For personal use I added a "geolocus" tool to a Deno-based MCP server (that has alot of random tools/functions in it).
It's been useful enough that I started extracting it to a standalone geolocus MCP server I shld be able to release in a couple days.
The @onyphe.io folks are super rad.
03.06.2025 02:22 — 👍 1 🔁 1 💬 0 📌 0
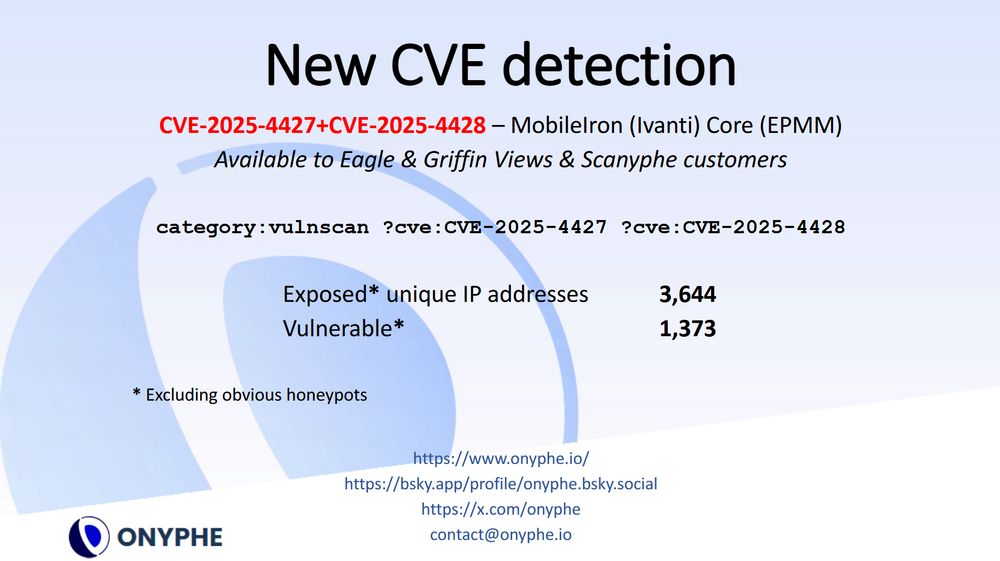
📣 We have added a new #vulnerability detection to our #ASM #AttackSurfaceManagement solution for #Ivanti product:
CVE-2025-4427+CVE-2025-4428 unauth RCE
search.onyphe.io/search?q=cat...
Thanks to watchTowr for detection method.
16.05.2025 10:08 — 👍 0 🔁 2 💬 0 📌 0
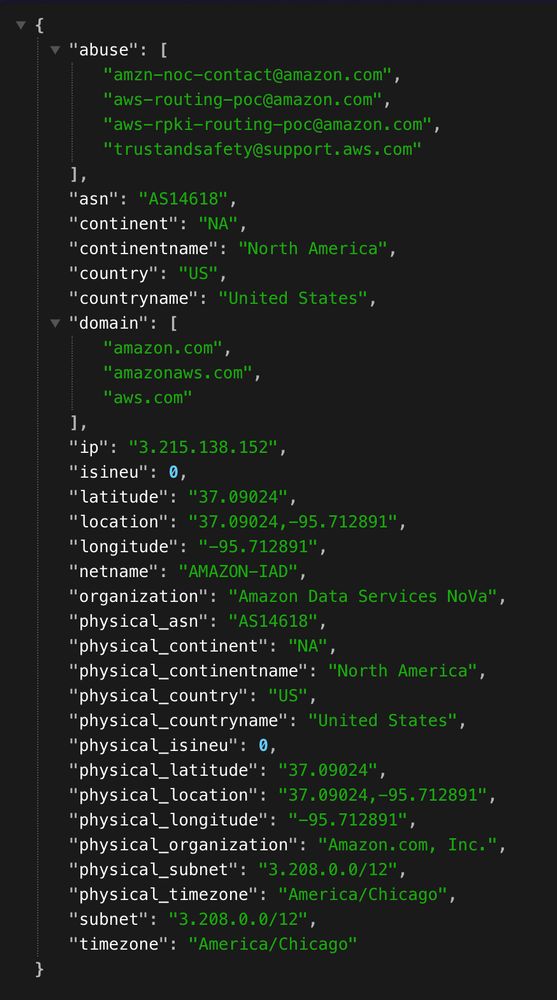
The image shows a block of structured JSON data displayed on a dark background.
The JSON object has the following top-level structure:
• abuse:
A list of four email addresses related to reporting abuse at Amazon and AWS:
• amzn-noc-contact@amazon.com
• aws-routing-poc@amazon.com
• aws-rpki-routing-poc@amazon.com
• trustandsafety@support.aws.com
• asn: "AS14618"
(This is Amazon’s autonomous system number.)
• continent: "NA" (North America)
• continentname: "North America"
• country: "US" (United States)
• countryname: "United States"
• domain:
A list of three domains:
• amazon.com
• amazonaws.com
• aws.com
• ip: "3.215.138.152"
(The specific IP address being described.)
• isineu: 0
(Indicates whether the IP is in the European Union — 0 means no.)
• latitude: "37.09024"
• longitude: "-95.712891"
• location: "37.09024, -95.712891"
• netname: "AMAZON-IAD"
(The name of the network.)
• organization: "Amazon Data Services NoVa"
• physical_asn: "AS14618"
• physical_continent: "NA"
• physical_continentname: "North America"
• physical_country: "US"
• physical_countryname: "United States"
• physical_isineu: 0
• physical_latitude: "37.09024"
• physical_longitude: "-95.712891"
• physical_location: "37.09024, -95.712891"
• physical_organization: "Amazon.com, Inc."
• physical_subnet: "3.208.0.0/12"
• physical_timezone: "America/Chicago"
• subnet: "3.208.0.0/12"
• timezone: "America/Chicago"
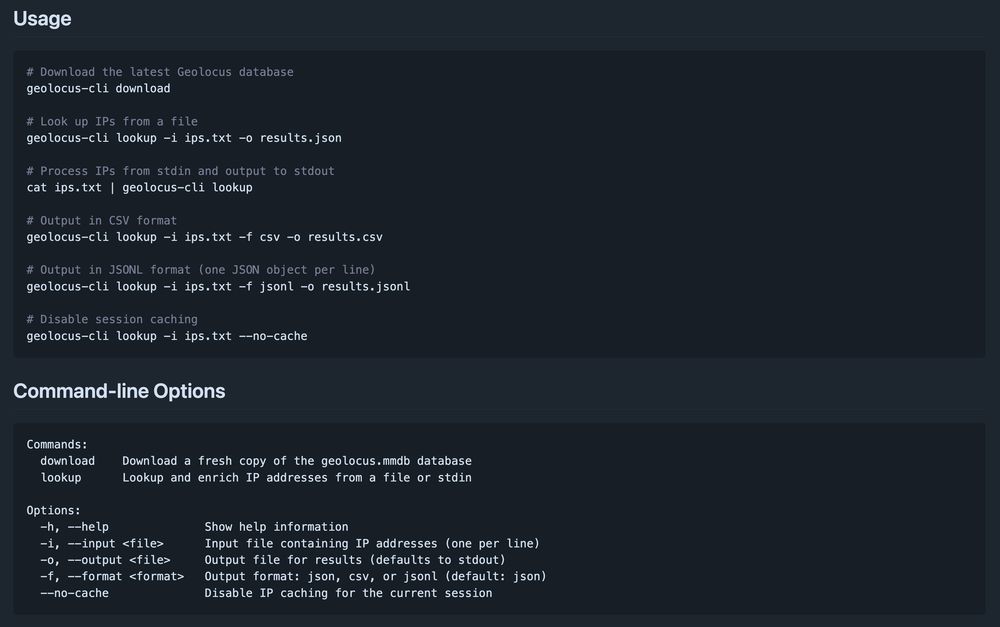
Usage
# Download the latest Geolocus database
geolocus-cli download
# Look up IPs from a file
geolocus-cli lookup -i ips.txt -o results.json
# Process IPs from stdin and output to stdout
cat ips.txt | geolocus-cli lookup
# Output in CSV format
geolocus-cli lookup -i ips.txt -f csv -o results.csv
# Output in JSONL format (one JSON object per line)
geolocus-cli lookup -i ips.txt -f jsonl -o results.jsonl
# Disable session caching
geolocus-cli lookup -i ips.txt --no-cache
Command-line Options
Commands:
download Download a fresh copy of the geolocus.mmdb database
lookup Lookup and enrich IP addresses from a file or stdin
Options:
-h, --help Show help information
-i, --input <file> Input file containing IP addresses (one per line)
-o, --output <file> Output file for results (defaults to stdout)
-f, --format <format> Output format: json, csv, or jsonl (default: json)
--no-cache Disable IP caching for the current session
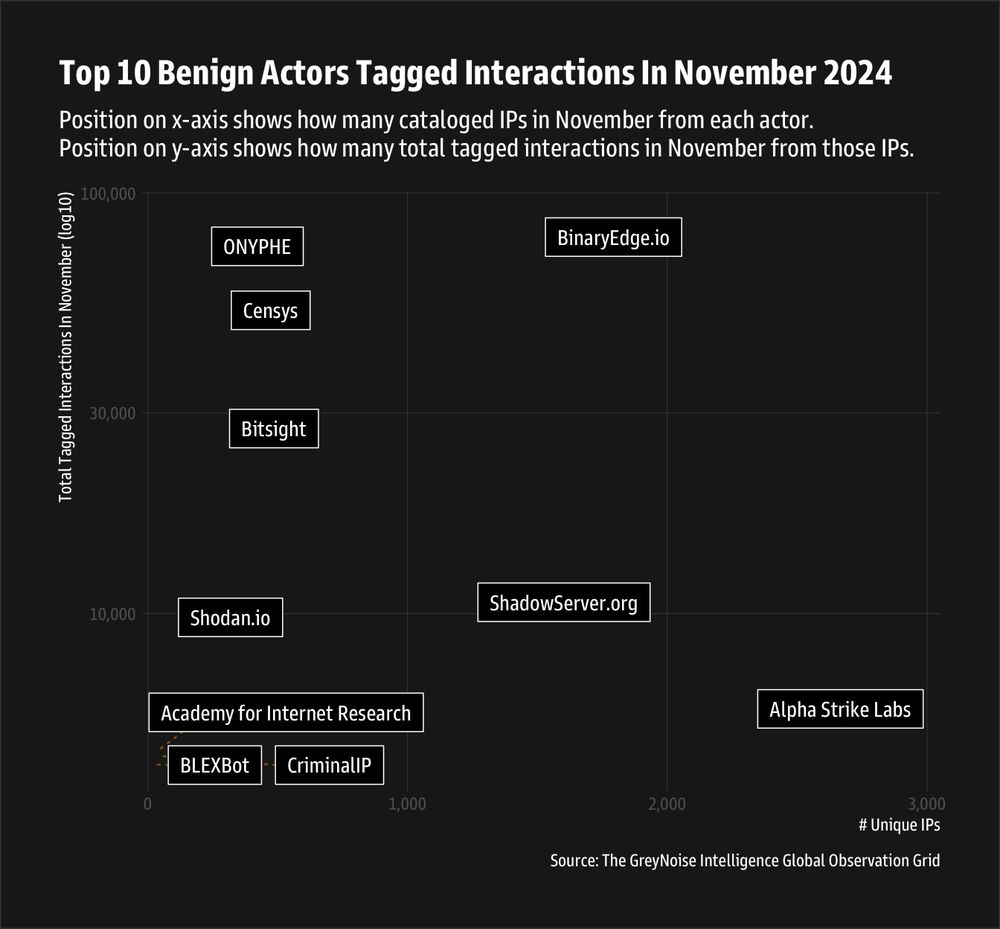
ONYPHE has a super cool geolocus MMDB — https://www.geolocus.io/ — that gets updated daily and has network-level metadata for IP addresses (ref first image JSON).
Since it's way more efficient to use this than their API, I built a cross-platform CLI tool for […]
[Original post on mastodon.social]
27.04.2025 17:09 — 👍 4 🔁 3 💬 0 📌 0
New geolocus-cli For ONYPHE’s Geolocus Database
ONYPHE has made available a free API and free MMDB download of their new Geolocus database. It provided IP address metadata in the form of: { "abuse": [ "amzn-noc-contact@amazon.com", "aws-routing-poc@amazon.com", "aws-rpki-routing-poc@amazon.com", "trustandsafety@support.aws.com" ], "asn": "AS14618", "continent": "NA", "continentname": "North America", "country": "US", "countryname": "United States", "domain": [ "amazon.com", "amazonaws.com", "aws.com" ], "ip": "3.215.138.152", "isineu": 0, […]
New geolocus-cli For ONYPHE’s Geolocus Database
ONYPHE has made available a free API and free MMDB download of their new Geolocus database. It provided IP address metadata in the form of: { "abuse": [ "amzn-noc-contact@amazon.com", "aws-routing-poc@amazon.com", "aws-rpki-routing…
#hackernews #news
28.04.2025 14:01 — 👍 2 🔁 1 💬 0 📌 0
The recovery continues, but things are not yet back to normal
29.04.2025 04:54 — 👍 1 🔁 1 💬 0 📌 0
Things are not yet getting better in Spain and Portugal. General downward trend and some visible instability in the remaining networks that are reachable.
#PowerOutage
28.04.2025 18:47 — 👍 2 🔁 0 💬 0 📌 2
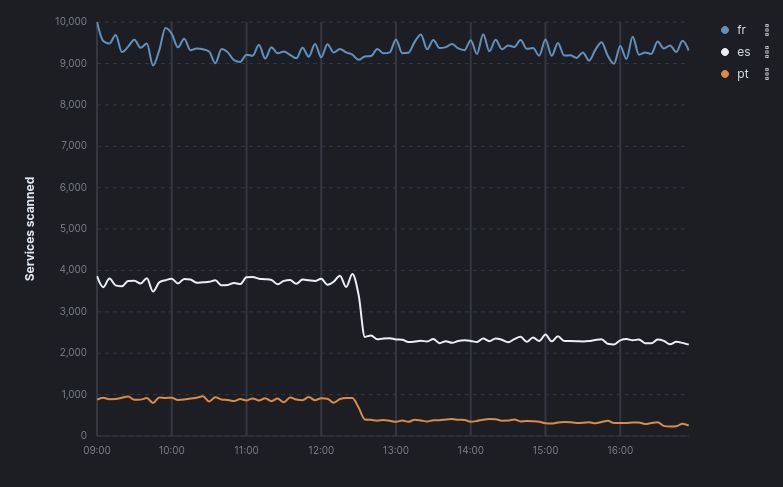
A chart showing Internet scan data plots for three countries; Spain, Portugal and France. The three lines are stable, with minor variations from 09:00 to 12:30. At 12:30 the lines for Spain and Portugal drop almost vertically to roughly 50% of their original levels. The line for France continues as for the start of the day.
The lines for Spain and Portugal have not returned to their original levels.
The electrical power outage in Spain and Portugal as seen from the Internet (France included for reference)
28.04.2025 16:03 — 👍 2 🔁 2 💬 0 📌 1
ERRATUM: the CVSS was given, it is a 9.8
25.04.2025 17:01 — 👍 0 🔁 0 💬 0 📌 0
CVE-2025-32432 – 0day Craft CMS discovered by Orange Cyberdefense – Blog | Big Data for Cyber Defense
#CVE-2025-32432 #0day #CraftCMS discovered by Orange Cyberdefense
💥Unauthenticated Remote Code Execution. No CVSS yet, we suggest to give it a 10
📌40,000 IP addresses representing over 37,000 domain names exposed, 12,168 unique domains vulnerable
Blog:
blog.onyphe.io/en/cve-2025-...
25.04.2025 15:45 — 👍 1 🔁 2 💬 1 📌 0
UPDATE: our scan has finished, near 22,000 devices are compromised.
22.04.2025 13:48 — 👍 0 🔁 0 💬 0 📌 0
Backdoor symlink sur des VPN SSL Fortinet – Blog | Big Data for Cyber Defense
💥Méthode de détection de la #backdoor #symlink sur #fortinet
"nous sommes prêts à la partager, en privé"
Plus de 18,000 équipements compromis
Lire l'article : blog.onyphe.io/backdoor-sym...
21.04.2025 12:50 — 👍 2 🔁 0 💬 0 📌 0
Symlink backdoor on Fortinet SSL-VPN devices – Blog | Big Data for Cyber Defense
💥Detection method for #symlink #backdoor on #fortinet
"we are willing to share it, privately"
More than 18k devices compromised
Read more: blog.onyphe.io/en/symlink-b...
21.04.2025 12:49 — 👍 4 🔁 2 💬 0 📌 2
Time to search for a decentralized way to deal with vulnerability identifiers.
16.04.2025 11:36 — 👍 2 🔁 0 💬 0 📌 0
You're nice to us, thank you for saying we are honorable ☺️
24.03.2025 17:14 — 👍 0 🔁 0 💬 0 📌 0
Many thanks :)
24.03.2025 10:12 — 👍 0 🔁 0 💬 0 📌 0
And there's an #RStats package for it—now.
codeberg.org/hrbrmstr/geo...
24.03.2025 08:38 — 👍 16 🔁 4 💬 2 📌 0

Geolocus by ONYPHE
Geolocus is an IPv4 & IPv6 geolocation service. Our motto is: you don't need misleading GPS coordinates, you need trusted IP to country locations. Furthermore, an IP address truly has 2 locations: 1 l...
❓Ever wanted to have an IP geolocation database with 2 locations, one physical for the device and one logical from whois data?
👉We provide a free MMDB file for download and a brand new Website for lookups & even a free API access:
www.geolocus.io
24.03.2025 07:46 — 👍 3 🔁 2 💬 0 📌 2

Zero Day
Bonjour ☕ Bienvenue dans la Cyber-revue à bas bruit de la semaine. Je sais, ça fait un bail, mais : j'ai eu des semaines de ouf (dont une qui s'est finie avec votre dévouée bloquée à Bruxelles pour ca...
👓La Cyber-revue à bas bruit est de retour ! L'alpha et l'oméga de cette édition : les zero days. C'est... surprenant 😇
Et aussi un podcast (coucou @nolimitsecu.bsky.social), des chiffres passionnants d' @onyphe.io et de La tech est politique et sa nouvelle rubrique.
www.linkedin.com/pulse/zero-d...
23.03.2025 14:01 — 👍 7 🔁 4 💬 0 📌 1
Installation | ONYPHE
Installation
The latest version of our cli tool has been released. Get v4.19.0 and find wrappers with sweet new APIs inside.
Available here ➡️
search.onyphe.io/docs/onyphe-...
or here 🐳 hub.docker.com/r/onyphe/ony...
or even here 🥷 metacpan.org/dist/Onyphe
18.03.2025 06:54 — 👍 3 🔁 2 💬 0 📌 0

💥 Great news 💥
#ASD #AttackSurfaceDiscovery APIs are on their way to general availability.
It will never be as easy to create an asset inventory for any organization attack surface #EASM
Backed by 10th of billions of informations we collect.
01.03.2025 17:37 — 👍 0 🔁 0 💬 0 📌 0

📣 Meet Thomas Damonneville - our founder - at the #M3AAWG organized by the Messaging, Malware, Mobile Anti-Abuse Working Group in Lisbon next week for his presentation entitled: “Hunting for phishing URLs, kits and business”.
👋 In partnership with Signal Spam
#phishing #phishingkit #cybersecurity
15.02.2025 18:20 — 👍 3 🔁 1 💬 1 📌 0
Yes, still 50k compromised devices. Since more than 12 months.
14.02.2025 12:21 — 👍 2 🔁 1 💬 0 📌 0
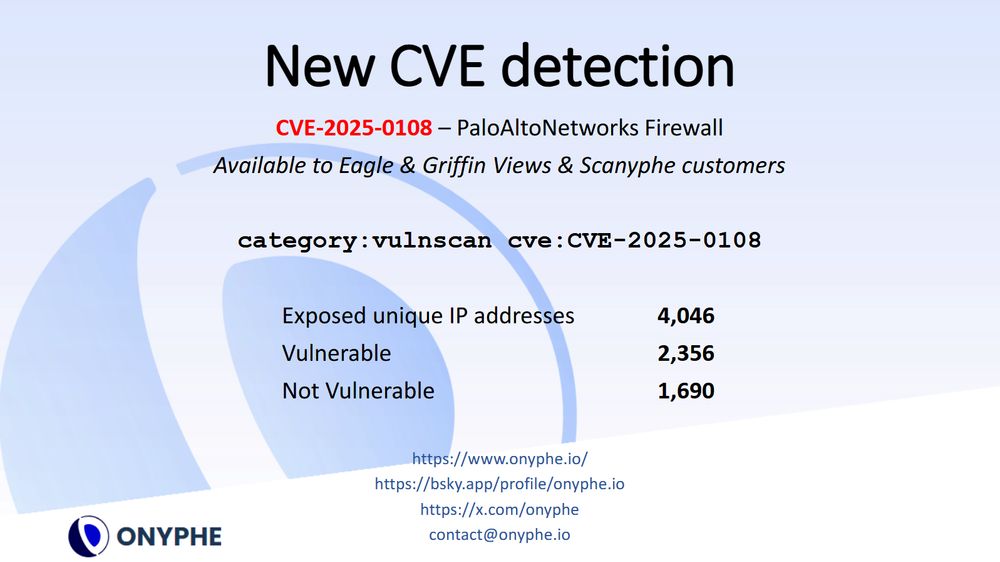
📣 We have added a new #vulnerability detection to our #ASM #AttackSurfaceManagement solution for #PaloAltoNetworks PA product:
CVE-2025-0108: authentication bypass on management interface
search.onyphe.io/search?q=cat...
Thanks to @assetnote.io for having shared the detection method.
14.02.2025 09:16 — 👍 6 🔁 3 💬 0 📌 0
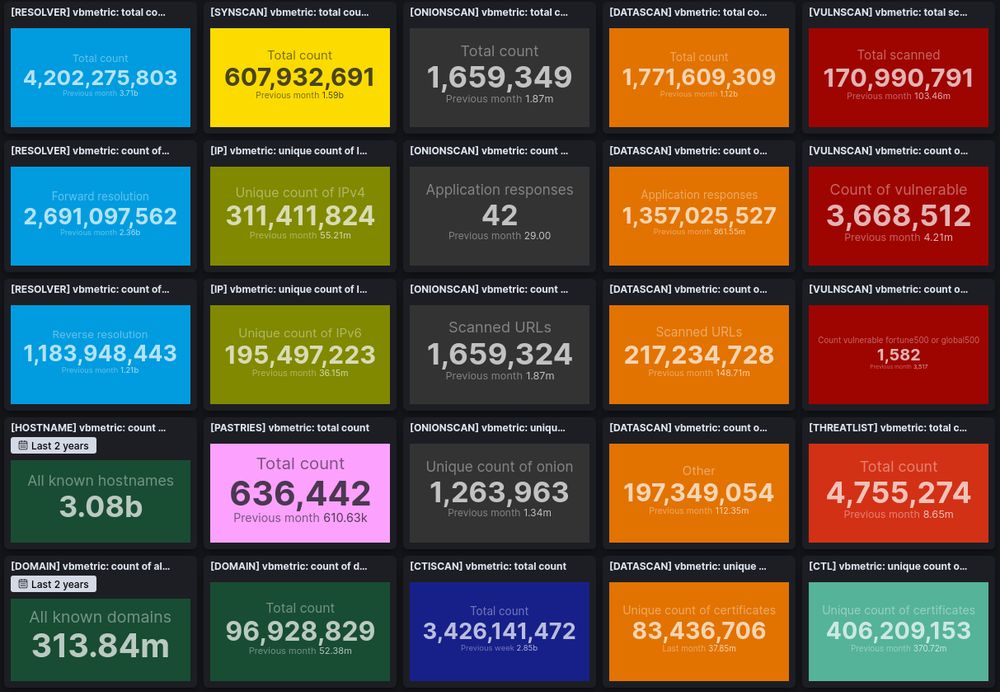
🎉 Retrospective 2024 and Roadmap 2025
👉 Over the last 12 months, we massively increased our visibility of Internet exposed assets. Until now, we focused on #ASM, but this year we will improve our automatic #ASD and expand into the #CTI segment.
Read more: search.onyphe.io/docs/write-u...
31.01.2025 14:22 — 👍 5 🔁 2 💬 0 📌 0
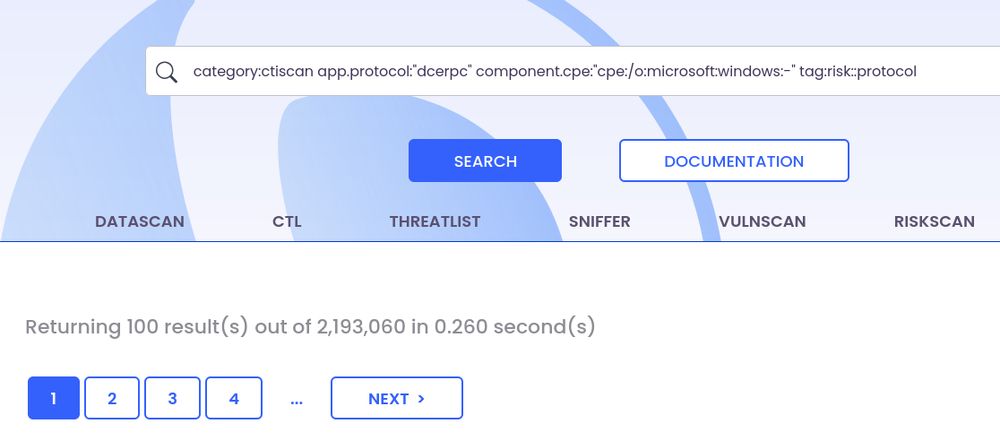
onyphe ctiscan result showing the number of rpc protocol exposed on Windows boxes, that is 2193060 found in 0.26 seconds
we tag it at a risky protocol
there are 2.2M results for Windows RPC boxes
03.01.2025 09:56 — 👍 1 🔁 1 💬 1 📌 0
Cc @greynoise.infosec.exchange.ap.brid.gy
21.01.2025 16:00 — 👍 1 🔁 0 💬 0 📌 0
Thanks, will do ☺️
21.01.2025 14:15 — 👍 0 🔁 0 💬 0 📌 0
🏁 Our main competitor, The Leading Internet Intelligence Platform for Threat Hunting and Attack Surface Management, can count on us to be their biggest challenger.
#AttackSurfaceManagement #ASM #CyberThreatIntelligence #CTI
Read the complete report here:
www.greynoise.io/blog/checkin...
21.01.2025 13:21 — 👍 0 🔁 0 💬 1 📌 0
cybersec engineer 🛡
devsecops enthusiast 💻
he/him
www.cybai.re
Infosec enthusiast. Stagiaire au #GIGN (Groupe Interceltique des Grammar Nazis)
a.k.a. boB Rudis • 🇺🇦 Pampa • Don't look at me…I do what he does—just slower. #rstats #js #duckdb #goavuncular•👨🍳•✝️• 💤• Varaforseti í Gögn Vísindi @ GreyNoise • 47-watch.com • https://stormwatch.ing • https://dailydrop.hrbrmstr.dev • Maine🦞
Dad, Vulnerability Research, Packet connoisseur. He/Him. Cyber Security Architect @greynoise.bsky.social
, DM's open. Top percentage Rattata. #cve #infosec #cybersecurity
https://remyhax.xyz/
@mttaggart@infosec.exchange. Displaced Philly boy. Threat hunter. Educator. Dad.
taggartinstitute.org
wtfbins.wtf
linktr.ee/mttaggart
Head of CERT @OrangeCyberdefense
https://research.cert.orangecyberdefense.com/
A geek. What else?
https://my.geekstory.net
A #SOCplatform boosted by #AI and #threatintelligence, combining #SIEM, #SOAR, #Automation in a single solution. Used by End-users, MSSP and APIs
My opinions are my own | IT Security engineer🛡️ I write articles on @50nuancesoctets 🚀 • #Cyber, #Tech and #Cloud 🌤️
I have permission to post all Cirnos. Feel free to ask for source.
I have a website: https://cirno.quest/
Not sure what to do with it though
pixiv: https://www.pixiv.net/en/users/59337025
CEO @TechAsiaLab -- Tweets for STEM, Maths, AI, Security, #Robotics, Technology, ESG, #SDG, CSR and #Sustainability
Location: Bangalore, India 🇮🇳
Linkedin: https://www.linkedin.com/in/amitavbhattacharjee
My Company: https://techasialab.com/
@ESET Distinguished Researcher | alum of McAfee, Microsoft MVP, Tribal Voice, Zultys | Mod @Lenovo, @Neowin.Net, Scots Newsletter forums | Intel Insider Council | Repost ≠ endorse
Parceque !
(mes opinions n'engagent que moi)
Ailleurs en ligne:
http://goupilland.net
http://github.com/FuraxFox/
http://mastodon.acm.org/@FuraxFox
Journaliste Sahel @jeuneafrique.com. Le cœur au Mali, le ventre en Italie et le dimanche dans @heidi-news.bsky.social. Passé par @liberation.fr @lemonde.fr