How about America first!
23.12.2025 12:37 — 👍 1 🔁 0 💬 0 📌 0Michaelette
@michaelette.bsky.social
Love and respect to all the resisters who have stood up and changed the world ❤️
@michaelette.bsky.social
Love and respect to all the resisters who have stood up and changed the world ❤️
How about America first!
23.12.2025 12:37 — 👍 1 🔁 0 💬 0 📌 0A damn daycare. This is sick. What are we doing?
05.11.2025 18:30 — 👍 11292 🔁 5115 💬 1131 📌 488Don’t look away
29.08.2025 02:39 — 👍 13640 🔁 7655 💬 2191 📌 1223If we got rid of the electoral college wouldn't that help?
07.08.2025 13:16 — 👍 4 🔁 0 💬 0 📌 0We need to get rid of the electoral college.
31.07.2025 19:33 — 👍 5 🔁 0 💬 0 📌 0 26.07.2025 19:11 — 👍 947 🔁 381 💬 23 📌 19
26.07.2025 19:11 — 👍 947 🔁 381 💬 23 📌 19
Looks like he got into trump's makeup drawer
08.07.2025 13:25 — 👍 3 🔁 0 💬 0 📌 0I'm sure trump will blanket pardon everyone in his cabinet. I hope there will be a way around that.
02.07.2025 13:55 — 👍 0 🔁 0 💬 0 📌 0@markhamillofficial.bsky.social Just saw your movie Life of Chuck!! One of the best movies I've seen in a long time!! You are such a great actor!! Absolutely LOVED it!!
01.07.2025 22:35 — 👍 3 🔁 0 💬 0 📌 0NYC Comptroller Brad Lander just got arrested while visiting immigration court.
What the hell is going on?
Avoid the USA
vm.tiktok.com/ZMSf2xNaA/
When they think no one is looking.
*Cops damaging their own cars?
 28.05.2025 22:00 — 👍 971 🔁 137 💬 33 📌 8
28.05.2025 22:00 — 👍 971 🔁 137 💬 33 📌 8
Done
20.05.2025 19:50 — 👍 2 🔁 0 💬 0 📌 0High school students at the Capitol: “Why is [Trump] so orange?”
GOP Rep. Brian Jack: “Uh, that’s, you know what, it’s, it’s, it’s your perspective...”

That’s much more like it
04.05.2025 13:21 — 👍 137 🔁 40 💬 5 📌 3Excited today to be a registered Florida Democrat, and to launch Florida 2026.
To learn more and to support, head to davidjolly.com.
Florida's next chapter starts today.
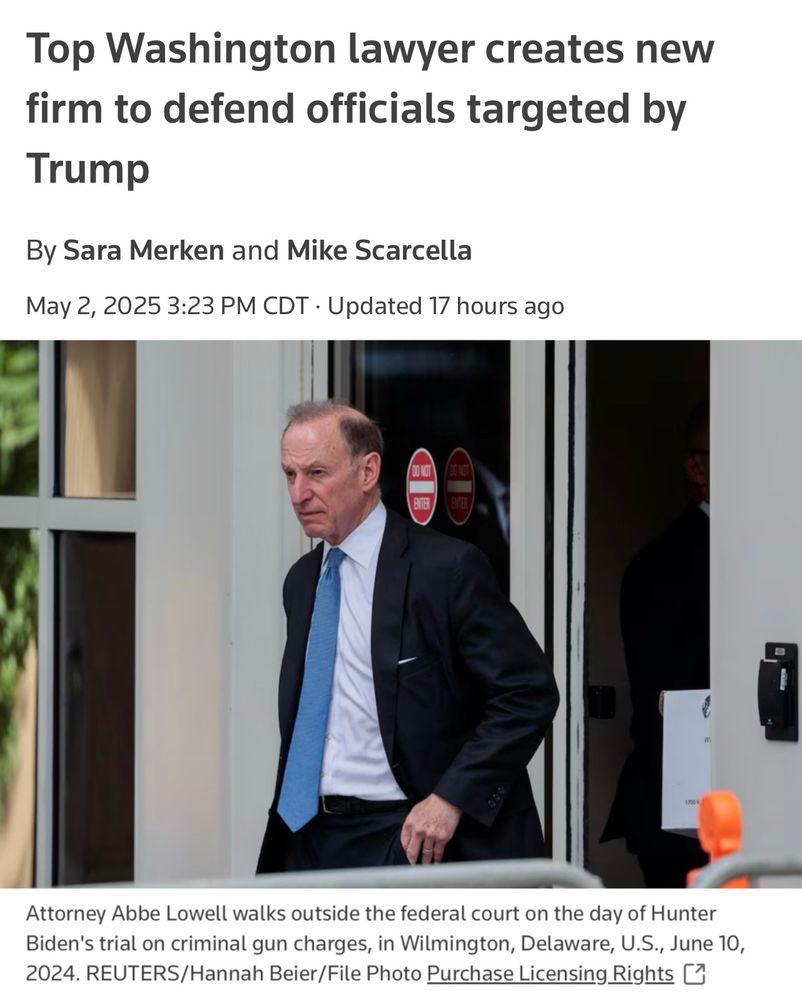
Not all heroes wear capes.
03.05.2025 13:48 — 👍 17202 🔁 4236 💬 302 📌 176Pope Francis’s "Urbi et Orbi" Easter speech:
“How much contempt is stirred up at times towards the vulnerable, the marginalized and migrants...I appeal to all those in positions of political responsibility in our world not to yield to the logic of fear which only leads to isolation from others.”

#ThisIsAmerica we’re watching our decline in real time
17.04.2025 11:46 — 👍 331 🔁 104 💬 6 📌 5
A whistleblower's disclosure details how DOGE may have taken sensitive labor data

The IT team met to discuss insider threats - namely, the DOGE engineers, whose activities it had little insight into or control over. "We had no idea what they did," he explained. Those conversations are reflected in his official disclosure. They eventually launched a formal breach investigation, according to the disclosure, and prepared a request for assistance from the Cybersecurity and Infrastructure Security Agency (CISA). However, those efforts were disrupted without an explanation, Berulis said. That was deeply troubling to Berulis, who felt he needed help to try to get to the bottom of what happened and determine what new vulnerabilities might be exploited as a result. In the days after Berulis and his colleagues prepared a request for CISAs help investigating the breach, Berulis found a printed letter in an envelope taped to his door, which included threatening language, sensitive personal information and overhead pictures of him walking his dog, according to the cover letter attached to his official disclosure. It's unclear who sent it, but the letter made specific reference to his decision to report the breach. Law enforcement is investigating the letter.
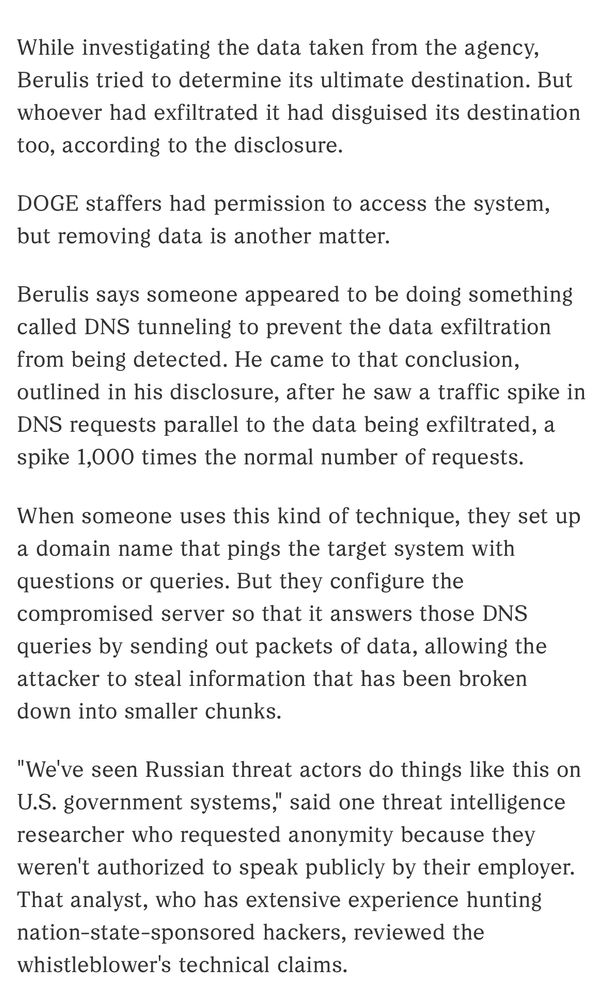
While investigating the data taken from the agency, Berulis tried to determine its ultimate destination. But whoever had exfiltrated it had disguised its destination too, according to the disclosure. DOGE staffers had permission to access the system, but removing data is another matter. Berulis says someone appeared to be doing something called DNS tunneling to prevent the data exfiltration from being detected. He came to that conclusion, outlined in his disclosure, after he saw a traffic spike in DNS requests parallel to the data being exfiltrated, a spike 1,000 times the normal number of requests. When someone uses this kind of technique, they set up a domain name that pings the target system with questions or queries. But they configure the compromised server so that it answers those DNS queries by sending out packets of data, allowing the attacker to steal information that has been broken down into smaller chunks. "We've seen Russian threat actors do things like this on U.S. government systems," said one threat intelligence researcher who requested anonymity because they weren't authorized to speak publicly by their employer. That analyst, who has extensive experience hunting nation-state-sponsored hackers, reviewed the whistleblower's technical claims.
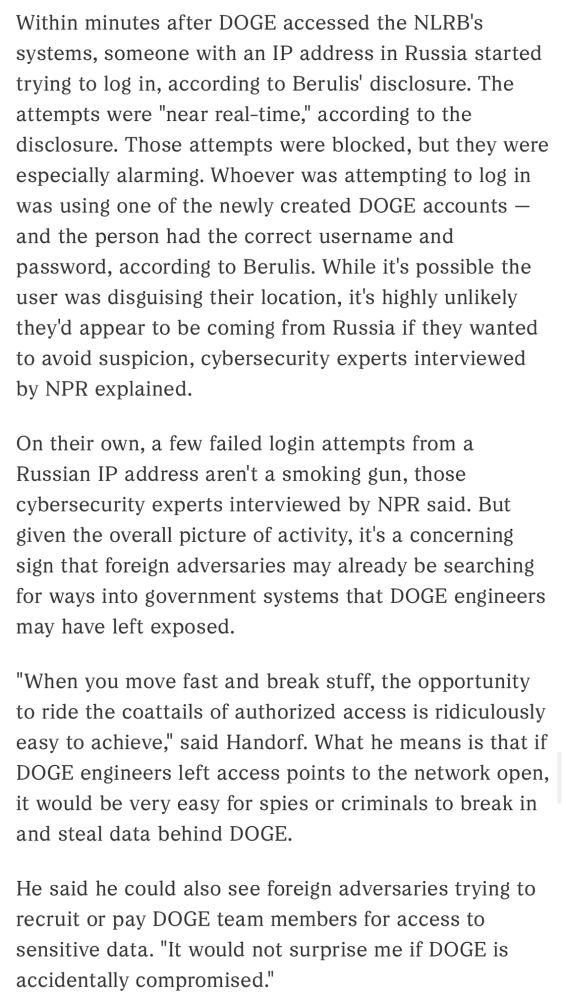
Within minutes after DOGE accessed the NLRB's systems, someone with an IP address in Russia started trying to log in, according to Berulis' disclosure. The attempts were "near real-time," according to the disclosure. Those attempts were blocked, but they were especially alarming. Whoever was attempting to log in was using one of the newly created DOGE accounts - and the person had the correct username and password, according to Berulis. While it's possible the user was disguising their location, it's highly unlikely they'd appear to be coming from Russia if they wanted to avoid suspicion, cybersecurity experts interviewed by NPR explained. On their own, a few failed login attempts from a Russian IP address aren't a smoking gun, those cybersecurity experts interviewed by NPR said. But given the overall picture of activity, it's a concerning sign that foreign adversaries may already be searching for ways into government systems that DOGE engineers may have left exposed. "When you move fast and break stuff, the opportunity to ride the coattails of authorized access is ridiculously easy to achieve," said Handorf. What he means is that if DOGE engineers left access points to the network open, it would be very easy for spies or criminals to break in and steal data behind DOGE. He said he could also see foreign adversaries trying to recruit or pay DOGE team members for access to sensitive data. "It would not surprise me if DOGE is accidentally compromised."
Musk’s DOGE involved in what appears to be a foreign espionage operation and data theft. They also have death threatened US federal whistleblowers and disabled security systems, deliberately allowing Russian IPs to access sensitive US federal government systems.
www.npr.org/2025/04/15/n...

Ukr military badge
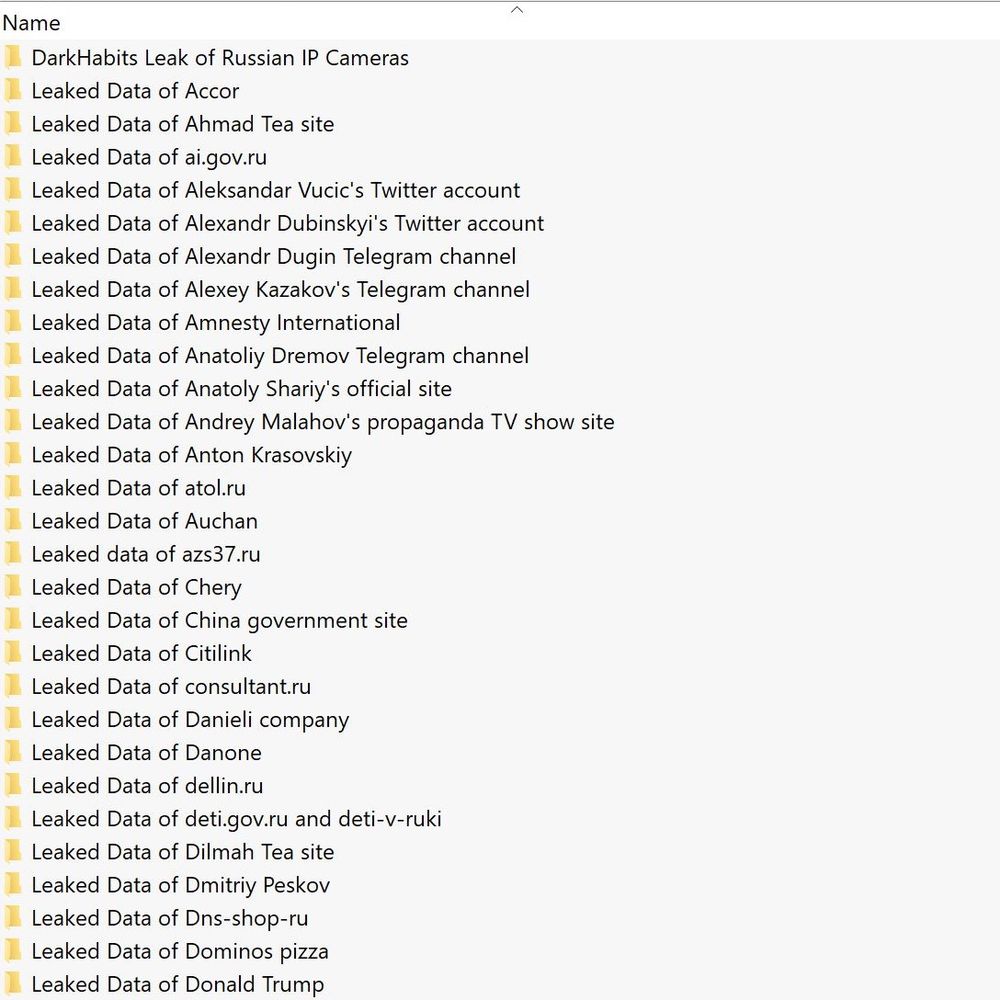
Files
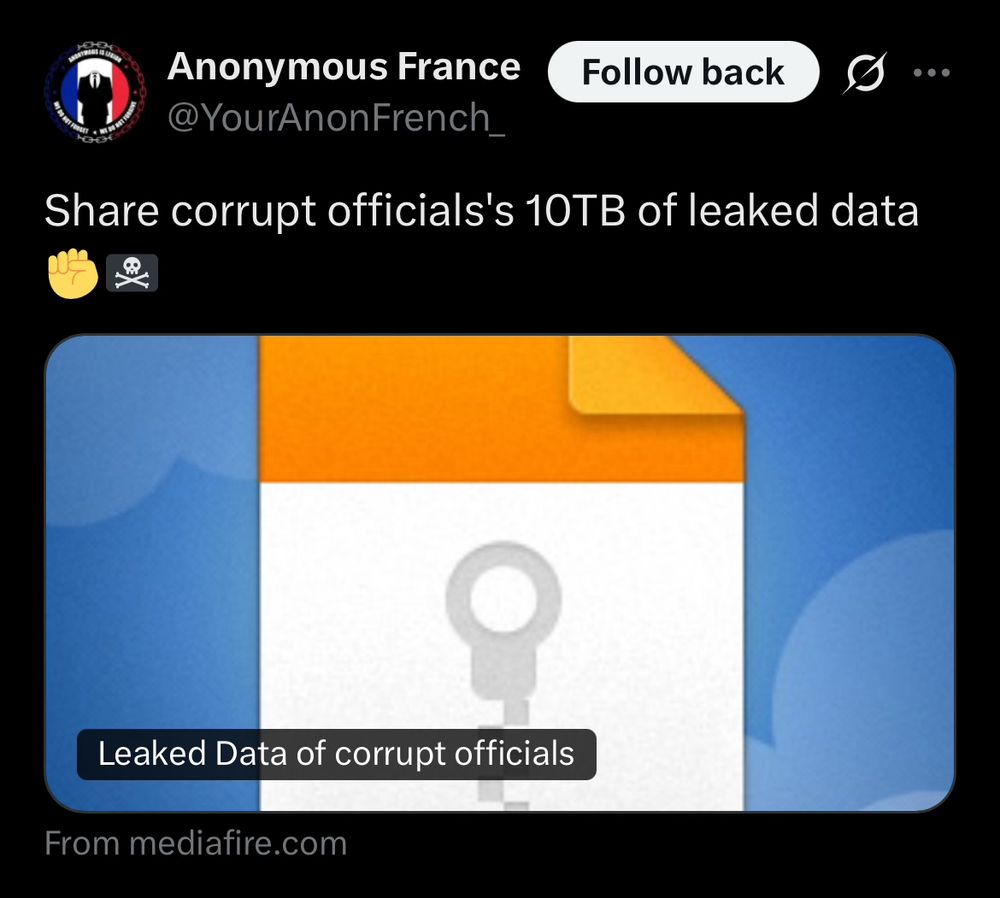
Leak
In defense of Ukraine Anonymous has released 10TB of leaked data on all businesses operating in Russia, all Kremlin assets in the West, pro-Russian officials, Donald Trump, and more. 🇺🇦 #OpRussia
15.04.2025 23:56 — 👍 6752 🔁 2355 💬 315 📌 188This breaks me — because I can see my wife and daughter living through this.
I don’t trust DHS, and you shouldn’t either because it could happen to anyone. They’re on a mission, and it feels lawless as hell.
I wish he was
05.04.2025 22:48 — 👍 2 🔁 0 💬 0 📌 0 16.03.2025 17:38 — 👍 17460 🔁 4279 💬 327 📌 138
16.03.2025 17:38 — 👍 17460 🔁 4279 💬 327 📌 138

Pretending you’re at Sotheby’s isn’t going to stop fascism.
05.03.2025 23:23 — 👍 18670 🔁 3050 💬 1363 📌 383