
From AI alignment with Eye on AI to blockchain governance on Unchained, these 2025 podcast picks cut through hype and surface the conversations worth carrying forward.
Full list & reflections: guptadeepak.com/the-best-tec...
@guptadeepak.com.bsky.social
🚀 Serial Entrepreneur - CEO & Co-founder @GrackerAI @LogicBalls 🌐 Cybersecurity Expert ➡️ AI Innovator 💡 Helping B2B SaaS companies boost revenue through AI

From AI alignment with Eye on AI to blockchain governance on Unchained, these 2025 podcast picks cut through hype and surface the conversations worth carrying forward.
Full list & reflections: guptadeepak.com/the-best-tec...
For tech-business context: a16z Podcast decodes industry shifts, while Pivot with Kara Swisher & Scott Galloway brings sharp, sometimes conflicting, takes on regulation, markets, and disruption. Diversity of viewpoints = deeper literacy.
15.08.2025 20:50 — 👍 0 🔁 0 💬 1 📌 0If security & privacy are on your mind: Risky Business remains must-listen for nuanced cybersecurity analysis. Want future-of-internet conversations? The Decentralists explores trust models beyond Big Tech control. Ideas that resonate with Bluesky’s vision.
15.08.2025 20:50 — 👍 1 🔁 0 💬 1 📌 1For AI thinkers: Lex Fridman Podcast still sets the gold standard, balancing technical depth with ethical nuance. For digital rights: Tech Won’t Save Us gives sharp critiques of how tech power is centralized. Both make you rethink what “progress” means.
15.08.2025 20:50 — 👍 0 🔁 0 💬 1 📌 0A thread on the tech podcasts shaping 2025.
In a year defined by AI leaps, cybersecurity battles & decentralization experiments, certain shows rise above the noise. These podcasts don’t just update you—they challenge how you think about the digital future.
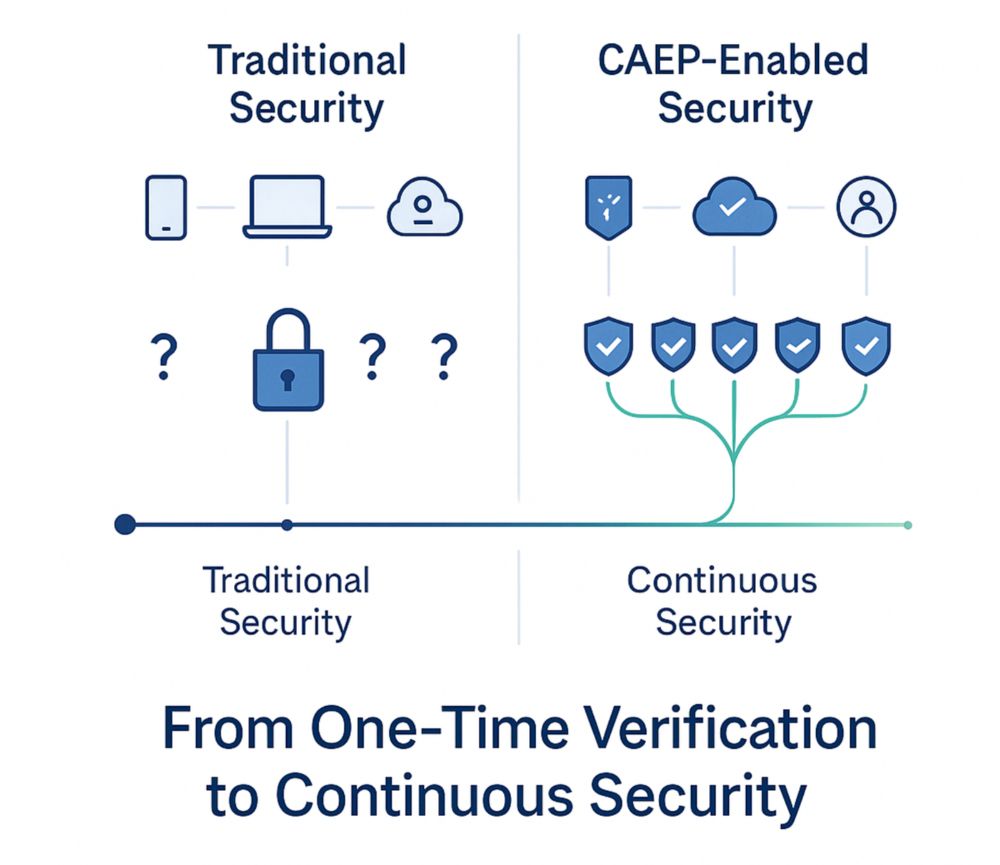
CAEP could become a cornerstone of zero trust and decentralized identity strategies — if adoption is as much about industry alignment as it is about technology.
Full article here: guptadeepak.com/the-future-of-continuous-access-control-openid-caep
The real shift here isn’t just technical — it’s philosophical.
We move from binary “allow/deny” decisions to adaptive trust models that evolve over a session.
Balancing security, privacy, and user experience becomes the core challenge.
OpenID’s CAEP framework standardizes this continuous trust evaluation across systems.
This matters because without interoperability, “continuous” security remains siloed, creating user friction and fragmented defenses.
Traditional access control assumes the world stays still between login and logout.
CAEP flips that: it evaluates trust continuously, adapting access as conditions change — location, device health, risk signals — without waiting for session expiry.
A thread on Continuous Access Evaluation Profile (CAEP) and why real-time, context-driven access control could redefine digital identity.
Static, one-time authentication isn’t enough in a world of dynamic users, devices, and threats.

Embracing these complexities is vital as decentralized identity frameworks emerge. Protecting digital identity isn’t just technical—it's societal. Thoughtful authentication design lays the groundwork for trust in digital ecosystems.
Full article here: guptadeepak.com/staying-secu...
We must move toward adaptive, risk-based authentication that considers user behavior and environmental signals. Such nuanced systems imply ethical design decisions about data collection and user autonomy. The path forward demands collaboration across tech, policy, and user advocacy.
07.08.2025 19:16 — 👍 2 🔁 0 💬 1 📌 0Password managers and biometrics offer usability gains but introduce trade-offs. Centralization of secrets or biometric data risks becoming high-value targets. This tension embodies larger challenges in digital identity: balancing convenience, privacy, and resilience in an evolving threat landscape.
07.08.2025 19:16 — 👍 0 🔁 0 💬 1 📌 0Multi-factor authentication (MFA) is more than a checkbox—it's a crucial shift in trust paradigms. But MFA's effectiveness depends on context, user education, and threat models. Blind reliance creates new attack surfaces, urging us to rethink layered security beyond technology alone.
07.08.2025 19:16 — 👍 0 🔁 0 💬 1 📌 0A thread on securing digital identities during login.
Our most routine act online—logging in—often hides systemic vulnerabilities. While passwords remain the baseline, their fragility reveals broader issues in how we design authentication for a decentralized, privacy-centric future.

The future of programming will integrate AI agents like Claude as partners, not just tools — transforming collaboration, creativity, and control. Navigating this requires humility and foresight.
Full article here: guptadeepak.com/claude-code-...
But complexity and trust remain challenges. Debugging AI-generated code requires new tools and mindsets. The AI may deliver elegant solutions quickly but leaves us with questions about reliability, accountability, and unintended consequences in critical systems.
05.08.2025 19:14 — 👍 0 🔁 0 💬 1 📌 0This shift implicates systemic changes in software engineering. Teams may prioritize AI prompt mastery and governance over syntax mastery. The roles of coders may evolve into more strategic architects and validators, addressing AI biases, correctness, and ethical concerns.
05.08.2025 19:14 — 👍 0 🔁 0 💬 1 📌 0Claude’s approach is not just about automating code writing; it redefines how we conceptualize programming itself. Instead of explicit instructions, we provide abstract goals. The AI interprets, plans, and iterates — blurring lines between coding, design, and communication.
05.08.2025 19:14 — 👍 0 🔁 0 💬 1 📌 0A thread on Claude and the future of programming.
We stand at a crossroads, where traditional coding paradigms shift under the influence of AI agents like Claude. This pushes us toward a future where human intent and AI collaboration reshape development workflows.

The future favors platforms, but specialized identity problems remain fertile ground for innovation. Enterprises must balance short-term integration pains against long-term unified security gains.
Full article here: guptadeepak.com/palo-alto-ne...
Yet consolidation risks slowing innovation. Large platforms may overlook niche challenges like privacy-preserving identities or AI behavioral audits, creating space for startups. The real frontier is now AI agent identity—contextual privileges, anomaly detection, scalable control at massive scale.
01.08.2025 20:23 — 👍 0 🔁 0 💬 1 📌 0Identity security is evolving: traditional boundaries—CIAM, PAM, workforce IAM—are blurring. Palo Alto’s move integrates CyberArk’s privileged access strengths with network security, answering CISOs' calls to simplify sprawling security stacks through unified policies and shared threat intelligence.
01.08.2025 20:23 — 👍 0 🔁 0 💬 1 📌 0This deal accelerates platform strategy, positioning Palo Alto to lead in AI agent security by managing privileged AI identities—crucial as autonomous AI agents proliferate. It also reflects broader industry consolidation, merging network, cloud, and identity security under one roof.
01.08.2025 20:23 — 👍 0 🔁 0 💬 1 📌 0A thread on Palo Alto Networks’ $25B acquisition of CyberArk—a landmark deal reshaping cybersecurity and identity. It signals a shift from fragmented tools to integrated platforms embracing human, machine, and AI identities, fundamentally redefining how we secure access in enterprise systems.
01.08.2025 20:23 — 👍 1 🔁 0 💬 1 📌 0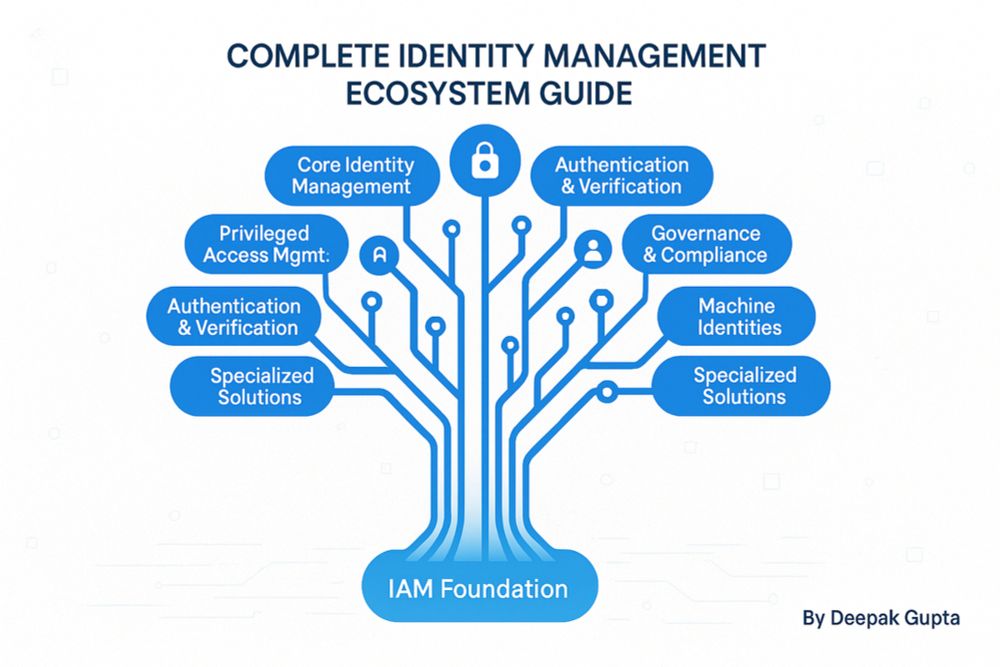
Decentralized and quantum-safe identity are future frontiers, offering privacy and resilience. Adoption is early, but success means ongoing evolution grounded in trust.
Full article here: guptadeepak.com/understandin...

Access models like RBAC, ABAC, PBAC suit different needs. Federation, directories, and identity analytics boost security and ease cross-system access. Sector-specific demands add complexity.
31.07.2025 23:18 — 👍 0 🔁 0 💬 1 📌 0Governance with IGA and Access Governance keeps compliance constant. Authentication evolved from MFA to passwordless and adaptive methods, balancing security and UX. Machines and AI agents also need strong identity management.
31.07.2025 23:18 — 👍 0 🔁 0 💬 1 📌 0Traditional IAM manages workforce access. CIAM scales customer identity with self-service and social login. PAM and PIM control privileged accounts, crucial for securing sensitive systems.
31.07.2025 23:18 — 👍 0 🔁 0 💬 1 📌 0A thread on understanding the complete identity management ecosystem…
Identity today is no longer just passwords. It’s a complex system with distinct solutions for customers, privileged users, and even machines. Each has unique security demands and roles that must align to build effective trust.