
OAuth Vulnerabilities in Desktop Apps
Security flaw in desktop app OAuth allows account takeover with malicious links. Understand attack steps, why it works, and fix strategies
From "Log in with OAuth" to "Your Account Is Mine"
I just published my first write-up on my blog:
blog.mirzadzare.net/from-log-in-...
This article is based on a recent #OAuth vulnerability I discovered. I hope you enjoy it! ❤️🔥🙌
#BugBounty #cybersecurity
01.12.2025 09:47 — 👍 3 🔁 0 💬 0 📌 0
You can use FBack to generate target-specific wordlists and fuzz for possible backup files:
echo https://example[.]com/files/config.php | fback -y 2020-2024 -m 1-12
Example Output:
config.php.bak
config_backup.php
config_2024.php
files_config.php
4/5
08.07.2025 06:44 — 👍 1 🔁 0 💬 2 📌 0
Methodology
You know those static websites, especially WordPress sites, where you encounter paths like:
example[.]com/files/config.php
But you don't have access to config.php, so now what? What should you test here?
3/5
08.07.2025 06:44 — 👍 0 🔁 0 💬 1 📌 0
What’s FBack?
It’s a tool that generates target‑specific wordlists to fuzz for backup files—think config.php.bak, config_backup.php, etc. Its perfect for hunting juicy unattended backups on static or WordPress sites.
2/5
08.07.2025 06:44 — 👍 0 🔁 0 💬 1 📌 0

It’s been a while since my last update, but I’m thrilled to share some exciting news about my project called Fback
1/5
#bugbounty #bugbountytips #bugbountytools #recon #hacking #CyberSecurity
08.07.2025 06:44 — 👍 1 🔁 0 💬 1 📌 0
GTA VI mountains:
12.02.2025 16:28 — 👍 0 🔁 0 💬 0 📌 0
We can extract subdomains from these providers using kaeferjaeger, which performs this task for us every 60 minutes.
[Passive Search] If you lack the necessary resources, you can utilize kaeferjaeger provider to conduct a passive search. 2/3
12.02.2025 16:21 — 👍 0 🔁 0 💬 1 📌 0

Subdomain Enumeration - Finding subdomains that are hidden in the cloud.
We need to conduct a certificate search on the IP ranges of cloud providers such as Amazon, Digital Ocean, Google, and Microsoft. 1/3
12.02.2025 16:21 — 👍 1 🔁 0 💬 1 📌 0
I’ve updated the bug bounty & content creators starter pack with classic research group @hackerschoice.bsky.social! Let me know if you’re not on this list and would like to be added.
go.bsky.app/GD7hKPX
03.02.2025 18:36 — 👍 44 🔁 12 💬 7 📌 1

I’ve added a new feature to Robofinder, and now you can extract old parameters from archived robots.txt files. This is very useful for your recon process because you may find hidden or deprecated parameters that other tools might miss.
Github: github.com/Spix0r/robof...
30.01.2025 18:45 — 👍 0 🔁 0 💬 0 📌 0
Why should i search for old robots.txt files?
Because it's possible that the site you are investigating had numerous paths listed in its robots.txt file that were subsequently removed in later updates. Despite their removal, those paths, files, and parameters may still be accessible.
3/3
30.12.2024 17:37 — 👍 1 🔁 0 💬 0 📌 0

Robots.txt File And #Reconnaissance
What is a robots.txt file?
The robots.txt file is designed to restrict web crawlers from accessing certain parts of a website. However, it often inadvertently reveals sensitive directories that the site owner prefers to keep unindexed.
1/3
30.12.2024 17:37 — 👍 1 🔁 0 💬 1 📌 0

Writeup-Miner is live again on T.me/Daily_Writeups
Join to be among the first to access the latest cybersecurity write-ups!
Source Code: github.com/Spix0r/write...
26.12.2024 12:28 — 👍 0 🔁 0 💬 0 📌 0
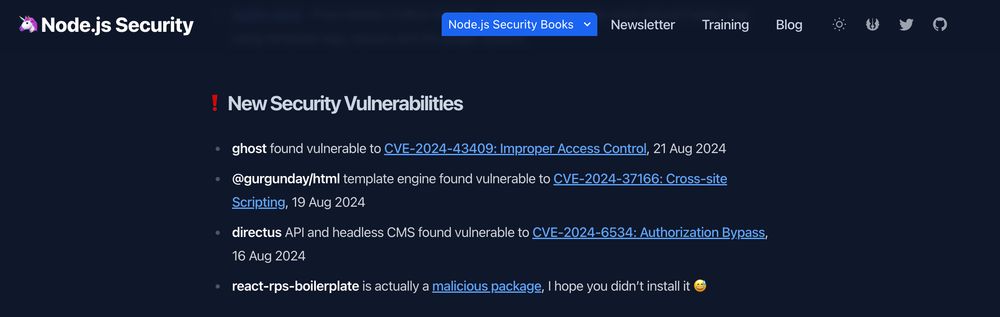
Find out about new JavaScript security vulnerabilites in npm packages on the Node.js Security newsletter: www.nodejs-security.com/newsletter/n...
25.12.2024 16:00 — 👍 2 🔁 1 💬 0 📌 0
To hack a thing, first learn to build it.
24.12.2024 15:12 — 👍 0 🔁 0 💬 0 📌 0
Happy Birthday♥️🍰
22.12.2024 15:39 — 👍 1 🔁 0 💬 0 📌 0
Helped me a lot! Thank you.
21.12.2024 17:23 — 👍 1 🔁 0 💬 0 📌 0
Hey BlueSky!
I case you missed it:
I've created cspbypass.com
A site where you can search for known CSP bypass gadgets to gain XSS.
It already contains a bunch of useful gadgets with contributions from your favourite hackers.
If you have some CSP bypasses to share, feel free to contribute!
14.11.2024 14:57 — 👍 71 🔁 24 💬 1 📌 1
These tools are amazing! I really liked the idea.
21.12.2024 17:20 — 👍 0 🔁 0 💬 0 📌 0
I'm building two web security tools at the moment:
Shazzer - A shared online fuzzer
shazzer.co.uk
Hackvertor - Web security conversion tool
hackvertor.co.uk
20.12.2024 09:12 — 👍 15 🔁 4 💬 2 📌 0
I challenge you to a duel🔫
21.12.2024 14:49 — 👍 1 🔁 0 💬 0 📌 0
XSS and coffee enjoyer @ Nord Security
https://www.brzozowski.io
| 🔐 appsec | 🤓 CTO | ✨ indy hacker | 🎛️ modular synth | 🪳 coder | 🏕️ camping
Developer of Faction: an open source pentesting framework.
https://github.com/factionsecurity/faction
https://bsky.app/profile/factionsecurity.com
CTF player with The Flat Network Society - bug bounty & web security research
Hacker, command injector and crowdsourced security enthusiast
Full Time Bug Bounty Huner
Security Researcher | Speaker | Cooker
LevelUpX Champion 2022/2023
Team Hunt - Hack Cup Winner 2022/2023
15+ 0Day
CVE-2022-21500 | CVE-2022-21567
Top 3 Bugcrowd P1 Warrior
Cyber, InfoSec, DevSecOps, AppSec, Hacker, Linux, CLI, IT Management, HPC, GenAI, Code, OWASP, ISC2, DEFCON, Memes. All my technical snark is kindhearted jest and sarcasm.
founder @bugcrowd && co-founder @disclose_io || hacker, entrepreneur, executive, advisor || عصا موسى || #w00w00
Security Architect | Bug Bounty Interested | Husband | Father | Early medieval reenactor | Glass bead maker
Security and insecurity things.
Mostly here for infosec, swe, devops, and other jobs babysitting computers.
Given up on fixing typos.
📍The elevator is at the rare of the platform.
Penetration Testing, Red Teaming, Incident Response, Managed Detection, Digital Forensics, Security Training, Managed Bug Bounty, Cyber Training Range
#InfoSec person. KT0DBK is my callsign. I run https://clairereynoldsforcongress.org
I post more often on https://infosec.exchange/@todb, bridged here as @todb2.hugesuccess.org and turns out, is much more #infosec than #txpol political. Follow both!
Hi I am the owner and Creator of Hack To Prove It.
Engineer, Hacker, Pentester, Gamer, and constantly curious.
th4ts3cur1ty.company Magical Genie Person 🧚♀️
Former/Recovering Cyber Security Recruiter
BSides Lancashire Founder
Responsible adult for BSides Leeds
Supporter of the Infosec community
Head of Mentoring for Capslock
Working Parent
Teacher, neurobiologist, hyper-follower from Milan, Italy.
















