
Using the Pyroelectric Effect to Identify Broken MLCC Capacitors
15.11.2025 21:30 — 👍 6 🔁 3 💬 0 📌 0@fjullien.bsky.social

Article original: social.treehouse.systems/@garyodernic...
14.11.2025 12:12 — 👍 0 🔁 0 💬 0 📌 0
Machdyne Schoko with ESP32-S3 as JTAG bridge

Lattice ECP5 in SSPI mode

new SpiOverJtag support able to access Flash in complex JTAG chain
🎉 openFPGALoader v1.0.0 is out!
Major highlights:
• Complete spiOverJtag rework for Xilinx(complex chains)
• New Sponsors/Partners section
• AlteraFPGA MAX10
• Lattice ECP3 + ECP5's SSPI
• EspressifSystem ESP32-S3 as JTAG
🔗 github.com/trabucayre/o...
Thanks to all!

board layout in KiCad with lots of layers and colors
i reverse-engineered the Raspberry Pi Compute Module 5! check it out at github.com/schlae/cm5-r...
24.08.2025 20:57 — 👍 346 🔁 63 💬 9 📌 8Je viens de voir ton message, je t'ai envoyé un mail.
17.07.2025 07:40 — 👍 1 🔁 0 💬 0 📌 0Part 2 of my SCA journey is now live: I demonstrate a successful CPA attack on an unmodified device during AES key unwrap.
collshade.fr/articles/cpa...
I've just had a look at the errata list, and yes, it's not short...
22.03.2025 19:26 — 👍 1 🔁 0 💬 0 📌 0Are these bugs documented somewhere?
22.03.2025 17:23 — 👍 0 🔁 0 💬 1 📌 0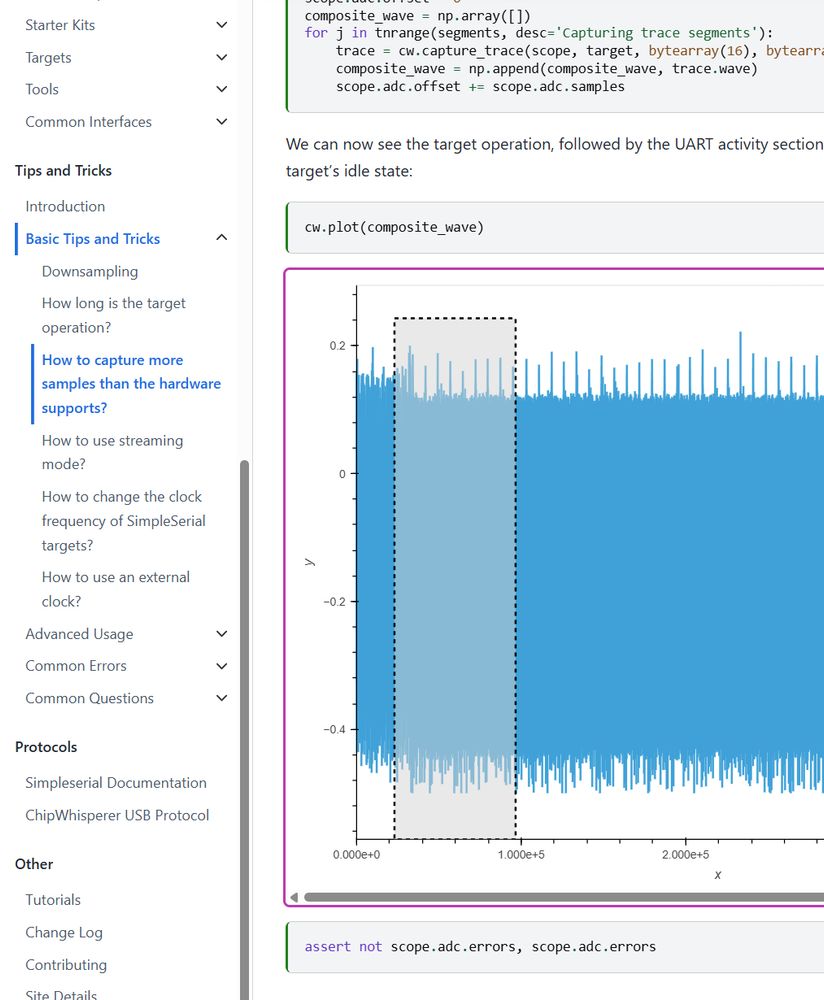
For the past while J-P at @newae.com has been working on a major #ChipWhisperer doc refactor - this is now live, check out chipwhisperer.readthedocs.io/en/latest/in... . It moves software, hardware, and even some tricks/tips all into once place using Jupyter Books. Huge improvement in usability!
14.03.2025 22:14 — 👍 8 🔁 6 💬 0 📌 0OK, it's official on the website now: KiCad 9 is out!
www.kicad.org/blog/2025/02...
Ghidra 11.3 is OUT!
PyGhidra is the new feature to be excited about.
It’s a Python library providing direct access to the Ghidra API.
I expect this to massively increase Reverse Engineering tool development, as it significantly reduces the barrier to entry for Ghidra interaction.

Stylized circuit board, showing a blue "K" with a DIP12 next to it that resembles the Ki from the KiCad logo. The dot for the "i" is drawn as a gold bodge wire shaped into the number 9
What's this? Oh, nothing much. Just KICAD VERSION 9RC2 dropped! We are only a couple weeks away from the final release. Test out the nightly builds now and see if you can find any showstoppers that we can fix before that happens.
forum.kicad.info/t/stable-ver...



🎉 Exciting news! We're thrilled to announce that @aisler.net is sponsoring our robotics team for the 3rd year in a row! 🙌 Their support helps us design and build high-quality PCBs for our robots 🤖
More on our blog: leskaribous.fr/posts/aisler/
Thanks, Aisler!
aisler.net
#Robotics #PCB #Makers
I've been diving into electromagnetic (EM) side-channel attacks with Correlation Power Analysis (CPA) these past few weeks and just published a blog article about my journey: collshade.fr/articles/cpa...
10.01.2025 06:45 — 👍 7 🔁 3 💬 1 📌 0
My videos for Flare-On 2024 are live! Watch me reverse engineer all the challenges from start to end. 🎉🥳
+ Commentary video featuring SuperFashi, where we review the chals together.
* 45 hours of content
* 400+ GB of raw footage
Merry Christmas! Link: www.youtube.com/watch?v=vwW9...
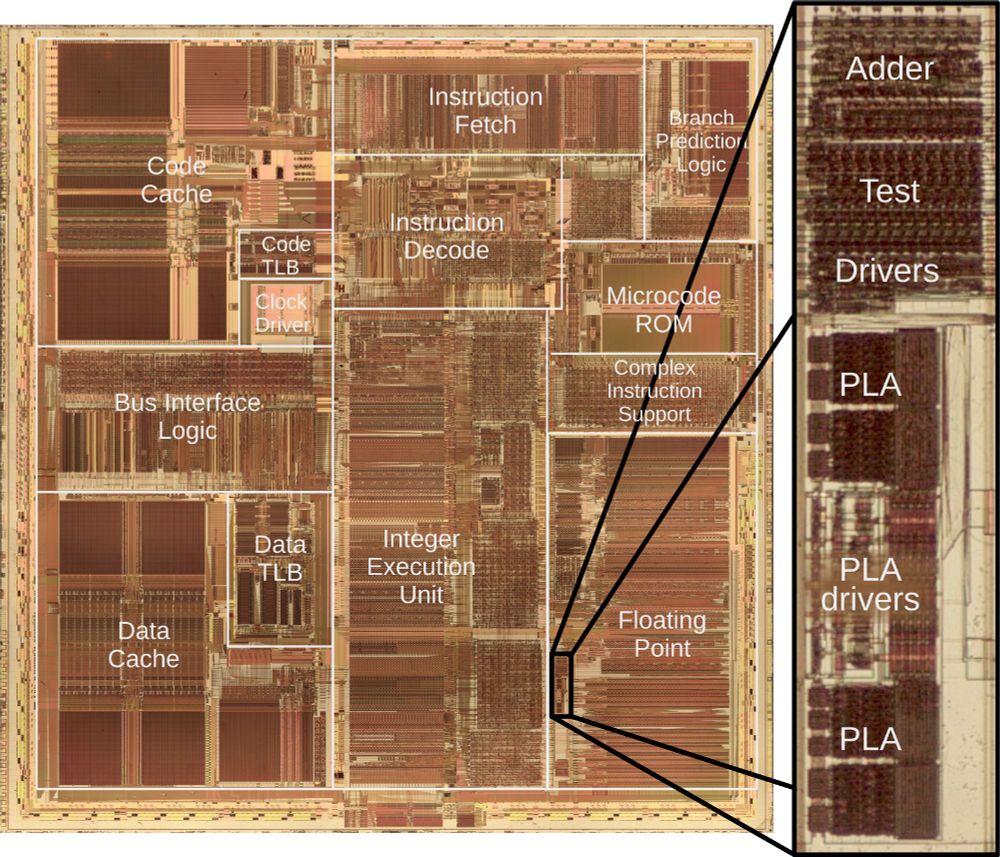
A die photo of the Pentium processor with the main functional blocks labeled including the caches, instruction fetch and decode, integer execution, and floating point. The image consists of complex patterns of rectangular regions in reddish and brownish colors. The image zooms in on a small part of the floating point unit giving a detail of an adder and PLA circuit.
Intel launched the Pentium processor in 1993. Unfortunately, dividing sometimes gave a slightly wrong answer, the famous FDIV bug. Replacing the faulty chips cost Intel $475 million. I reverse-engineered the circuitry and can explain the bug. 1/9
06.12.2024 16:48 — 👍 712 🔁 235 💬 16 📌 28
I understand why people need HPC to work on side channel. It took me hours to get this convergence plot. It's ONE byte and only 10000 traces...
11.12.2024 17:36 — 👍 1 🔁 0 💬 0 📌 0"In AES decryption, the round keys are used in reverse order compared to encryption. The first round key for decryption is actually the last round key of the encryption key schedule." 🤦
I was looking for my key, not that....
Now I start to see good key guess!
Multi-track drifting, er, dragging coming to KiCad 9! Video and code courtesy of Tom W :)
04.12.2024 22:47 — 👍 208 🔁 39 💬 11 📌 7KiCad is proud to announce the release of 8.0.7
We have lots of bug fixes and speed improvements in this release, so upgrading is highly recommended!
www.kicad.org/blog/2024/12...
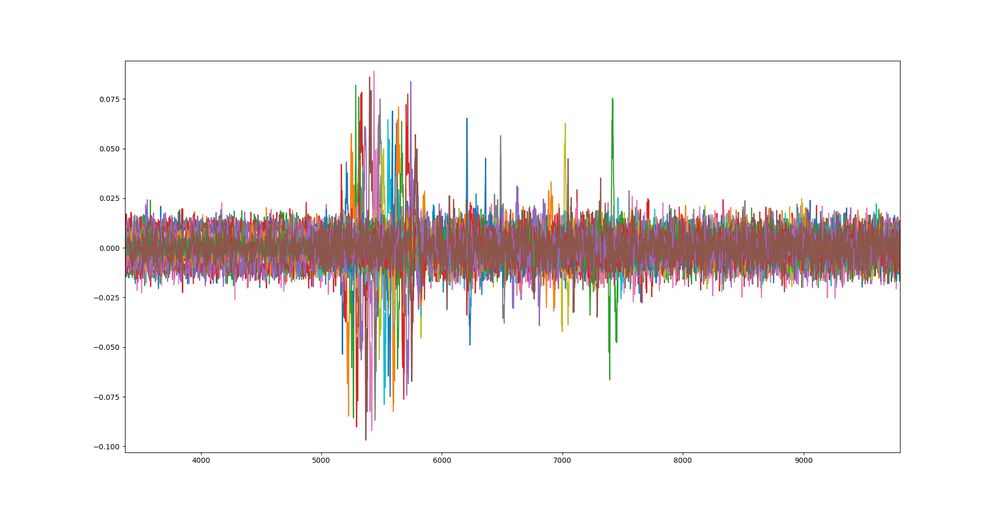
I made some progress. I couldn't find any correlation. Turned out my traces were not properly aligned. As suggested by
@Baldanos
I made a CPA on the cyphertext just to be sure I can detect something. And yes, this is my input bytes leaking:

Hello AES!
18.11.2024 21:35 — 👍 0 🔁 0 💬 1 📌 0
I didn't know that italic could be a variant for part numbers 🤨
17.11.2024 20:51 — 👍 1 🔁 0 💬 0 📌 0