One of the fastest ways to trigger me in a work context these days is to whisper "Mustang Panda". Instant menty b ✨
29.01.2026 13:50 — 👍 2 🔁 1 💬 1 📌 0Mark Kelly
@mkyo.bsky.social
🇨🇳 Threat Research at Proofpoint
@mkyo.bsky.social
🇨🇳 Threat Research at Proofpoint
One of the fastest ways to trigger me in a work context these days is to whisper "Mustang Panda". Instant menty b ✨
29.01.2026 13:50 — 👍 2 🔁 1 💬 1 📌 0In addition to espionage threat actors, financially motivated cybercriminals have been exploiting the WinRAR vulnerability CVE-2025-8088.
The highly effective ecrime actor, typically seen distributing Koi Stealer/Koi Loader (TA4561), was observed doing so in Fall 2025.
Details. ⤵️
Alongside this activity recently highlighted by Google (cloud.google.com/blog/topics/...), Proofpoint threat researchers have observed additional exploitation of WinRAR vulnerability CVE-2025-8088 by state‑aligned groups linked to China and the DPRK.
28.01.2026 21:34 — 👍 2 🔁 1 💬 1 📌 0The report includes a section on suspected RU-aligned actor UNK_AcademicFlare, which has been very active using compromised gov/mil emails to target gov, think tanks, academia & transport sectors in US/EU, often via weeks-long benign rapport building prior to delivering a device code phish.
18.12.2025 17:20 — 👍 0 🔁 0 💬 0 📌 0New espionage/e-crime crossover blog from the team on the continued rise of device code phishing by state-aligned and financially motivated groups.
18.12.2025 17:18 — 👍 7 🔁 3 💬 1 📌 0
A study in the evolution of SVR cyberespionage tradecraft
06.12.2025 19:07 — 👍 22 🔁 4 💬 0 📌 1
@volexity.com tracks a variety of threat actors abusing Device Code & OAuth authentication workflows to phish credentials, which continue to see success due to creative social engineering. Our latest blog post details Russian threat actor UTA0355’s campaigns impersonating European security events.
04.12.2025 18:36 — 👍 10 🔁 8 💬 0 📌 0
1/ Today we release a new report exposing previously undisclosed entities connected to the wider #Intellexa ecosystem as well as newly identified activity clusters in Iraq and indications of activity in Pakistan: www.recordedfuture.com/research/int...
04.12.2025 04:17 — 👍 26 🔁 18 💬 2 📌 4PlugX C2: doorforum[.]com
25.11.2025 18:57 — 👍 3 🔁 0 💬 0 📌 0I'm just glad I'm not the one being shut up this time
05.11.2025 17:39 — 👍 3 🔁 0 💬 1 📌 0
New Iran drop from me tracking an attribution nightmare - UNK_SmudgedSerpent! A little Charming, a little Muddy, and a lot C5. Targeting policy experts with benign conversation starters, health-themed infra, OnlyOffice spoofs, and RMMs. Check out the full story www.proofpoint.com/us/blog/thre...
05.11.2025 13:37 — 👍 19 🔁 12 💬 2 📌 0Proofpoint threat researchers have designed an open-source tool—named PDF Object Hashing—to track and detect the unique characteristics of PDFs used by threat actors... similar to a digital fingerprint.
We use this tool internally to help track multiple threat actors with high confidence.
📣 🔥 🛋️ SAVE THE DATE 🛋️ 🔥 📣
The next #PIVOTcon will be on 6-8 May 2026, in Malaga, ES!!!
You favorite ;) #ThreatResearch conference is coming back and we are planning to bring you the usual experience and content of utmost quality. Follow us + #StayTuned for more info
#CTI #ThreatIntel #PIVOTcon26
Good piece covering a big burst of TA416 activity targeting European governments last week!
04.10.2025 11:32 — 👍 4 🔁 2 💬 0 📌 0
First public report at Recorded Future by yours truly is out! RedNovember (formerly TAG-100, a.k.a. Storm-2077) is a Chinese state-sponsored threat group focused on intelligence collection, especially on flashpoint issues of strategic interest to China. www.recordedfuture.com/research/red...
24.09.2025 18:57 — 👍 22 🔁 14 💬 2 📌 0
Proofpoint threat researchers have published new research identifying a new cyber-espionage campaign by #TA415 (#APT41), a China-aligned threat actor, exploiting growing uncertainty in U.S.-China economic relations.
Blog: www.proofpoint.com/us/blog/thre....
Our reporting overlaps this recent WSJ article:
www.wsj.com/politics/nat...
See our full research here:
www.proofpoint.com/us/blog/thre...
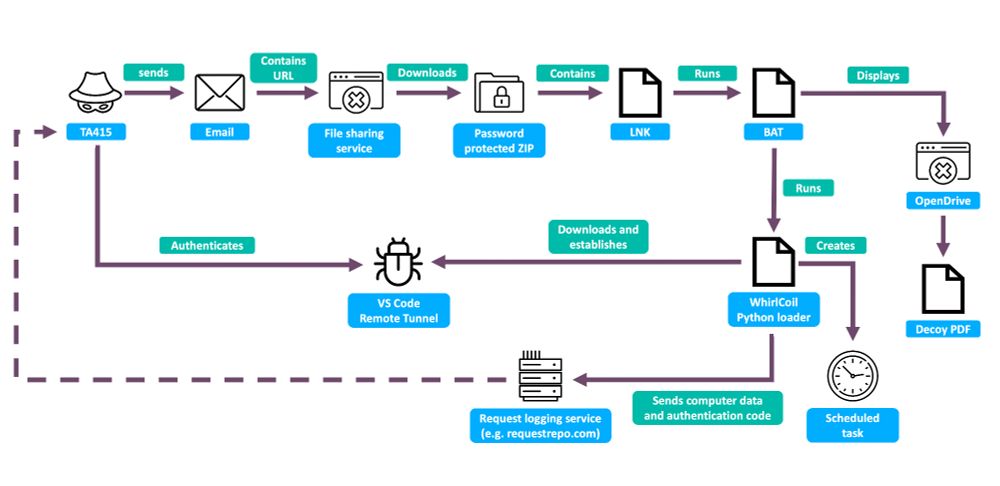
TA415 infection chain diagram
In these campaigns, TA415 delivered infection chains to set up VS Code Remote Tunnels 🚇 This is in line with recent TA415 phishing operations over the past year, which have relied on legit services (e,g, Google Sheets, Google Calendar, VS Code) for C2 to blend w/ trusted traffic
16.09.2025 12:49 — 👍 0 🔁 0 💬 1 📌 0🚨🇨🇳💰 New @threatinsight.proofpoint.com blog on TA415 (aka APT41) economy and trade-themed spearphishing against US govt, think tanks & academia.
The campaigns used U.S.-China economic lures and spoofed the Chair of the House Select Committee on CCP competition + the US-China Business Council.
It is time the Mustang Panda moniker went the way of Winnti Group ☠️
11.09.2025 10:24 — 👍 5 🔁 0 💬 1 📌 0
1/ We've just released a new report uncovering new infrastructure tied to multiple activity clusters linked to the Israeli spyware vendor #Candiru across several countries. Full report: www.recordedfuture.com/research/tra...
05.08.2025 14:18 — 👍 12 🔁 12 💬 1 📌 0
🚨🆕🐟🍟 New blog from me and the amazing @threatinsight.proofpoint.com team covering recent activity by multiple China-aligned threat actors targeting semiconductor companies in Taiwan over the past few months:
www.proofpoint.com/us/blog/thre...

New: A handful of Chinese-linked cyber espionage groups are stepping up targeting of Taiwanese semiconductor companies, per new analysis from @proofpoint.com. Campaigns include targeting of financial analysts focused on the sector as well: www.reuters.com/sustainabili...
16.07.2025 21:16 — 👍 16 🔁 9 💬 1 📌 0
New DISCARDED podcast drop! Join
@greg-l.bsky.social and me as we talk about our fave North Korean groups, DPRK as the neglected child, TA406 and the Russian connection, and finally, the dreaded but pervasive IT worker problem podcasts.apple.com/us/podcast/c...
open.spotify.com/episode/01d1...

Fun crossover blog about TA829 (RomCom) & TransferLoader with my ecrime pals @selenalarson.bsky.social it’s got it all:
🛰️ Popped routers for sending phish
📊 ACH on attribution
👾 custom protocols
👽 cool malware
🕵️ crime
🎯 espionage
❔many unanswered questions
www.proofpoint.com/us/blog/thre...
🚨 We’re hiring at Recorded Future’s Insikt Group
Two senior analyst roles are open right now. Both focus on tracking nation-state threats.
🧵

Today we’re publishing new findings on Predator spyware, still active despite global sanctions, now with a new client and ties to a Czech entity. Here’s what we found 🧵
www.recordedfuture.com/research/pre...

Dropping some joint research today with Threatray on TA397/Bitter 🔍
We dive into the confluence of signals that led us to our attribution of the threat actor 🎯
Shoutout to @konstantinklinger.bsky.social and Threatray for collaborating on this research.
www.proofpoint.com/us/blog/thre...

From phishes to hands-on-keyboard commands 🔥 new @proofpoint.bsky.social research from @nickattfield.bsky.social and @konstantinklinger.bsky.social on Indian state-sponsored actor TA397 (Bitter) with a great story on the steps to technical and political attribution www.proofpoint.com/us/blog/thre...
04.06.2025 11:08 — 👍 11 🔁 3 💬 0 📌 0