There are other behaviours since CA has changed to protect resources instead of Apps.
for example it's not possible anymore to exlude or include a specific app in some circumstances.
CA unfortunatly is getting useless for 3rd party apps without resources within M365..
22.02.2025 06:43 — 👍 0 🔁 0 💬 1 📌 0
So this probably "resolves" issue 2 described here:
www.msb365.blog?p=5780
When MS decided to change from targeting resources instead of apps, several problems have been created for us & our customers. Hopefully MS will resolve this issues also on a technical level, not only adjusting the docs..
05.02.2025 11:54 — 👍 0 🔁 0 💬 0 📌 0

Heads-up!
I just published a new article on the MSB365 Blog that dives into an unexpected behavior uncovered with Conditional Access.
This article is written by @sololugan0.bsky.social as a guest contribution.
www.msb365.blog?p=5780
#MVPbuzz #ConditionalAccess #EntraID #MSAzure #Azure
15.01.2025 07:18 — 👍 1 🔁 1 💬 0 📌 0
You can use the Grant Control of MFA together with a Sign-in frequency Session Control: Every time in the same policy which is targeting the Authentication context.
07.01.2025 15:58 — 👍 1 🔁 0 💬 1 📌 0
CA Policy, Include Resources: All, Exclude: Another random App
Auth behaviour :
- Web: Applied
- Single-page application: NOT Applied
- Mobile and desktop applications: NOT Applied
This applies only to policies with GRANT Controls. Policies with Session controls are always applied.
19.12.2024 08:07 — 👍 0 🔁 0 💬 0 📌 0
more detail about the strange behaviour:
CA Policy, Include Resources: All, Exclude: None
Auth behaviour depending on platform config of the App:
- Web: Applied
- Single-page application: Applied
- Mobile and desktop applications: Applied
19.12.2024 08:07 — 👍 0 🔁 0 💬 1 📌 0
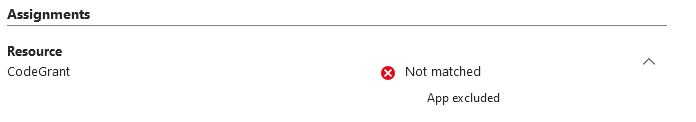
Update on that one, i tested it with other app exclusions.
Its seems that, i can exclude any random app (tested with custom App or even 'Report Message').
As soon as one app is excluded from the CA Policy, when getting a token for my test app, behaviour is again the same.
18.12.2024 20:06 — 👍 0 🔁 0 💬 0 📌 0
When removing the excluded Microsoft Intune Enrollment App, CA & controls targeted to all resources are applied even for my test app.
Other CAs targeted to specific App still 'not included', but that seems to be expected behaviour.
18.12.2024 19:55 — 👍 0 🔁 0 💬 1 📌 0
On a Desktop without PRT using HTTP Requests / PS Invoke-RestMethod & OAuth 2.0 auth code grant (without client secret or cert)
BUT: I might have found the problem: CA Policy which is targeted to all resources had one App excluded: 'Microsoft Intune Enrollment'
18.12.2024 19:55 — 👍 0 🔁 0 💬 1 📌 0
After that i'm able to use the token against Graph to read information about the user or related groups, for example:
"https://graph.microsoft.com/v1.0/me/people"
with platform configuration SinglePageApp (also public client), I'm not able to do so withour fullfulling requested CA controls.
18.12.2024 12:38 — 👍 0 🔁 0 💬 1 📌 0
In my test-App, if platform configuration of the app is 'Mobile and desktop applications' I'm able to get a token for the scope "People.Read","user.read" successfully without fulfilling MFA or compliant device requirement of CA Policy targeted to all ' resources'.
18.12.2024 12:38 — 👍 0 🔁 0 💬 1 📌 0
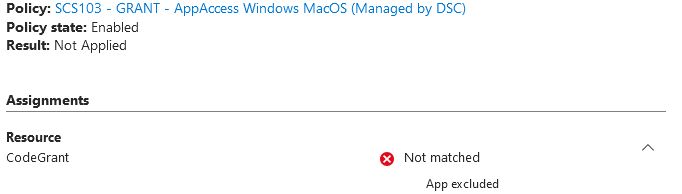
Okey, but it's not even included in a CA requiring compliant devices (or any other control) for "all resources' (only 'Mobile Apps and Desktop Client', not for Browser)
And why is there a difference in CA Policy evaluation between the different platforms when requesting the same scopes?
18.12.2024 11:08 — 👍 0 🔁 0 💬 1 📌 0
Compliant Devices, Networks (also GSA) or even Block specific users from accessing certain apps.
Therefore #ZeroTrust and #SASE implementations with CA are not possible anymore. What am I missing?
@merill.net @markasimos.bsky.social
#MicrosoftSecurity
18.12.2024 10:29 — 👍 0 🔁 0 💬 1 📌 0
This means that, until an App is configured with a platform of 'Mobile and desktop applications' and doesn't access other resources within M365 (as usual with 3rd party Apps), CA is not able (anymore?!) to enforce controls such as
18.12.2024 10:29 — 👍 1 🔁 0 💬 1 📌 0
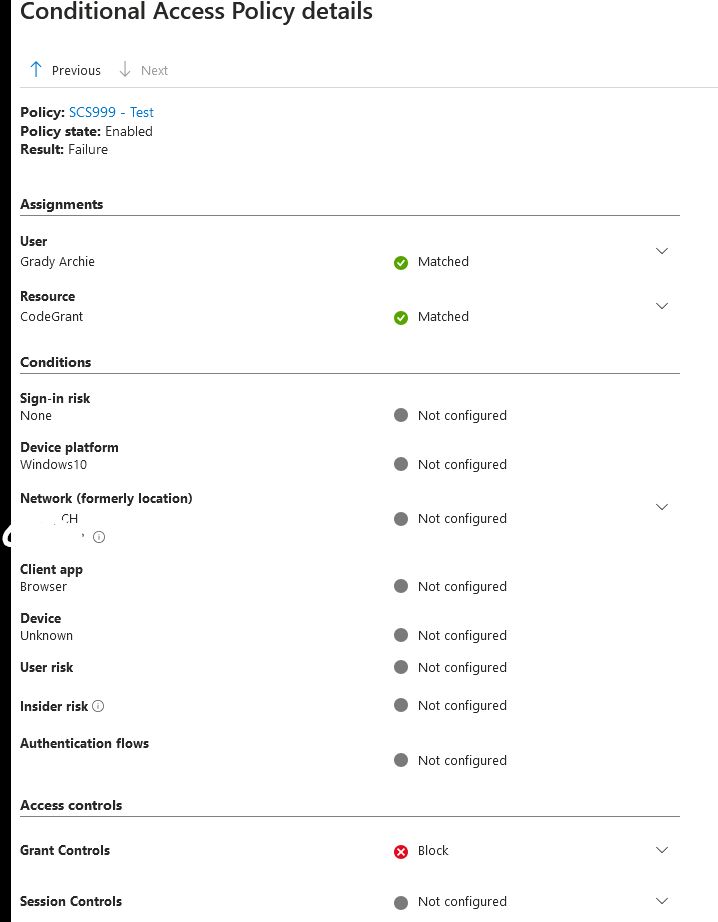
When we do the same for a SPA or Web platform, the App is included and controls are applied as expected:
18.12.2024 10:29 — 👍 0 🔁 0 💬 1 📌 0
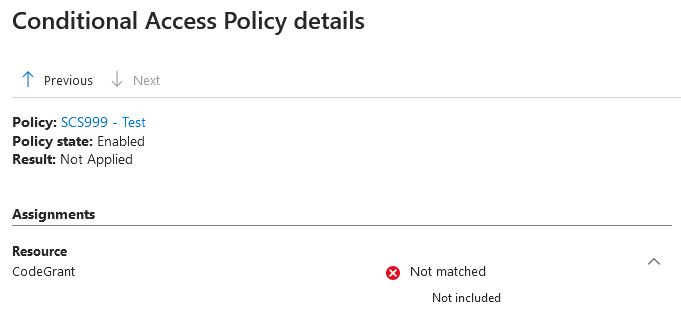
Was it really just a renaming from all 'All cloud apps' to 'All resources' or are there more changed wich are not mentioned?
When requesting a token for the platform 'Mobile and desktop applications' #ConditionalAccess policies are 'not applied' anymore because the app is 'excluded':
18.12.2024 10:29 — 👍 1 🔁 0 💬 1 📌 0

Cloud apps, actions, and authentication context in Conditional Access policy - Microsoft Entra ID
What are cloud apps, actions, and authentication context in a Microsoft Entra Conditional Access policy
It seems that ConditionalAcces in #EntraID has become useless for Apps requiring only minimum Graph scopes when authenticating.
When requesting Accesstokens with OAuth for an App, CA-Policies are not applied (anymore). As described:
learn.microsoft.com/en-us/entra/...
18.12.2024 10:29 — 👍 1 🔁 0 💬 1 📌 0
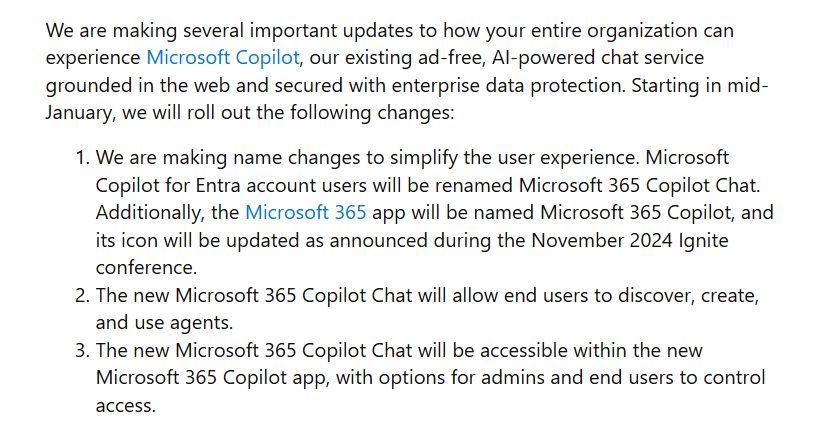
Bing Chat Enterprise => Microsoft Copilot => Microsoft 365 Copilot Chat
Well, I am not sure if this helps the end users understand the difference between the "free" chat included in Entra ID and Microsoft 365 Copilot 😆
17.12.2024 05:55 — 👍 1 🔁 1 💬 0 📌 0
Should not be the case for Privateapps. maybe if they are MAM managed --> you mentioned App Policy in the controls..
Device Filter would require an additional Policy wich blocks Devices (Control Block) and exclude Devices with correct enrollment profile name.
29.11.2024 10:42 — 👍 2 🔁 0 💬 1 📌 0
You could work with the Grant/Compliant Device operator in CA and a enrollment restriction in Intune. This way only selected enrollmenttypes can get a compliant state for CA.
If you use other enrollment methods for Android (MDM), maybe you could use the include Filter IN CA (personal, corporate, .)
29.11.2024 06:41 — 👍 1 🔁 0 💬 1 📌 0
Microsoft MVP/Modern Workplace consultant
systanddeploy.com
#Powershell #MSIntune #MDT #WPF #MECM #MEMPowered #SelfX
Multiple Microsoft MVP and Speaker for #MSTeams and #Microsoft365. Principal Microsoft Cloud Architect at @swisscom and Blog at @_MSB365 | #MVPbuzz
Mountainbiker, Microsoft 365
Microsoft 365, Azure, AI • Frankie 🐶
🇩🇪🇬🇧
Sarcastic. Subtle. Curious.
Principal Identity Security Researcher @Microsoft. Ex-Secureworks (PhD, MSc, MEng, CITP, CCSK).
And yes, opinions are my own ;)
Principal Security Researcher @Microsoft. Author, Blogger, Speaker, and Baseball Nerd. Always has an overwhelming backlog of books and video games to get through.
computer security person. former helpdesk.
SecOps Witch 🔮
Lego zealot & Blizzard tragic 🎮
Slave to 7yo terror 👶
Australian based 🦘
Provider of sarcasm & profanity 🤬
she/her ♀️
Views ALL MINE 💜
https://linktr.ee/girlgerms
Cybersecurity Specialist, Public Speaker, Ex-Hacker.
https://marcushutchins.com
Hacker. Friend. Cybersecurity Researcher at Huntress.
I'm Thee Sarcastic Warrior, Keeper of Secrets in MSR, Inquisitor of the CTO, Defender of Caturdays, Hugger of Trees and Hunter of Bots.
Security researcher.
I have a blog: https://sapirxfed.com
Azure Technical Trainer @ Microsoft | MCT | Founder AzureCrazy.com | Blog at cloudbuild.co.uk | #Microsoft #Azure | Views are mine
Microsoft Security MVP + Microsoft Security Practice Lead at Threatscape
Mostly: Entra, Defender, Intune, Purview, and Microsoft 365
Also: dad, metal, lifting, wrestling, cars
Mostly on Twitter rather than here: @rucam365
April 22-24, 2026, in Paris (Cité des sciences et de l'industrie); Modern Endpoint Management Summit, EMEA Edition
#MEMSummit
https://linktr.ee/modernendpointmanagement
#ConfigMgr | #MSIntune | #Windows10 | #Windows11 | #Azure | https://www.youtube.com/channel/UC3Kii1MYmVNmla5VgWIGqwA | blog.mindcore.dk | msendpointmgr.com
Founder of MSEndpointMgr.com
Microsoft MVP (2016 - Present)
Blog - https://msendpointmgr.com
X / Twitter - https://x.com/NickolajA
Reddit - https://www.reddit.com/r/MSIntune







