spear phishing email using Trend Micro updates as a lure

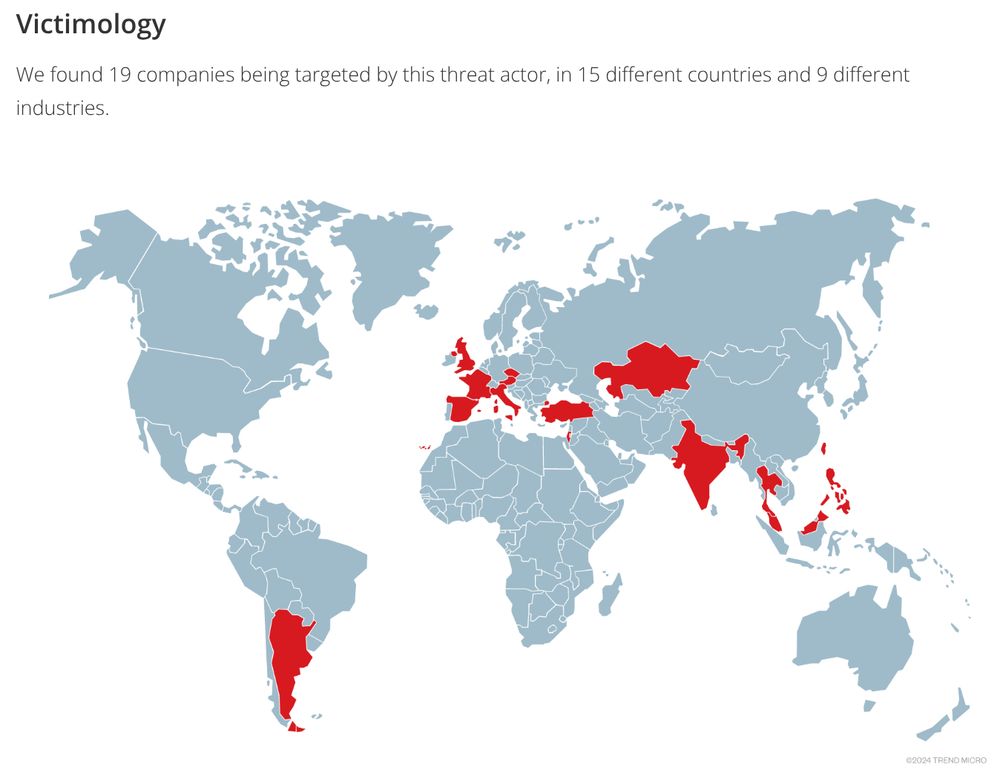
targeted industries

comparison between this intrusion set and Void Rabisu

Website mimicking Trend Micro graphical design
We investigated an #APT with links to Void Rabisu (Romcom) that used Trend Micro updates as a lure in a recent campaign involving vulnerability exploitation. There were at least 4 stages before the final payload, some of them being tailored to the targeted machine www.trendmicro.com/en_us/resear...
11.12.2025 15:03 — 👍 1 🔁 1 💬 0 📌 0

There are some links from Earth Estries to Salt Typhoon but we don't have enough evidence to say there is 100% overlap
There is a typo in the link (remove the extra "7" at the end, will ask for it to be fixed, thanks!).
Regarding your question, this is what we wrote about Salt Typhoon in our third Earth Estries blogpost www.trendmicro.com/en_us/resear...
22.10.2025 16:42 — 👍 1 🔁 0 💬 0 📌 0

Earth Estries and Earth Naga malware links

List of Earth Estries and Earth Naga targets, classified by targeted industry and location

Collaboration types and the related MITRE tactic stage where such collaboration occurs

Earth Estries and Earth Naga malware toolkits
We saw Earth Estries, an advanced #APT intrusion set, sharing its access to Earth Naga (Flax Typhoon). We introduce the term "Premier Pass" to describe this behavior, and propose a four-tier classification framework for collaboration types among advanced groups www.trendmicro.com/en_us/resear...
22.10.2025 09:18 — 👍 20 🔁 14 💬 2 📌 1
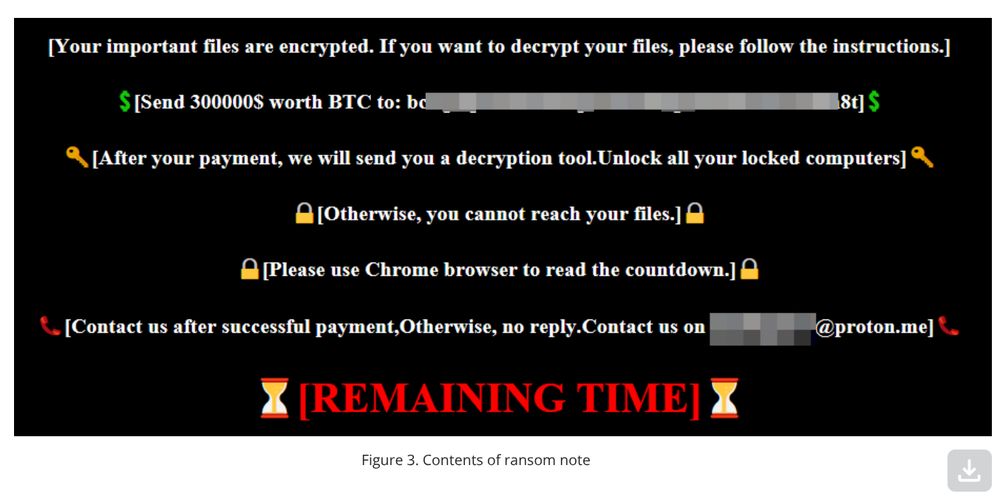
Orange Cyberdefense saw the same threat and named the ransomware "NailaoLocker" orangecyberdefense.com/global/blog/.... They share interesting thoughts on the motivations of the ransomware deployment, although they don't have the final answer. We also saw no financial gain for the threat actor
20.02.2025 09:39 — 👍 0 🔁 0 💬 0 📌 0
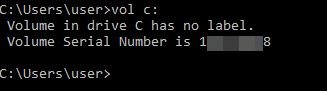
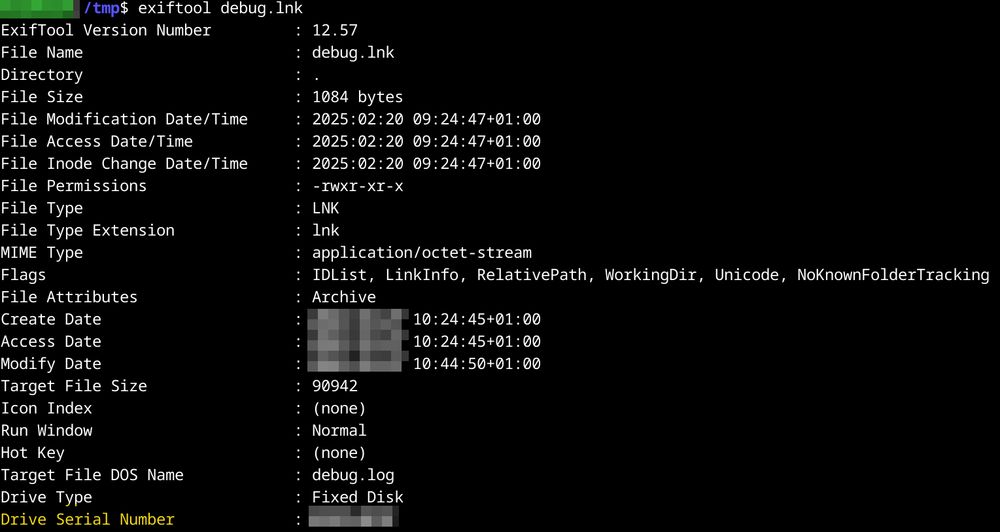
For incident responders, remember to retrieve the volume serial number where #Shadowpad was deployed, since it is used to encrypt the payload in the registry. Those serial numbers can also be found in LNK and Prefetch files in case you don't have live access to the host anymore
20.02.2025 09:39 — 👍 0 🔁 0 💬 1 📌 0

Earth Koshchei Coopts Red Team Tools in Complex RDP Attacks
Since Aug 2024 Earth Koshchei (APT29, Midnight Blizzard) used 193 RDP relays and 34 rogue backends against military, MFAs and others. The campaign peak was likely preceded by barely audible campaigns that ended with a bang in Oct 2024. Details and indicators here: www.trendmicro.com/en_us/resear...
17.12.2024 08:33 — 👍 8 🔁 7 💬 0 📌 0
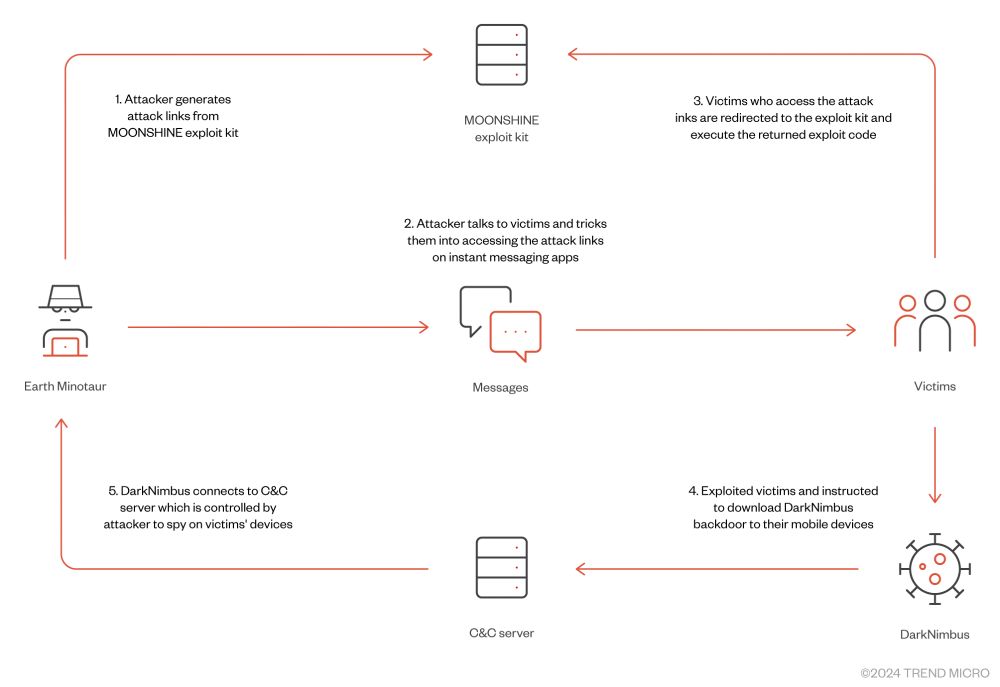
Attack chain showing attacker generating link on Moonshine, then sending it through targeted application to the victim, which after clicking the links gets compromised and delivered the DarkNimbus backdoor
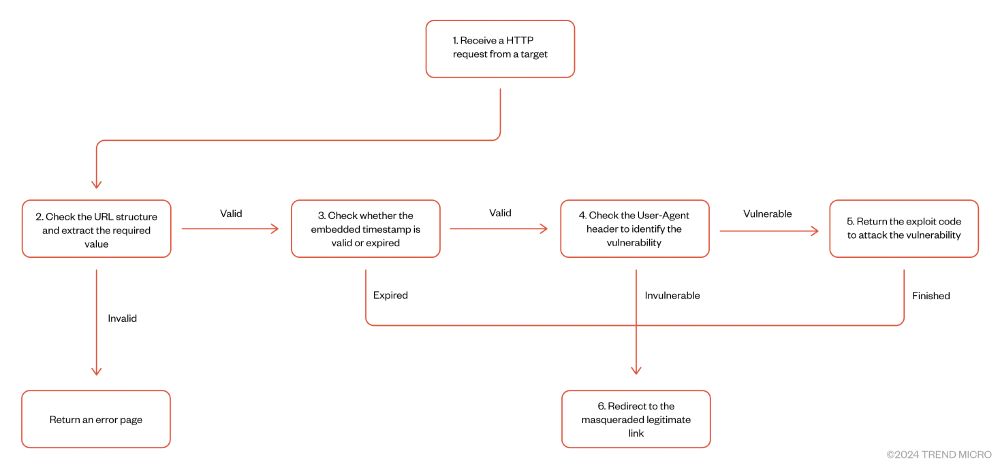
Validation flow that fingerprints the target by looking at user agent and delivering the proper exploit
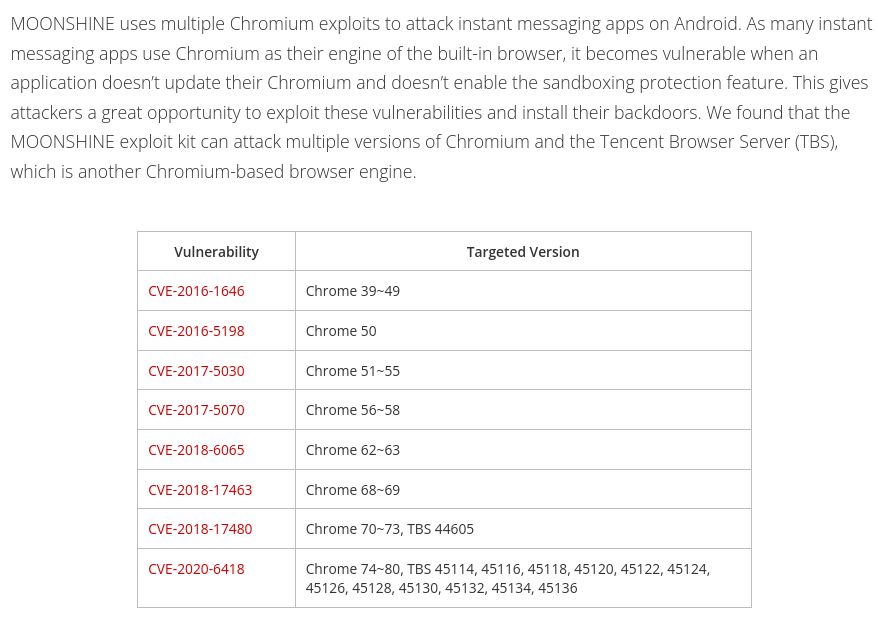
multiple Chrome vulnerabilities exploited in the third-party applications
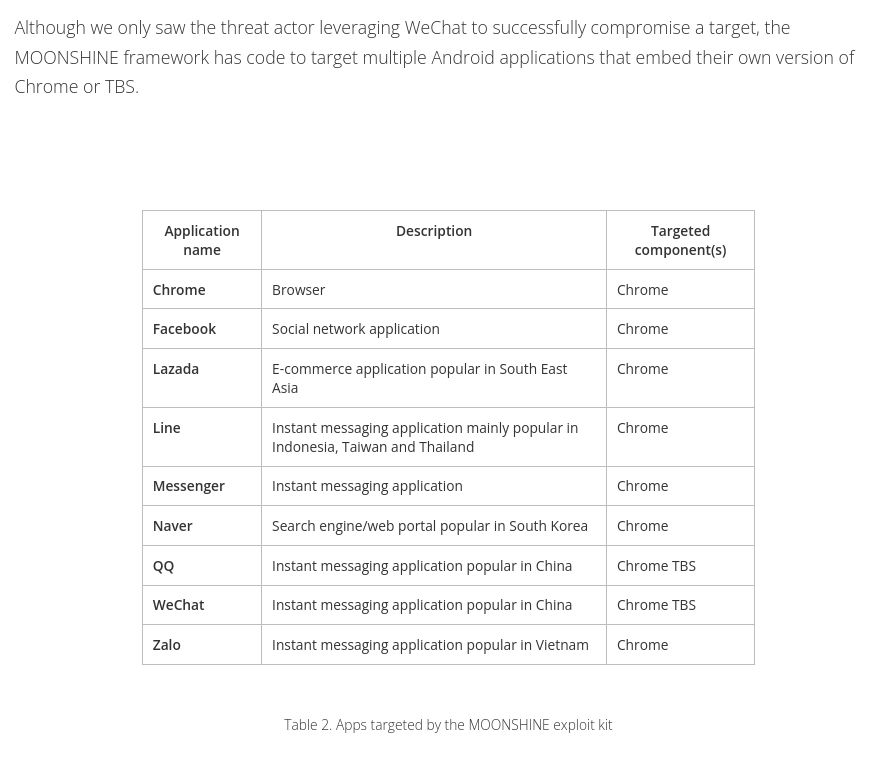
List of Android applications being targeted
Most are very popular in South East Asia
Our latest report presents Earth Minotaur, a threat actor targeting Tibetans and Uyghurs using Moonshine, an exploitation framework for Android apps described in 2019 by
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
05.12.2024 08:48 — 👍 12 🔁 7 💬 0 📌 2
Author of open-source projects oletools, olefile, ViperMonkey, ExeFilter, Balbuzard. Posting about #DFIR, #malware analysis, maldocs, file formats and #Python.
https://linktr.ee/decalage
Cyber threat intelligence research and analysis from geopolitical, economic, social, cultural and linguistic perspectives.
https://www.nattothoughts.com/
Blue team - DFIR/SOC - Author of ADTimeline, DFIR-O365RC, DFIR4vSphere
Reverse engineering, malware
Journaliste Le Monde - cyber, influence - ✉️ freynaud at lemonde
🇰🇵 #BSidesPyongyang2025 : Nov 18 2025 (Missile Industry Day) @ Lazarus HQ Pyongyang
https://bsidespyongyang.com/
Security and insecurity things.
Mostly here for infosec, swe, devops, and other jobs babysitting computers.
Given up on fixing typos.
📍The elevator is at the rare of the platform.
reporter covering cyber (both crime and state-sponsored) for Der Spiegel and ZDF, short overview at https://linktr.ee/hakantanriverdi, Signal: hakan.25
The Hague Threat Intelligence Exchange (Hague TIX) conference by @thehagueprogram - back on 30 June 2026 for #HagueTIX2026!
--> www.hague-tix.nl
Journaliste, aux manettes de la newsletter cybercrime Pwned | gabrielthierry@protonmail.com https://linktr.ee/gabrielthierry
Native Hawaiian Hacker | Prev Co-captain of @Shellphish | PhD Student in Comp Sci @ASU l Decompiler Research | https://mahaloz.re
Ported vx-underground from twitter.
vx-staff: if you want me to take it down, pm me
i'm not using to impersonate you!
Research and development at the intersection of cyberspace, global security, and human rights. Based at Munk School of Global Affairs & Public Policy, University of Toronto.
Programmer, #malware analyst. Author of #PEbear, #PEsieve, #TinyTracer. Private account. All opinions expressed here are mine only (not of my employer etc) ; https://hasherezade.net
Security Researcher @Meta. Writer. Would-be musician. Maintainer of Manalyze and Gepetto. Trolling on a purely personal capacity.
Offensive security conference in the heart of Paris. 10-11th October 2025
https://www.hexacon.fr/
World Watch CTI team from Orange Cyberdefense
https://www.orangecyberdefense.com/global/offering/managed-services/threat-and-risk-management/world-watch