mscoree.dll, RunDll32ShimW lolbin
www.hexacorn.com/blog/2025/05...
bohops
@bohops.bsky.social
Mostly on X
@bohops.bsky.social
Mostly on X
mscoree.dll, RunDll32ShimW lolbin
www.hexacorn.com/blog/2025/05...
Moving from pizza box servers and large tower PCs to mini and pico-style PCs has been absolutely amazing. A few NUCs and Pi s going along way.
28.04.2025 14:40 — 👍 0 🔁 0 💬 0 📌 0When I was doing sysadmin work back in the day, I inherited a few systems like this. Legacy but rock solid. Worse part was no one knew what it was used for until we decided to disconnect the network cable one day.... 😀
27.04.2025 12:05 — 👍 1 🔁 0 💬 1 📌 0Thank you, Casey! It definitely means a lot coming from you.
25.03.2025 21:41 — 👍 0 🔁 0 💬 0 📌 0
[Blog] This ended up being a great applied research project with my co-worker Dylan Tran on weaponizing a technique for fileless DCOM lateral movement based on the original work of James Forshaw. Defensive recommendations provided.
- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...

I am excited to announce the first conference dedicated to the offensive use of AI in security! Request an invite at offensiveaicon.com.
Co-organized by RemoteThreat, Dreadnode, & DEVSEC.
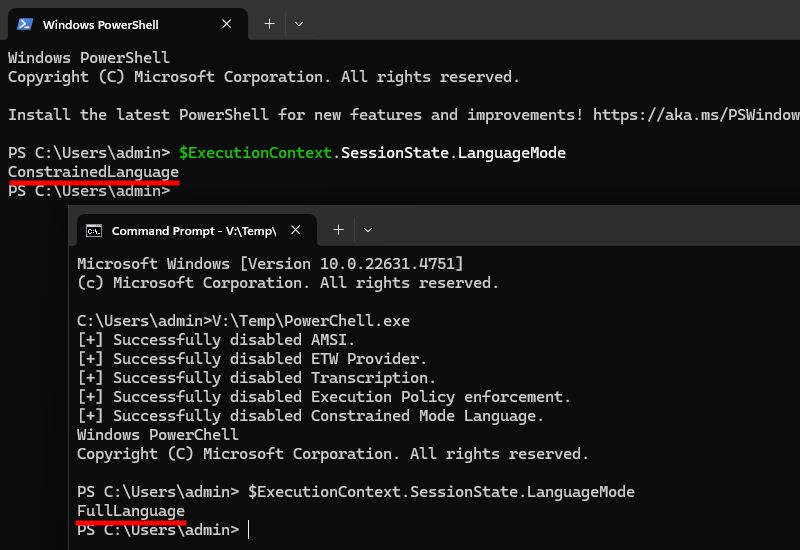
Screenshot showing the execution of the proof-of-concept named PowerChell in comparison to a typical PowerShell prompt. In particular, it shows that PowerChell is able to bypass the Constrained Language Mode (CLM).
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
New blog post on the abuse of the IDispatch COM interface to get unexpected objects loaded into a process. Demoed by using this to get arbitrary code execution in a PPL process. googleprojectzero.blogspot.com/2025/01/wind...
30.01.2025 18:37 — 👍 65 🔁 41 💬 2 📌 0Apex Farms Red Team! I'm in.
15.01.2025 14:35 — 👍 1 🔁 0 💬 0 📌 0You can find our @shmoocon.bsky.social presentation slides at the below GitHub repo. Thanks again to all that attended. Also, thank you to the conference organizers for putting on a great con and having us! #shmoocon
github.com/h4wkst3r/Con...