ BigSleep Bugs
Automated, Nov 2025+
mobile security / symbolic execution . he / him
🌱 Grow your cybersecurity skills with concise and well-edited courses - in early access now! Created by @LiveOverflow and @stacksmashing.
https://hextree.io/
Founder & Security Researcher @alleleintel.com
Blog: https://blog.andersonc0d3.io
Reversing, hacking, cracking, coding, caffeine junkie, OSCP, ALLES! - CTF Member | thevamp@infosec.exchange
KEYWORDS ➡︎ cats, hacking, reverse engineering, llvm, binary analysis, side channel analysis, FPGAs, NFC/EMV tricks
Previously Pay Security
he/him
(Unofficial) VP of Developer Productivity at Microsoft. Developer tools, engineering systems, .NET, C#, Roslyn, Visual Studio, Editor, WPF, Avalonia, MSBuild.
We are the National Cyber Security Centre – part of the UK’s intelligence & cyber agency GCHQ. We help to make the UK the safest place to live and work online.
We’re here to provide world-leading vulnerability research and research capabilities. From browsers, mobile, automotive and everything in between.
www.interruptlabs.co.uk
THE news & reviews site for Microsoft, Windows, Xbox, AI, and PC gaming. Tips: tips@windowscentral.com | Not part of Microsoft.
A programming language empowering everyone to build reliable and efficient software.
Website: https://rust-lang.org/
Blog: https://blog.rust-lang.org/
Mastodon: https://social.rust-lang.org/@rust
Adversary Services @xforce
https://h4wkst3r.github.io
GDC Festival of Gaming returns March 9-13, 2026, in San Francisco!
Security Researcher, Musician, SANS Fellow and Offensive Ops Curriculum Lead, Off By One Security, Gray Hat Hacking Author. Berkeley, California
 01.04.2025 02:46 — 👍 37 🔁 7 💬 2 📌 0
01.04.2025 02:46 — 👍 37 🔁 7 💬 2 📌 0
 01.04.2025 04:11 — 👍 14 🔁 2 💬 0 📌 0
01.04.2025 04:11 — 👍 14 🔁 2 💬 0 📌 0