MCP: An Introduction to Agentic Op Support
LLMs and Agents offer a powerful combination for driving automation. In our new blog, Senior Security Consultant Brandon McGrath outlines how he harnesses the power of angentic AI to autonomously map a network. Read it now! trustedsec.com/blog/mcp-an-...
28.03.2025 13:57 — 👍 4 🔁 4 💬 0 📌 0

Exploring NTDS.dit – Part 1: Cracking the Surface with DIT Explorer
In our new #blog, Senior Research Analyst @codewhisperer84.bsky.social unveils his new tool DIT Explorer which he created after researching NTDS.dit files on Active Directory. Read part one of this series now to find out what this tool can do! trustedsec.com/blog/explori...
20.02.2025 18:54 — 👍 16 🔁 11 💬 0 📌 1

From RAGs to Riches: Using LLMs and RAGs to Enhance Your Ops
In our new blog, Senior Security Consultant Brandon McGrath explores how to apply Retrieval-Augmented Generation (RAG) to research capabilities. Find out how he leverages AI to enhance his ops. Read it now! trustedsec.com/blog/from-ra...
11.02.2025 16:02 — 👍 9 🔁 6 💬 0 📌 0
Fair amount of people with ball joint issues
26.01.2025 12:47 — 👍 0 🔁 0 💬 0 📌 0
Having brake issues is weird since they have regen a lot of people go 100k on stock brakes
26.01.2025 12:44 — 👍 0 🔁 0 💬 2 📌 0

Operating Inside the Interpreted: Offensive Python
Who says Python Malware is out of style? In our new blog, Security Consultant Kevin Clark revisits an old technique he believes is a prime candidate to host malware payloads—Python for Windows. Read it now! trustedsec.com/blog/operati...
23.01.2025 16:42 — 👍 13 🔁 4 💬 0 📌 0


Cool Silicon Valley gifts
25.12.2024 22:57 — 👍 10 🔁 0 💬 0 📌 0


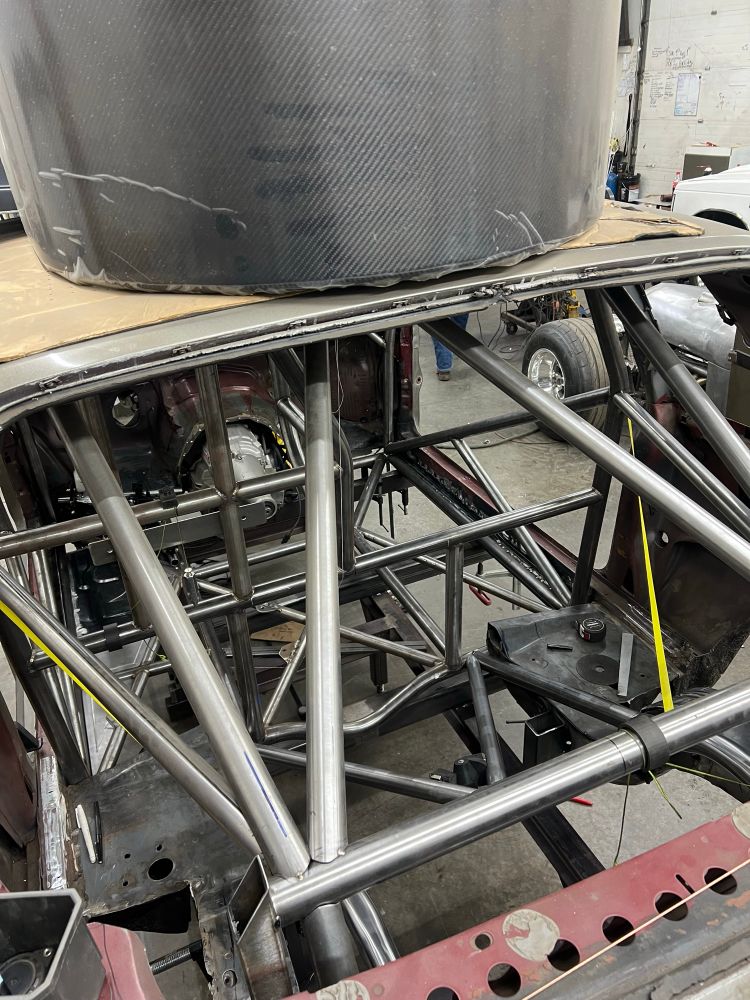
Friday car stuff this one was 3500-4000hp
20.12.2024 21:50 — 👍 6 🔁 0 💬 0 📌 0

Top 10 Blogs of 2024
It's that time of year again! We are excited to reveal our top 10 most read blogs of 2024 🥳
trustedsec.com/blog/top-10-...
17.12.2024 17:15 — 👍 7 🔁 4 💬 0 📌 0

We are hiring! TrustedSec is looking to grow our marketing team with a new Marketing Director and Marketing Coordinator. Find out more about the position requirements and apply via the link below!
recruiting.paylocity.com/recruiting/j...
#marketingjobs #infosecjobs
17.12.2024 18:34 — 👍 4 🔁 5 💬 0 📌 0

Stay ready this holiday season
13.12.2024 12:48 — 👍 46 🔁 6 💬 5 📌 1
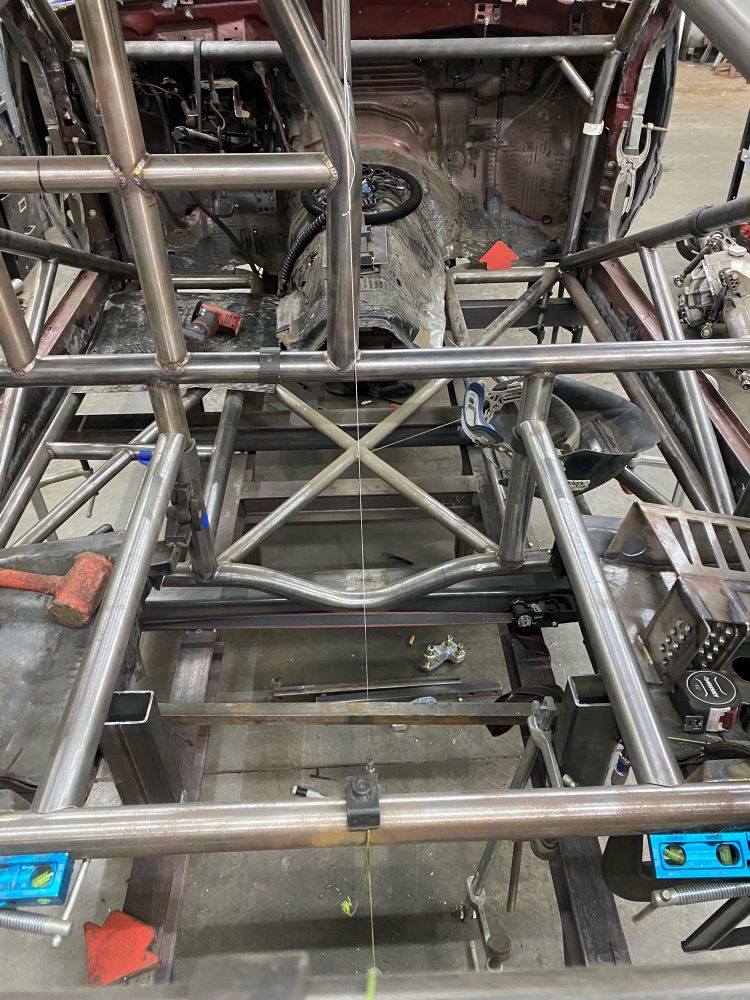
It’s an 86 Mustang for drag racing stuff but still drives on street
12.12.2024 16:56 — 👍 0 🔁 0 💬 1 📌 0
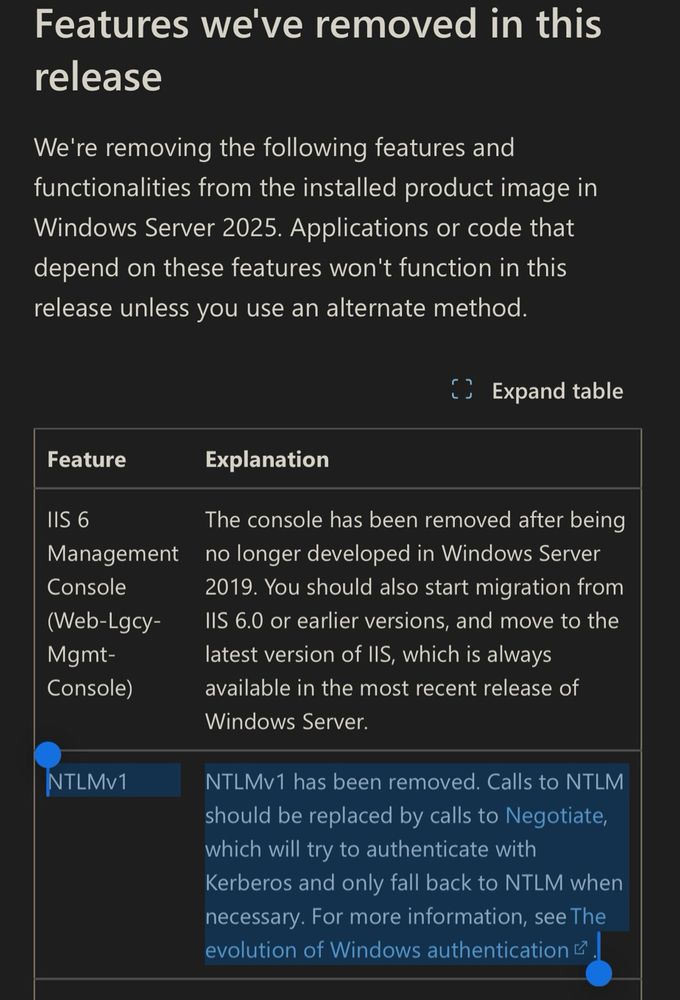
NTLM v1 is removed from the latest version of Windows
Oh by the way
06.12.2024 01:08 — 👍 102 🔁 35 💬 9 📌 6