I've heard that my fellow Red Teamers like to use SOCKS proxies for stealth operations, so here's one that (ab)uses Azure Blob Storage 🚇
30.04.2025 16:10 — 👍 0 🔁 0 💬 0 📌 0

Proxybloby, the read teamer's mascot that will byte your SOCKS if left alone in your internal network
Look at those cute little blobs in your internal network. They look harmless, but how about the one carrying SOCKS?
It's ProxyBlob, a reverse proxy over Azure.
Check out Alexandre Nesic's article on how it came to exist after an assumed breach mission ⤵️
👉 blog.quarkslab.com/proxyblobing...
29.04.2025 17:32 — 👍 1 🔁 1 💬 0 📌 1

For us, EDR bypass is not just a buzzword.
MacroPack, ShellcodePack, and DarwinOps all come with bypass presets for major EDRs and Antivirus
Those presets are regularly updated and tested!
If you want to see a demo or an equivalent screenshot for the major EDRs contact us !
#redteam
03.04.2025 15:47 — 👍 3 🔁 2 💬 0 📌 0

Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
08.04.2025 23:00 — 👍 27 🔁 20 💬 1 📌 2
A CTF challenge in PHP, what could possibly not be a RCE?
Next week at the Hack The Box 0x4d meetup in Lille, France @rayanle.cat will talk about PwnShop, the challenge he prepared for the PwnMe CTF 2025 and how he accidentally discovered a RCE 0day while doing so.
Join him next Monday at Campus Cyber Hauts-the-France:
www.meetup.com/hack-the-box...
25.03.2025 14:01 — 👍 7 🔁 2 💬 0 📌 0

Loading a shellcode from a file/URL with ShellcodePack
Shellcode in EXE files can sometimes be detected during static analysis, requiring various kinds of obfuscation to bypass EDRs.
This…
Balliskit Evasion Tip 🤖
To help with static analysis detection by EDR,
ShellcodePack implements a method to load a shellcode from a separate file or from an URL
This tutorial explains how to use that option!
#redteam
blog.balliskit.com/loading-a-sh...
20.03.2025 17:18 — 👍 3 🔁 2 💬 0 📌 0
YouTube video by Adam Chester
Mythic MCP - Claude Sonnet driving Mythic (Apollo)
On PTO and bored, so playing around with MCP by exposing Mythic APIs to Claude and seeing what the result. Attempting to have it emulate threat actors while operating Apollo in a lab... would make a good sparring partner :D www.youtube.com/watch?v=ZooT...
20.03.2025 22:24 — 👍 20 🔁 6 💬 1 📌 0

Evilginx Pro is finally here!
After over two years of development, Evilginx Pro reverse proxy phishing framework for red teams is finally live!
🚨 Evilginx Pro is finally here! 🚨🎣🐟
This is it! After over two years of development, countless delays, and hundreds of manual company verifications, Evilginx Pro is finally live!
Thank you all for your invaluable support 💗
breakdev.org/evilginx-pro...
12.03.2025 15:29 — 👍 11 🔁 6 💬 0 📌 0
GitHub - decoder-it/KrbRelayEx-RPC
Contribute to decoder-it/KrbRelayEx-RPC development by creating an account on GitHub.
KrbRelayEx-RPC tool is out! 🎉
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
14.03.2025 10:18 — 👍 9 🔁 10 💬 0 📌 0
If you thought phishing was now ineffective, you may have missed something 👀
My latest post highlights the advanced tactics used to bypass security controls and deceive even the most savvy users. Check it out ⤵️
11.03.2025 16:21 — 👍 1 🔁 1 💬 0 📌 0
Phishing in the Cloud with Diamonds
From classic HTML pages to advanced MFA bypasses, dive in with @atsika.bsky.social in an exploration of phishing techniques 🎣.
Learn some infrastructure tricks and delivery methods to bypass common detection.
👉 blog.quarkslab.com/technical-di...
(promise this one is legit 👀)
11.03.2025 16:06 — 👍 5 🔁 4 💬 0 📌 2

#PEbear (github.com/hasherezade/...) is now available via WinGet (learn.microsoft.com/en-us/window...)! You can install it easier than ever - just type: `winget install pe-bear` from Powershell.
09.03.2025 16:07 — 👍 12 🔁 8 💬 0 📌 0
YouTube video by hasherezade
[DEMO] Searching for AceLdr in memory, with PE-sieve/HollowsHunter thread scan
[DEMO] Searching for #AceLdr in memory, with #PEsieve/#HollowsHunter threads scan: www.youtube.com/watch?v=RQf2... ; read more: github.com/hasherezade/...
09.03.2025 16:08 — 👍 4 🔁 4 💬 0 📌 0

A Plan to Pwn: Reviving a 17 year old bug or winning a race against Project Management? We've got both.
Mathieu Farrell shows you how in the "Pwn Everything, Bounce Everywhere, all at once" blog post series.
blog.quarkslab.com/pwn-everythi...
25.02.2025 19:39 — 👍 3 🔁 2 💬 0 📌 0

An AI generated picture depicting exploitation kungfu against SOplanning. We guess they did not plan for that.
ICYMI: 5 vulnerabilities in SOPlanning, an open source project management application used by major consulting services providers.
In part 2 of "Pwn Everything, Bounce Everywhere, all at once" Mathieu Farrell tells you how to chain them for unautheticated RCE
blog.quarkslab.com/pwn-everythi...
26.02.2025 16:04 — 👍 1 🔁 1 💬 0 📌 0
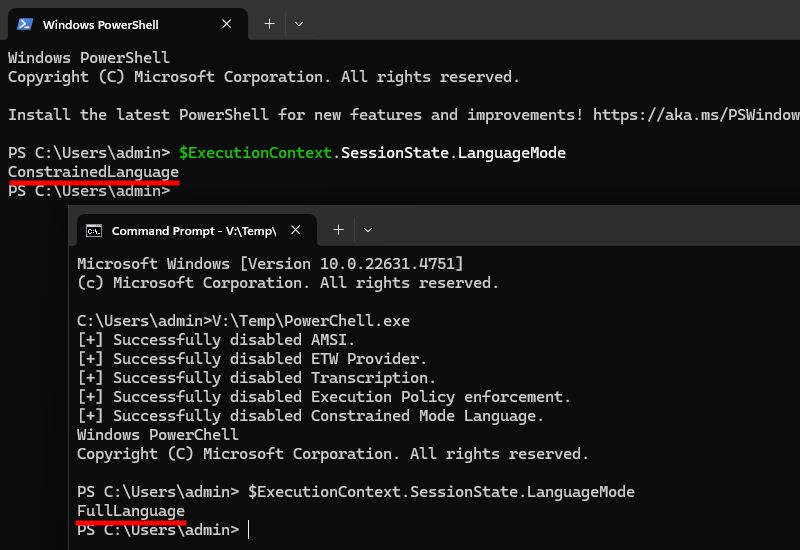
Screenshot showing the execution of the proof-of-concept named PowerChell in comparison to a typical PowerShell prompt. In particular, it shows that PowerChell is able to bypass the Constrained Language Mode (CLM).
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
19.02.2025 09:13 — 👍 43 🔁 19 💬 2 📌 2
Riding around in the breeze. Security Thinker. Hacker. USAF Veteran. https://aff-wg.org
Windows Internals Author, Developer, Reverse Engineer, Security Researcher, Speaker, Trainer, and most recently Nation State Hacker.
Core OS Platform Developer at Apple, Hyper-V Vendor at Microsoft, Chief Architect at CrowdStrike and now Director at CSE.
RedTeam | Pentest
Author of PayloadsAllTheThings & SSRFmap
http://github.com/swisskyrepo
wannabe hacker... he/him
🌱 grow your hacking skills https://hextree.io
The world’s premier hacker conference. Serving the global hacker community since 1993.
Defcon.org
Forum.defcon.org
Defcon.social
The world's premier Technical Cybersecurity Conference Series
hacker, maldev, pokemon irl
Red Teamer and maker of things
🪦Previously : https://x.com/dsec_net
意志 / Antiquarian @ IBM Adversary Services / Ex-TORE ⚔️🦅 / I rewrite pointers and read memory / AI Psychoanalyst / Teaching
at labs.calypso.pub
content dev and researcher @offsectraining | r&d @OutflankNL | 🥁
www.uf0.org
hacker, poster, weird machine mechanic
https://chompie.rip
CTO @TrustedSec.com | Former Optiv/SecureWorks/Accuvant Labs/Redspin | Race cars
Running on vibes. Cyber vibes.
Red Brain, Blue Fingers
Malware Analysis, Reverse Engineering, Threat Hunting, Detection Engineering, DFIR, Security Research, Programming, Curiosities, Software Archaeology, Puzzles, Bad dad jokes
https://www.hexacorn.com/blog/
hexacorn@infosec.exchange
A circus artist with a visual studio license









![[DEMO] Searching for AceLdr in memory, with PE-sieve/HollowsHunter thread scan](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:bt437wewqcvsurogzlpcxque/bafkreibbqpujeyz2exwkdqbmzkzkr4p5cxvrbw5vwj3nn6h7k5fzdtjvvq@jpeg)



