On the long road to agentic systems, MCP tools are a well-lit highway rest stop, almost universally needed but still maybe not where you wanna linger too long
23.09.2025 00:42 — 👍 0 🔁 0 💬 0 📌 0
It’s funny to me that LLMs can perform better when given better English, when the reason many folks use LLMs is to minimize or eliminate the exercise of good writing
06.09.2025 21:55 — 👍 2 🔁 0 💬 0 📌 0
Agentic AI = nobody uses your web/mobile apps except when there is no other choice, which puts those UI assets in the same category as fax machines and paper contracts
25.08.2025 18:00 — 👍 1 🔁 0 💬 0 📌 0
Hard to admit but my #1 superpower is actually having failed so much, in so many different ways, and at different levels of scale, that I can sense failure in teams in real time as a physical sensation, the way dogs start barking before an earthquake
24.08.2025 19:50 — 👍 1 🔁 0 💬 0 📌 0
So much of “prompt engineering” is what we used to just call “being a good manager” and you might not really grok that without having managed a midsize team at some point in your career
05.08.2025 20:48 — 👍 1 🔁 0 💬 0 📌 0
I believe my marketing/events team would recognize this as my writing process
09.04.2025 02:36 — 👍 7 🔁 1 💬 2 📌 0

Why API Discovery Is Critical to Security
API discovery is critical to an organization's security posture because shadow and deprecated APIs are unmanaged risks that attackers can take advantage of.
Unmanaged #APIs create #security blindspots. 🕶️ 😧 And, as orgs build out their application ecosystems, the number of APIs integrated into IT environments expands — which can easily overwhelm security teams. ↕️ 👀 😵
Enter... API discovery.💥 Learn more.👇
graylog.org/post/why-api... #cybersecurity
04.03.2025 22:39 — 👍 2 🔁 1 💬 0 📌 0
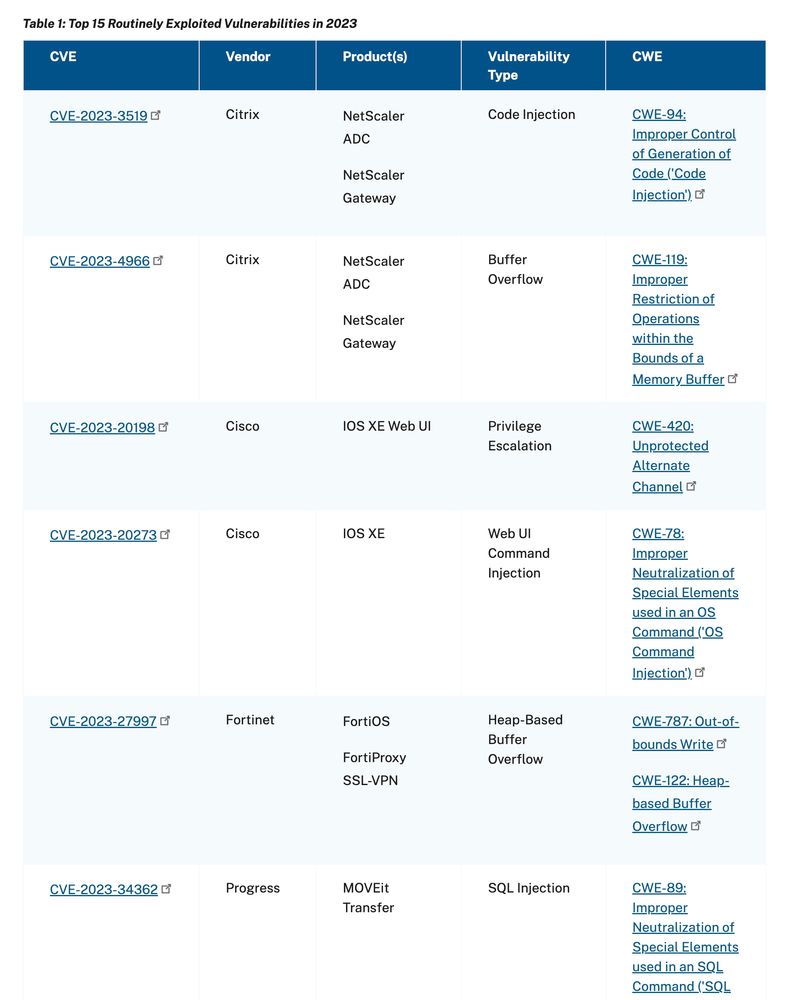
Table 1: Top 15 Routinely Exploited Vulnerabilities in 2023
- SQL injection
- Code injection
- Command injection
19.02.2025 16:01 — 👍 2 🔁 1 💬 0 📌 0
Fact: ORMs aren't a magic bullet for SQL injection. Misusing the API or vulnerabilities in the library itself can still cause problems.
I've seen it already with TypeORM and with Sequelize.
11.02.2025 10:01 — 👍 7 🔁 1 💬 0 📌 0

How To Approach API Security Amid Increasing Automated Attack Sophistication
In 2025, security teams must prioritize API monitoring, threat detection, and protection against both automated and traditional attacks to safeguard sensitive data.
#APIsecurity incidents were at an all time high in 2024. 🙀
With increasing #cyberattacks driven by #AI & automation, #security teams must have a strategy that emphasizes monitoring firewalls, gateways, etc. but also works towards detecting API data exfiltration.
www.itprotoday.com/vulnerabilit...
11.02.2025 21:17 — 👍 4 🔁 2 💬 0 📌 0
omg 🤦🏻♂️
10.02.2025 18:13 — 👍 2 🔁 0 💬 1 📌 0
The obvious question is whether this would actually be enforced…but imho establishing a federal standard of care for privacy is worth it either way
06.02.2025 18:04 — 👍 1 🔁 0 💬 0 📌 0

Syslog Protocol: A Reference Guide
Follow this guide Syslog Protocol: A Reference Guide and you will have enough information to understand the differences and nuances of Syslog.
Need a reference guide for the Syslog protocol? 📑 We've got you covered! 🙌
#Syslog is a logging protocol that is supported across many applications as well as hardware, and despite having been developed in the 1980s is still a very common format in use today. graylog.org/post/syslog-... #cybersec
04.02.2025 01:52 — 👍 5 🔁 3 💬 0 📌 0
Watch and wait and enjoy sports and hope that a national moment of realization obtains, gotcha
03.02.2025 22:20 — 👍 0 🔁 0 💬 0 📌 0
Just today have seen multiple phishing attempts offering “help” accessing frozen government funds and benefits
03.02.2025 19:48 — 👍 0 🔁 0 💬 0 📌 0
This is a really big deal about protecting critical infrastructure.
If any adversary takes down your water supply, you got a problem.
#CyberCivilDefense #take9
27.01.2025 20:03 — 👍 11 🔁 5 💬 1 📌 0

Everyday we're all for-real under threat of cyber attacks, that's seriously scary.
Good news is there’s something we can all do to thwart these dangers.
Here's a start: just pause and #Take9 seconds before you click, download, or share.
Follow @pausetake9 for more!
#CyberCivilDefense
27.01.2025 16:32 — 👍 34 🔁 12 💬 4 📌 0

Using Data Pipelines for Security Telemetry
Data pipelines automate the collection, transformation, and delivery processes to make data usable for analytics and visualization.
Not all orgs need heavy-hitting data pipeline management tools.🏋 Complex tools create extra work & require more skills. Simple ones won't give you the data you need. You need the “just right” tool.
Learn more about data pipelines & their benefits for security telemetry. graylog.org/post/using-d...
24.01.2025 21:20 — 👍 8 🔁 2 💬 0 📌 0
 17.01.2025 20:07 — 👍 2 🔁 1 💬 0 📌 0
17.01.2025 20:07 — 👍 2 🔁 1 💬 0 📌 0

Biden signs 11th-hour cybersecurity executive order
Ransomware, AI, secure software, digital IDs – there's something for everyone in the presidential directive
Is Biden's 11th-hour EO on cybersecurity DOA?
"Given the timing right before a change in the administration, I can't help but think it's a bit of a Hail Mary designed to include everything possible and just see what sticks."
17.01.2025 20:33 — 👍 5 🔁 3 💬 1 📌 0

Why Patching Isn’t the Ultimate Goal in Cybersecurity
Patching critical systems is always the fix for eliminating vulnerabilities. Or Is it? A focus on what matters and the priorities is best.
Hi #infosec, I wrote a blog about patching prioritization. CVE scores weren't meant to be the gold standard. Context from your runtime activity is an essential ingredient. And for those systems that cant/wont be patched, you need monitoring in place. graylog.org/post/why-pat...
08.01.2025 18:03 — 👍 3 🔁 2 💬 0 📌 0

These are the cybersecurity stories we were jealous of in 2024 | TechCrunch
The very best work from our friends at competing publications.
I love the annual tradition of @lorenzofb.bsky.social @zackwhittaker.bsky.social and @carlypage.bsky.social highlighting the best cybersecurity stories (and, in quite a few cases, thorough investigations) that other people wrote techcrunch.com/2024/12/24/t...
24.12.2024 18:59 — 👍 21 🔁 10 💬 0 📌 1
It's truly amazing we've reached the level of cybersecurity where China has hacked so many US telecom companies that the US government is now recommending the general public uses end-to-end encrypted messaging (something they spent the last 10+ years trying to ban "because terrorism").
19.12.2024 00:04 — 👍 469 🔁 111 💬 10 📌 3
What is an API attack and how does it work
To protect your organization from an API attack, you should know what APIs are and how threat actors use them to steal data.
Let's talk about #APIsecurity. As orgs integrate more applications, they add more #APIs, making API #security both more important and more challenging. 👀
Do you need help with API security? We've got you covered! Learn more.👇
graylog.org/post/what-is... #cybersecurity #infosec
17.12.2024 23:00 — 👍 2 🔁 1 💬 0 📌 0
Due to U.S. telco networks being compromised, today CISA is recommending:
1. Use only end-to-end encrypted communications
2. Enable Fast Identity Online (FIDO) phishing-resistant authentication
3. Migrate away from SMS-based MFA
4. Use a password manager to store all passwords
18.12.2024 17:59 — 👍 27 🔁 13 💬 2 📌 1
YouTube video by Trino
Virtual view hiearchies with Trino
The video from my Trino Summit talk on virtual views is now available: youtu.be/z8eh_3vBpvg
18.12.2024 21:05 — 👍 0 🔁 0 💬 0 📌 0
CEO & Co-founder @ Inventegy AI - https://inventegy.com
Building AI Products for Business Growth & Professional Efficiency!
🇸🇪📍 Stockholm, Sweden.
CYFI - Cyber Filings - Get Alerted First When Cybersecurity Filings Occur
Building AI products for business growth and professional efficiency!
https://inventegy.com
#AI #LLM #OpenAI #Anthropic #Gemini #Grok
We're an Al safety and research company that builds reliable, interpretable, and steerable Al systems. Talk to our Al assistant Claude at Claude.ai.
I want you to win and be happy. Code, OSS, STEM, Beyoncé, T1D, open source artificial pancreases, Portland, 3D printing, sponsorship http://hanselminutes.com inclusive tech podcast! VP of Developer Community @ Microsoft 🌮
http://hanselman.com/about
Events. Fun. My little person. My big Great Dane. Ice Cream. Beer.
Senior dev @github.com| Speaker & educator | Talking accessibility, refactoring, AI & career growth | Host of Overcommitted | The Balanced Engineer | Building sustainable careers in tech | brittanyellich.com #pdx
Dad, husband, teacher, coach, veteran. Governor of Minnesota. Working to move our state forward as #OneMinnesota.
Berkeley professor, former Secretary of Labor. Co-founder of @inequalitymedia.bsky.social and @imcivicaction.bsky.social.
Substack: http://robertreich.substack.com
Buy my new book: https://sites.prh.com/reich
Visit my website: https://rbreich.com/
Entertaining & educational conversations about science, tech, + more. Hosted by Ira Flatow and Flora Lichtman. From WNYCStudios.
Trans Rights are Human Rights.
alexwinter.com
Formerly of Tellme Networks
🐈 cat daddy 👨🍼 kid daddy
💘 husband 🧑🎓 MIT
⚾ Red Sox 💻 UI dev
📝 author 🎶 musician
📚 reader ⚛️ atheist
🚫 anti-MAGA 🌈 ally
🤡 woke AF 🦸♂️ nice guy
🍉Fun Stack Vibing at @xogot.bsky.social
Started Xamarin, Mono, Gnome. Prev: Microsoft/.NET/Xamarin/Mono/VSMac/MAIA http://mastodon.social/@migueldeicaza
Blog @ www.InnoVirtuoso.com | InfoSec, Cyber, AI Enthusiast | I write about Tech and News, AI, BCI, and other IT stuff.
Contact me at 📧 info@innovirtuoso.com
Journalist and Researcher | Reporting and Research on the U.S. Radical Right | Publisher of Radical Reports @radicalreports.bsky.social | Subscribe: https://www.radicalreports.org | Support My Work: https://linktr.ee/reportbywilson
Dr, apparently. Security Adovcate @semgrep & Hacker. #BugBounty hunter & #infosec YouTuber. APIs & Interlinked OffSec, PhD in AI+Sec @hacknotcrime. she/her
Engineering Manager @linkedin - a @microsoft company. Manages awesome @trinodb team. Past: @oracle (stream processing, middleware, RDBMS), @netapp, @ibm
Building https://typedef.ai | host @ https://techontherocks.show | Done some cool stuff with trinodb | ex-RudderStack | previously CEO @ Blendo








 17.01.2025 20:07 — 👍 2 🔁 1 💬 0 📌 0
17.01.2025 20:07 — 👍 2 🔁 1 💬 0 📌 0