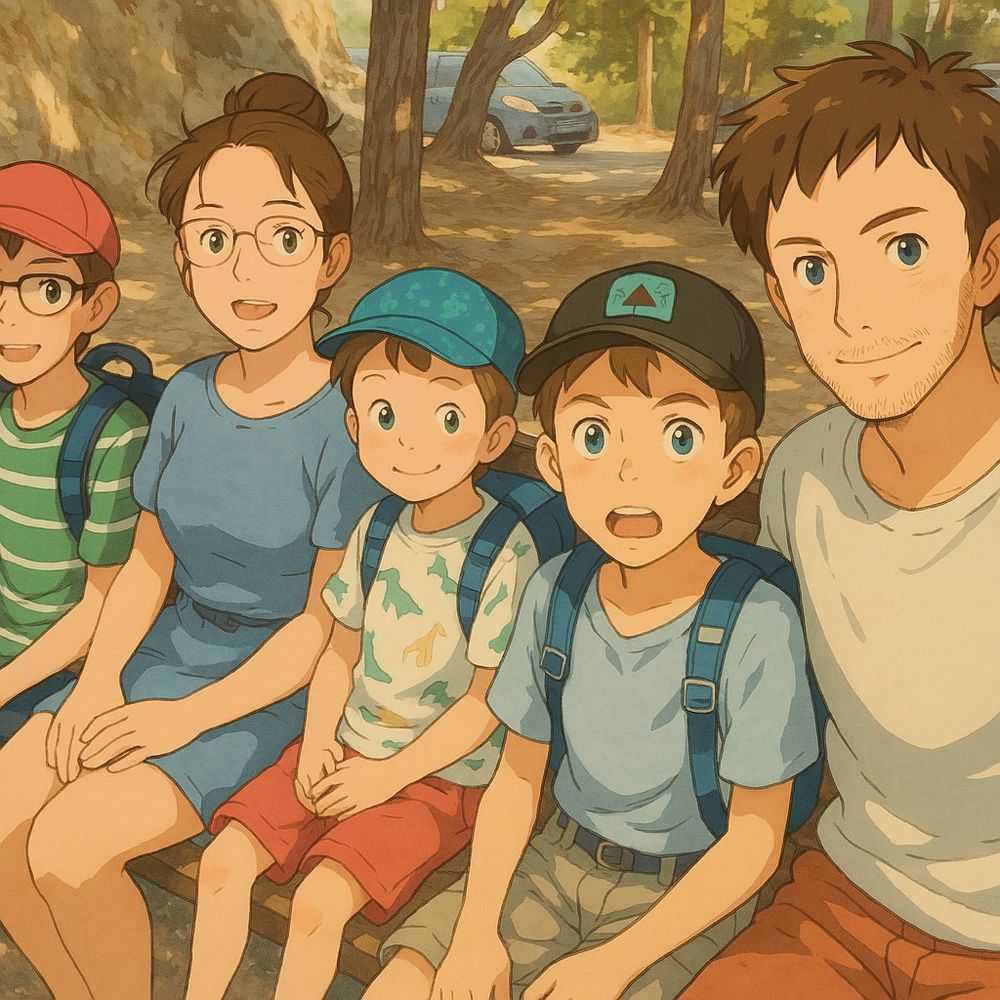
this is so much fun xD
27.03.2025 10:21 — 👍 0 🔁 0 💬 0 📌 0@gregor.plusepsilon.com
Co-founder zksecurity.xyz | Math & crypto | 🇦🇹

this is so much fun xD
27.03.2025 10:21 — 👍 0 🔁 0 💬 0 📌 0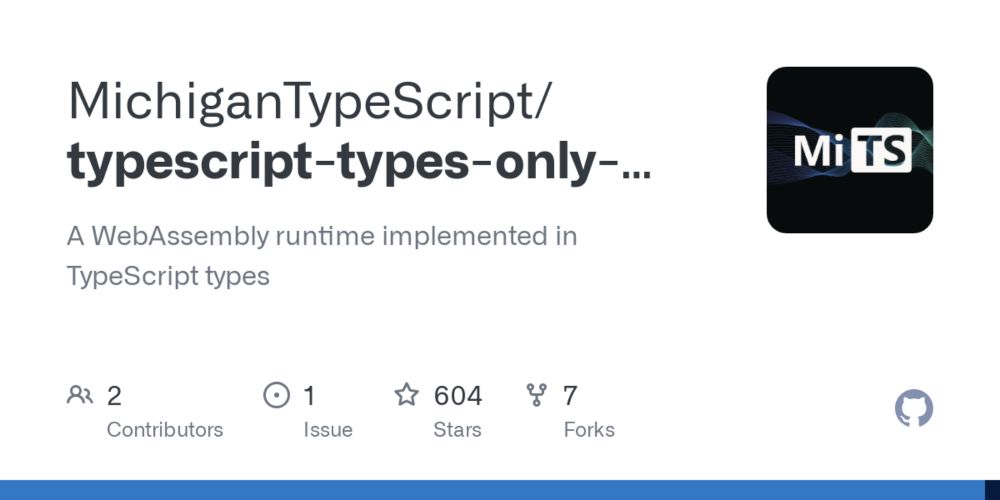
Code base: github.com/MichiganType...
27.02.2025 08:48 — 👍 0 🔁 0 💬 0 📌 0I think this is testament to the power and usefulness of TS "literal types", and I wonder why these don't seem to be common in type systems
Correct me if I'm wrong but don't think you can replicate this with e.g. Rust's or Lean4's types, even if they are generally seen as more advanced than TS
ridiculous and beautiful, TS types running Doom
27.02.2025 08:40 — 👍 1 🔁 0 💬 1 📌 0Ein LLM sollte mehr wie ein Lexikon sein als wie ein Schulbuch. Es sollte Informationen liefern, ohne den Anspruch diese moralisch korrekt zu interpretieren.
17.02.2025 08:03 — 👍 0 🔁 0 💬 1 📌 0Danke fürs Teilen! Für mich hören sich die Änderungen am Model Spec nicht falsch an, selbst wenn sie durch den politischen Rechtsshift motiviert sind.
Ich glaub dass sich LLMs bei heiklen Themen selbst zensieren war nie im Interesse der User, sondern eher nur um öffentlichen Aufschrei zu vermeiden

Abstract. The Fiat-Shamir (FS) transform is a prolific and powerful technique for compiling public-coin interactive protocols into non-interactive ones. Roughly speaking, the idea is to replace the random coins of the verifier with the evaluations of a complex hash function. The FS transform is known to be sound in the random oracle model (i.e., when the hash function is modeled as a totally random function). However, when instantiating the random oracle using a concrete hash function, there are examples of protocols in which the transformation is not sound. So far all of these examples have been contrived protocols that were specifically designed to fail. In this work we show such an attack for a standard and popular interactive succinct argument, based on the GKR protocol, for verifying the correctness of a non-determinstic bounded-depth computation. For every choice of FS hash function, we show that a corresponding instantiation of this protocol, which was been widely studied in the literature and used also in practice, is not (adaptively) sound when compiled with the FS transform. Specifically, we construct an explicit circuit for which we can generate an accepting proof for a false statement. We further extend our attack and show that for every circuit C and desired output y, we can construct a functionally equivalent circuit C^(*), for which we can produce an accepting proof that C^(*) outputs y (regardless of whether or not this statement is true). This demonstrates that any security guarantee (if such exists) would have to depend on the specific implementation of the circuit C, rather than just its functionality. Lastly, we also demonstrate versions of the attack that violate non-adaptive soundness of the protocol – that is, we generate an attacking circuit that is independent of the underlying cryptographic objects. However, these versions are either less practical (as the attacking circuit has very large depth) or make some additional (reasonable) assumptions on the underlying cryptographic primitives.

Image showing part 2 of abstract.
How to Prove False Statements: Practical Attacks on Fiat-Shamir (Dmitry Khovratovich, Ron D. Rothblum, Lev Soukhanov) ia.cr/2025/118
27.01.2025 01:58 — 👍 38 🔁 17 💬 0 📌 6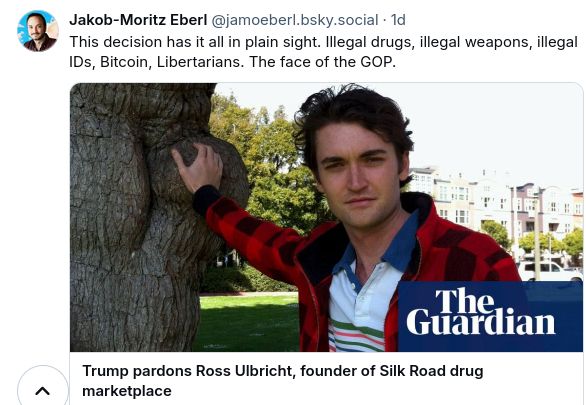
context:
23.01.2025 11:29 — 👍 3 🔁 0 💬 0 📌 0
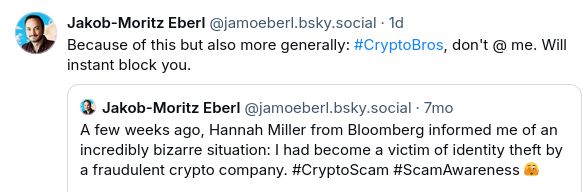
wurde das erste mal hier geblockt, und es fühlt sich nicht gut an. nur weil ich in der crypto industrie arbeite hab ich nichts mit irgendeinem scam zu tun
als linker finde ich es extrem schade wie negativ crypto (& tech generell) bei vielen konnotiert ist. speziell v einem politikwissenschaftler :(
Ich bin das Gegenteil von einem Trump-Fan, aber bin froh über diese Entscheidung. Warum soll jemand der einen "wild west" Marktplatz betrieben hat ein Leben lang im Gefängnis sitzen?? (Er hat auch nicht selbst mit Drogen gehandelt, btw, sondern nur die Plattform betrieben)
22.01.2025 08:13 — 👍 0 🔁 0 💬 1 📌 0Thanks, yep the aggregation of events is actually the biggest lift probably!
19.12.2024 07:00 — 👍 4 🔁 0 💬 0 📌 0"Profit/loss report" sounds relevant 🤔
18.12.2024 09:09 — 👍 3 🔁 0 💬 1 📌 0can it help me compute my taxes that are due to realized crypto gains? (Austria-style, where gains are only "realized" once you off-ramp to Euro or goods & services)
18.12.2024 09:07 — 👍 3 🔁 0 💬 1 📌 0Great thesis explaining the weird state of politics
06.12.2024 08:24 — 👍 1 🔁 0 💬 0 📌 0Seems like .at 🇦🇹 suddenly became a cool TLD because of atproto :D
02.12.2024 12:03 — 👍 1 🔁 0 💬 0 📌 0Abgesehen davon ist solches Signaling extrem gut und wichtig für die Adoption von Bluesky! Ich wäre nie hierher gewechselt wenn es nicht schon Traction gegeben hätte -- und von dieser Traction weiß ich in erster Linie durch die Ankündigungen auf X
02.12.2024 11:34 — 👍 10 🔁 0 💬 0 📌 0Wtf this makes no sense
28.11.2024 19:59 — 👍 1 🔁 0 💬 0 📌 0Yep - git was designed for merging, it's a much more natural flow
27.11.2024 14:35 — 👍 0 🔁 0 💬 0 📌 0Watching this great talk about the AT protocol
+ seeing the #eXit of big Austrian journalist accounts
= genuinely excited about BlueSky ❤️